by Josef Weiss
October 18, 2023
Email and web browsers are the most common applications used to communicate online. These applications are extensively used to access a wide variety of systems from commercial sites to enterprise systems. Email and web browser applications represent two of the most essential tools for communication and information access. Vulnerabilities are a common concern, and these applications are prime targets for cyber attacks.
The Center for Internet Security (CIS) states: “Web browsers and email clients are very common points of entry and attack because of their technical complexity, flexibility, and their direct interaction with users and with other systems and websites. Content can be crafted to entice or spoof users into taking actions that greatly increase risk and allow introduction of malicious code, loss of valuable data, and other attacks. Since these applications are the main means that users interact with untrusted environments, these are potential targets for both code exploitation and social engineering.”
Clicking on malware designed to deceive users, either inside of an email or on a malicious website is certainly a very common and successful method of attack. However, this method is best cured with a solid cybersecurity awareness program. Security training is an invaluable tool in educating users on best practices, in particular on how to identify phishing emails, avoiding browser plugins, extensions, and keeping applications up to date and reducing the likelihood of this type of attack being successful. Another very common attack path is via unpatched applications.
Email clients and Web browsers that are unpatched may contain vulnerabilities that allow a compromised user’s device to be vulnerable to a number of attacks. In regard to web browsers, malicious or poorly coded extensions may allow attackers to gain unauthorized access to sensitive information, or inject malicious code. To mitigate these vulnerabilities, users and organizations should practice safe email and web browsing habits, keep software up-to-date, and utilize antivirus and anti-phishing software.
Tenable can assist organizations reduce these threats by reducing the attack surface and the opportunities for attackers to manipulate human behavior through their interaction with web browsers and email systems.
This dashboard uses a combination of cpe filters and plugin names to display the email and browser threats and provides indicators for common browser vulnerabilities. The content enables organizations to understand the full scope of the current attack surface and refine their security strategy accordingly. Tenable products allow security operations teams to use Tenable One to analyze endpoint browser and email client configurations. Using a variety of active and passive plugins paired with Tenable Vulnerability Management the organization can verify established configuration policies are followed.
Tenable provides several solutions for organizations to better understand vulnerability management. Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization's security posture. The requirements for this dashboard are: Tenable.io Vulnerability Management (Nessus).
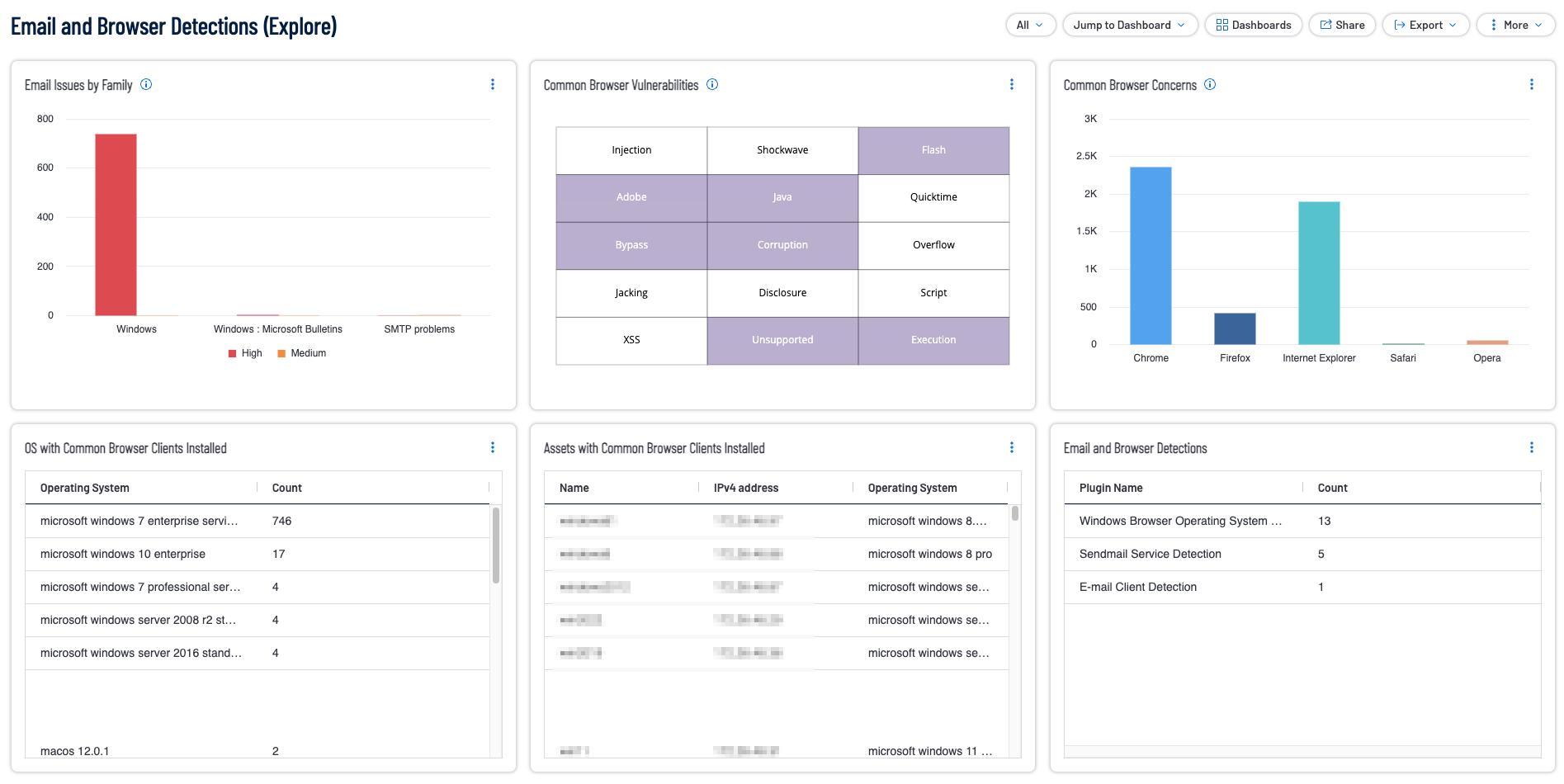
Widgets
Common Browser Concerns: This widget provides a summary of vulnerabilities relating to a common browser detected on an asset.Common browsers include Chrome, Firefox, Internet Explorer, Safari, and Opera.
Assets with Common Browser Clients Installed: This widget provides a summary of Assets that have a common browser installed. Common browsers include Chrome, Firefox, Safari, Internet Explorer, Edge, and Opera.
Common Browser Vulnerabilities: This widget provides a summary of common browser vulnerabilities. Common browsers include Chrome, Firefox, Safari, and Internet Explorer.
Email and Browser Detections: This widget provides a summary of all email and browser detection plugins.
Email Issues by Family: This widget provides a summary of medium, high, or critical vulnerabilities that are related to email.
OS with Common Browser Clients Installed: This widget provides a summary of Operating Systems (OS) detected that have a common browser installed.Common browsers include Chrome, Firefox, Safari, Internet Explorer, Edge, and Opera. Results are sorted by count for each respective detection plugin. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).