Transforming Security from Defense in Depth to Comprehensive Security Assurance

Over the past 20 years, we have seen steady growth in the development and marketing of security solutions. But despite the fact that organizations are investing in sophisticated security, major breaches are still occurring every day.
Layers of information security tools designed to protect our networks are leaving us vulnerable.
The problem is defense in depth. Layers of information security tools designed to protect our networks are leaving us vulnerable. Today’s CISO may deploy up to 100 tools throughout an organization for prevention, detection, and response. The tools may give the appearance of full coverage, but in reality, attackers find gaps in the layering of security solutions – holes that they can easily exploit. While your security investments may be effective individually, they must work together to deliver a comprehensive solution.
And defense in depth is not always effective at protecting newer technologies against threats. Today’s digital enterprise runs borderless technologies—in the cloud, on virtual systems, and on mobile devices—making it hard to stay ahead of new and malicious attacks.
This is why experts now say that it’s not a question of if you will be breached, but when.
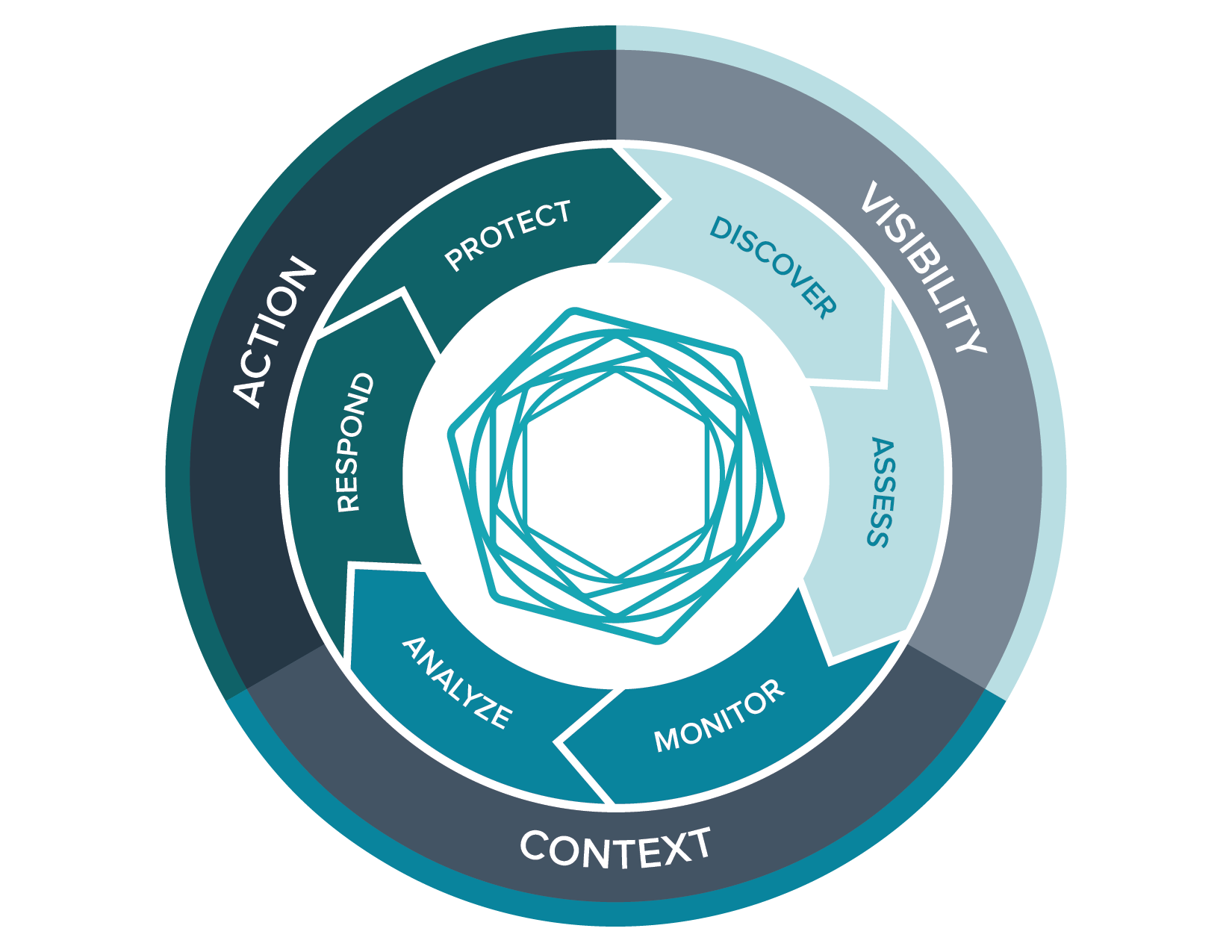
It’s time to transform security from a defense in depth model to comprehensive security.
It’s time to transform security from a defense in depth model to comprehensive security. Achieving a holistic solution requires three pillars of security assurance:
- Continuous Visibility into all assets, to meet the challenge of eliminating blind spots
- Critical Context to prioritize threats and weaknesses for response
- Decisive Action to reduce exposure and loss
Tenable is reimagining the security model to deliver comprehensive security for your organization. Our new whitepaper, Transforming Security from Defense in Depth to Comprehensive Security Assurance, explains the principles behind holistic security assurance. Get your copy to better understand how you can identify critical gaps and achieve comprehensive protection.
- Announcements
- Security Policy