Cybersecurity Snapshot: Phishing Scams, Salary Trends, Metaverse Risks, Log4J Poll

Get the latest on worrisome phishing stats; businesses’ embrace of the metaverse, come what may; a (small) improvement in CISO job stability; the compensation cost of security leaders; and more!
Dive into six things that are top of mind for the week ending Dec. 16.
1 - CISA: Employees fall for phishing scams at an alarming rate
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has revealed distressing stats about the prevalence and success of phishing attacks.
In a newly published infographic, CISA shared phishing data collected during assessments it has conducted for federal agencies and for public and private critical infrastructure organizations.

Here are stats from the phishing tests CISA conducted at these agencies and organizations:
- In 80% of assessed organizations, at least one individual fell victim to a phishing attempt.
- Users executed a malicious attachment or interacted with a malicious link in 10% of the phishing emails.
- Products designed to protect assessed organizations’ networks failed to block 70% of malicious files or links.
- Endpoint protection tools failed to block 15% of malicious attachments or links.
CISA’s recommendations to prevent phishing attacks include:
- Deploy strong network border protections
- Set up email servers to use protocols that verify emails are legit
- Configure firewalls to block known malicious domains, URLs and IP addresses
- Train employees to recognize phishing indicators and report phishing emails
- Require phishing-resistant multifactor authentication
- Cut the number of accounts with access to critical data and systems
For more information, check out the CISA infographic.
More phishing prevention resources:
- “Phishing protection: Keep employees from getting hooked” (TechTarget)
- “How to prevent spear phishing attacks: 8 tips for your business” (TechRepublic)
- “Prepare for deepfake phishing attacks in the enterprise” (TechTarget)
- “What is phishing-resistant multifactor authentication? It’s complicated.” (Cybersecurity Dive)
- “CISA Publishes MFA Guidelines to Tackle Phishing” (Infosecurity Magazine)
2 - Report: Turnover slows among CISO ranks
CISOs are always on the hot seat but job stability improved in 2022, as the average tenure increased, turnover slowed down and internal hiring grew.
That’s according to the report “Global Snapshot: The CISO in 2022,” from global executive search firm Marlin Hawk, which polled CISOs from 470 companies in North America, Europe and Asia Pacific with at least 10,000 employees.
Key findings include:
- The percentage of CISOs who have been at their current role for two years or less dropped to 45% from 53% in 2021, with an 18% turnover rate – still high but potentially stabilizing.
- A slightly higher percentage of CISOs were hired from within – 38% in 2022 versus 36% last year.
- Diversity among CISO ranks -- not good to start with -- worsened a bit: 13% of respondents were women and 20% were non-white, down from 14% and 21% respectively in 2021.

The report also looks at how the CISO role is evolving – namely towards a broader scope of responsibilities, such as data privacy compliance, physical security, engineering, business risk, operational resilience, product design/security and technology architecture.
Regarding reporting structures, most CISOs report to either the CIO or CTO (78%), and only 12% report to the CEO – but whichever the case, the typical CISO is accountable to many top executives.
“The CISO reporting line can go into any one – or multiple dotted lines -- of a variety of C-suite leaders reflecting the breadth of knowledge required from today’s CISO,” reads the report.
For more information, read a summary of the report or the full report.
To get more details about CISO trends, check out these Tenable blogs:
- “CISOs Tell All: Everything You’ve Ever Wanted To Know About CISOs in 2022”
- “A Recipe for Success: CISOs Share Top Tips for Successful Board Presentations”
- “The shift to integrated cybersecurity platforms: a growing trend among CISOs”
- "How Security Leaders Can Become Dev and Ops Whisperers"
- "Consolidate and Unify to Accelerate Your Security Efforts"
3 - How much do cybersecurity leaders make?
And speaking of CISOs, one of their key responsibilities is recruiting and retaining a strong roster of security leaders with the right skills and experience. To accomplish this, CISOs must know the most current compensation trends for these “cybersecurity lieutenant” roles.
That’s the focus of a new report from information security consultancy IANS Research and executive recruiter Artico Search, which polled 522 CISOs and compiled compensation data – in U.S. dollars, Canadian dollars, euros and British pounds – for seven CISO “direct report” roles.
The average total compensation for these executives, including deputy CISOs and leaders of security operations, product security and app security, is – drumroll! – $301,000, while the median is $245,000. Those compensation figures include base salary, bonuses and equity grants.
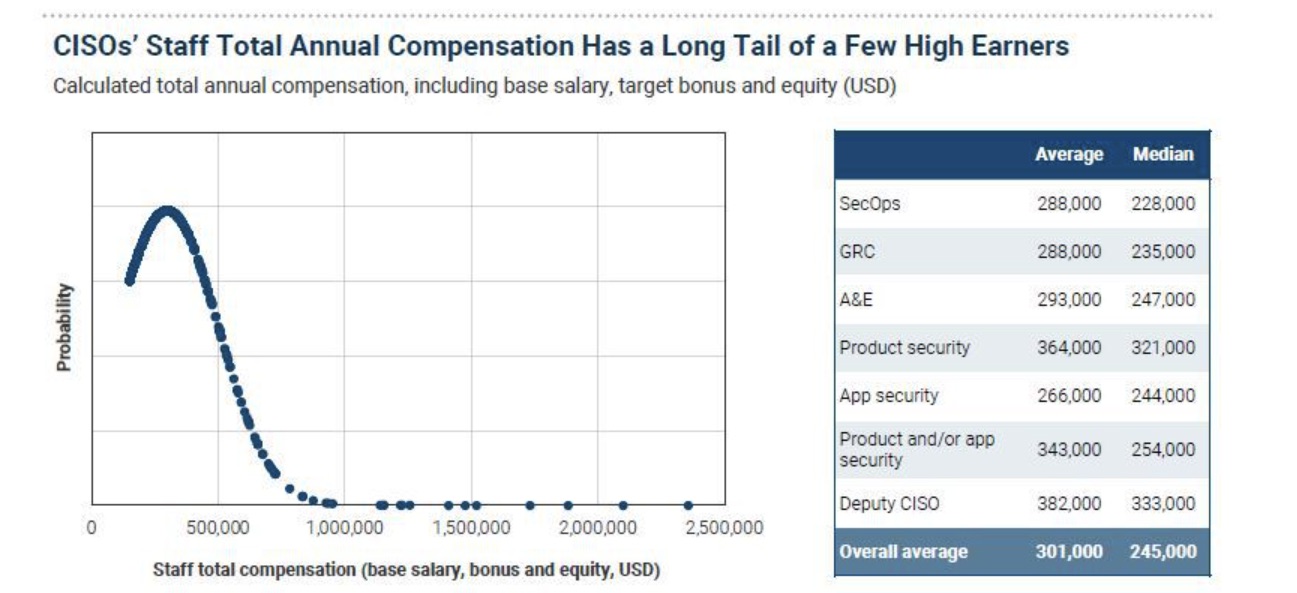
(Source: “2022 Security Organization and Compensation Benchmark Report” from IANS Research and Artico Search, December 2022)
Another insight: Almost all CISOs struggle to recruit for and maintain a fully staffed leadership team, with vacant roles taking two to four months to fill because the competition for candidates is fierce.
This means that hiring and retaining the best candidates isn’t going to be cheap. “CISOs should focus on paying rates in the top quartile comp brackets to gain a recruiting and retention advantage,” reads a blog about the report.
In case you’re wondering, that translates to an average total compensation of $540,000 based on the report’s data.
For more information, request a copy of the report.
To dive deeper into recruitment and compensation of cybersecurity leaders, check out:
- “Executive Recruiters Scrambling to Find Cybersecurity Leaders” (Hunt Scanlon Media)
- “How To Handle Today’s High CISO Turnover” (Chief Executive)
- “7 CISO succession planning best practices” (TechTarget)
- “CISOs to employers: Show me the money!” (Tenable)
- “Cybersecurity master’s grads are landing $200K-plus pay packages” (Fortune)
4 - Tenable: Businesses take metaverse plunge as cyber risks loom
Eager to capitalize on emerging business opportunities, most organizations are venturing into the metaverse, and thereby significantly expanding their already large and complex cyber attack surfaces.
That’s a key finding from Tenable’s “Measure Twice, Cut Once: Meta-curious Organizations Relay Cybersecurity Concerns Even as They Plunge Into Virtual Worlds” report, based on a survey of 1,500 IT, cybersecurity and DevOps pros in Australia, the U.K. and U.S.
The study found that 23% of polled organizations have already launched offerings in the metaverse, while 58% plan to do business in the metaverse within the next year. In other words, metaverse protection, involving the customary required triad of people, processes and technology, either is or soon will be another critical task for many cybersecurity teams.

However, despite this metaverse “gold rush,” under 50% of organizations reported feeling very confident at this point about curbing threats in this still nascent environment, which houses both new and legacy cybersecurity risks, such as conventional phishing attacks and novel cloning of avatar voice and facial features.
Tenable CSO Robert Huber said organizations establishing a metaverse presence should invest wisely in their security staff and in the security and integrity of their infrastructure. “The foundation of the cybersecurity program must be solid before making a big leap into largely unknown territory and drastically expanding your attack surface,” Huber said.
To get all the details, download the 18-page report, view an infographic and read a blog about it.
For more information about metaverse cybersecurity:
- “Why privacy and security are the biggest hurdles facing metaverse adoption” (VentureBeat)
- “Europol: Police chiefs need to get hip to the metaverse” (Tenable)
- “The metaverse is coming, and the security threats have already arrived” (ZDNet)
- “Top metaverse cybersecurity challenges” (TechTarget)
- “The metaverse has a groping problem already” (MIT Technology Review)
VIDEOS:
- Interview with Tenable Senior Staff Engineer Satnam Narang (Ticker Insight)
Three Things to Know about the Metaverse (TechTarget)
Trapped in the Metaverse (Wall Street Journal)
How criminals are targeting investors on the metaverse (CNBC)
5 - Log4j poll: How’s it going? What’s changed?
It’s now been a little over a year after the massive Log4j crisis rocked the IT and cybersecurity worlds, so at recent Tenable webinars we asked attendees a few questions about this topic. Here are the results of our unscientific but nonetheless enlightening poll.
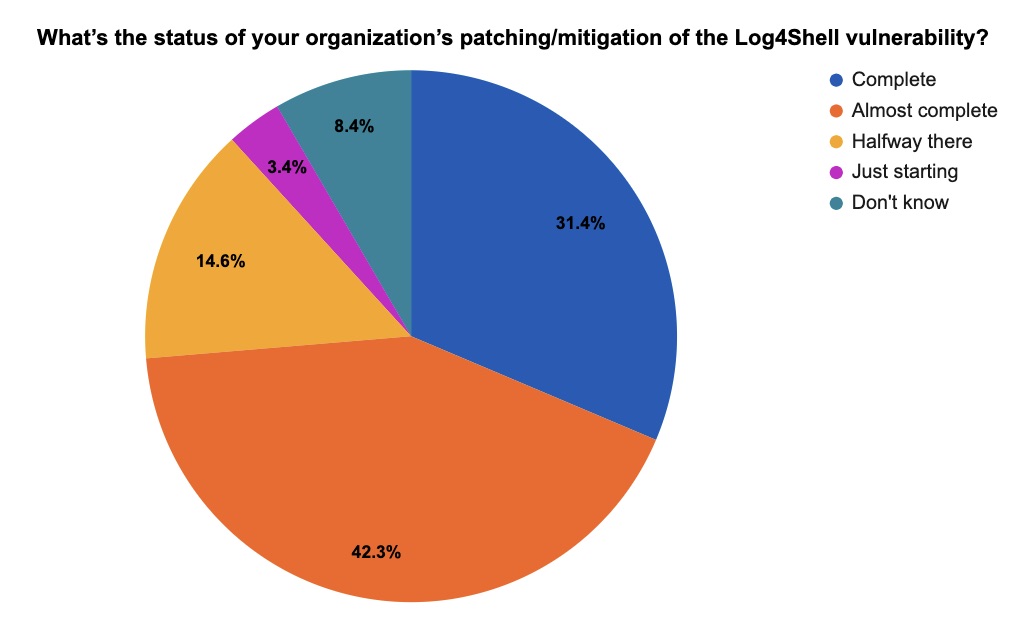
(357 respondents polled by Tenable, December 2022)
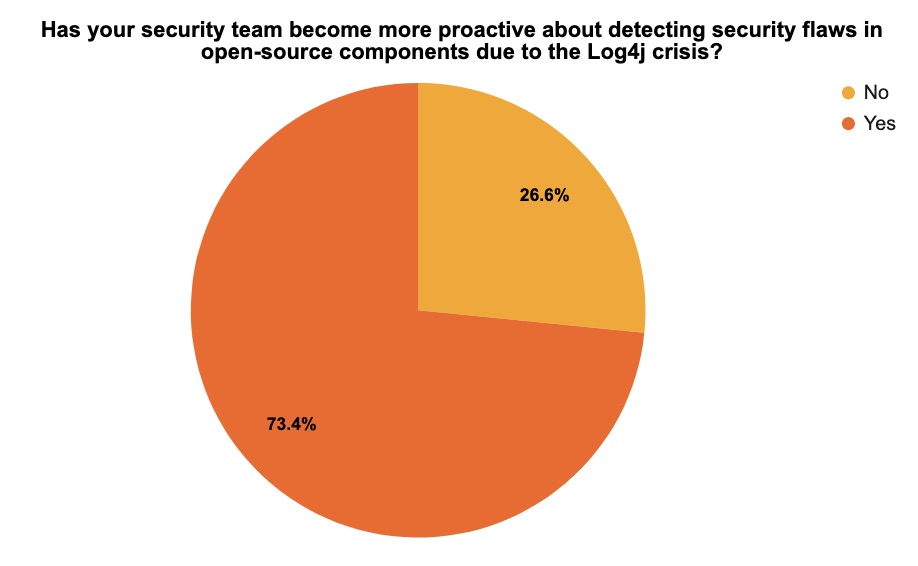
(143 respondents polled by Tenable, December 2022)
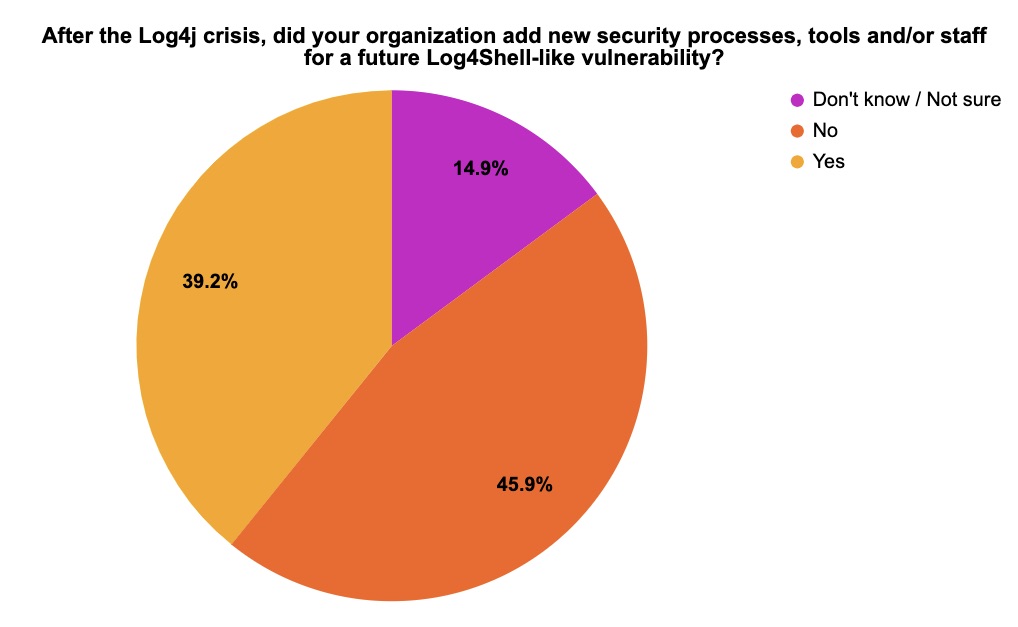
(148 respondents polled by Tenable, December 2022)
For more insights, recommendations and best practices about Log4j, check out these Tenable resources:
- “Tenable Research Finds 72% of Organizations Remain Vulnerable to ‘Nightmare’ Log4j Vulnerability” (Telemetry data analysis)
- “Are You Ready for the Next Log4Shell? Tenable’s CSO and CIO Offer Their Advice” (blog)
- Tenable’s Log4j resource page
- “Apache Log4j Flaw: A Fukushima Moment for the Cybersecurity Industry” (blog)
VIDEOS
Discovering Log4Shell (CVE-2021-44228) vulnerabilities: Tenable.io
Discovering Log4Shell (CVE-2021-44228) vulnerabilities: Tenable.sc
Discovering Log4Shell (CVE-2021-44228) vulnerabilities: Tenable.io Web App Scanning
Discovering Log4Shell (CVE-2021-44228) vulnerabilities: Nessus Professional
6 - Patch these vulnerabilities – now!
Here are the most recent zero-day vulnerabilities that Tenable recommends you patch ASAP.
- In its December Patch Tuesday, Microsoft addressed 48 CVEs, including two zero-day vulnerabilities – one of which (CVE-2022-44698) has been exploited in the wild. Get the whole story in this blog from Tenable’s Security Response Team (SRT)
- Citrix this week disclosed CVE-2022-27518, a critical remote code execution (RCE) vulnerability impacting several supported versions of Citrix Application Delivery Controller (ADC) and Citrix Gateway. Read the Tenable SRT blog for all the details about this zero-day vulnerability reportedly exploited in the wild.
- Fortinet patched an actively-exploited, zero-day overflow vulnerability in FortiOS (CVE-2022-42475) that could lead to remote code execution, as Tenable Senior Research Engineer Claire Tills explains in this blog.
Check out these recently published blogs from Tenable’s SRT team:
- “Top 20 CVEs Exploited by People's Republic of China State-Sponsored Actors (AA22-279A)”
- “Brazen, Unsophisticated and Illogical: Understanding the LAPSUS$ Extortion Group”
- “AA22-257A: Cybersecurity Agencies Issue Joint Advisory on Iranian Islamic Revolutionary Guard Corps-Affiliated Attacks”
- “Understanding the Ransomware Ecosystem: From Screen Lockers to Multimillion-Dollar Criminal Enterprise”
- “Analyzing the Vulnerabilities Associated with the Top Malware Strains of 2021”
And one more thing! View the latest episode of Tenable Cyber Watch, a weekly video newscast that highlights topics drawn from this blog that matter for cybersecurity professionals around the world. Catch it every Monday morning on the Tenable blog or subscribe to our YouTube playlist.
- Cybersecurity Snapshot
- Exposure Management
- Government
