by Carole Fennelly
April 29, 2022
In the event of a security breach, a software inventory is essential to determine what was breached, and who needs to be notified. First responders require a software inventory to perform forensic analysis and determine breach notification requirements for vendors, business partners, and regulatory bodies. Organizations that have a clear understanding of software in their environment can quickly assess a breach impact and identify affected areas. If legal proceedings are involved, an organized software inventory greatly assists in limiting data handed over to Law Enforcement and assists technical staff in depositions or testimony.
Business Continuity and Disaster Recovery plans specify requirements for restoration of critical assets and services, but these need to be identified to establish a Recovery Time Objective (the amount of time to recover a service to an acceptable level of operation) and Recovery Point Objective (the last point of known good data.) Developing and maintaining a software inventory is a critical first step in implementing an effective cyber security program.
A software inventory helps demonstrate compliance with regulatory controls and Service Level Agreements (SLAs) for software used in the environment. From the perspective of “less is more,” a software inventory also identifies unnecessary software running in the environment, which increases the attack surface without providing a business advantage.
Security operations perform scans to identify operating system and application versions, including unsupported software and unpatched systems. This information is used to establish a secure baseline and measure drift from that baseline. A software inventory is necessary to determine if the software is authorized, appropriately licensed, supported, and has the most recent security fixes applied.
Identifying the authorized software assets is an important step to ensure critical assets are protected. The larger the organization, the more difficult the inventory process becomes. Tenable.io and Tenable.sc help organizations build a software inventory. There are several software discovery plugins that run by default in the following scan templates:
- Basic and Advanced Agent Scans
- Advanced (Network) Scan
- Basic (Network) Scan
- Credentialed Patch Audit
- Internal PCI Network Scan
Maintaining a software inventory aids in cyber hygiene and minimizes unauthorized software installation. Many organizations perform an annual audit by an external third party, where they are required to enumerate authorized software that is running in the environment. Organizations that maintain a current software inventory throughout the year can produce information required by auditors and vendors with minimal effort.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Discovery and Detection .
The dashboard requirements are:
- Tenable.sc 5.19.1
- Nessus 10.0.1
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture.
Components
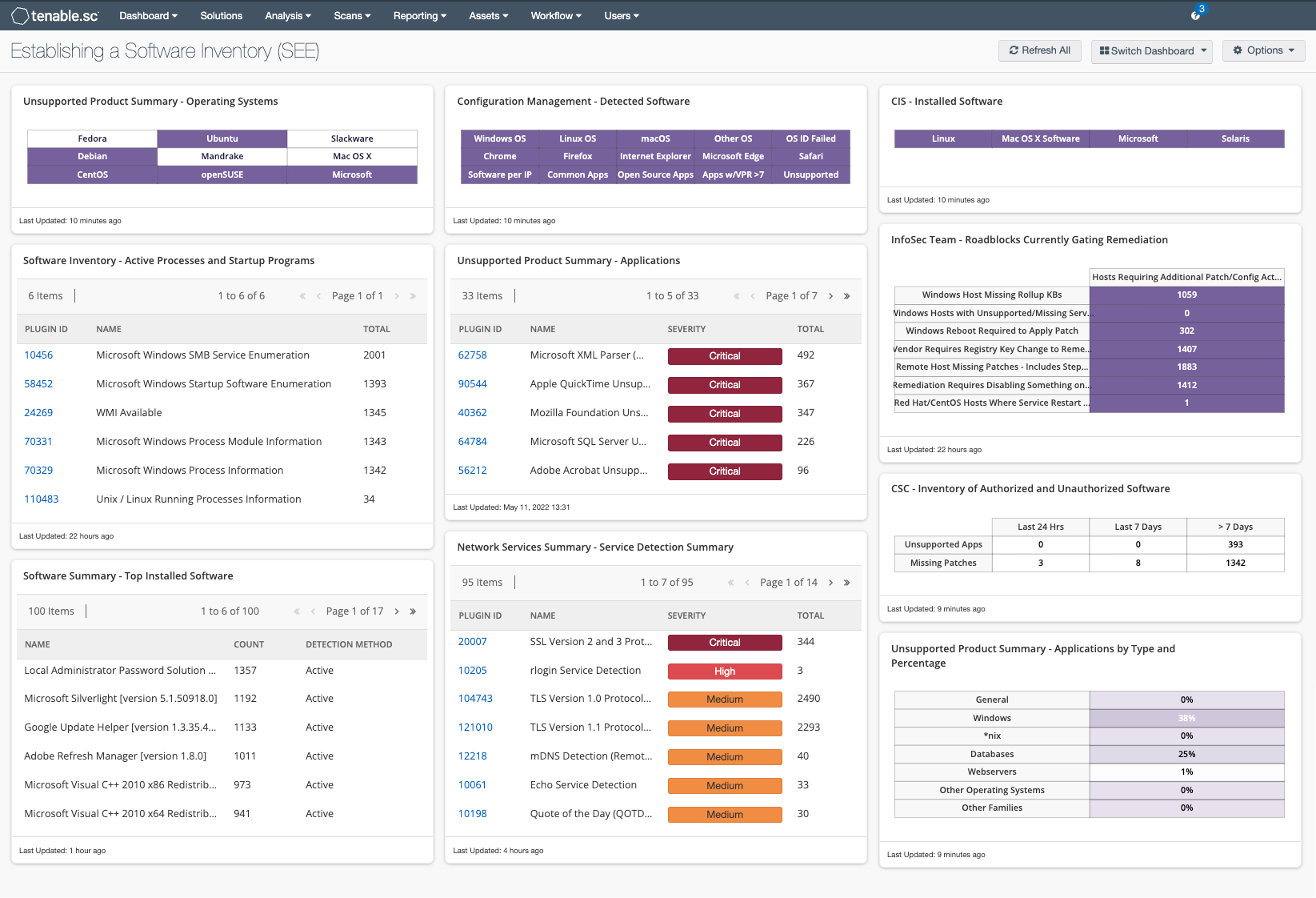
Software Inventory - Active Processes and Startup Programs: This table provides an overview of startup programs, and active processes on internal hosts on the network.
Unsupported Product Summary - Operating Systems: This indicator matrix reports on operating systems that are no longer supported.
Software Summary - Top Installed Software: This table displays a list of the software currently discovered on the network.
Configuration Management - Detected Software: This matrix presents indicators for operating systems, browsers, unsupported, and other software installations on systems within a network.
Unsupported Product Summary - Applications: The table displays unsupported applications by name and sorted by severity. Displayed is the plugin ID, application name, plugin family, severity, and the total host count found
Network Services Summary - Service Detection Summary: This component presents a list of services detected on internal network hosts. Services presented within this table can include network protocols, databases, servers, or remote desktop services.
CIS - Installed Software: This matrix component uses software enumeration plugins to aid the administrators in reviewing software detected on systems.
Unsupported Product Summary - Applications by Type and Percentage: This matrix displays the percentage of unsupported applications and operating systems based on plugin family, such as database servers, web servers, Windows, or other operating systems.
CSC - Inventory of Authorized and Unauthorized Software: This component shows the count of applications that either require patches or are unsupported by the vendor.
InfoSec Team - Roadblocks Currently Gating Remediation: This matrix displays known/identified roadblocks to completing remediation efforts. Items include: Windows Hosts missing rollups, unsupported/missing Service Packs, hosts requiring a reboot to apply patches, and hosts where registry key changes are required.