by Josef Weiss
September 14, 2023
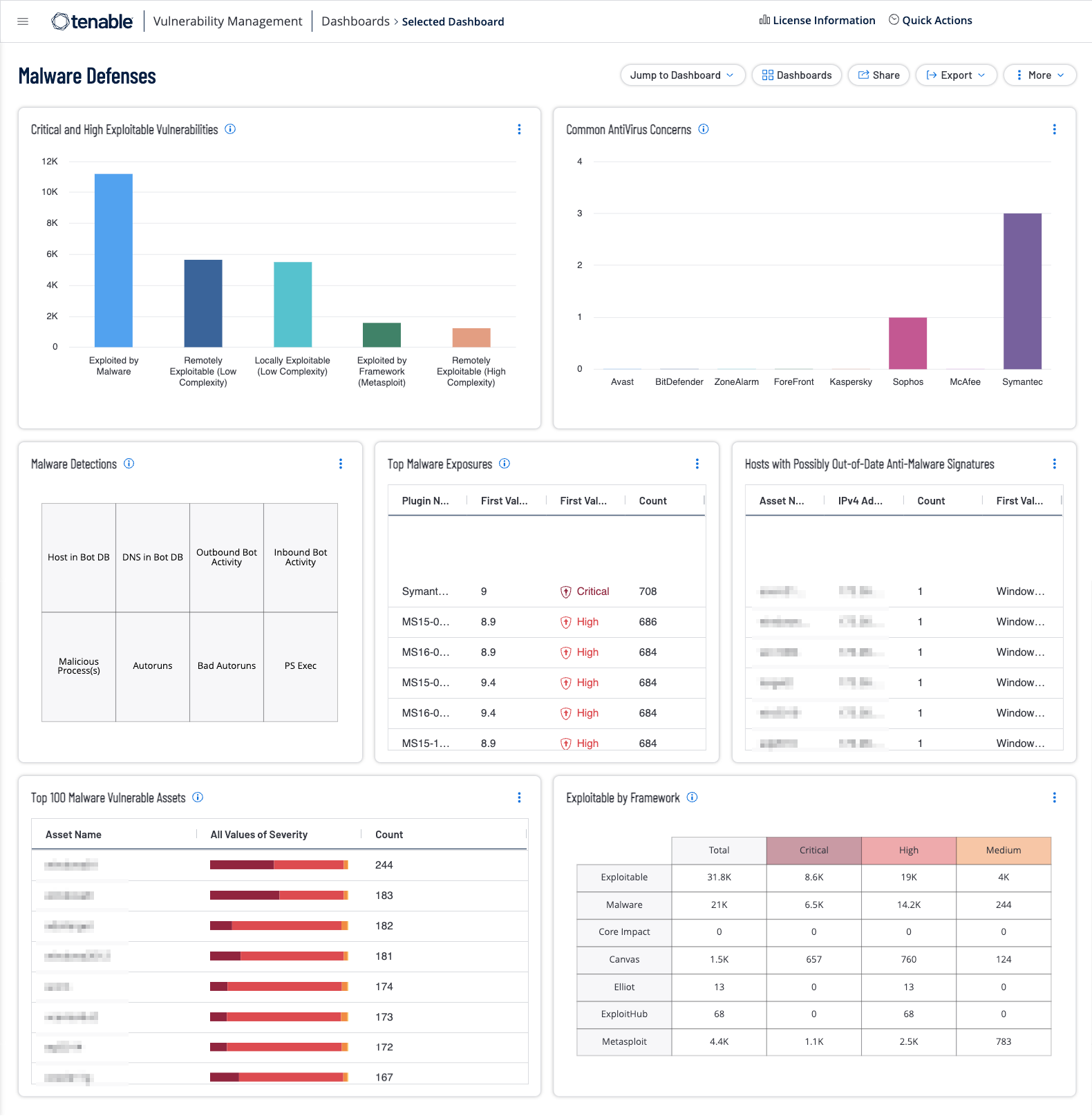
Malware remains a constant and ever-growing threat among organizations. Even with anti-virus systems in place, advanced malware can still bypass these solutions and propagate throughout a network. Systems can become infected from users accessing a compromised website, which can install malware and other malicious software. Malware variants can allow for long-term persistence, provide a backdoor to internal systems, or exfiltrate confidential data on demand. The Malware Defenses dashboard helps organizations monitor the enterprise for potential malware infections, botnet interactions, malicious processes, and also ensure that the anti-virus software is functioning as intended.
Anti-malware software includes both signature and non-signature methods of detection, and is frequently updated to leverage new advances in technology, such as machine learning and artificial intelligence. New malware is created and released almost daily. Keeping anti-malware software up-to-date involves applying patches when they become available to fix bugs or vulnerabilities and to update to the latest stable version to leverage the latest features. Any signature based anti-malware rules must be updated with the latest signatures from the vendor to ensure the latest known malware is detected.
One critical part of keeping the network secure is enabling a continuous monitoring strategy and monitoring of all possible network endpoints. Information gathered from Tenable products provides organizations with a complete picture of malicious activity, malware infections, and compromised hosts. This dashboard provides a detailed view of potential malware, suspicious processes, and malicious activity, enabling security analysts to easily identify malware activity on hosts. Event data provides valuable information from devices and services on suspicious files, unauthorized logins, malicious websites, requests, and more. Systems are scanned for malicious backdoors, botnet activity, potential malware, and unknown processes. Indicators provide information on systems communicating with botnets or other malicious hosts.
Information provided within this dashboard enables organizations to detect, respond, and recover more effectively, thus allowing organizations to stay on top of the challenging threat landscape.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable Vulnerability Management discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture.
Widgets
Critical and High Exploitable Vulnerabilities - This widget focuses on the most severe current threats, critical and high exploitable vulnerabilities to help prioritize remediation.
Common Antivirus Concerns - This widget focuses on the most common antivirus vendor’s vulnerabilities to help prioritize remediation.
Malware Detections - This widget displays warning indicators for potential malware-related events and vulnerabilities detected on the network, such as, botnet interactions, malicious processes, and bad Windows autoruns.
Top Malware Exposures - This widget displays the most prevalent, active malware exposures.
Hosts with Possibly Out-of-Date Anti-Malware Signatures - This widget utilizes several plugin IDs to determine if anti-malware/antivirus signatures are up-to-date.
Top 100 Malware Vulnerable Assets - This widget provides a list of the top 100 assets with vulnerabilities that are known to be exploitable by malware.
Exploitable by Framework - This widget provides a summary of exploitable vulnerabilities by framework.