Tenable Facilitates Detection of OpenSSL Vulnerability Using Nessus and Nessus Perimeter Service
Facilitate easy detection of the OpenSSL Heartbeat vulnerability in your enterprise
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
Tenable Network Security® released plugins for the detection of the OpenSSL heartbeat vulnerability (aka the “Heartbleed Vulnerability”) on the 8th of April for Nessus® and the Passive Vulnerability Scanner™ (PVS™). A plugin for detecting the vulnerability in Apache web server logs has also been added to the Log Correlation Engine™ (LCE™) and available for reporting in SecurityCenter™ and SecurityCenter Continuous View™. Details about the vulnerability can be found in a blog by Tenable’s Ken Bechtel, Beware of Bleeding Hearts.
To facilitate the detection process for its customers, Tenable has also provided a new “Heartbleed Detection” Policy Wizard which is now available for use with Nessus and Nessus Perimeter Service. This wizard will create a policy that performs a remote check for the Heartbleed vulnerability (CVE-2014-0160) on all ports where SSL is detected.
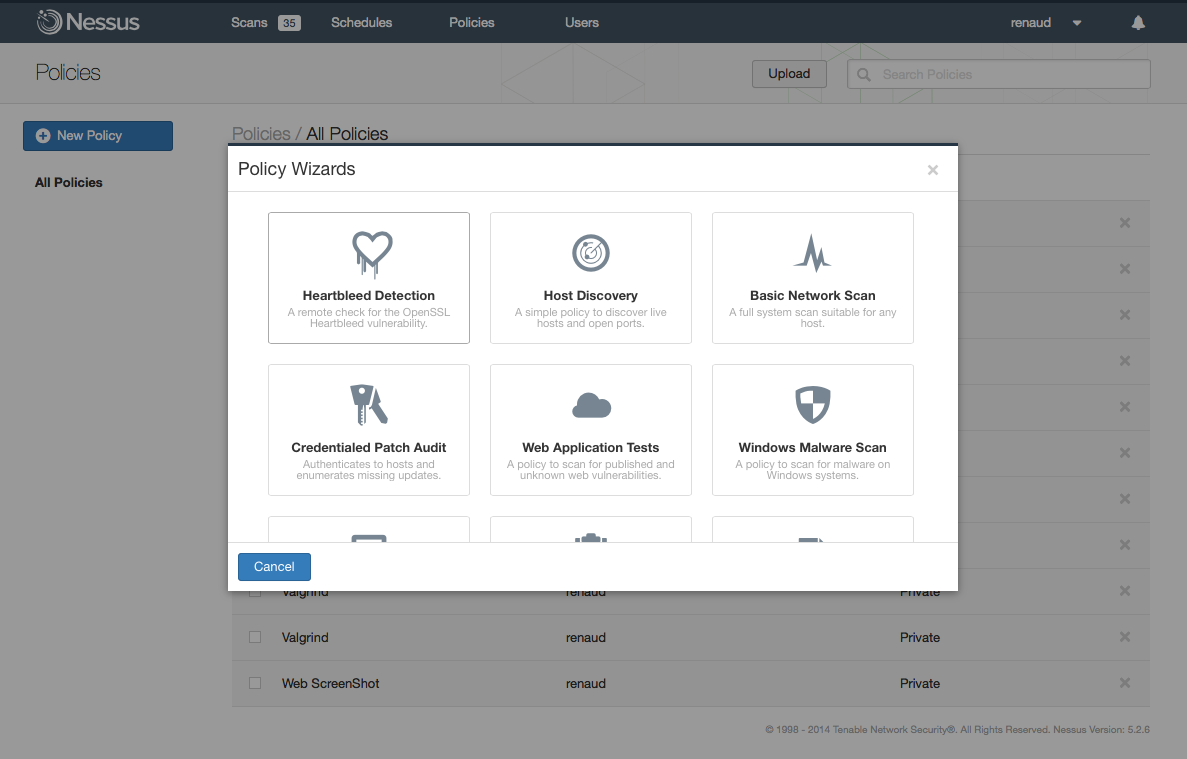
To use the wizard simply click on the “Policies” tab and then click on “New Policy”. Select the Heartbleed Detection wizard and you will be guided through a simple two-step process. Step One: Name your policy and modify any of the other optional settings then click on “Next”:
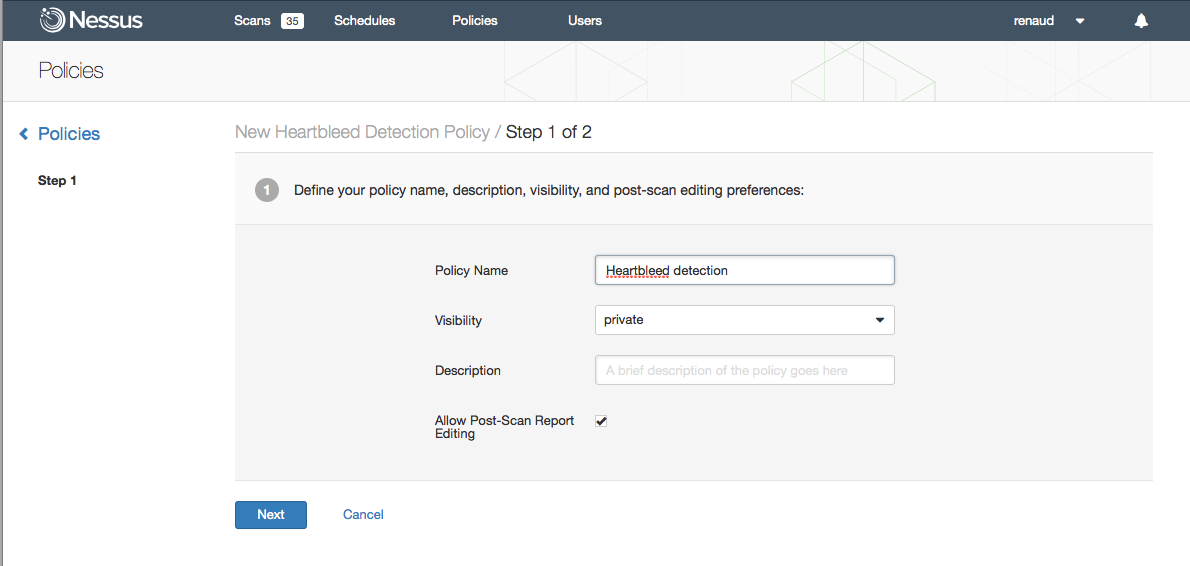
Step 2. Select the type of scan you want to perform based on the following levels of “intrusiveness”:
- QUICK – scans the ports known to be associated with SSL (such as HTTPS, IMAP, LDAP, NNTP, POP3, SMTP, XMPP, SQL);
- NORMAL – scans the Nessus default set of ports (~5000); or
- THOROUGH – scans all 65,535 ports and attempts to negotiate SSL on each of them (usually we negotiate SSL on ports that are known to host an SSL service, as the SSL negotiation is known to crash some 3rd party services).
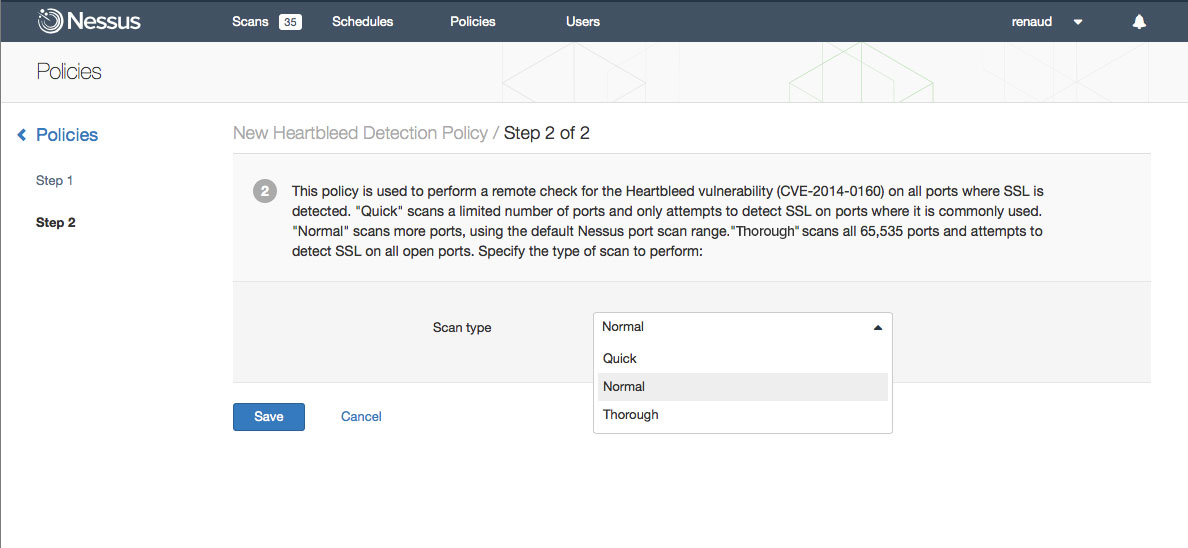
Click Save and the Policy will now be available for use when you create a new scan or scan schedule. Additional details on testing for the Heartbleed vulnerability can be found on the Tenable Discussion Forum.
If you discover any systems using a vulnerable version of OpenSSL, the only fix for this is to update the OpenSSL package to version 1.0.1g. Tenable also strongly recommends that once you are patched, you should also revoke the associated SSL key(s), and reissue new keys. This is the best way to ensure that your trusted SSL communications are not compromised.
- LCE
- Nessus
- Nessus Network Monitor
- OpenSSL
- Plugins
- SecurityCenter