by Sharon Everson
February 26, 2016
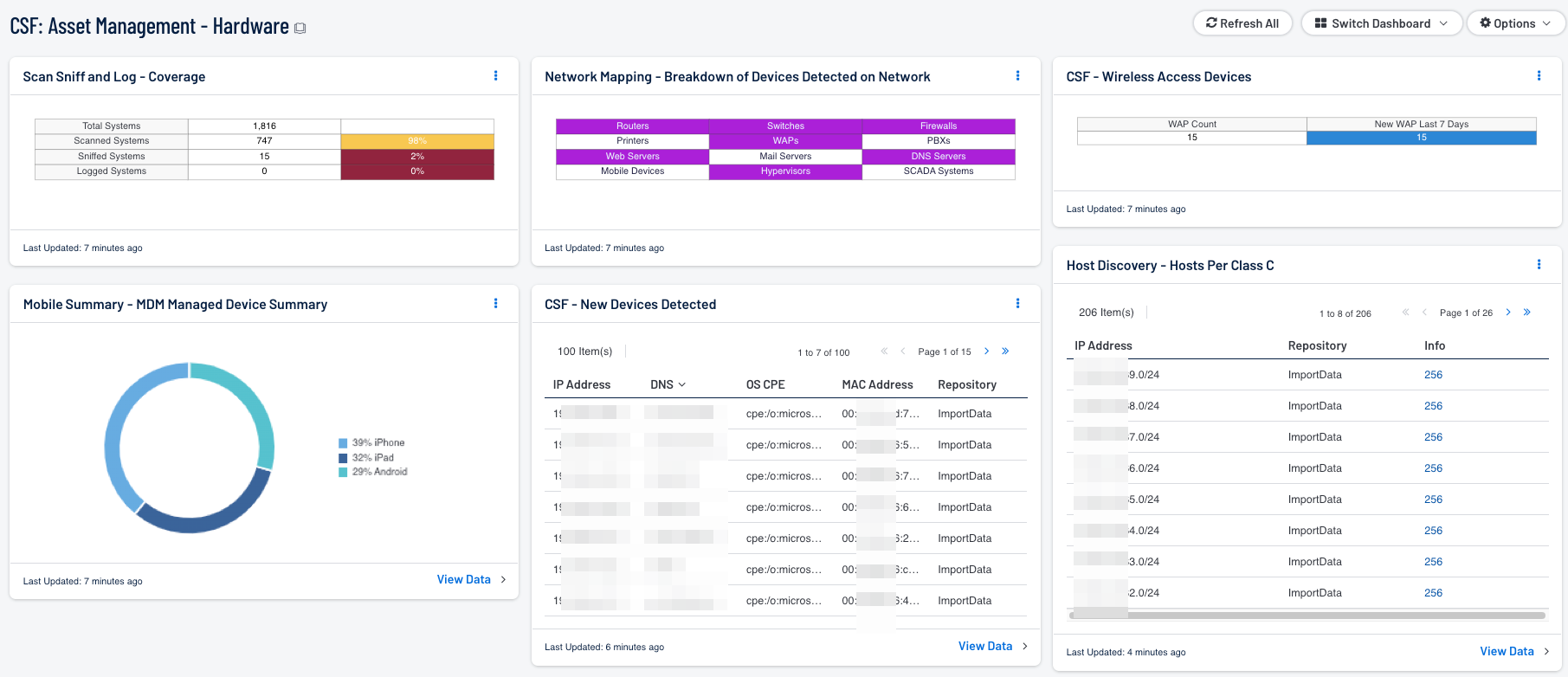
Most organizations today deploy and utilize a wide variety of hosts and devices, which becomes problematic for analysts to keep track of and manage properly. Gaps in the continuous monitoring of devices and assets can lead to an increased risk of unknown or rogue devices infiltrating a network. This dashboard aligns with the NIST Cybersecurity Framework (CSF) Asset Management category, which identifies, categorizes, and tracks multiple types of new and existing network devices and assets.
The CSF provides guidance based on existing standards, guidelines, and practices, which can be tailored to specific organizational needs. The first of five functions within the CSF is Identify, which is defined as “Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.” Each function includes multiple categories, and subcategories that address specific security requirements. The first category within Identify function is Asset Management (ID.AM), which is tailored to identifying Hardware, Software, Critical Assets, and External Systems. This dashboard focuses on the ID.AM-1 subcategory, which identifies multiple types of assets from physical, virtual, wireless, mobile, routers, servers, and more.
Keeping track of network assets can be problematic for analysts to maintain. Organizations often inventory and track purchased physical devices, and do not account for virtual, mobile, or wireless devices and systems. Proper hardware asset management should account for all assets that contain a MAC address from deployment to disposal. Inside this dashboard, the analyst will be able to detect both new and existing assets, along with virtual hosts, infrastructure devices, and previously detected systems. To ensure continued compliance, the analyst will need to scan, monitor, and identify new and existing devices on a regular basis.
When identifying assets, the analyst should begin with setting up specific asset lists and scans within Security Center. Additionally, mobile asset lists should also be created to identify mobile device types present within the network. New and existing hosts are detected by asset list, MAC address, and Class C address space, which aids in identifying the location of a host. In addition to detecting hosts, the analyst will also be able to detect infrastructure devices, servers, and mobile devices present on the network. Trend data is provided through daily host alerts, which tracks new and existing hosts observed for the first time each day. The analyst can utilize this data to identify hosts that may or may not be authorized.
Wireless access points and their SSIDs are another essential device type that organizations need to monitor. Wireless devices are detected both actively and passively by plugin ID and vulnerability text. To provide additional support in detecting the number of unique hosts, systems are identified through sniffing, and scanning. This provides a unique combination that will assist the analyst in detecting both authorized and unauthorized hosts.
By utilizing this dashboard, organizations can gain a clear and comprehensive view of devices and assets on the network. This will also allow organizations to quickly identify new and existing assets, reduce unnecessary costs, and makes effective purchasing and budgetary decisions that drive the business.
The dashboard and its components are available in the Security Center Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Security Center Feed under the category Compliance & Configuration Assessments. The dashboard requirements are:
- Security Center 5.2.0
- Nessus 8.5.1
- NNM 5.9.0
Tenable Security Center is the market-defining continuous network monitoring platform. Security Center includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable’s Nessus Network Monitor (NNM). Using Security Center, the organization will obtain the most comprehensive and integrated view of its network devices and assets.
This dashboard includes the following components:
- Scan and Sniff - Coverage: This matrix presents the total number of systems, along with the total number of scanned or sniffed systems and corresponding percentages. Scanned systems are detected by Nessus through network scans performed. Sniffed systems are discovered passively through NNM. The data displayed within this table includes the detected IP address and DNS name of the newly detected host.
- Mobile Summary - MDM Managed Device Summary: This component provides a model summary of managed devices with the MDM solution. Using the 'Model Summary' tool and sorting devices based on the Model column, the device count is used to create a pie chart that is easy to read and understand. From a quick glance, the user can understand the number of managed mobile devices.
- Network Mapping - Breakdown of Devices Detected on Network: This matrix presents a breakdown of detected network systems by type. A purple indicator denotes that systems of that type were detected; clicking on the indicator will bring up information on each of the detected systems, including IP address and MAC address. This information can assist an organization in maintaining an accurate inventory and detecting any unauthorized systems. The type of the network system is determined either based on its operating system (OS) or by the actively or passively detected vulnerabilities it has. Indicators are included for routers, switches, firewalls, printers, wireless access points (WAPs), PBXs, web servers, mail servers (IMAP, POP, and SMTP servers, as well as other specific servers such as Microsoft Exchange), DNS servers, mobile devices, hypervisors (virtual machines), and SCADA systems.
- Discovery Scan - Hosts Per Asset List: The 'Hosts Per Asset List' table component lists the live host counts distributed across Security Center assets. The table is sorted so the highest number of systems is presented at the top. In the screen shot, example network locations with their labels have been uploaded into Security Center. Organizations can create a wide variety of asset lists tailored to individual business requirements.
- CSF - New Devices Detected: This component presents newly detected hosts within the last 48 hours. Hosts are identified by multiple plugins, which provide the most comprehensive and accurate detection of new hosts. The plugin Host TTL discovered is utilized to passively identify the number of hops to a host. Other plugins leveraged within this component detect the number of hosts that have been scanned by different Nessus scanner versions. The data displayed within this table includes the detected IP address and DNS name of the newly detected host.
- CSF - Wireless Access Devices: This component uses passive and active plugins to locate wireless access devices. This matrix also allows the analyst to identify both authorized wireless and rogue access points that have joined the network within the last 7 days.
- Host Discovery - Hosts Per Class C: This table component displays live hosts across /24 network blocks. The table is sorted so the highest number of systems is presented at the top. A dashboard user can modify the component to report across /16 or /8 network blocks. If more sophisticated VLSM network division is required, it is recommended to leverage the Hosts Per Asset List table and upload the network ranges required with appropriate labels.