ThreatConnect: Indicator for Suspicious Behavior and Malware
Information about threats comes from many different sources. Several third parties, such as ThreatConnect, offer such information which can be used as indicators for suspicious behavior and/or malware in your environment. ThreatConnect technology can be integrated with Tenable's SecurityCenter and Nessus products as follows:
- IP addresses, file hashes, and URLs can be used as indicators with SecurityCenter.
- File hashes can be used as part of malware scanning with Nessus.
For example, custom file hashes could be exported from ThreatConnect and used in Nessus or SecurityCenter custom malware scans. Below is the example output:
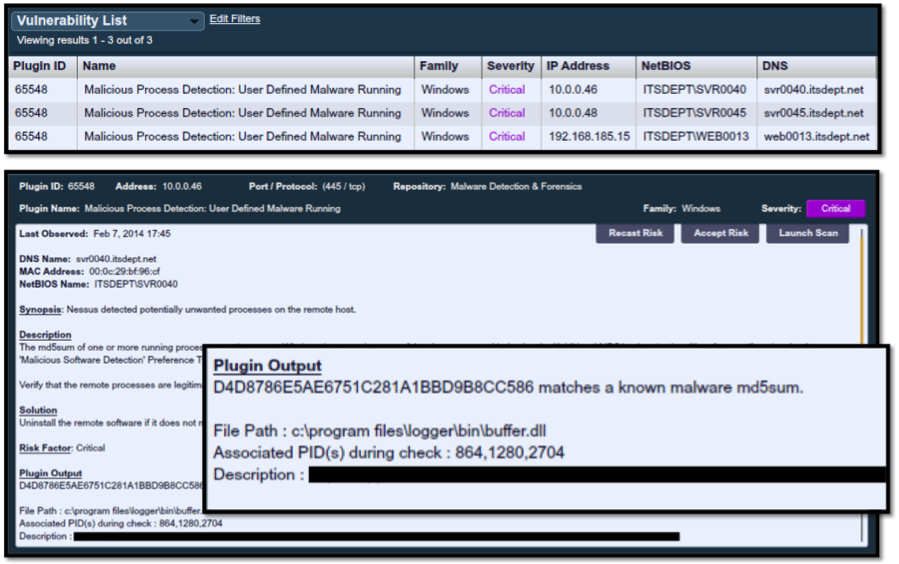
We've detected 3 hosts running malware, and the report output provides details such as process name, file path, and PID.
The list of "bad guy" IP addresses can also be imported into a SecurityCenter watch list as follows:
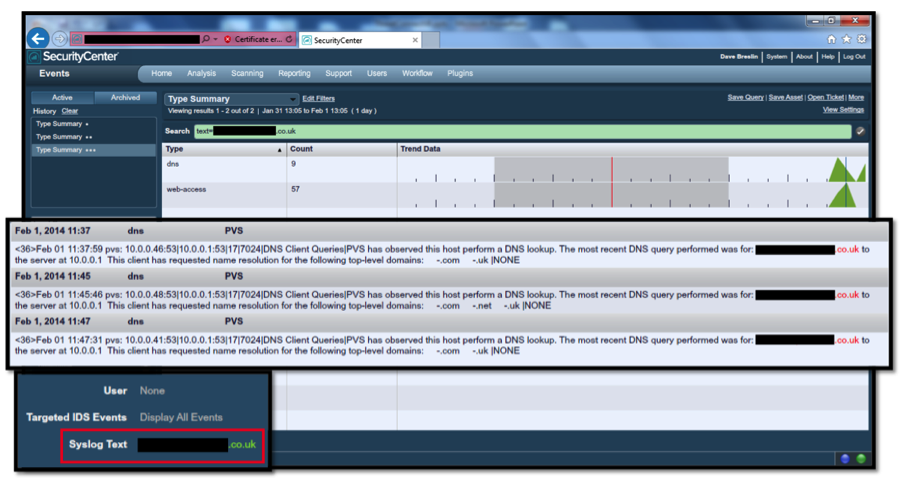
The domain name, which has been obfuscated, can be detected in the DNS logs being correlated inside SecurityCenter, ultimately producing the log entries showing the client IP addresses that have likely been infected.
For more details on this functionality, please see the document titled "Using ThreatConnect Indicators" posted to the Tenable Discussions Forum.
- Integrations
- Nessus
- SecurityCenter
- Threat Intelligence


