The Buck Stops There: NIST SP 800-171
The U.S. government is ultimately responsible for preventing unauthorized access and disclosure of its non-public information. However, it will soon require its service providers to put adequate safeguards in place as well.
Unauthorized access and disclosure of government information has become all too common in these times of frequent cyberattacks. As a result, the government is extending mandatory safeguards to nonfederal organizations that process, store or transmit Controlled Unclassified Information (CUI) or Covered Defense Information. These nonfederal organizations include contractors, subcontractors and service providers. Additionally, CUI is often provided to, or shared with, state and local governments, colleges and universities, and independent research organizations.
NIST SP 800-171: Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations provides federal agencies with recommended requirements for protecting the confidentiality of Controlled Unclassified Information (CUI) and DoD Covered Defense Information when it is processed, stored or transmitted by nonfederal organizations.
If you are familiar with NIST SP 800-53: Security and Privacy Controls for Federal Information Systems and Organizations, SP 800-171 will look familiar. It is essentially an SP 800-53 subset of tailored controls designed to protect CUI confidentiality, when the confidentiality impact value of the CUI is no lower than moderate.
Challenges of safeguarding CUI and Covered Defense Information
NIST SP 800-171 promises to promote standardization across the previously differing regulations and conflicting guidance that in the past, often resulted in confusion and inefficiencies. However, that does not mean that 800-171 compliance is without the following challenges:
Readiness Assessments: Prior to information system deployment, security assessments are required to demonstrate that safeguards comply with NIST SP 800-171 or with alternative, but equally effective, security measures. If you self-assess you must support these security assessments with comprehensive documentation to demonstrate that required controls are implemented correctly, operating as intended and producing the desired outcome. Assessing administrative controls, such as documenting security awareness training, can be done manually. However, realistically you must automate technical control assessment.
Ongoing Security Assessment: Obtaining initial authorization to operate is merely a good start. However, most networks are highly dynamic, so you cannot rely on periodic snapshots to safeguard covered information. Therefore, you must also monitor security controls on an ongoing basis to ensure their continued effectiveness. When the inevitable issues are discovered, you must communicate them internally and implement corrective action.
Control Consolidation: If your organization is one of the many with multiple compliance requirements, you are forced to dedicate an inordinate amount of resources to generating documentation for various auditors. This is especially costly if you are using multiple systems to monitor, assess and report across multiple compliance domains. Wherever possible, you need a common set of controls and “multilingual” reporting that documents control status using domain specific language.
Monitor, assess and communicate
Tenable just announced a new capability in SecurityCenter Continuous View® (SecurityCenter CV™) that enables you to measure, visualize and effectively communicate adherence to most NIST SP 800-171 technical security controls by automating their operation, monitoring and assessment to ensure they are implemented correctly, operating as intended and producing the desired outcome.
SecurityCenter CV provides fully customizable reports, dashboards and Assurance Report Cards® (ARCs) specific to NIST SP 800-171 – all out-of-the-box. You can use them as-is or quickly and easily tailor them to meet your specific security and business needs.
For example, the SecurityCenter CV Audit and Monitoring Dashboard aligns with the Audit and Accountability (section 3.3) and System and Information Integrity (section 3.14) families in NIST SP 800-171. These families are closely related, requiring the monitoring, analysis, investigation and reporting of unlawful, unauthorized or inappropriate information system activity – including inbound and outbound communications traffic – to detect attacks and indicators of potential attacks. By using this dashboard, you can better correlate audit review, assessment and reporting processes for investigating and responding to indications of inappropriate, suspicious or unusual activity. You will also be able to monitor information system security alerts and advisories and take appropriate actions in response.
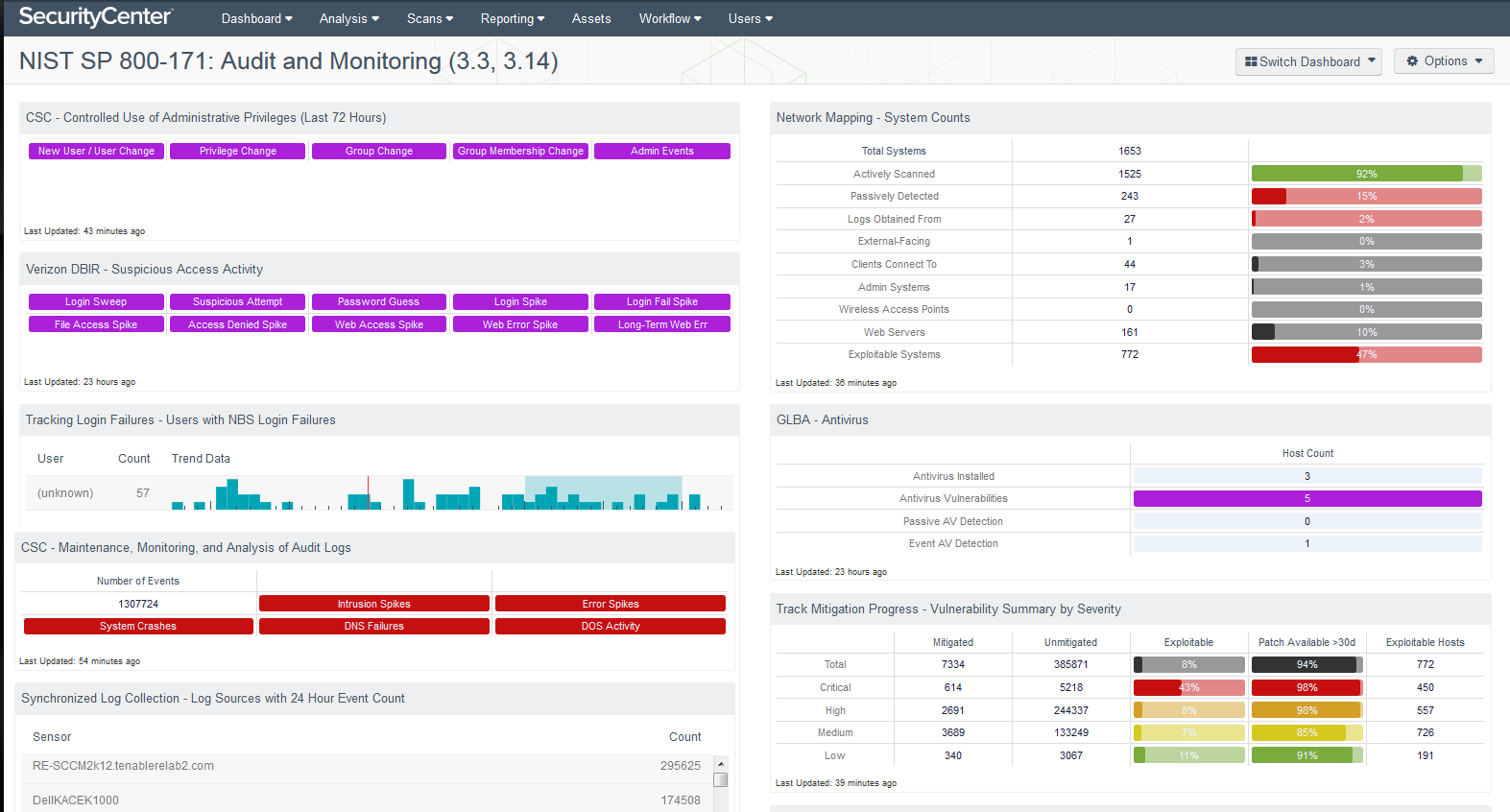
SecurityCenter CV offers multiple dashboards and Assurance Report Cards to help you automate SP 800-171 control monitoring, assessment and communication. Please take a minute to learn more about these new ARCs.
- Government
- NIST
- Security Frameworks


