Proof-of-Concept Code Gives Standard Microsoft Exchange Users Domain Administrator Privileges (CVE-2019-0724, CVE-2019-0686)

Publicly released and newly named “PrivExchange” proof-of-concept (POC) privilege escalation code exploits protocol flaws and default configurations to give standard Exchange users Domain Administrator access.
Background
Update February 12: Microsoft released updates for CVE-2019-0724 and CVE-2019-0686 to address this vulnerability.
Update February 6: Microsoft published a security advisory (ADV190007) that includes a Throttling Policy that will mitigate this vulnerability until a software update. Additionally, they noted that the vulnerability described in the blog post below only affects on-prem deployments of Microsoft Exchange. Microsoft notes in the advisory that this workaround might disrupt some functions in Outlook for Mac, Skype for Business Client, Apple Mail Clients and third-party applications.
Previously documented protocol weaknesses and vulnerabilities in fully patched Microsoft Exchange are now in the spotlight due to publicly released POC code. According to security researcher Dirk-Jan Mollema, this vulnerability: “Probably affects the majority of orgs using AD and Exchange.”
The POC code submitted to Github allows a standard Exchange user to gain Domain Administrator access to a fully patched Microsoft Exchange 2016 server and dump domain credentials from the Domain Controller.
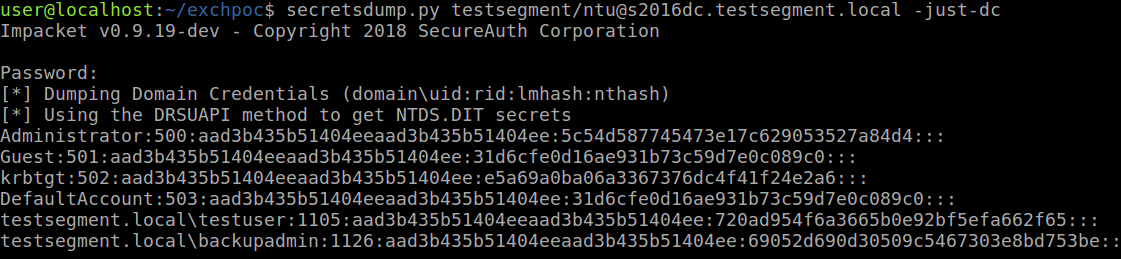
Vulnerability Details
This issue is not a single vulnerability, but rather a collection of previously disclosed protocol weaknesses affecting NT LAN Manager (NTLM) authentication and Exchange Server vulnerabilities. Per the researcher’s blog:
- Exchange Servers have (too) high privileges by default
- NTLM authentication is vulnerable to relay attacks
- Exchange has a feature which makes it authenticate to an attacker with the computer account of the Exchange server
Mollema also included a script that reportedly allows for unauthenticated attacks where one could relay the authentication of a user in the same network segment to Exchange Web Services (EWS) and use their credentials to perform the exploit.
Urgently required actions
This issue reportedly affects fully patched Microsoft Exchange servers, however the following mitigations, including one recommended by Microsoft, are listed by the security researcher:
- Remove the unnecessary high privileges that Exchange has on the Domain object (references included below).
- Enable Lightweight Directory Access Protocol (LDAP) signing and enable LDAP channel binding to prevent relaying to LDAP and LDAPS respectively
- Block Exchange servers from making connections to workstations on arbitrary ports.
- Enable Extended Protection for Authentication on the Exchange endpoints in IIS (but not the Exchange Back End ones, this will break Exchange). This will verify the channel binding parameters in the NTLM authentication, which ties NTLM authentication to a TLS connection and prevent relaying to Exchange web services.
- Remove the registry key which makes relaying back to the Exchange server possible, as discussed in Microsoft’s mitigation for CVE-2018-8581. (Tenable provides coverage for this mitigation)
- Enforce SMB signing on Exchange servers (and preferable all other servers and workstations in the domain) to prevent cross-protocol relay attacks to SMB.
Identifying affected systems
A list of Nessus plugins to identify this vulnerability can be found here.
Tenable also provides the mitigation-specific configuration audit checks below for Server Message Block (SMB) signing and NTLM v2 at https://www.tenable.com/downloads/audit using these audit files:
CIS_DC_SERVER_2012_Level_1_v2.0.1.audit
CIS_DC_SERVER_2012_R2_Level_1_v2.3.0.audit
CIS_DC_SERVER_2016_Level_1_v1.0.0.audit
CIS_MS_2008_Server_Enterprise_v1.2.0.audit
CIS_MS_2008_Server_SSLF_v1.2.0.audit
CIS_MS_SERVER_2012_Level_1_v2.0.1.audit
CIS_MS_SERVER_2012_R2_Level_1_v2.3.0.audit
CIS_MS_SERVER_2016_Level_1_v1.0.0.audit
CIS_MS_Windows_10_Enterprise_Level_1_Bitlocker_v1.3.0.audit
CIS_MS_Windows_10_Enterprise_Level_1_v1.3.0.audit
CIS_MS_Windows_Server_2008_DC_Level_1_v3.0.1.audit
CIS_MS_Windows_Server_2008_MS_Level_1_v3.0.1.audit
CIS_MS_Windows_Server_2008_R2_DC_Level_1_v3.1.0.audit
CIS_MS_Windows_Server_2008_R2_MS_Level_1_v3.1.0.audit
DISA_STIG_Server_2008_DC_v6r40.audit
DISA_STIG_Server_2008_MS_v6r40.audit
DISA_STIG_Server_2012_and_2012_R2_DC_v2r12.audit
DISA_STIG_Server_2012_and_2012_R2_MS_v2r12.audit
DISA_STIG_Windows_10_v1r13.audit
DISA_STIG_Windows_Server_2016_v1r4.audit
الحصول على مزيد من المعلومات
Learn more about Tenable.io, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


