What's New in Tenable Cloud Security: Enhanced Visibility, Prioritization, and Navigation

We have enhanced our Tenable Cloud Security CNAPP product to give you greater visibility, smarter prioritization, and a more streamlined user experience.
Key takeaways
- Tenable has improved our CNAPP by streamlining its navigation, making reports more customizable, and boosting visibility with a new "TV mode".
- Cloud workload protection has been enhanced with a more efficient Vulnerability Priority Rating (VPR) and granular Kubernetes vulnerability mapping.
- New identity and access management (IAM) features and just-in-time (JIT) updates simplify the enforcement of least-privilege policies.
The Tenable Cloud Security team is always hard at work to ensure our cloud-native application protection platform (CNAPP) has all the capabilities you need to secure your multi-cloud environment.
In this blog, we’ll outline our latest round of enhancements, focused on providing greater visibility, smarter prioritization, and a more streamlined user experience. Read on to get all the details.

A more intuitive and efficient platform
We're excited to introduce these significant usability and reporting enhancements to the Tenable Cloud Security CNAPP:
- Streamlined console navigation: We've completely redesigned the console navigation menu for a more intuitive and efficient user experience. This major update helps you find the insights you need faster.
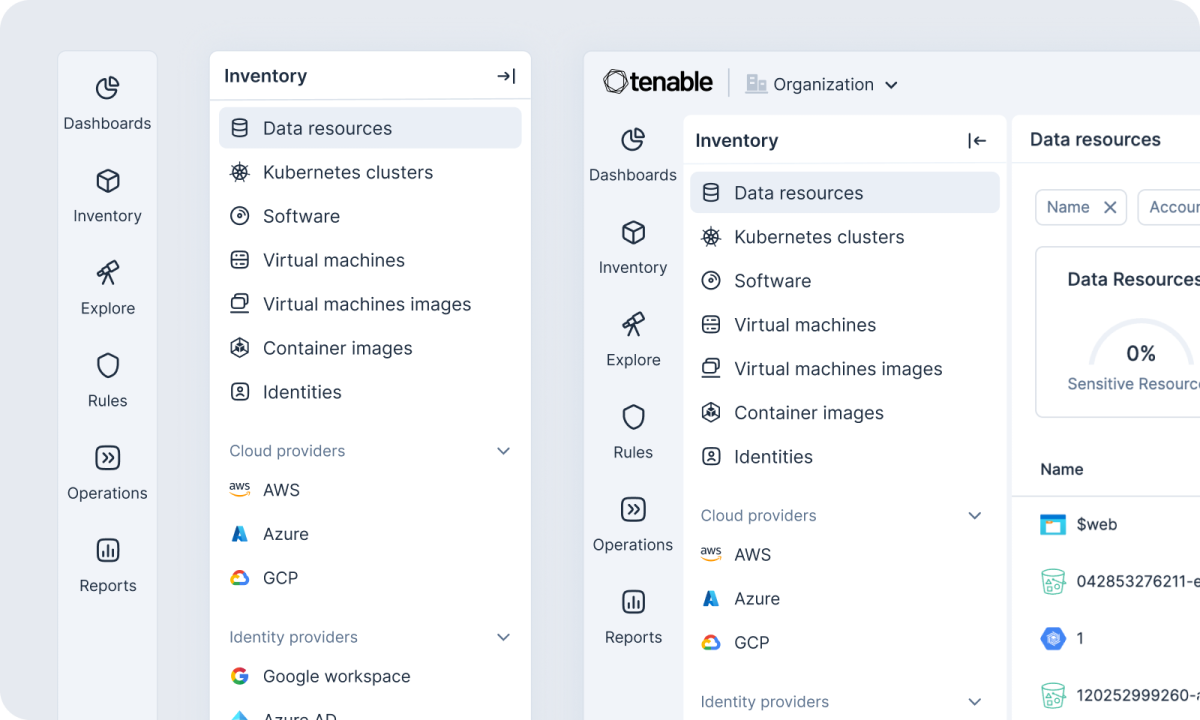
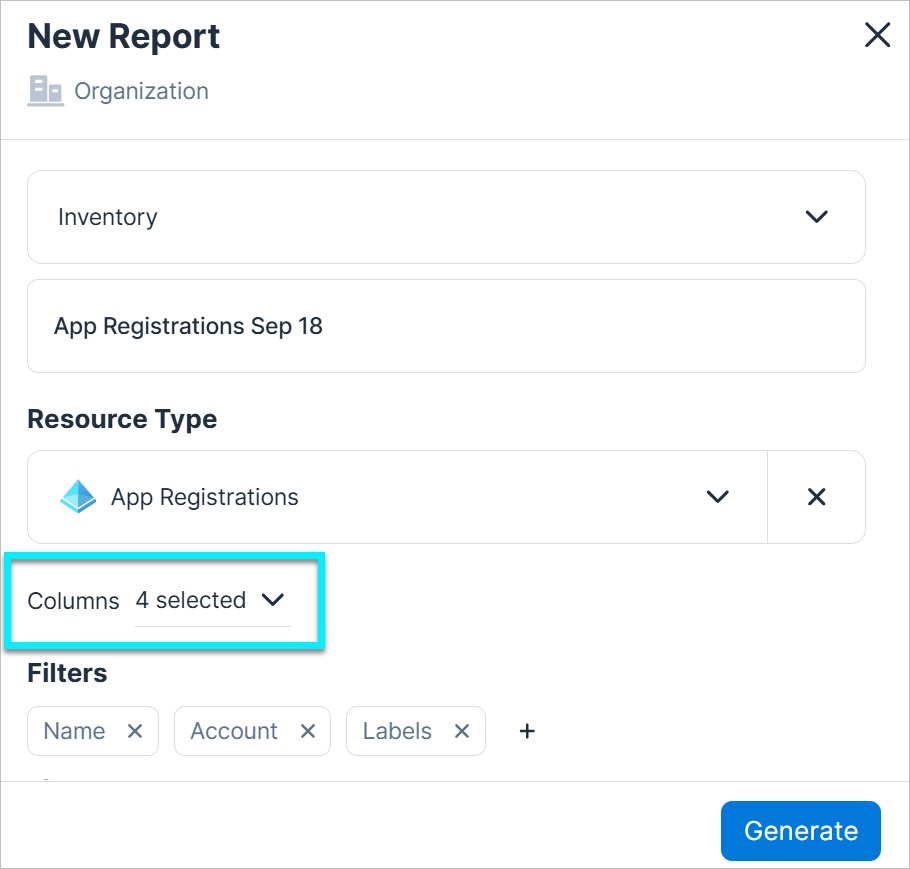
- Customizable inventory reports: You can now customize your inventory reports by selecting specific columns to include. This allows you to create more focused and efficient reports with just the information you need for expedited decision-making.
- TV mode: For continuous, real-time operational display and broad visibility of your security status, you can now view any dashboard in a full-screen, distraction-free "TV mode."

These updates are all about providing more context and value, allowing you to see and act on your security data more efficiently with intuitive navigation, tailored reports, and always-on visibility.
Enhanced cloud workload protection (CWP)
We've made significant strides in our cloud workload protection capabilities to provide you with more precise, risk-contextualized visibility and prioritization:
- Enhanced Vulnerability Priority Rating (VPR): Our enhanced VPR is now twice as efficient, enabling your teams to focus on the 1.6% of vulnerabilities that pose a real risk, sharpening your prioritization efforts.
- Improved coverage and accuracy: We've improved vulnerability detection accuracy by adding scoped npm packages for better visibility into workloads running Node.js and by no longer flagging unused kernel versions in Linux workloads.
- Granular Kubernetes vulnerability management: You can now directly map vulnerability findings in container images to specific Kubernetes workloads, which clarifies risk attribution and streamlines remediation.
Advanced identity and access management (IAM)
Identity-related issues are a top concern in cloud security. We're introducing new features to help you establish a pervasive and frictionless least-privilege posture:
- Configure trusted vendors: You can now mark external vendors as trusted users to reduce non-critical alerts about them. This helps focus your monitoring and toxic-combination analysis on truly risky identity exposures.
- Automated remediation of unused SSO permissions: You can now quickly identify and remove inactive single sign-on (SSO) groups or users with a single click to streamline your process of eliminating dormant roles and their permissions.
- Streamlined just-in-time (JIT) access: We’ve enhanced our Slack support with key actions from the JIT Portal, including self-revoking active sessions and submitting recurring access requests. These updates streamline the adoption of least-privilege policies.
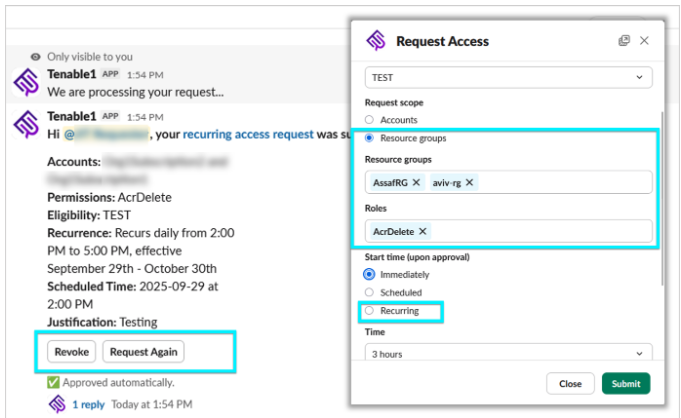
These new features in Tenable Cloud Security are designed to empower you to work faster and smarter. By providing a more intuitive platform, enhancing workload protection, and offering advanced IAM and JIT capabilities, we're helping you to stay ahead of evolving cloud threats and proactively secure your multi-cloud environment.
New cloud security use cases and research from Tenable
Check out these new cloud security resources we’ve recently published:
- Four common uses for Tenable Cloud Security:
- Recent cloud security research:
- Gemini Trifecta: Read about the three (now-remediated) vulnerabilities Tenable Research discovered within Google’s Gemini AI assistant suite.
- A new insight brief: Explore key observations on complexity gleaned from our recent “State of the Cloud & AI Security” report.
- Cloud



