by Cody Dumont
April 5, 2021
Building an effective cybersecurity program is an ongoing process requiring the Chief Information Security Officer (CISO) to establish vulnerability management metrics. The CISO needs the ability to publish content quickly and easily, which clearly communicates the state of the cyber security programs to executive leadership. This report provides a high level summary of the top 10 vulnerabilities based on Common Vulnerability Scoring System (CVSS) and Vulnerability Priority Rating (VPR).
Tenable calculates a dynamic VPR for most vulnerabilities. The VPR is a dynamic companion to the data provided by the vulnerability's static CVSS score, since Tenable updates the VPR to reflect the current threat landscape. The VPR score combines research insights, threat intelligence, and vulnerability ratings to reduce noise. VPR values range from 0.1-10.0, with a higher value representing a higher likelihood of exploit.
This report assists cyber security leaders that are building or strengthening a vulnerability management program to better visualize the most threatening vulnerabilities. When using CVSS filters alone, the noise increases and a large quantity of critical and high vulnerabilities are the result. This larger quantity of vulnerabilities often results in a task list that becomes cumbersome and difficult to prioritize and mitigate. By leveraging VPR in addition to CVSS, there is less noise and the analyst can focus on the findings that organizations should prioritize and mitigate first.
Using VPR, the CISO quickly understands which threats are active in the wild and can better direct mitigation efforts. Effective vulnerability remediation becomes easier as vulnerabilities are presented in a manner that helps visualize vulnerability remediation programs and provides measures against established goals and SLAs. The CISO is better able to establish a measurable reference point used by cyber security leaders to create actionable mitigation tasks.
The report supports filters from the Nessus user interface, which are reflected in the output report. In the Nessus user interface, the analyst can use filters either by host or vulnerability. For example, by setting a filter for hosts that contain “192.168.0.”, the output of the report will be limited to the specified network. This allows risk managers to identify risks based on subnet or other data attributed collected by Nessus. This report template is available for Nessus Professional PDF or HTML reports.
Tenable built the most innovative vulnerability scanner, Nessus, which is the world's most widely deployed vulnerability assessment scanner. Powerful and flexible to adapt to the unique requirements of today's modern networks. Nessus provides visibility into a wide range of assets on many computing platforms. The data in this report provides insight into user account and group membership information.
This report contains the following chapters:
Overview
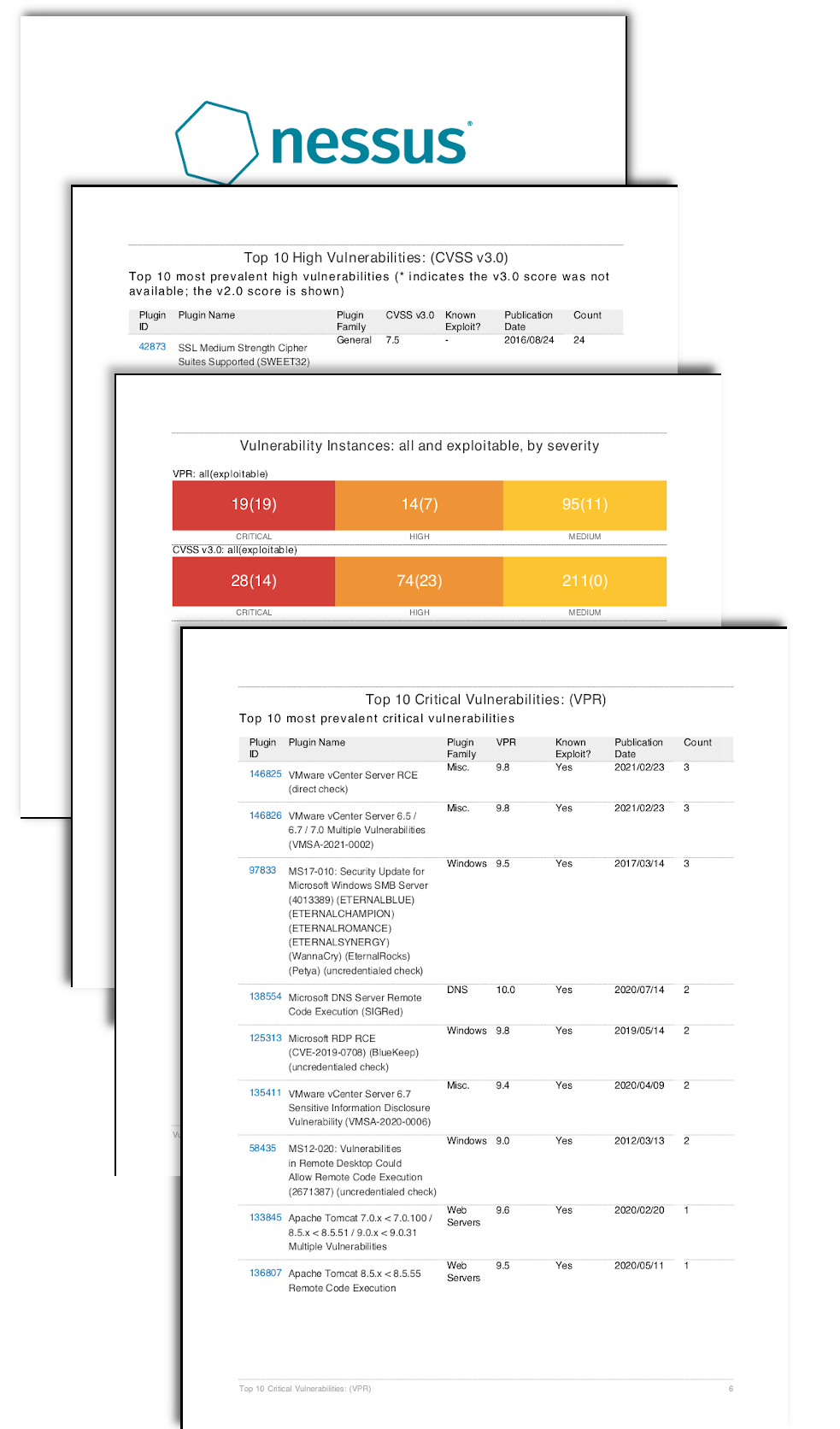
The Overview section contains two summary tables of vulnerabilities by severity, by VPR and CVSSv2 or CVSSv3, depending on the base severity selected for the scan. The number shown represents the vulnerability count, and in parentheses is the count of exploitable vulnerabilities. Also provided is the count based on severity level, which differs by severity metric. Severity classifications are explained as follows:
- VPR - Critical (Red) 9.0 - 10, High (Orange) 7.0 - 8.9, Medium (Yellow) 4.0 - 6.9
- CVSSv3 - Critical (Red) 9.0 - 10, High (Orange) 7.0 - 8.9, Medium (Yellow) 4.0 - 6.9
- CVSSv2 - Critical (Red) 10, High (Orange) 7.0 - 9.9, Medium (Yellow) 4.0 - 6.9
Top 10 Critical Vulnerabilities
The two tables in this chapter provide the top 10 vulnerabilities filtered by the critical VPR and by critical CVSSv2 or CVSSv3, depending on the base severity selected for the scan. Critical severity is used for VPR scores between 9.0 - 10, CVSSv2 10, and CVSSv3 between 9.0 – 10. The vulnerabilities identified using VPR are exploitable and prevalent in the current threat landscape, and based on an in-depth threat analysis, are considered the most critical to mitigate. Traditionally, the method for identifying risk was most commonly with CVSSv3 or CVSSv2. While each still remain important, and should be mitigated, these vulnerabilities do not have the same context as VPR identified vulnerabilities.
Top 10 High Vulnerabilities
The two tables in this chapter provide the top 10 vulnerabilities filtered by the High VPR and by High CVSSv2 or CVSSv3, depending on the base severity selected for the scan. High severity is used for VPR and CVSSv3 scores between 7.0 - 8.9, CVSSv2 between 7.0 – 9.9. The vulnerabilities identified using VPR are exploitable and prevalent in the current threat landscape, and based on an in-depth threat analysis, are considered the most critical to mitigate. Traditionally, the method for identifying risk was most commonly with CVSSv3 or CVSSv2. While each still remain important, and should be mitigated, these vulnerabilities do not have the same context as VPR identified vulnerabilities.
Top 10 Prevalent Vulnerabilities
The two tables in this chapter provide a top 10 vulnerabilities grouped using the Medium through Critical. For VPR, CVSSv3, and CVSSv2 the rating is 4.0 - 10. The vulnerabilities identified using VPR are exploitable and prevalent in the current threat landscape, and based on an in-depth threat analysis, are considered the most critical to mitigate. Traditionally, the method for identifying risk was most commonly with CVSSv3 or CVSSv2. While each still remain important, and should be mitigated, these vulnerabilities do not have the same context as VPR identified vulnerabilities.