Taking Nessus Perimeter Service to the Next Level
There are several organizations who fit the mold of having just one Nessus scanner. The fact that they own and operate just one scanner is fantastic, it means they have the capability to discover vulnerabilities in their environment, and for most small to mid-sized companies can perform internal scans on a regular basis and react on the results.
However, one component missing from this equation is the perspective of the external view. Your Internet-facing systems face a much larger and diverse threat, yet I am amazed at how many organizations are not scanning it on a regular basis. I understand the issue; you may not have systems or networks setup that are outside of your own network authorized to do scanning. Also, your internal scanner is tied up doing other tasks, such as credentialed patch audits, mobile device scanning, and web application scanning.
To solve this problem, Nessus Perimeter Service users can combine two offerings/features from Tenable Network Security:
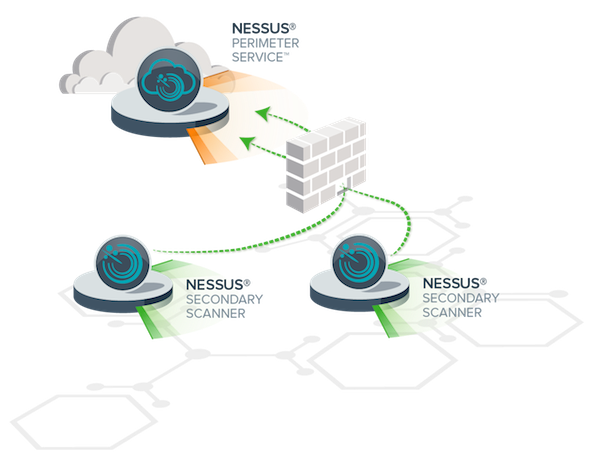
- Nessus Perimeter Service - The cloud-based offering from Tenable runs 24/7, eliminating the need for the end user to have to worry about Nessus upgrades and plugin updates, and the overhead of managing yet another device in your environment. Scans of your network perimeter can be scheduled, and the results sent to the team(s) responsible for fixing the problems
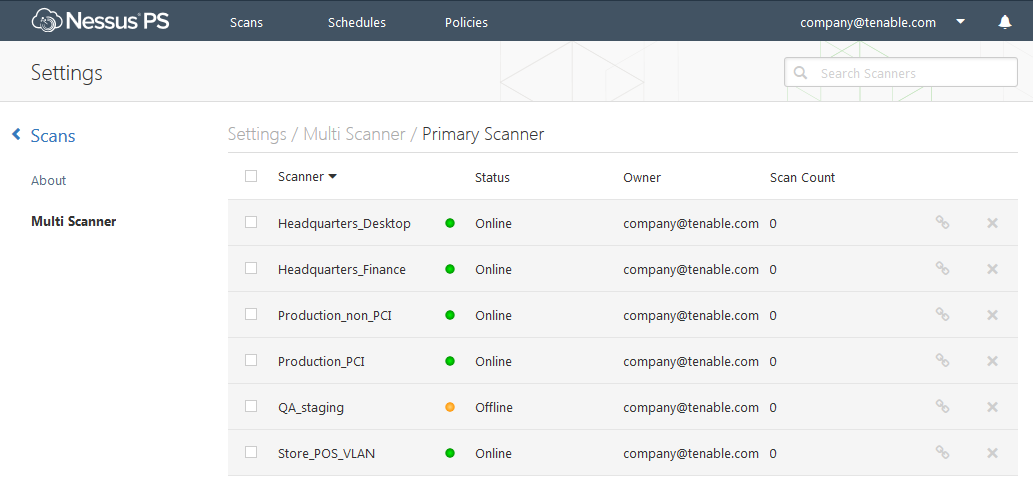
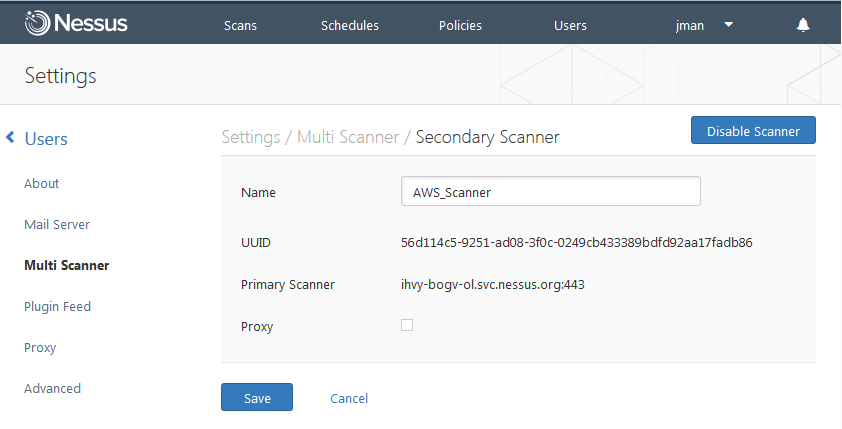
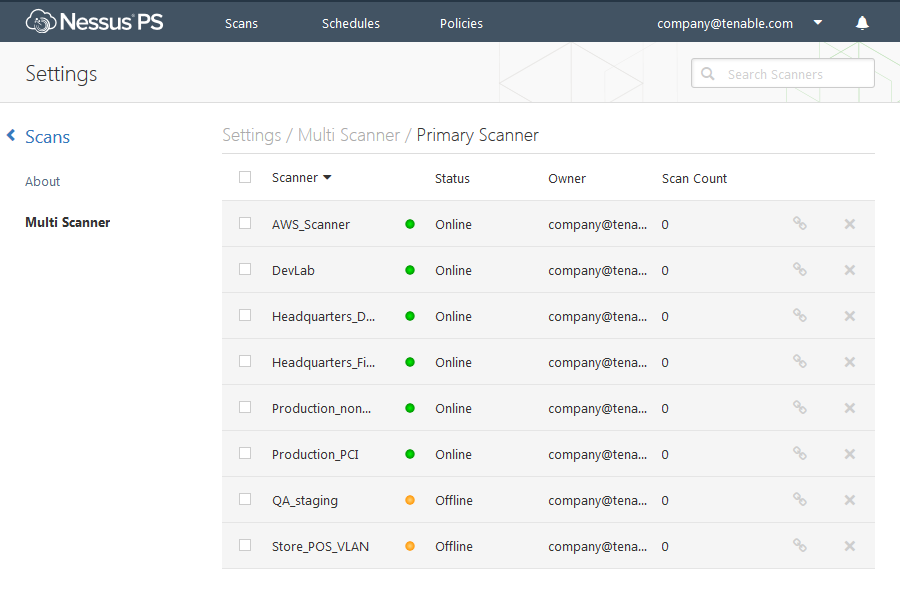
- Nessus Multi-Scanner - You are now able to designate an unlimited amount of Nessus scanners to be secondary scanners of your Nessus Perimeter Service (primary scanner). Lets start with just one at first, and setup an internal Nessus scanner, then make it a secondary scanner to Perimeter Service. Now you can scan both your internal network and external network from the same place. This allows you to control your scans, policies, schedules and email reports from one Nessus scanner, giving you both the internal and external views of your vulnerabilities.
[video:http://youtu.be/TidTX_inBGM]
Nessus Level: Expert
I'd like to add yet another scenario. As your company grows, so do the number of systems and even the number of locations. A new branch office is opening and you as the security team, must provide insights into the vulnerabilities at remote offices. You can deploy an additional server to that location, and use Perimeter Service to delegate scans, and email those reports to the responsible parties.
Now lets take it even further. You've just had a meeting with your boss and told him how much money the company can save by using a cloud deployment. It will dramatically reduce overhead and allow for easier management of systems. But, the question becomes, how do you manage the vulnerabilities and security of your new cloud deployment? Not a problem, if you are using Amazon's EC2 offering, you can deploy a Nessus AMI instances, configured for you already, apply a license and set it as the secondary server to your Nessus Perimeter Service scanner. Now, you can scan from both within your cloud using the secondary scanner in AMI and scan the external perimeter of your cloud instance for vulnerabilities.
Conclusion
Nessus and Nessus Perimeter Service now offer many different options to cover all areas of your organization, so there is a slim chance vulnerabilities will hide from you. The combination of Perimeter Service and the Nessus multi-scanner feature allow you to scan the internal, external, remote locations, and cloud deployments from one easy-to-use interface.
Scanners on the more trusted internal networks can perform credentialed patch and/or configuration audits, in addition to detecting malware, integrating with patch management systems, and a host of other features. External scans will detect vulnerabilities in your web servers, web applications, and indicate certain compromises of your Internet-facing systems.
- Cloud
- Nessus