CVE-2021-21985: Critical VMware vCenter Server Remote Code Execution

VMware has issued patches for a critical remote code execution vulnerability in vCenter Server. Organizations are strongly encouraged to apply patches as soon as possible.
Update June 2: The Identifying Affected Systems section has been updated to include audit checks for the workaround.
Update June 4: The Proof of Concept section has been updated to reflect the publication of exploit code and active scanning for vulnerable servers.
Background
On May 25, VMware published an advisory (VMSA-2021-0010) regarding two vulnerabilities impacting vCenter Server, a centralized management software for VMware vSphere systems. In a rare move, VMware also published a blog post providing guidance on how users can mitigate these vulnerabilities.
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2021-21985 | Remote code execution vulnerability in vSphere Client | 9.8 |
| CVE-2021-21986 | Authentication mechanism issue in vCenter Server Plug-ins | 6.5 |
In February, VMware patched two other vCenter Server vulnerabilities, CVE-2021-21972 and CVE-2021-21973. Researchers saw mass scanning for CVE-2021-21972 within a day of its publication.
Analysis
CVE-2021-21985 is a remote code execution vulnerability in the vSphere Client via the Virtual SAN (vSAN) Health Check plugin, which is enabled by default. This vulnerability is assigned a CVSSv3 score of 9.8, making this a critical flaw.
To exploit this vulnerability, an attacker would need to be able to access vCenter Server over port 443. Even if an organization has not exposed vCenter Server externally, attackers can still exploit this flaw once inside a network. VMware specifically calls out ransomware groups as being adept at leveraging flaws like this post compromise, after having gained access to a network via other means such as spearphishing. Successful exploitation would give an attacker the ability to execute arbitrary commands on the underlying vCenter host.
CVE-2021-21986 is an authentication mechanism issue in several vCenter Server Plug-ins, which is assigned a CVSSv3 score of 6.5, making it moderate severity. The affected vCenter Server Plug-ins include:
- vSAN Health Check
- Site Recovery
- vSphere Lifecycle Manager
- VMware Cloud Director Availability
CVE-2021-21986 can also be exploited via port 443 and allow an attacker to perform plugin functions without authentication.
Both of these vulnerabilities impact vCenter Server versions 6.5, 6.7, and 7.0.
Proof of concept
At the time this blog post was published, no proof-of-concept code was available for either CVE-2021-21985 and CVE-2021-21986.
On June 3, a researcher named Jang published a working proof-of-concept for CVE-2021-21985.
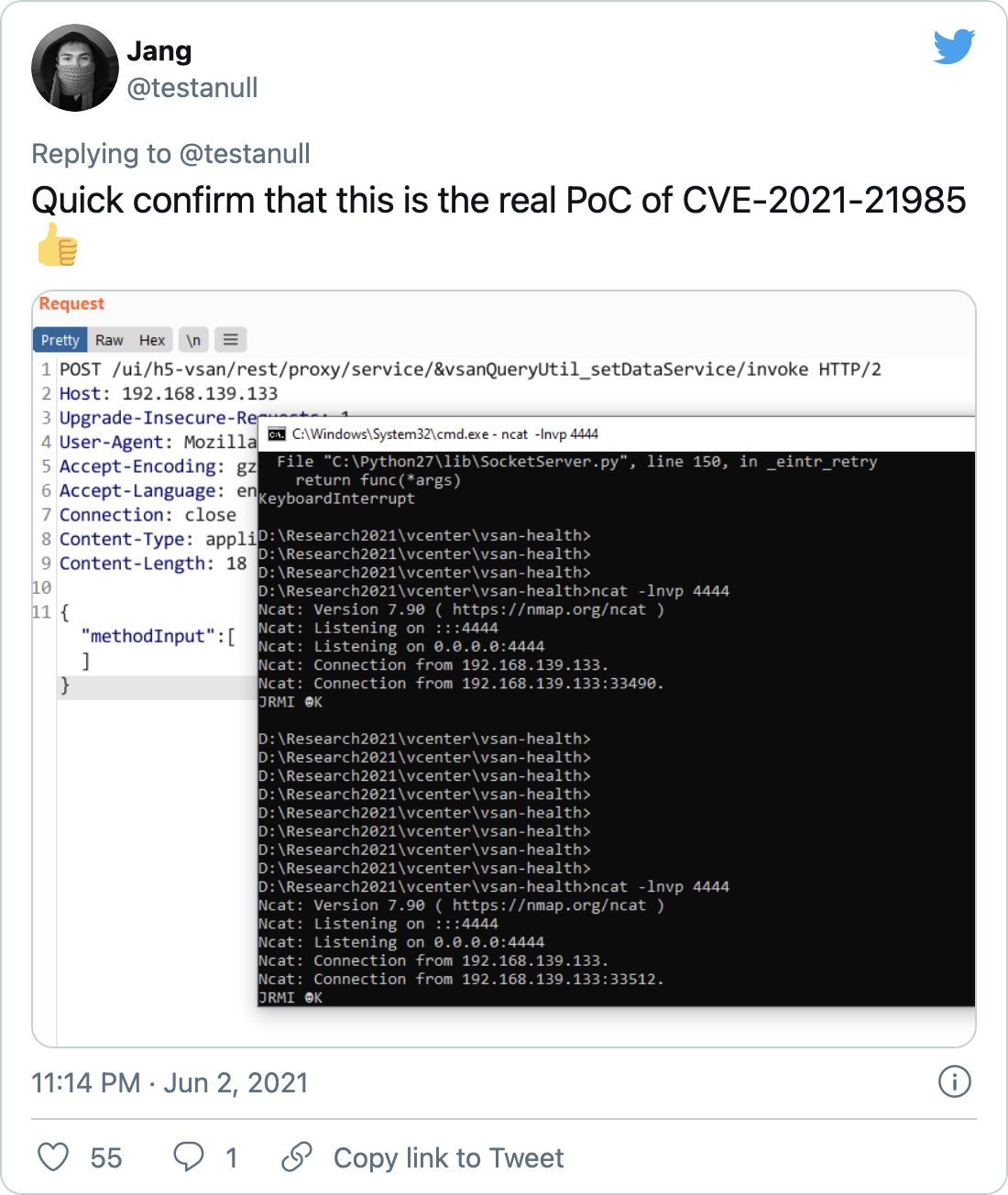
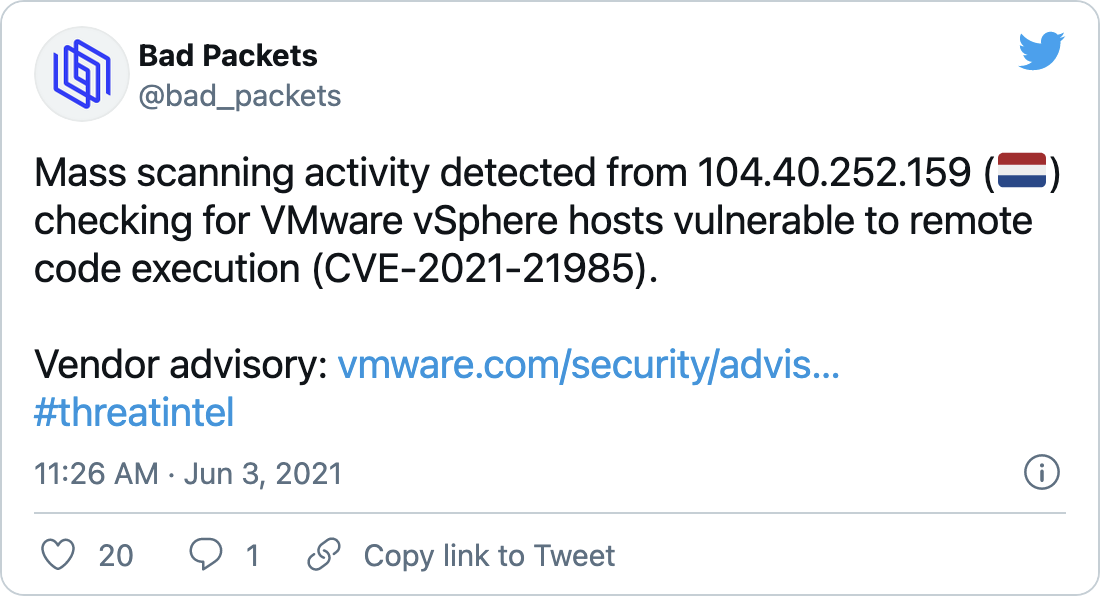
Following that, Troy Mursch, chief research officer at Bad Packets reported mass scanning activity for vulnerable vCenter servers.
Solution
VMware has released patches to address both of these vulnerabilities and recommends organizations urgently mitigate them, particularly CVE-2021-21985.
| Product Version | Fixed Version |
|---|---|
| vCenter Server 7.0 | 7.0 U2b |
| vCenter Server 6.7 | 6.7 U3n |
| vCenter Server 6.5 | 6.5 U3p |
VMware published a FAQ page with additional details about patches and mitigations. If patching is not possible, VMware has published a workaround page with guidance on how to disable the vSAN plugin, along with several others. This is a temporary measure until patches can be applied. For more detailed guidance, please refer to VMware’s blog post.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released. Tenable has also released audit checks to verify the workaround is in place.
Get more information
- VMware Advisory VMSA-2021-0010
- VMware Blog Post
- Tenable Blog for CVE-2021-21972, CVE-2021-21973, CVE-2021-21974
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


