by Carole Fennelly
November 1, 2022
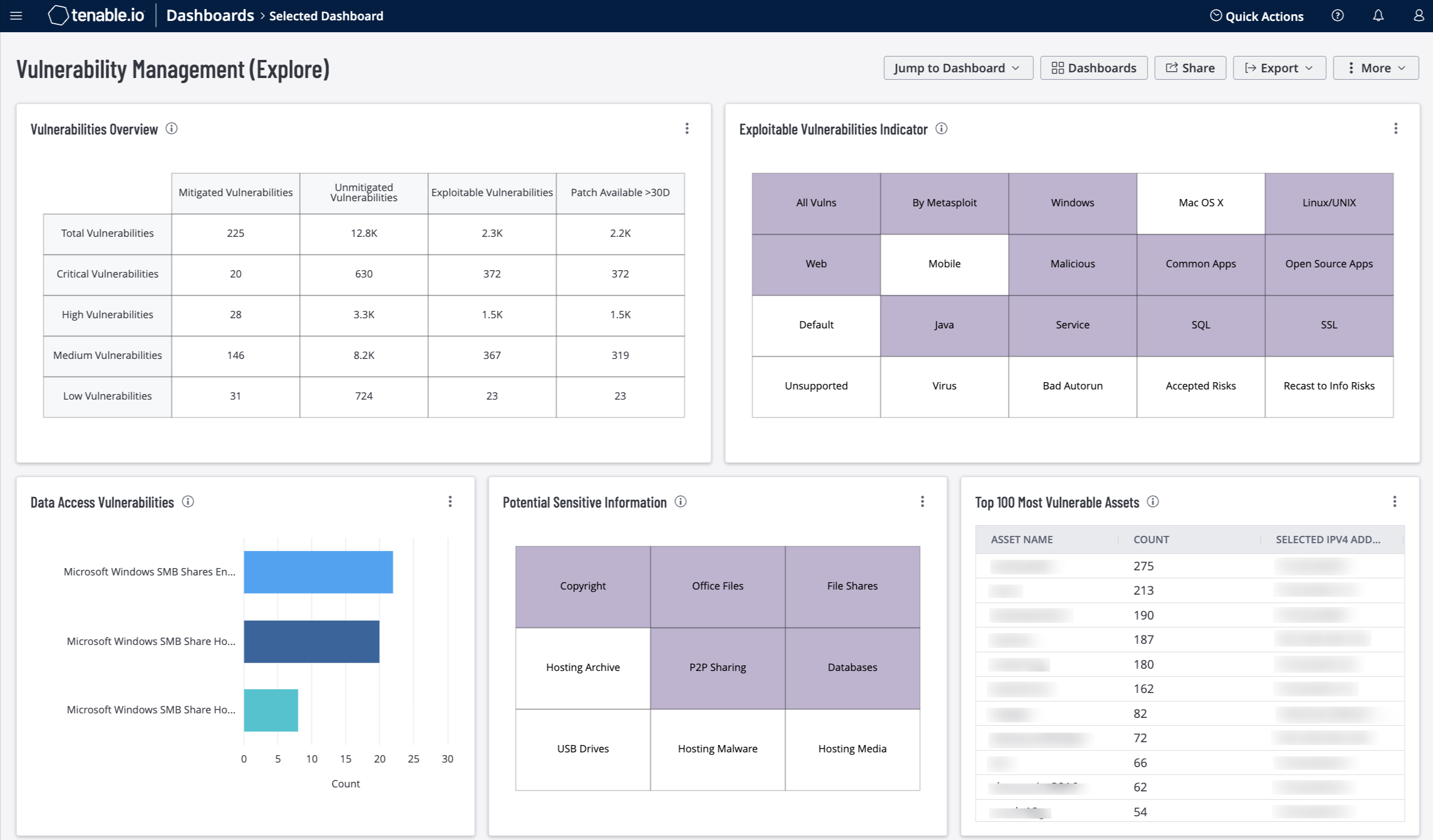
Vulnerabilities that affect the confidentiality, integrity, and availability of data are discovered constantly. Tenable.io enables organizations to proactively monitor the network to discover vulnerabilities in their environment. This dashboard provides a high-level overview of an organization's vulnerability management program and helps organizations to identify vulnerabilities, prioritize remediations, and track remediation progress.
Organizations often need a big picture view of the current state of their assets. Individual scans and reports focus on specific areas of assessment and analysis. The Vulnerabilities Overview widget provides an updated overview of an organizations risk level, asset count, and overall cyber gap. The vulnerability information is grouped by different focuses and needs, enabling organizations to plan a high-level mitigation strategy and ensure cyber security team members have the appropriate data for their role
Organizations often need a big picture view of the current state of their assets. Individual scans and reports focus on specific areas of assessment and analysis. The Vulnerabilities Overview widget provides an updated overview of an organizations risk level, asset count, and overall cyber gap. The vulnerability information is grouped by different focuses and needs, enabling organizations to plan a high-level mitigation strategy and ensure cyber security team members have the appropriate data for their role.
This dashboard helps monitor for potentially sensitive data and data access vulnerabilities on the network. Security teams can provide stronger file security and integrity protections by knowing where sensitive or valuable information is stored and identifying associated vulnerabilities.
The current total number of vulnerabilities and their exploitability factor identifies current risk in relation to the total attack surface. The most vulnerable asset information enables organizations to address the most problematic assets first, and addresses the vulnerabilities that pose the greatest threat to those assets. Assets that are hosting internal or user data can be identified to ensure risk is appropriately identified and mitigated.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture. The requirements for this dashboard are: Tenable.io Vulnerability Management (Nessus, NNM).
Widgets
Vulnerabilities Overview – This widget assists in tracking vulnerability mitigations. The widget presents vulnerability summary information by severity. Each row displays vulnerabilities within each severity. The top row displays total vulnerabilities, the second row displays critical severity vulnerability information, the third row displays high severity, the fourth row is medium severity, and the last row is low severity. The Mitigated column displays the total number of mitigated vulnerabilities. The Unmitigated column displays the total number of vulnerabilities that have not yet been mitigated. The Exploitable column displays the number of unmitigated vulnerabilities that are known to be exploitable. The Patch Available >30D column displays the number of the unmitigated, exploitable vulnerabilities that have had a patch available for more than 30 days. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Top 100 Most Vulnerable Assets – This widget presents a list of the top most vulnerable assets at risk for exploitation. Information is filtered by vulnerabilities of high or critical severity that are exploitable, and is sorted by total vulnerabilities. This data on detected vulnerabilities enables analysts to prioritize remediation efforts. This widget identifies the top vulnerabilities to mitigate to reduce the organization's overall attack surface. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Potential Sensitive Information – This widget displays indicators to detect various types of potentially sensitive information. Displayed are indicators for copyright information, file shares, databases, peer to peer file sharing, USB Drives, websites hosting potentially sensitive information, and Office files. An indicator will be highlighted if the information was detected during an active scan and can be selected to display more details. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Exploitable Vulnerabilities Indicator – This widget displays warning indicators for exploitable vulnerabilities detected on the network. Displayed are vulnerabilities related to Windows, web servers, open-source applications, and vulnerabilities by keyword. Vulnerabilities that can be exploited by Metasploit are very dangerous and must be remediated as soon as possible. Exploitable vulnerabilities that have been marked as Accepted Risks or Recast to Informational are also noted. Clicking on a highlighted indicator displays the vulnerability findings details within Explore Overview for further investigation. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Data Access Vulnerabilities – This widget lists the top ten vulnerabilities related to data access by count. Plugin IDs are used to filter for vulnerabilities related to file access and sharing, copyrighted files, and data storage. Security analysts can leverage the information provided to ensure compliance with data access and storage policies. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).