U.S. HHS Cracks Down on HIPAA Non-Compliance

The healthcare industry is one of the most heavily regulated business types today. To secure electronic protected health information (ePHI), organizations look to the Health Insurance Portability and Accountability Act (HIPAA) Security Rule and the Health Information Technology for Economic and Clinical Health (HITECH) Act. But they must also protect personal information, financial, and payment data in compliance with a variety of regulations including the Payment Card Industry (PCI) Data Security Standards (DSS).
Major 2014 fines
This past year, the U.S. Department of Health and Human Services, Office for Civil Rights (HHS-OCR) started fining and settling with healthcare organizations for HIPAA non-compliance. While the organizations had adopted HIPAA policies and procedures, they often failed to follow up with regular reviews of ePHI for risks, vulnerabilities, and unpatched software. For example, a community mental health service in Alaska was recently fined $150,000 for failure to patch software. And earlier in 2014, two New York hospitals settled fines totaling $4.8 million for protected data being made accessible through public search engines when servers were deactivated without appropriate technical safeguards.
They often failed to follow up with regular reviews of ePHI for risks, vulnerabilities, and unpatched software
The expansion of electronic medical records (EMR) and the use of portable devices, virtual systems, and cloud services are often outpacing the implementation of security technologies. Along with those trends comes the increased risk of unauthorized exposure of sensitive protected data. It’s true that the HIPAA Security Rule is largely non-prescriptive when it comes to specific security procedures, leaving organizations on their own to determine and implement best practices. But the HHS-OCR penalty fines should be a wake-up call to healthcare organizations to implement comprehensive and stringent security procedures and to make security a daily practice.
Challenges
One of the challenges in migrating to electronic records is overcoming attitudes developed over decades of reliance on paper records. While there was rarely much security around paper records, stealing them would have required physically entering healthcare facilities and gathering records individually. The connectivity that allows near-instant access to EMR for improved patient care can also expose those same records to near-instant mass theft from anywhere in the world.
The HHS-OCR penalty fines should be a wake-up call
In 2013, 43.8% of all major data breaches were healthcare data targets – the first time that healthcare was listed on the Identity Theft Resource Center’s list. And in 2014, that statistic held nearly steady at 42.5%. Organizations must have and enforce a comprehensive security policy, including a commitment to continuous monitoring for vulnerabilities and rapid remediation. It is no longer sufficient to just scan/audit/patch Windows targets for HIPAA compliance; there must be a more comprehensive approach across all computers, network devices, firewalls, databases, and mainframes.
One of the challenges in migrating to electronic records is overcoming attitudes developed over decades of reliance on paper records
In February 2014, Experian published the 6th Annual HIMSS (Healthcare Information and Management Systems Society) Security Survey of information technology and security professionals from U.S. healthcare organizations. The threat to ePHI is high; 56% of respondents were concerned about viruses, malware, and disruptive software; 51% said that device functionality was a concern; 56% were worried about hacking attacks, and 66% noted that software vulnerabilities or errors were a threat. Clearly the risk is increasing and security budgets are not necessarily keeping pace.
Multiple technologies
99% of professionals surveyed in the Experian report said that they have at least one security tool tested and in place. Total security cannot be achieved by using just one technology such as a firewall or user access controls; stronger protection is required, and technologies must be combined to provide the maximum protection: technologies such as encryption of sensitive data, intrusion detection and prevention systems, continuous network monitoring, endpoint defenses, and two-factor authentication.
How Tenable can help
Tenable’s SecurityCenter Continuous View™ (SecurityCenter CV™) can baseline an organization’s environment and discover 100% of IT assets, providing a comprehensive understanding of very large network topologies. SecurityCenter CV goes beyond vulnerability detection and compliance monitoring to detect unknown software, which helps detect new types of malware as well as potentially unwanted and unmanaged software in the IT systems.
Total security cannot be achieved by using just one technology
With a growing set of over 100 audit policies, SecurityCenter CV also audits systems to determine if they are configured correctly or compliant with specific regulations. Dashboards and reports display audit findings in summary and detailed formats.
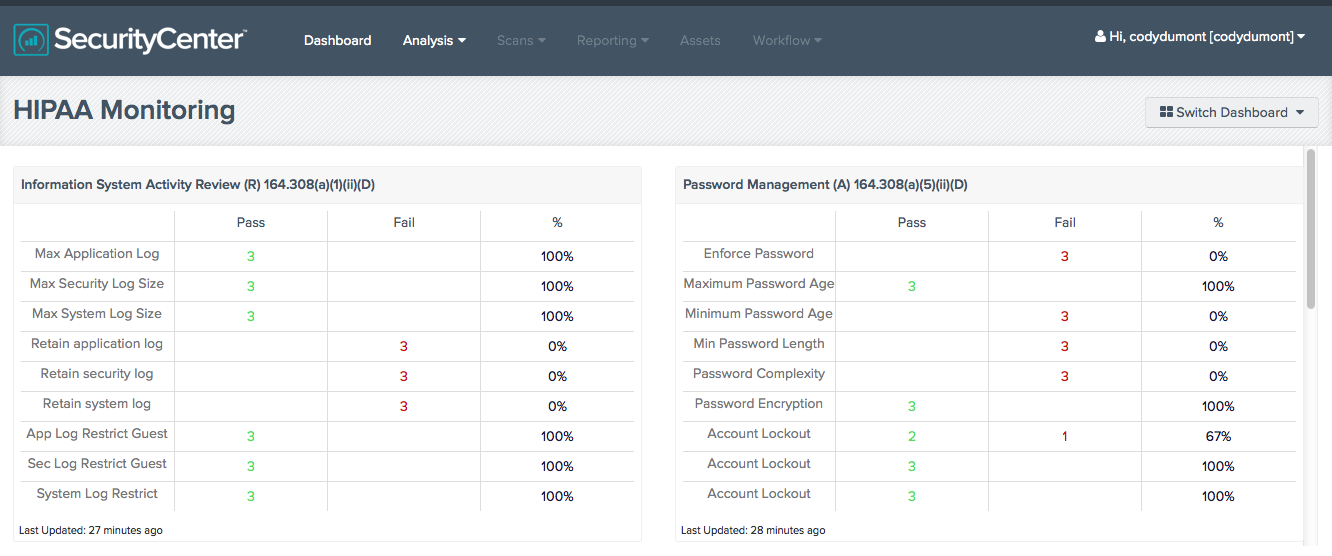
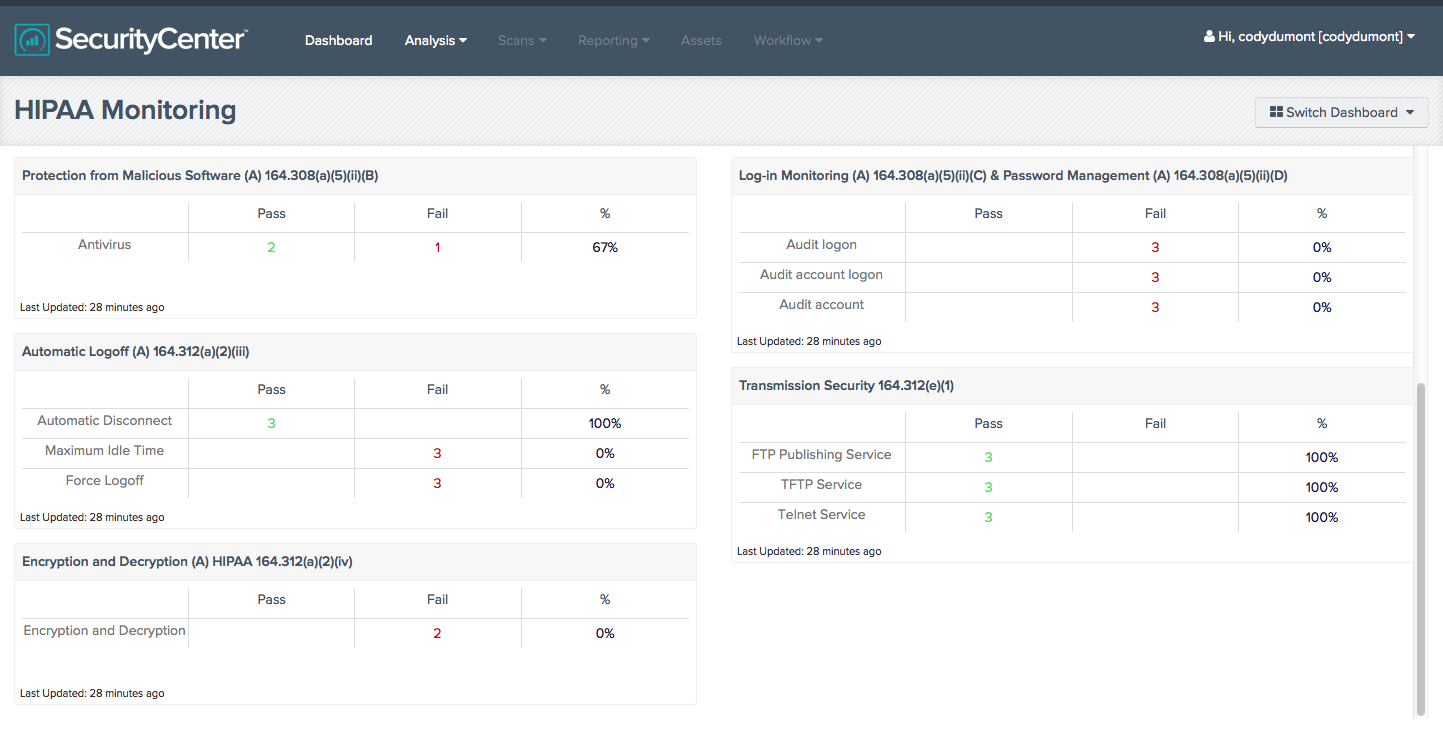
For example, the HIPAA Monitoring Dashboard in SecurityCenter CV provides configuration check results compared to the HIPAA Security Rule (subparts 164.308 and 164.312). The configuration checks are implemented through the Microsoft OS HIPAA Audit file which you can download from the SecurityCenter CV feed. The Dashboard displays compliance and non-compliance data in an easy to follow chart.
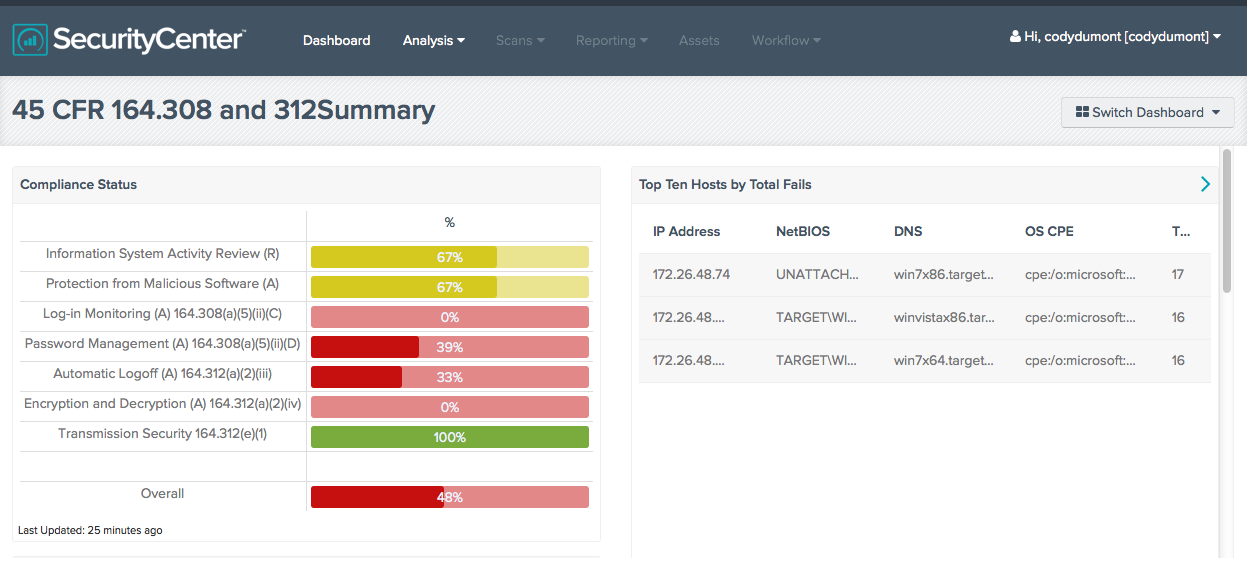
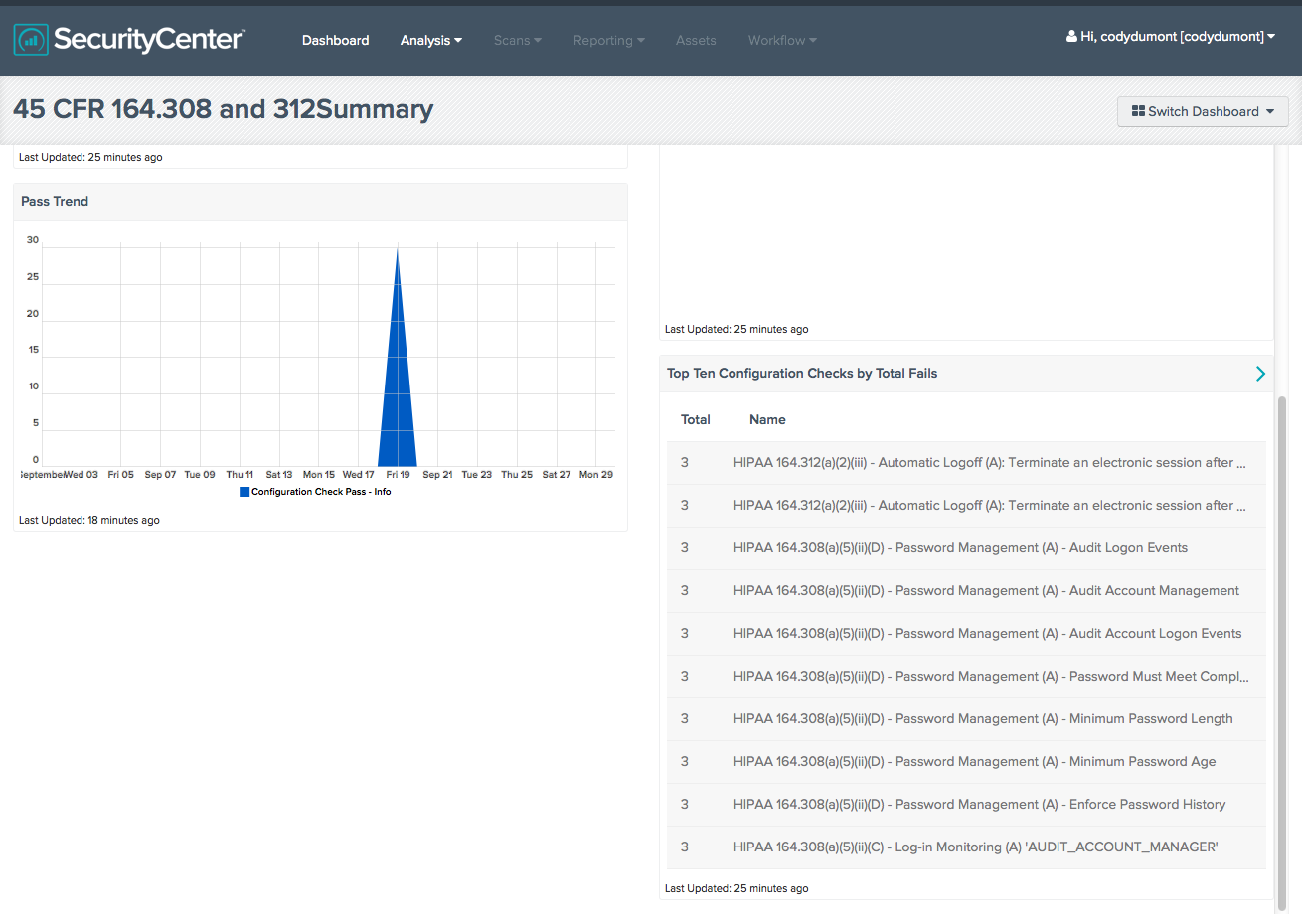
A HIPAA Monitoring Summary Dashboard summarizes the same configuration checks in graphs and consolidated tables for a quick view of compliance status and pass trends.
For more details on these Dashboards, see HIPAA Monitoring and HIPAA Monitoring Summary.
There is also a growing inventory of digital medical devices which cannot be actively scanned without potentially incurring functional or data-related damage. Such devices must be passively detected and monitored on the network to protect the systems and data. The Passive Vulnerability Scanner™ (PVS™) in SecurityCenter CV provides automatic discovery of devices, including transient portable devices, providing passive vulnerability scanning without interfering with critical operations.
SecurityCenter CV provides an advanced analytics engine that dramatically reduces the time it takes to conduct forensic analysis and reduces the potential damage that security threats can cause.
For more information about evaluating SecurityCenter Continuous View as a platform for demonstrating HIPAA and HITECH compliance, see the paper, Tenable Product Evaluations Application: HIPAA.
- Government
- Healthcare
- Security Frameworks