Tracking Scan Authentication Failures
IT systems change all the time. New applications are added, configurations are changed, permissions get revised – the list goes on and on. In some cases, the changes end up restricting access to the system. For example, user accounts are removed, access is revoked, account credentials change or expire, leading to unexpected authentication failures and lockouts. And when the credentials fail, applications that depend on them fail, too.
When the application that ends up failing is a vulnerability scanner (such as Nessus), it could significantly impact an organization. Most organizations run vulnerability scans on a weekly or a monthly schedule, so a missed scan (due to authentication failure) could result in missed vulnerabilities, leaving systems within an organization exposed to those vulnerabilities for weeks, if not months, before the failures are identified and rectified.
To help our customers identify such failures earlier and resolve issues sooner, we recently released a new plugin, which consolidates authentication failures across various protocols and reports them in a single plugin.
The plugin runs toward the end of a scan and collects results from the entire scan to provide a consolidated report. The plugin needs to be enabled in the scan policy for it to provide a report. Also, note the plugin will not report authentication failures for any host that Nessus is able to successfully authenticate to for a given protocol.
The plugin currently reports authentication failures for the following protocols/technologies:
SSH
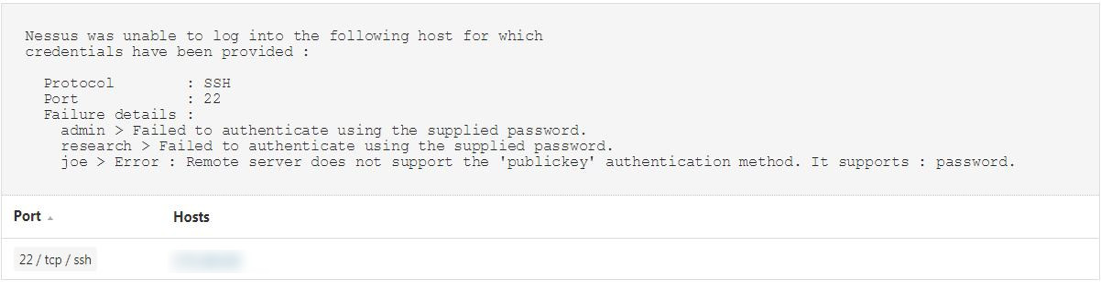
The plugin reports detailed information on authentication failures on a per-credential basis. As an example, if the scan policy had three credentials defined, and each one of them failed for one reason or another, it will provide a report on each user credential that failed and the reason it failed.
Here’s an SSH example:
SMB
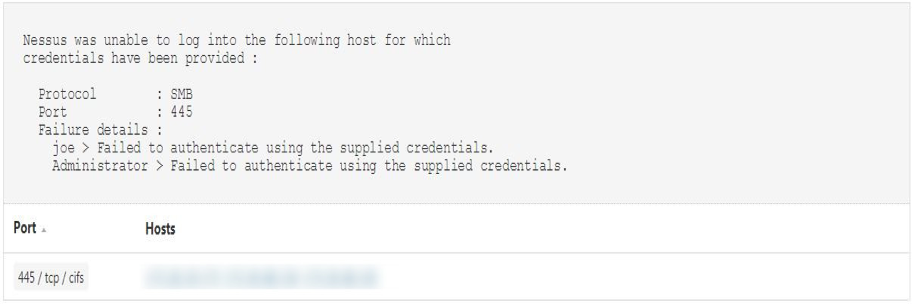
The plugin reports authentication failures on a per-credential basis for SMB as well.
Here’s an example:
Database authentication
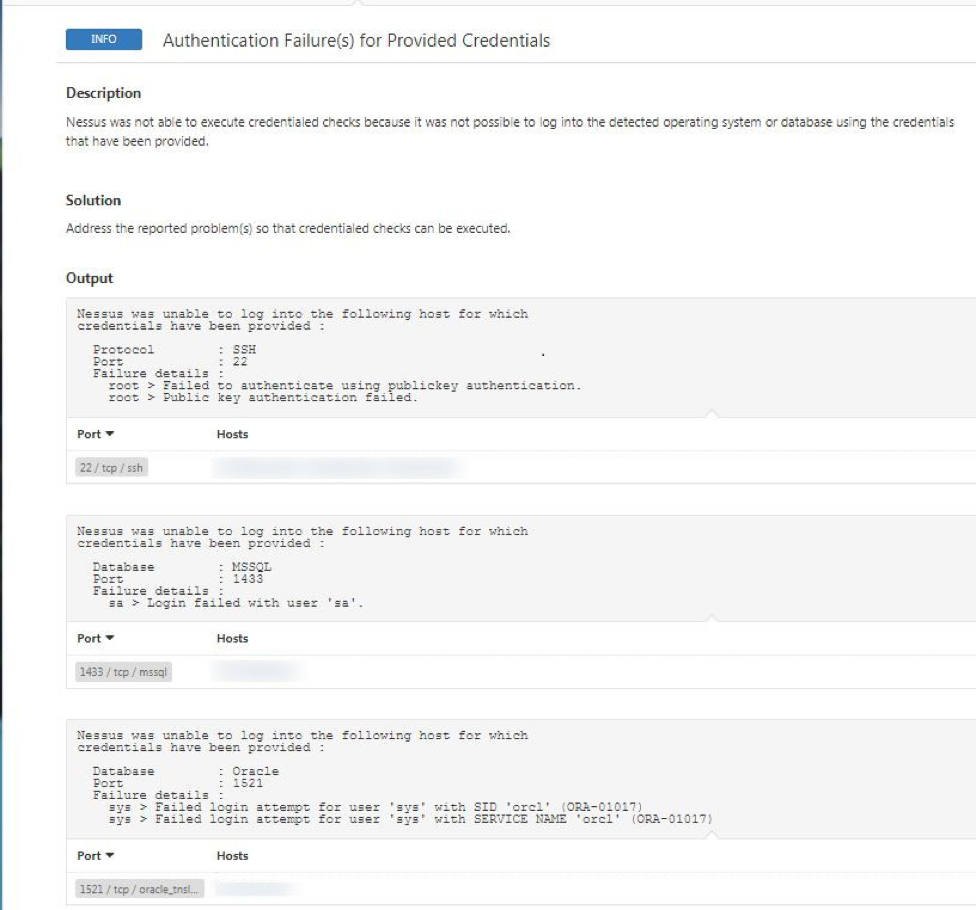
If database credentials are provided as part of the scan, and the credentials fail for one or more database technologies (e.g., MySQL, Oracle), this plugin will report those failures as well.
Here’s an example of database credential failure output:
IBM iSeries
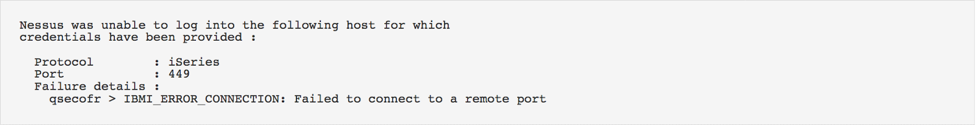
If IBM iSeries credentials are provided as part of the scan and Nessus fails to authenticate, the plugin will report authentication failure along with a reason why it failed.
Here’s an example:
Wrap-Up
For Nessus to perform an accurate and complete vulnerability scan, it needs credentials with appropriate privileges to do its job. We realize providing the right set of credentials and privileges to perform the scan is a challenging problem. And recently, we’ve released additional functionality to help solve some of those problems.
But a failed scan due to incorrect credentials shouldn’t be left unattended for a long time since it could have a huge unintended impact. The last thing you want is to be lulled into a false sense of safety while your environment changes around you.
Therefore, tracking such failures sooner should be a top priority for any organization. With the release of this new plugin, we hope our customers can do just that.
- Plugins
- Vulnerability Scanning

