Terrascan Joins the Nessus Community, Enabling Nessus To Validate Modern Cloud Infrastructures

The addition of Terrascan to the Nessus family of products helps users better secure cloud native infrastructure by identifying misconfigurations, security weaknesses, and policy violations by scanning Infrastructure as Code repositories. Try Terrascan in your browser with Terrascan Sandbox.
Twenty-three years ago when Nessus was created by Renaud Deraison, the computers the scan engine was designed for were physically attached to hubs and switches, changed infrequently and were always available unless somebody shut their system down for the weekend. Fast forward to the current day: Almost every organization has a cloud-first strategy and new workloads can be spun up and down in minutes across the globe with just a few clicks.
It would only follow that the tactics and tools security professionals use to evaluate the security of systems would need to change. This is especially true when dealing with cloud native environments which require security practitioners to do a deep dive into the guts of configuration files (aka Infrastructure as Code) in order to validate things like secrets management, RBAC, encryption, user privileges and other controls configured by individual developers.
That’s why we decided to integrate Nessus with Terrascan, our open-source IaC security analyzer. Terrascan enables cloud security practitioners to scan infrastructure code and find security issues as part of the software delivery process. Including Terrascan in Nessus enables Nessus users to expand the scope of their security assessments to include the validation of modern cloud infrastructure before it gets deployed.
Intro to Terrascan: Cloud-First Security Testing
As the creator of Terrascan, I see this as a super exciting opportunity for both the Nessus and Terrascan communities. Coming from a security and risk management background, I can relate to the challenges that security teams face when their company moves to a cloud-first strategy. In addition to having to deal with securing a whole new stack of technology, security team members have to deal with new workflows and requirements.
I remember one of my first public cloud projects. The company had decided it needed to rewrite a critical customer-facing system using a cloud-native architecture in order to stay competitive. It set an aggressive timeline of 12 weeks for the first working release. To accomplish this, they created a cross-functional team that included representatives from the business, software development, architecture, security, and operations teams. I was moved from security into the project team.
At first the task seemed daunting. There was a lot to learn and implement in a short period of time, and as the representative of the security team, I wanted to make sure security was embedded into every decision we made. That meant having a scalable way to review and provision network security settings and configuration, identity and access management policies, and ensuring that any cloud resource was configured following security best practices.
Speed, Consistency and Scalability with Infrastructure as Code
Around that time I discovered a tool called Terraform and the concept of Infrastructure as Code (IaC). Using Terraform we were able to quickly provision our infrastructure in a consistent manner where the code to provision our infrastructure lived side by side to our application code. This was a huge benefit compared to the way things were done in our on-premises data center, where we used ticketing systems to engage the security team and where developers perceived security as a black box that a siloed team handled.
But wait? What about standardization and security checks?
I soon realized IaC tools like Terraform still require a high level of governance in order to ensure each team and developer adhere to security standards and build infrastructure uniformly. Without a process of ensuring standards and security controls, development teams could quickly and consistently push misconfigured resources into production at scale. This translated into having to spend an increasing amount of time performing manual reviews of Terraform templates and code. Not only was this process an inefficient use of time but it was also not scalable, and would result either in missing product-delivery deadlines and/or releasing code to production that had not been tested for security issues.
With that I knew we were going to need a different approach to security in the cloud and started thinking about a solution.
Security Standard Enforcement and Risk Mitigation with Terrascan
With this in mind I developed an open source code scanner for Terraform - Terrascan.
Why Terrascan?
Typically, businesses decide to embark into cloud transformation journeys to reduce costs and increase the agility of their development teams. What I’ve found is that by adopting a tool like Terrascan and other cloud security best practices the security team can contribute to these goals while reducing risks in the environment. Adopting a policy-as-code approach to security allows for better understanding of security controls across the organization where issues are found as early as possible during development. This helps reduce the cost of finding and fixing issues in production, while empowering development teams to release with confidence.
Today, Terrascan features a pluggable architecture that uses the same approach to scan multiple IaC and cloud-native solutions including Terraform, AWS CloudFormation, Azure Resource Manager, Kubernetes, Helm, and Kustomize, and is used to address two core challenges:
Standardization: Terrascan helps implement policy as code by including 500+ policies across multiple providers that assess for misconfigurations using the Open Policy Agent (OPA) engine. Using the underlying Rego language, policies can be easily written and extended to include any standards specific to your environment. Examples of common security weaknesses that can be easily mitigated using Terrascan include:
- Server-side encryption misconfigurations
- Use of AWS Key Management Service (KMS) with Customer Managed Keys (CMS)
- Encryption in-transit SSL/TLS not enabled and configured properly
- Security Groups open to the public internet
- Inadvertent public exposure of cloud services
- Access logs not enabled on resources that support them
Risk Mitigation: Using Terrascan you can easily integrate cloud infrastructure security into DevOps pipelines to prevent security issues from reaching production. This includes integration with tools like Atlantis, Argo CD, GitLab and GitHub Actions.
Why Open Source?
Our belief at Tenable is that security is an important, foundational concern of any cloud project. The creation of open source tools like Terrascan helps to standardize and democratize security in a way that anyone can contribute to. It benefits all organizations, and the community itself, to have security policies open for everyone to look at so we can quickly identify the best practices. Then we can apply those best practices consistently across all applications by exposing our code base to community members to actively contribute to the underpinning policy base and easily modify to meet their specific needs.
Get Started Today with Terrascan!
Accessing the new Terrascan capabilities within Nessus is a breeze. The first thing you will need to do is download the latest Nessus version (10.1.2 or later). Once you log back in, click on the new Terrascan resource item on the left-hand side navigation menu to install.
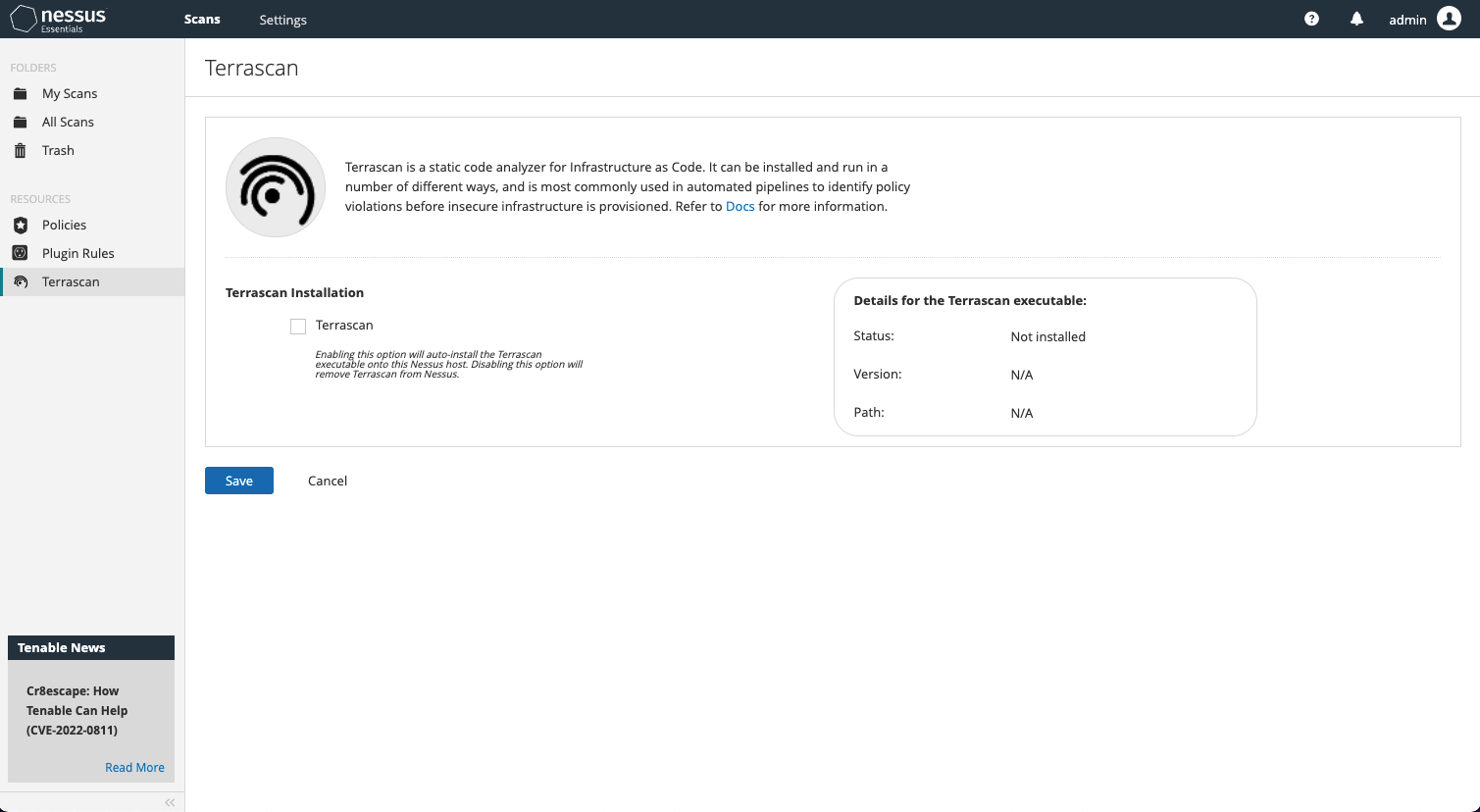
Once installed, you’re ready to launch your first Terrascan assessments. It’s that easy!
Looking to try Terrascan in your browser today? Try Terrascan Sandbox and scan IaC languages like Docker, Kubernetes and Terraform with just a few clicks. With the Terrascan Sandbox you’re one scan away from safer code.
- Nessus
- Vulnerability Management

