by Cody Dumont
July 13, 2021
On July 6, Microsoft updated its advisory to announce the availability of out-of-band patches for a critical vulnerability in its Windows Print Spooler that researchers are calling PrintNightmare. Microsoft originally released its advisory for CVE-2021-34527 on July 1. This advisory was released in response to public reports about a proof-of-concept (PoC) exploit for CVE-2021-1675, a similar vulnerability in the Windows Print Spooler. To help clear up confusion about the vulnerability, Microsoft updated its advisory for CVE-2021-1675 to clarify that it is “similar but distinct from CVE-2021-34527.” This remote code execution (RCE) vulnerability affects all versions of Microsoft Windows.
CVE-2021-34527 is an RCE vulnerability in the Windows Print Spooler Service, which is available across desktop and server versions of Windows operating systems. The service is used to manage printers and print servers. The vulnerability exists because the service does not handle privileged file operations properly. An authenticated, remote or local attacker, could exploit this flaw in order to gain arbitrary code execution with SYSTEM privileges.
Interest is rapidly growing. Since July 1, researchers have been diligently developing PoCs for PrintNightmare. Within a week there were at least 34 public PoC exploit scripts for PrintNightmare on GitHub. These PoCs include scripts that can achieve local privilege escalation (LPE) on a targeted system, as well as remote code execution. Previous PoCs relied on the Microsoft Print System Remote Protocol (MS-RPRN) to exploit PrintNightmare.
However, on July 3, a researcher going by the nickname cube0x0, developed a PoC called SharpPrintNightmare, which uses the Microsoft Print System Asynchronous Remote Protocol (MS-PAR) instead, which confirmed that PrintNightmare could be successfully exploited against servers and desktop systems as well as domain controllers. Subsequently, Benjamin Delpy, developer of the comprehensive post-exploitation tool Mimikatz, updated the software to add support for the PrintNightmare exploit using cube0x0’s method.
Microsoft updated its advisory on July 7 to address the Point and Print aspect of this vulnerability. Specifically, they mention that while Point and Print is “not directly related to this vulnerability” its usage “weakens the local security posture” allowing for exploitation even if patches have been applied.
Microsoft Security Response Center released a blog post to announce that the cumulative patch released for CVE-2021-34527 also includes a new feature that provides users with the ability to allow non-administrative users to only install signed printer drivers which are trusted by “the installed root certificates in the system’s Trusted Root Certification Authorities”. More information on these enhanced security controls can be found in Microsoft KB5005010.
The PrintNightmare dashboard displays detailed information related to PrintNightmare vulnerabilities and can be used to identify systems and show progress towards mitigation. Additionally, Tenable released a Cyber Exposure Alert containing additional details and links to more information, including detailed information on critical registry key checks. The blog can be found here.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends. The dashboard requirements are:
- SecurityCenter 5.9.0
- Nessus 8.15.0
The Security Response Team (SRT) in Tenable Research works to dig into technical details and test proof-of-concept attacks when available, to ensure customers are fully informed of the risks. The SRT also provides breakdowns for the latest vulnerabilities on the Tenable blog. Tenable Research has released over 160,000 plugins and leads the industry on CVE coverage. Tenable's SRT team continuously works to help organizations prioritize and create remediation plans for the new threats, which often leaves very little time for reflection.
The Dashboard contains the following components:
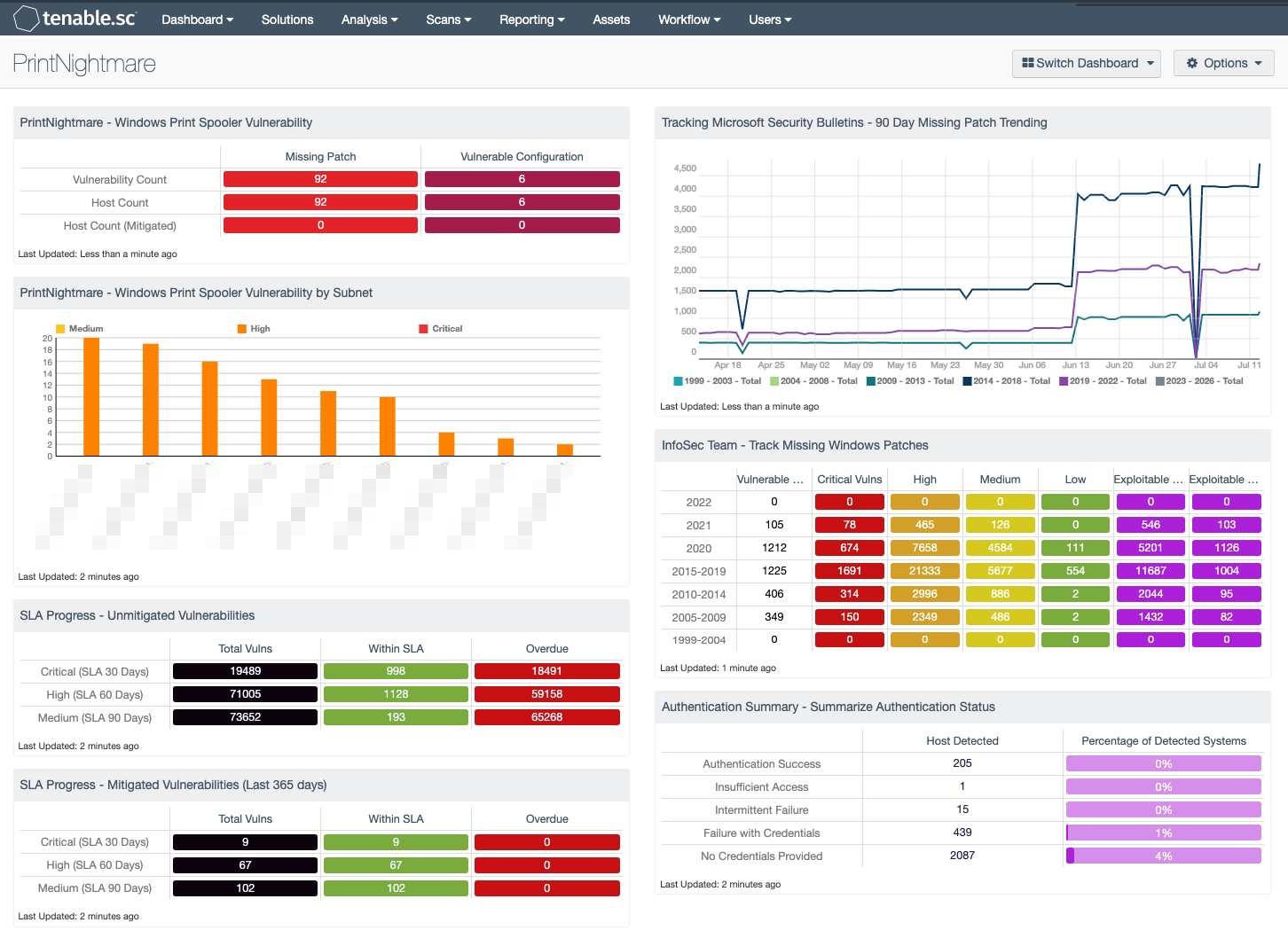
PrintNightmare - Windows Print Spooler Vulnerability: This matrix displays the missing patch and vulnerability configurations concerns for CVE-2021-34527, aka PrintNightmare. The missing patch cells display the number of vulnerabilities and hosts that are missing the PrintNightmare patch, as well as the number of hosts that have been patched (mitigated).
PrintNightmare - Windows Print Spooler Vulnerability by Subnet: This chart displays the vulnerability counts for CVE-2021-34527, aka PrintNightmare by Subnet.
Infosec Team – Track Missing Windows Patches : This matrix tracks missing Microsoft patches across the organization. InfoSec teams can quickly determine the number of missing patches and the severity, allowing them to determine where Microsoft patching efforts need to occur.
Authentication Summary - Summarize Authentication Status: This matrix provides an overall authentication summary of the systems that have been scanned. A given target should trigger at least one of these plugins. The matrix provides two columns, the “Host Detected” column provides a host count with the respective plugin(s), while the “Percentage of Detected Systems” provides a ratio of total systems scanned.
SLA Progress - Unmitigated Vulnerabilities: This matrix provides a summary of vulnerabilities based on the CVSS score and the SLA of 30, 60, 90 days. Each of the three rows are based on the CVSS severity from Medium to Critical. The three columns illustrate the count of vulnerabilities across all systems.
SLA Progress - Mitigated Vulnerabilities (Last 365 days): This matrix provides a summary of the mitigated vulnerabilities discovered over the past 365 days. The rows depict the time required to mitigate (30, 60, 90 days) and the CVSS severity level. The three columns illustrate the count of vulnerabilities across all systems.
Tracking Microsoft Security Bulletins – 90 Day Missing Patch Trending: This chart provides a 90-day trend analysis of unpatched systems with respect to Microsoft Security Bulletins. The different lines in the line chart depict the year the Security Bulletin was released. The data points are calculated every 3 days over the past 90 days.