by David Schwalenberg
June 18, 2015
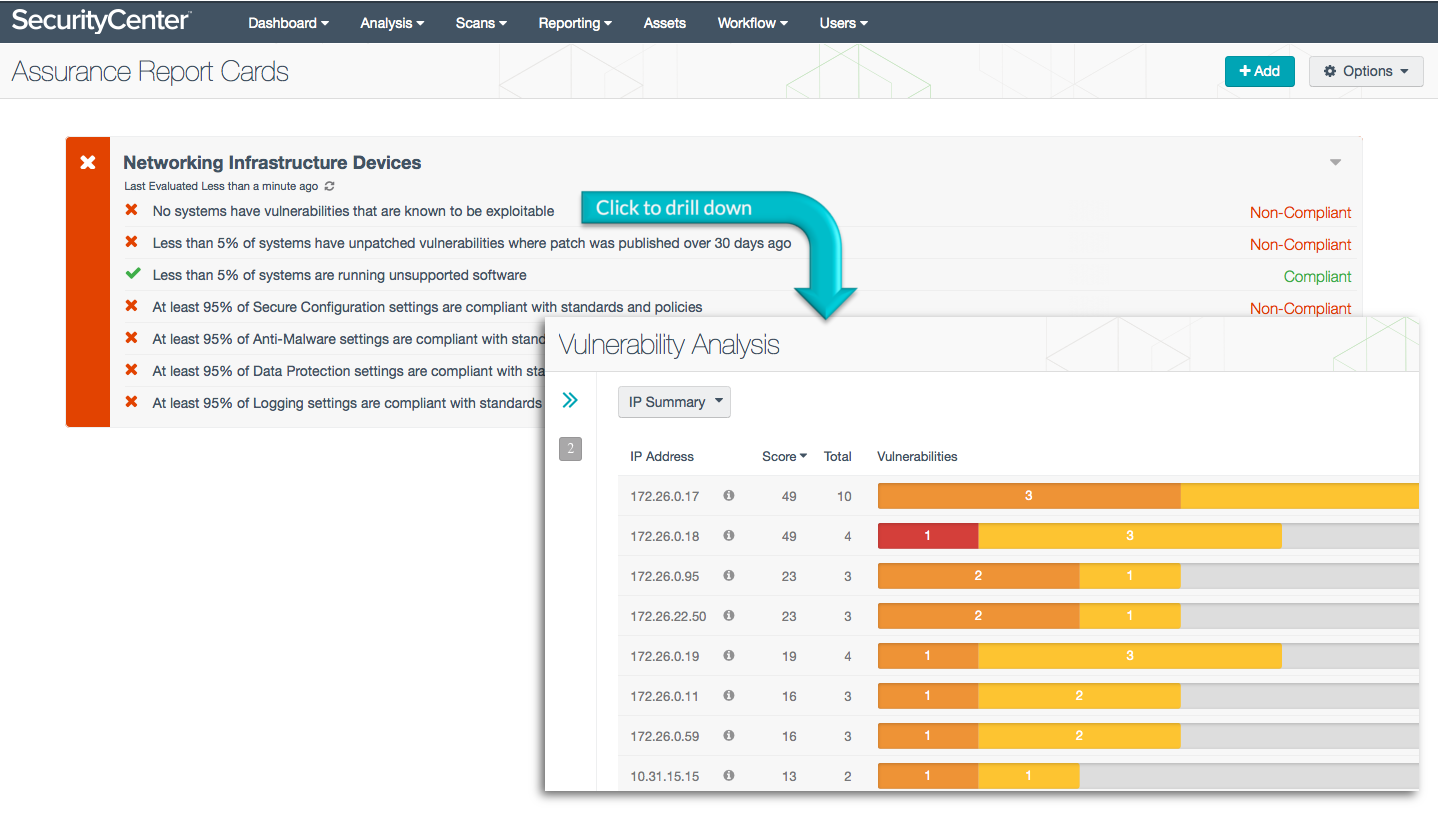
Networking infrastructure devices that are vulnerable and not compliant with organizational policy based on current accepted standards present great risks to an organization, including the threats of network intrusion and data disclosure. The Networking Infrastructure Devices Assurance Report Card (ARC) presents policy statements that measure, for infrastructure devices, percentage compliance against organizational policies such as secure configuration policy, anti-malware policy, and data protection policy. Organizational policy will be based on appropriate current accepted standards. This ARC makes use of standards such as NIST 800-53, DoD Instruction 8500.2, and the PCI Data Security Standard to highlight compliance failures on infrastructure devices, all the way from encryption and anti-virus requirements to least functionality concerns.
Additional policy statements are included to measure compliance with organizational policy for devices with exploitable and unpatched vulnerabilities and devices running unsupported software. The information in this ARC will allow the Compliance Manager to continuously monitor policy compliance for networking infrastructure devices, so that weak policies and weak policy enforcement can be identified and corrected and the network made more secure.
More details on each of the policy statements included in the ARC are given below. The Compliance Manager can click on a policy statement to bring up the analysis screen to display details on any compliance failures related to that policy statement. In the analysis screen, setting the tool to IP Summary will display the systems on which the compliance failures are present.
This ARC relies both on audit results obtained from Nessus scans of the systems on the network using appropriate audit files, and on vulnerability information collected by Nessus and PVS. The descriptions of the policy statements below include information on what details are used to find those checks relevant to the policy statement and what the percentage pass rate must be to be considered compliant. The audit files and ARC policy statement parameters are guides that can be customized as necessary to meet organizational requirements.
This ARC is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The ARC can be easily located in the Feed under the category Compliance. The ARC requirements are:
- SecurityCenter 5.0.0.1
- Compliance data
- Nessus 6.3.6
- PVS 4.2.1
Tenable's SecurityCenter Continuous View (SecurityCenter CV) is the market-defining continuous network monitoring platform. SecurityCenter CV includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable's Passive Vulnerability Scanner (PVS), as well as log correlation with Tenable's Log Correlation Engine (LCE). Using SecurityCenter CV, an organization will obtain the most comprehensive and integrated view of its network, in order to best measure compliance against complex standards.
ARC Policy Statements:
No systems have vulnerabilities that are known to be exploitable - This policy statement displays Compliant in green if no networking infrastructure devices have vulnerabilities that are known to be exploitable. To secure the network and meet compliance requirements, all known exploitable vulnerabilities must be patched as soon as possible.
Less than 5% of systems have unpatched vulnerabilities where patch was published over 30 days ago - This policy statement displays Compliant in green if less than 5% of networking infrastructure devices have unpatched vulnerabilities where the patch was published over 30 days ago. To secure the network and meet compliance requirements, patches must be applied in a timely manner.
Less than 5% of systems are running unsupported software - This policy statement displays Compliant in green if less than 5% of networking infrastructure devices are running unsupported software. To secure the network and meet compliance requirements, versions of software that are no longer supported should be updated as soon as possible.
At least 95% of Secure Configuration settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Secure Configuration settings have passed. Secure Configuration settings may include requirements to disable unnecessary ports and other functionality, among other things. Compliance is measured against those policy checks that reference one or more of the following standards:
- NIST 800-53 control CM-6 (CONFIGURATION SETTINGS)
- NIST 800-53 control CM-7 (LEAST FUNCTIONALITY)
- SANS/Council on CyberSecurity Critical Security Control 3 (Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers)
- SANS/Council on CyberSecurity Critical Security Control 10 (Secure Configurations for Network Devices such as Firewalls, Routers, and Switches)
- SANS/Council on CyberSecurity Critical Security Control 11 (Limitation and Control of Network Ports, Protocols, and Services)
- DoD Instruction 8500.2 control ECSC (Security Configuration Compliance)
- PCI DSS requirement 2.2.2 (Enable only necessary services, protocols, daemons, etc., as required for the function of the system)
- PCI DSS requirement 2.2.3 (Implement additional security features for any required services, protocols, or daemons that are considered to be insecure)
- PCI DSS requirement 2.2.4 (Configure system security parameters to prevent misuse)
- PCI DSS requirement 2.2.5 (Remove all unnecessary functionality)
At least 95% of Anti-Malware settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Anti-Malware settings have passed. Anti-Malware settings may include requirements to use and regularly update anti-virus software, among other things. Compliance is measured against those policy checks that reference one or more of the following standards:
- NIST 800-53 control SI-3 (MALICIOUS CODE PROTECTION)
- SANS/Council on CyberSecurity Critical Security Control 5 (Malware Defenses)
- DoD Instruction 8500.2 control ECVP-1 (Virus Protection)
- PCI DSS requirement 5 (Protect all systems against malware and regularly update anti-virus software or programs)
At least 95% of Data Protection settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Data Protection settings have passed. Data Protection settings may include encryption and access control requirements, among other things. Compliance is measured against those policy checks that reference one or more of the following standards:
- NIST 800-53 control SC-8 (TRANSMISSION CONFIDENTIALITY AND INTEGRITY)
- SANS/Council on CyberSecurity Critical Security Control 15 (Controlled Access Based on the Need to Know)
- SANS/Council on CyberSecurity Critical Security Control 17 (Data Protection)
- DoD Instruction 8500.2 control ECCD (Changes to Data)
- DoD Instruction 8500.2 control ECCR (Encryption for Confidentiality (Data at Rest))
- DoD Instruction 8500.2 control ECCT (Encryption for Confidentiality (Data in Transit))
- DoD Instruction 8500.2 control ECNK (Encryption for Need-To-Know)
- PCI DSS requirement 3 (Protect stored cardholder data)
- PCI DSS requirement 4 (Encrypt transmission of cardholder data across open, public networks)
- PCI DSS requirement 7 (Restrict access to cardholder data by business need to know)
At least 95% of Logging settings are compliant with standards and policies - This policy statement displays Compliant in green if at least 95% of the compliance checks on Logging settings have passed. Logging settings may include log retention and Network Time Protocol (NTP) requirements, among other things.