by Ryan Seguin
January 26, 2021
Massive events such as the FIFA 2022 World Cup™ present a significant attack surface and target rich environment for the criminally motivated. The State of Qatar is taking this seriously and setting cybersecurity and privacy at the top of the FIFA 2022 World Cup™ event agenda, requiring entities to adopt and implement The Qatar 2022 Cybersecurity Framework, and elevate application security in preparation for the World Cup.
The Cybersecurity Frameworks Capability Description – Application Security section (Chapter 4) focuses on reducing risk within applications, thereby decreasing the likelihood of successful exploitation. Program Managers require a detailed view of application risk and any potentially exploitable assets. Tenable.sc provides vulnerability and configuration assessment information that allows entities to mitigate identified risks and to meet standards, guidelines, and policies.
Modeled from the Cybersecurity Governance Capability within the framework, this dashboard is organized to highlight current application risk and potential exploitability. Managers need to know their current application risk, the exploitability of their applications, and compliance with security standards during development. Using the data presented, managers are given comprehensive vulnerability data, and areas in need of attention to prevent attack.
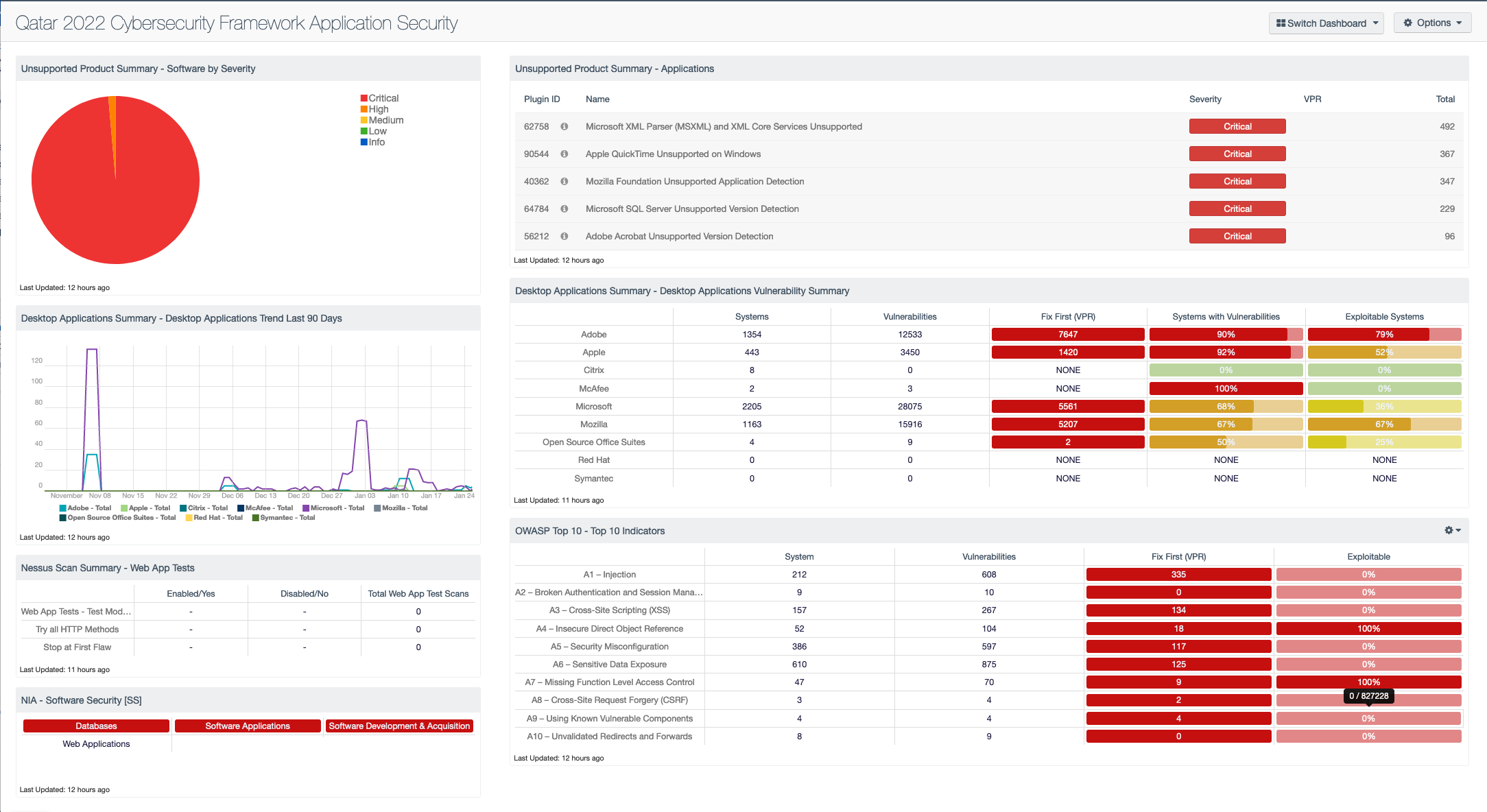
The Application Security capability outlines the process by which an entity can monitor their application risk to prevent a potential breach. The left column of this dashboard displays the current state of an entity's application state, which outlines the applications that may be unsupported or misconfigured. If applications are no longer supported, managers should prioritize removal or upgrades for applications to versions that receive active security support.
The right column assists managers by offering vulnerability counts for application families, which allows for greater insight into areas of potential exploitability and criticality determined by Tenable’s VPR. The VPR score is an output of Predictive Prioritization, which allows entities to focus on items that help drive key performance indicators, by combining research insights, threat intelligence, and vulnerability rating to reduce noise. In addition, the right column contains vulnerability data related to the OWASP Top 10: a list of the top 10 most critical web application risks. Remediating vulnerabilities related to the OWASP Top 10 greatly reduces the likelihood of external attacks, which is a key requirement of the Qatar 2022 CSF.
The Qatar 2022 CSF clearly outlines the compliance and risk management requirements to ensure a secure environment for the 2022 World Cup. The tools within this dashboard offer managers a decisive way to confidently make decisions regarding the enterprise that they direct. Armed with proper knowledge and tools, entities ensure that their organization’s needs are fully met.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessments. The dashboard requirements are:
• Tenable.sc 5.15.0
• Nessus 8.11.1
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Tenable.sc provides customers with a complete Cyber Exposure platform for completing effective cybersecurity practices.
Components
- Unsupported Product Summary - Software by Severity - This pie chart presents a graphical representation based on severity, unsupported applications and operating systems found in the environment.
- Desktop Applications Summary - Desktop Applications Trend Last 90 Days - This trend line chart depicts the detection of vulnerabilities related to specific vendors of desktop applications over the last 90 days.
- Nessus Scan Summary - Web App Tests - This component provides information on the web application test settings enabled and the number of systems where web app tests were performed.
- NIA - Software Security [SS] - This matrix provides indicators for failed audit checks which are controls of the NIA Software Security [SS] domain. The policy in this domain defines the importance of including security in the process of software development and acquisition, rather than adding it as an add-on.
- Unsupported Product Summary - Applications - The table displays unsupported applications by name and sorted by severity.
- Desktop Applications Summary - Desktop Applications Vulnerability Summary - This matrix displays information about the systems and vulnerabilities detected on the network, listed by desktop applications vendor.
- OWASP Top 10 - Top 10 Indicators - This component collects the vulnerabilities from the CGI Abuses, CGI Abuses : XSS, and Web Servers plugin families for both active and passive vulnerabilities.