Customizing a Security Policy with New SecurityCenter Assurance Report Cards

Note: Tenable SecurityCenter is now Tenable.sc. To learn more about this application and its latest capabilities, visit the Tenable.sc web page.
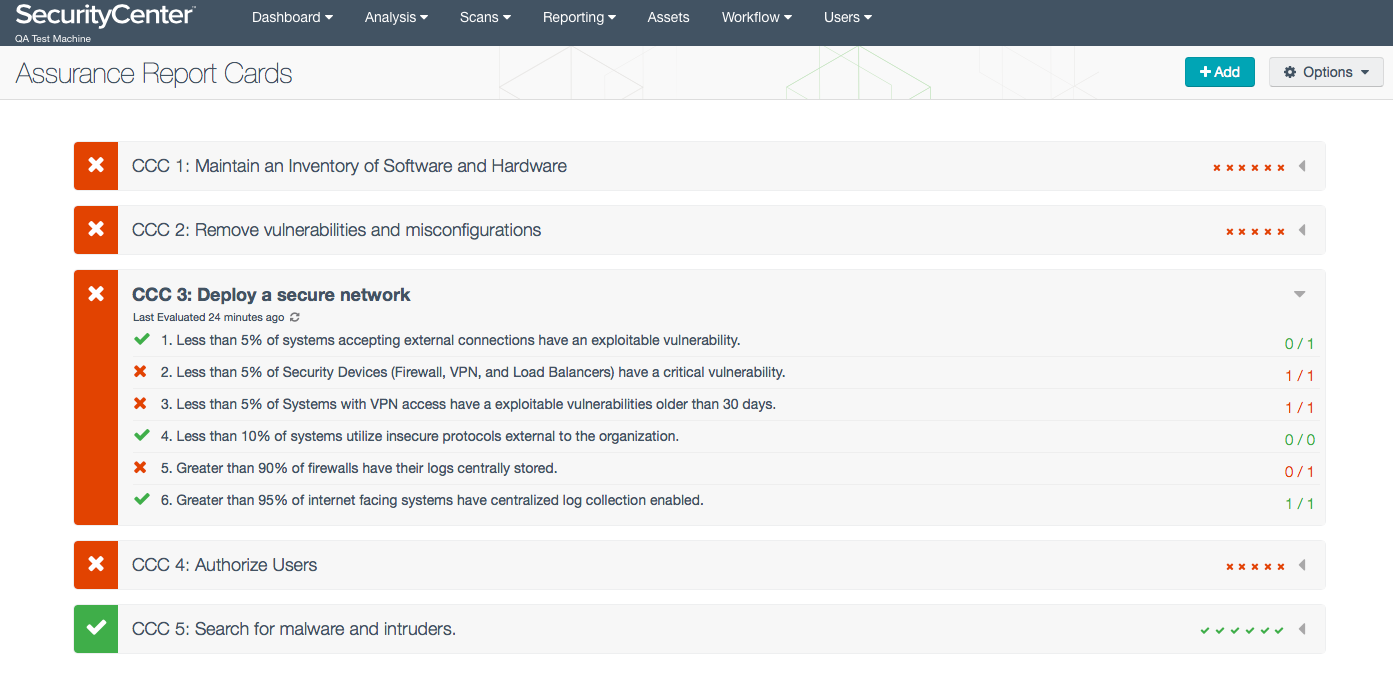
Tenable recently defined 5 Critical Cyber Controls, common themes found in most major security standards and frameworks—such as NIST, PCI, and the SANS/Council on CyberSecurity Critical Security Controls —to help infosec professionals formulate a resilient security policy. Shortly after that, our developers created Assurance Report Cards™ (ARCs) for SecurityCenter Continuous View™ (SecurityCenter CV™). ARCs bridge the communication gap between security professionals and business executives by visually communicating the status of the most critical security issues in a familiar report card format. ARCs that represent Tenable’s 5 critical cyber controls are available with SecurityCenter CV to provide continuous assurance that your security program is effective:
- CCC1: Maintain an inventory of software and hardware
- CCC2: Remove vulnerabilities and misconfigurations
- CCC3: Deploy a secure network
- CCC4: Authorize users
- CCC5: Search for malware and intruders
Measuring and communicating security program effectiveness
Each ARC is a customer defined business objective expressed in terms of multiple policy statements
Each ARC is a customer defined business objective expressed in terms of multiple policy statements. These policy statements are continuously evaluated by SecurityCenter, using Nessus® vulnerability scanners, Passive Vulnerability Scanner™ (PVS™) network sensors, and Log Correlation Engine™ (LCE™) logs. For example, when you drill down into CCC3 in SecurityCenter, you view the policies that are measured and monitored to determine the effectiveness of your network security:
ARCs and their underlying policy statements are all customizable so you can create a security program and reporting mechanism that is relevant to your organization’s unique needs.
New ARCs
ARCs have become so popular with our customers that our developers are regularly adding new ARCs to the SecurityCenter Feed. Recent additions include these reports:
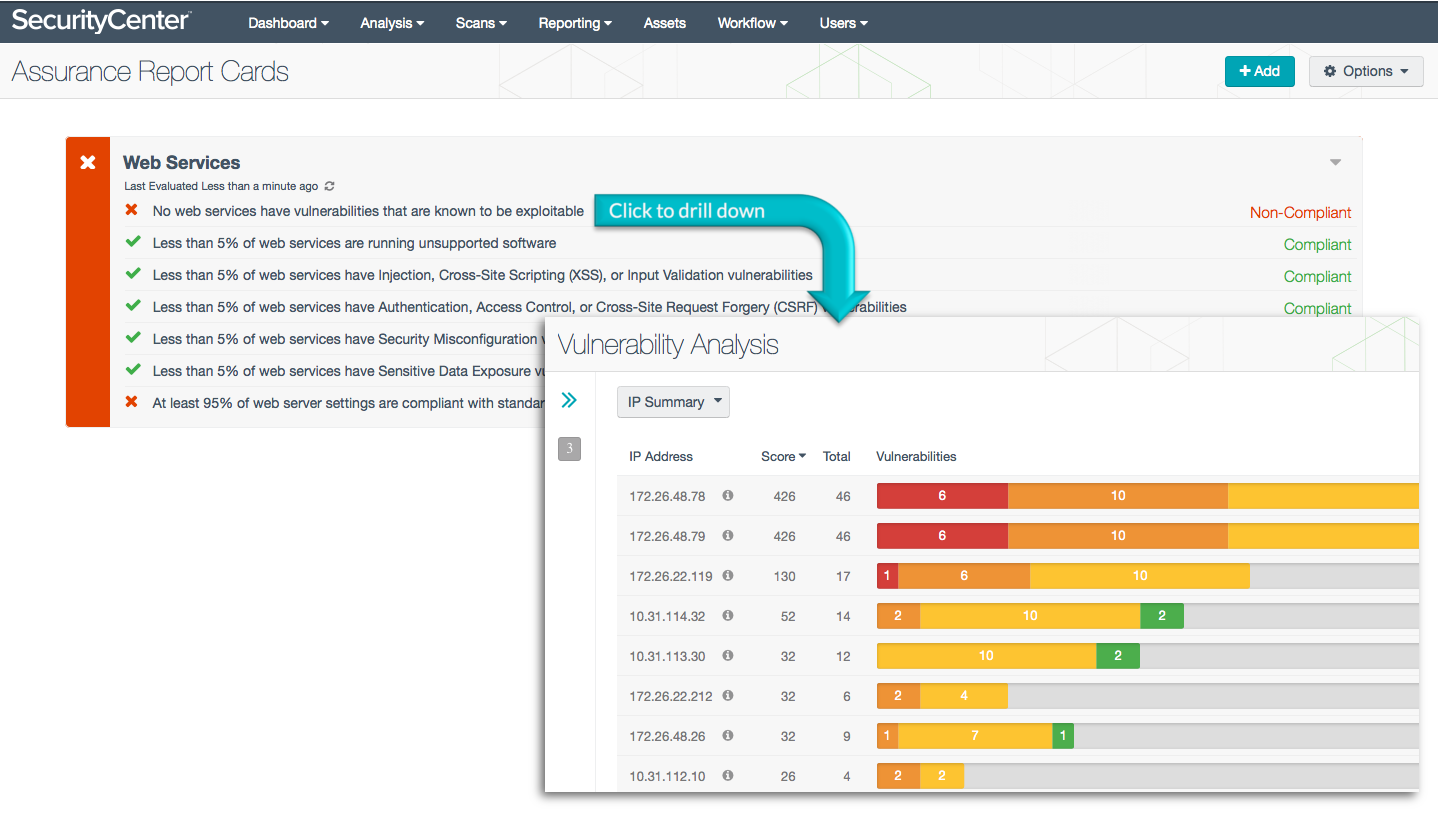
Web Services
The Web Services ARC references the Open Web Application Security Project (OWASP) Top Ten list of critical web application security flaws that can leave your organization vulnerable to network intrusions and data breaches. For example, the ARC looks for exploitable vulnerabilities, unsupported software, and security misconfigurations on systems running web services. This ARC uses Nessus and PVS information to monitor compliance with OWASP recommendations for secure web services.
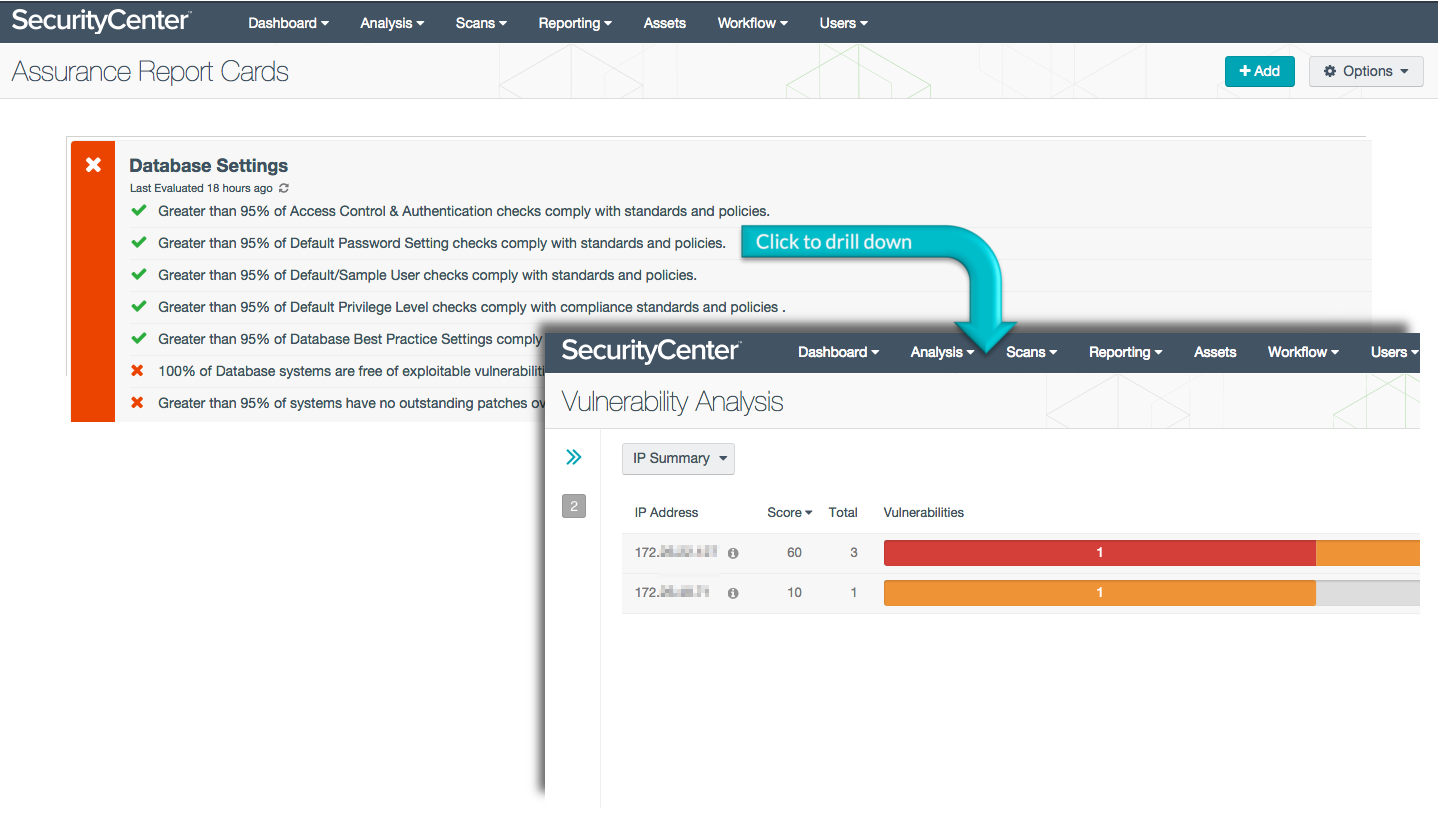
Database Settings
In an era of daily data breaches, database protection is crucial. The Database Settings ARC identifies exploitable weaknesses and compliance issues including the percentage of systems complying with patching requirements, the existence of default users and passwords, and default privilege levels left in database environments.
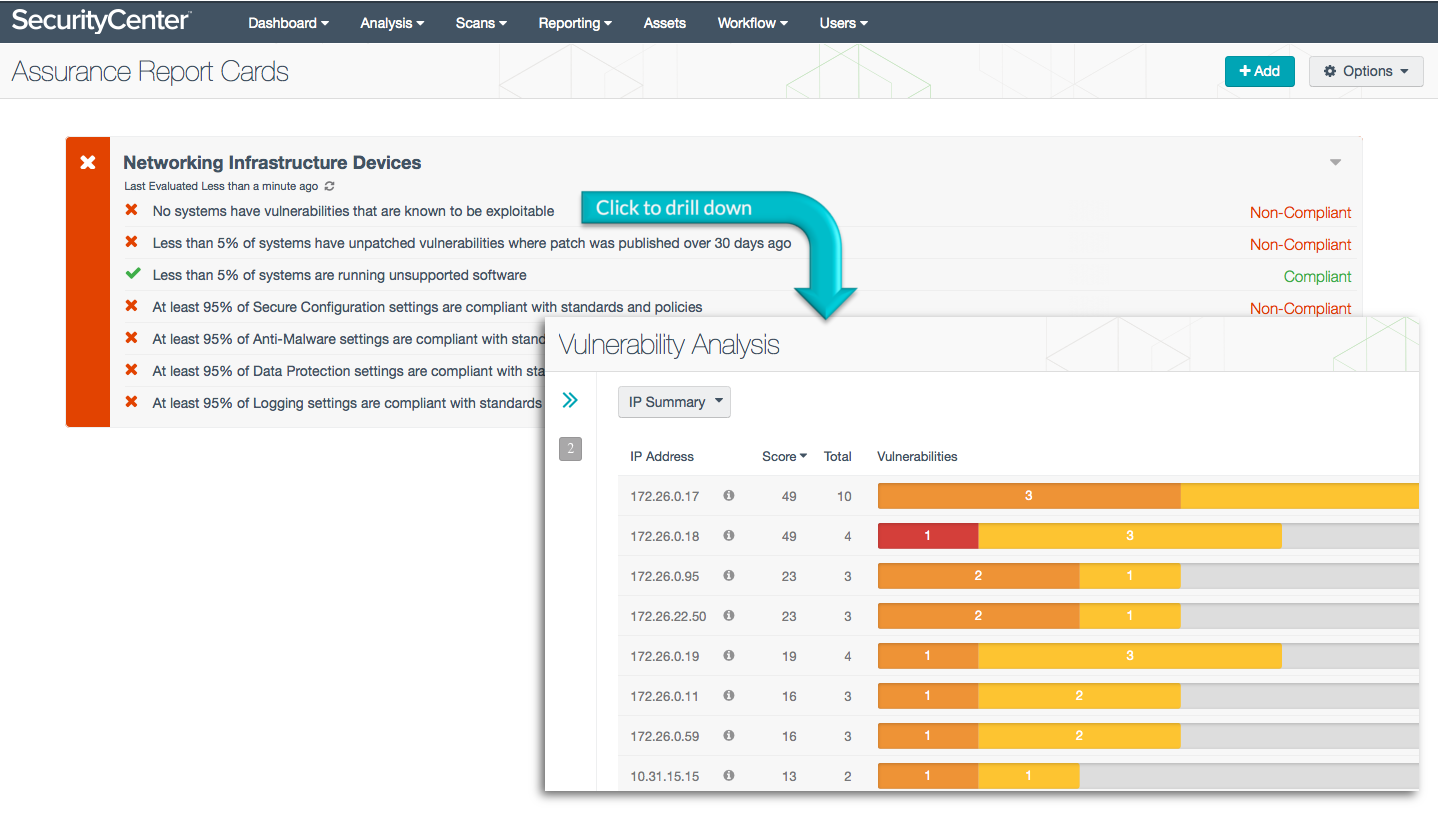
Networking Infrastructure Devices
This ARC monitors the health of network infrastructure devices, and compliance with such policies as anti-malware and data protection. The heart of the ARC is built around standards from NIST 800-53, the PCI DSS, the SANS/Council on CyberSecurity Critical Security Controls, and DoD Instruction 8500.2, measuring for 95% compliance with key policies and requirements. The Networking Infrastructure Devices ARC uses data collected by Nessus and PVS.
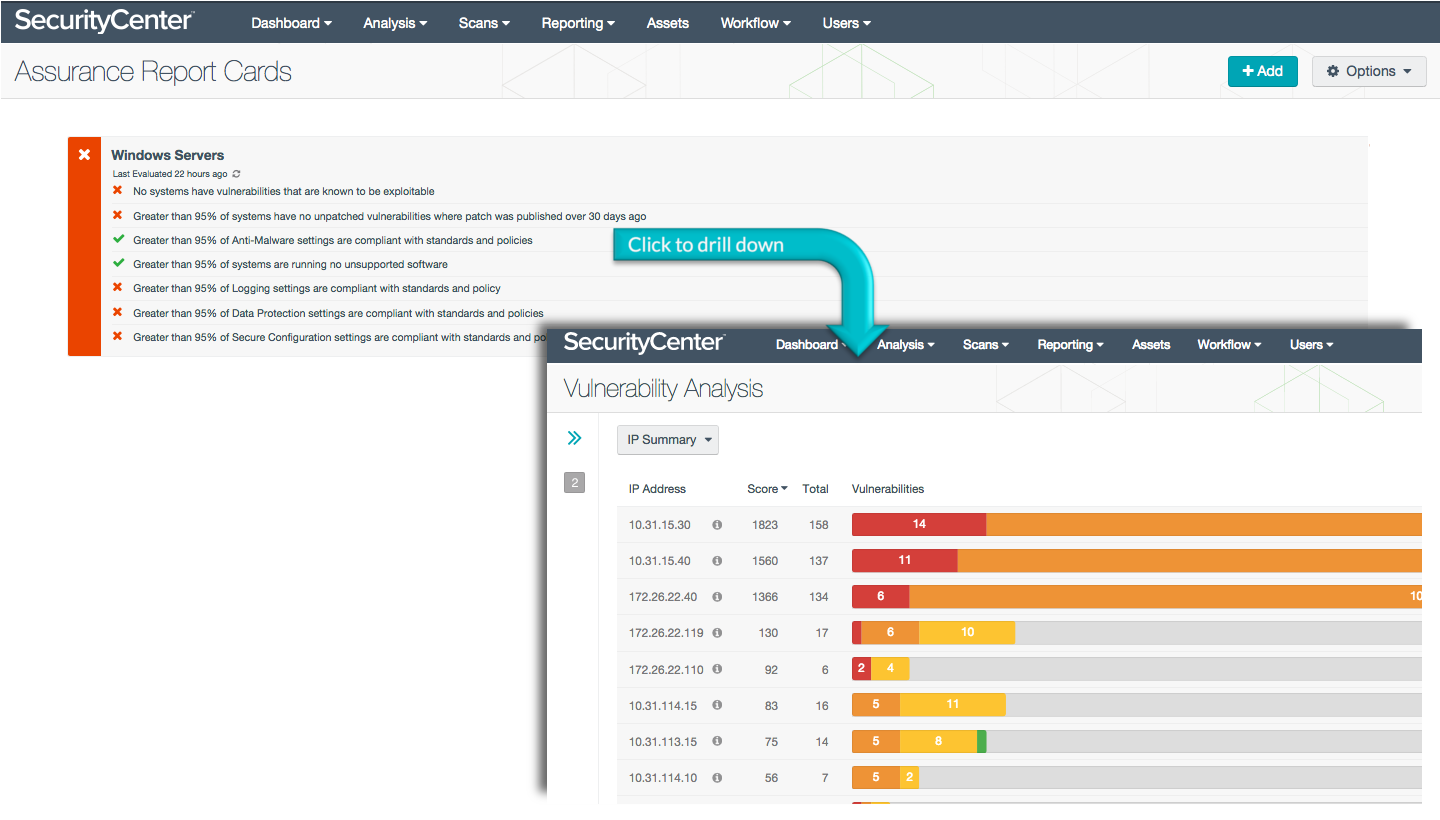
Windows Server
A Windows Server that is exposed to exploitable vulnerabilities and misconfigurations is one of the biggest threats to your security program, opening a path for malicious attacks against the entire organization. This ARC uses NIST 800-53, DoD Instructions 8500.2, and the PCI DSS to evaluate compliance with data protection and anti-malware settings, patch management timeliness, and logging parameters. The Windows Server ARC uses data collected by Nessus and PVS to report results.
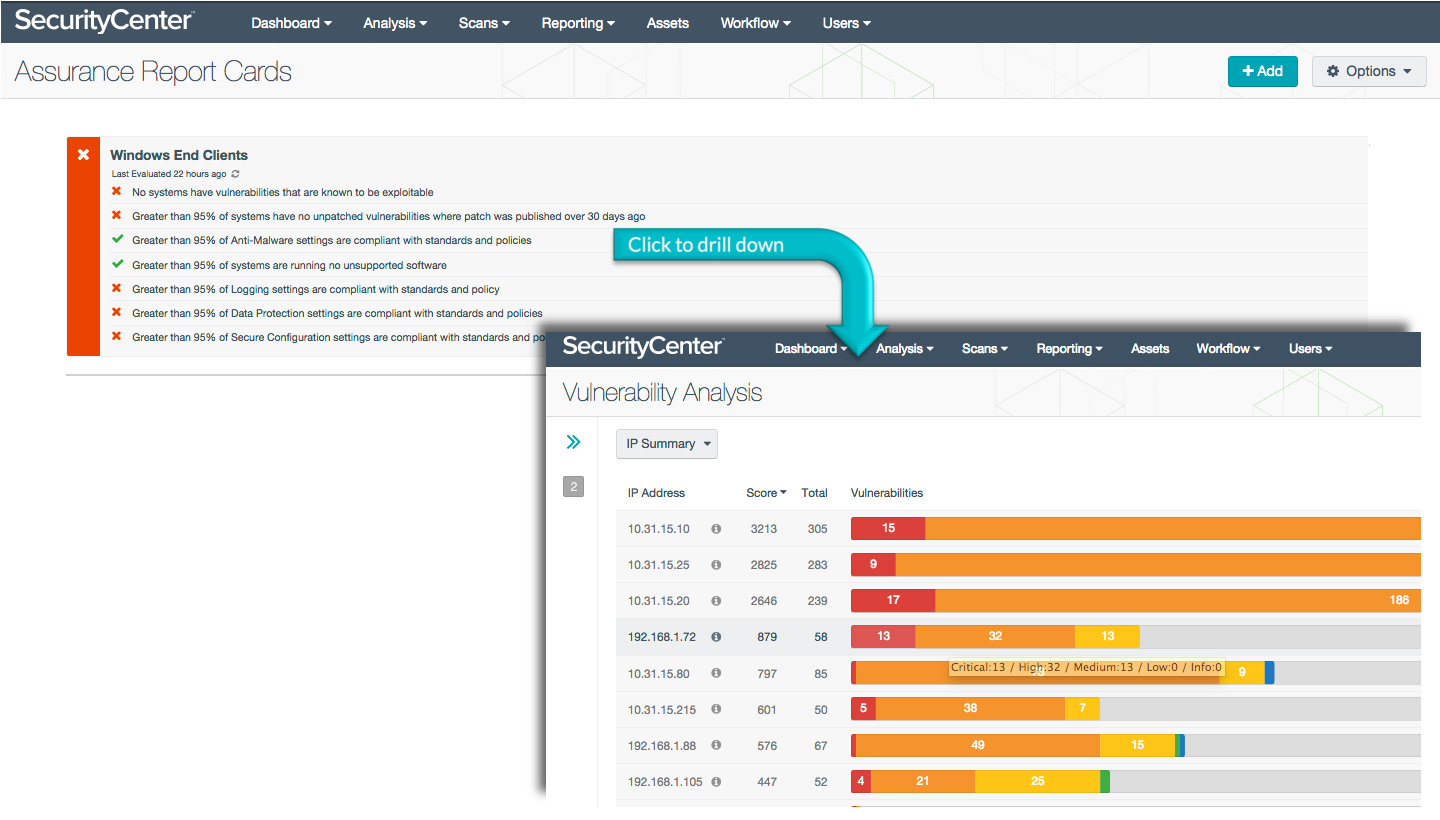
Windows End Clients
This ARC complements the Windows Server ARC by examining just the Windows end points for vulnerabilities and misconfigurations. Again referencing NIST, DoD, and PCI standards and using Nessus and PVS data for reporting, the Windows End Clients ARC measures for 95% of systems being free from unsupported software and unpatched vulnerabilities, and being compliant with site-defined anti-malware settings, data protection checks, and log settings.
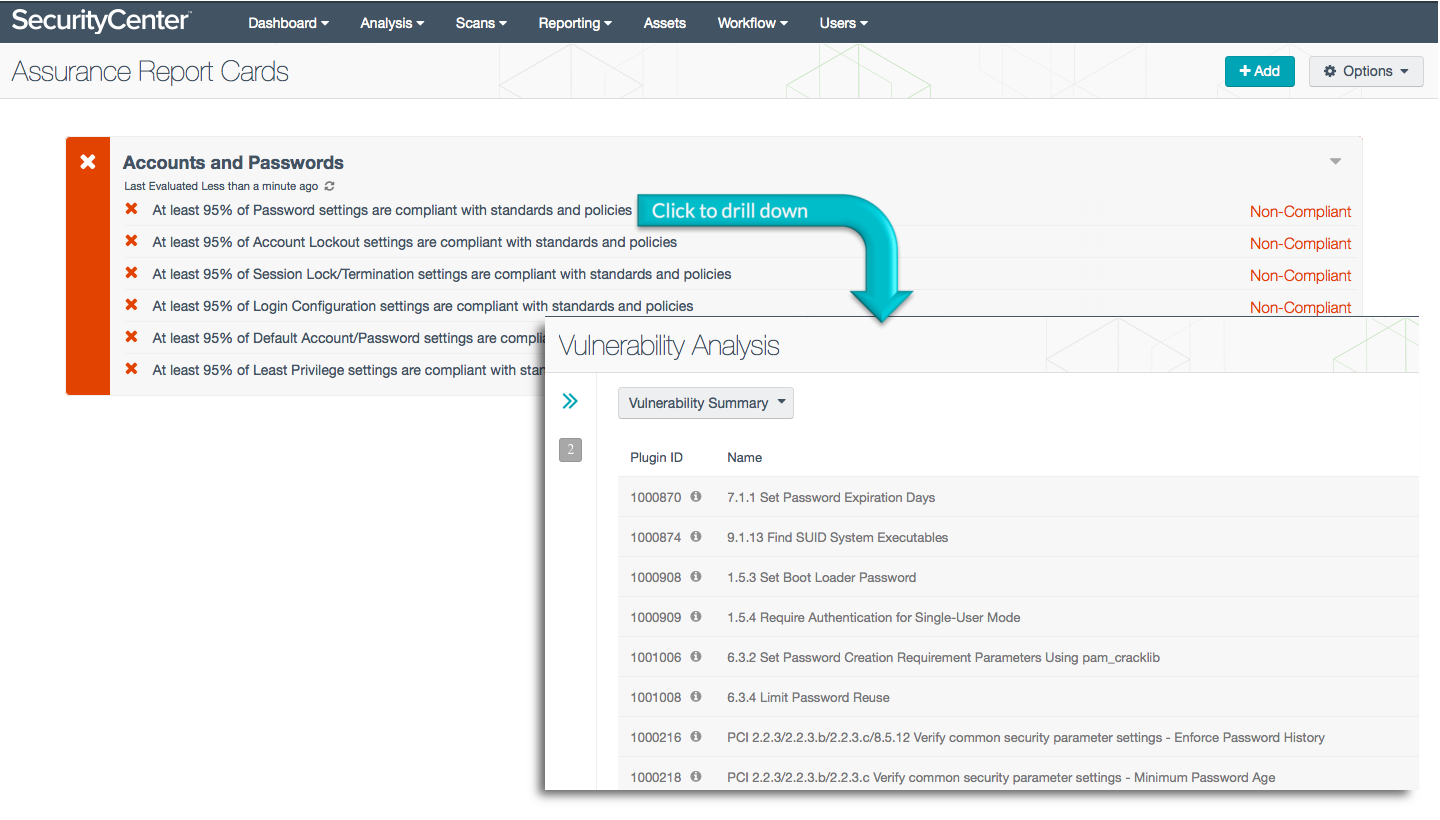
Accounts and Passwords
This ARC measures compliance against password, account lockout and least privilege policies, using standards such as NIST 800-53, PCI DSS, and DoD Instruction 8500.2 as the authoritative sources. For example, policies state that 95% of account lockout, session termination and default password settings must be compliant to receive a passing grade in this ARC. The Accounts and Passwords ARC uses data collected by Nessus to report results.
Customizing ARCs for your security program
The new ARCs can be used to amplify the original 5 critical cyber control ARCs. For example, the Accounts and Passwords ARC measures more detail in support of CCC4: Authorize Users. The Windows Server ARC expands on CCC3: Deploy a secure network. As you harden a security program, you can add to the ARCs that you use for executive reporting, and you can edit the policy statements to match site-specific compliance requirements. ARCs are flexible and not meant to be rigid standards.
Check out the new ARCs and make them your own to visualize the effectiveness of your security program for executives and board members.
More resources
You can find all the new Assurance Report Cards in the Compliance category of the SecurityCenter Feed.
To learn more about ARCs, consult these resources:
- A listing of all available ARCs on the Assurance Report Cards page
- The Tenable whitepaper on SecurityCenter Assurance Report Cards: A How-to Guide
- Security Policy
- SecurityCenter