Patching Makes Perfect

Malware and ransomware are a big topic these days, especially with the recent releases of WannaCry and Petya variants.Typically, when I read about new malware my first thought is, “How can I stop the infection from happening in the first place?” Tenable.io™, the first Cyber Exposure platform, answers that question by identifying vulnerabilities and presenting the information in an easy-to-understand format.
A common method of malware delivery is via an exploit kit. An exploit kit is a scalable software package, which allows modules to be removed, added or updated with new exploits. These kits typically come bundled with a management console, vulnerabilities for different applications and functions that allow an attacker to launch attacks.
As new vulnerabilities are identified, exploit modules are created which take advantage of the new exposures. Unpatched applications such as Adobe Flash, Adobe Acrobat and Microsoft Internet Explorer are commonly sought out by attackers. When activated, the kit identifies any vulnerabilities in the software installed on the targeted system.
Patching is an effective method of mitigating this risk. According to the 2017 Verizon Data Breach Investigations Report, “Having a good patch process is a fundamental security practice.” But patching can be a pain due to the sheer number of updates available. If you have multiple system architectures within your organization, the number of patches increases exponentially, which also increases your cyber risk.
When speaking with customers about the importance of patching, I’ve often heard the following two questions:
- With so many patches available, how do we prioritize them?
- How can we keep our organization up-to-date when vendors continue to release new updates?
Luckily, Tenable.io can help answer these two questions. Tenable.io helps you manage, measure and reduce your attack surface by prioritizing patches based on their risk.
All Patches Are Not Equal, Focus on What is Important
All vulnerabilities are not equal and should be evaluated against policies and operational requirements. When planning mitigation efforts, you will need to assign priorities to vulnerabilities and then execute your patching strategies accordingly. Tenable.io easily provides you the information needed to determine which patches are missing, and which are more critical than others.
Filters help to focus the vulnerability workbench to a manageable and more targeted view. In the example below, we are setting the date range to a specific 90-day time period using the advanced filter.
From the drop down picker select ‘Patch Publication Date.’ Set the date ‘earlier than’ today’s date, click the ‘+’ icon and select ‘Patch Publication Date’ once again. Set the date ‘later than’ three months prior.
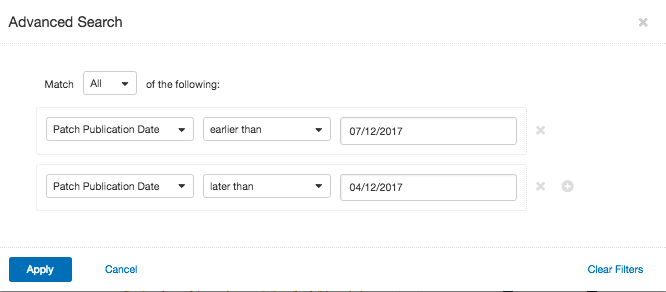
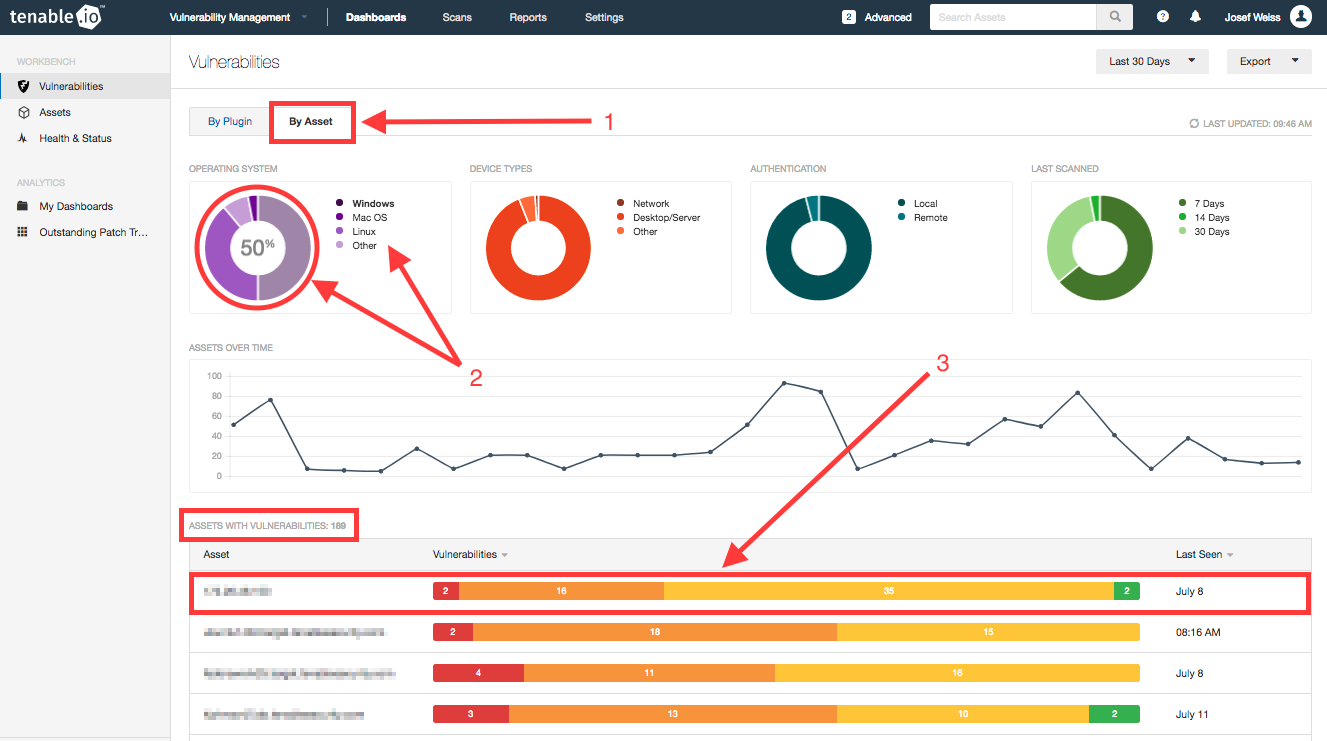
Once you click apply, you will be returned to the Vulnerabilities By Plugin Workbench. The missing patches that meet the search criteria will be displayed, which can still be a lot of information. Then click on the ‘By Asset’ tab, noted by the number 1 in the screenshot below. If you hover over the first ring chart, noted by the number 2, percentages will be displayed. In this example, I hover over either ‘Windows’ or the color associated with Windows assets, and can see that 50 percent of Windows Operating Systems are missing patches from the last 90 days.
You can view details for the ‘Assets with Vulnerabilities’ in the areas noted by the number 3. Here you can see the number of assets with vulnerabilities, sort Assets, Sort by Vulnerability Count, and by Last Seen date.
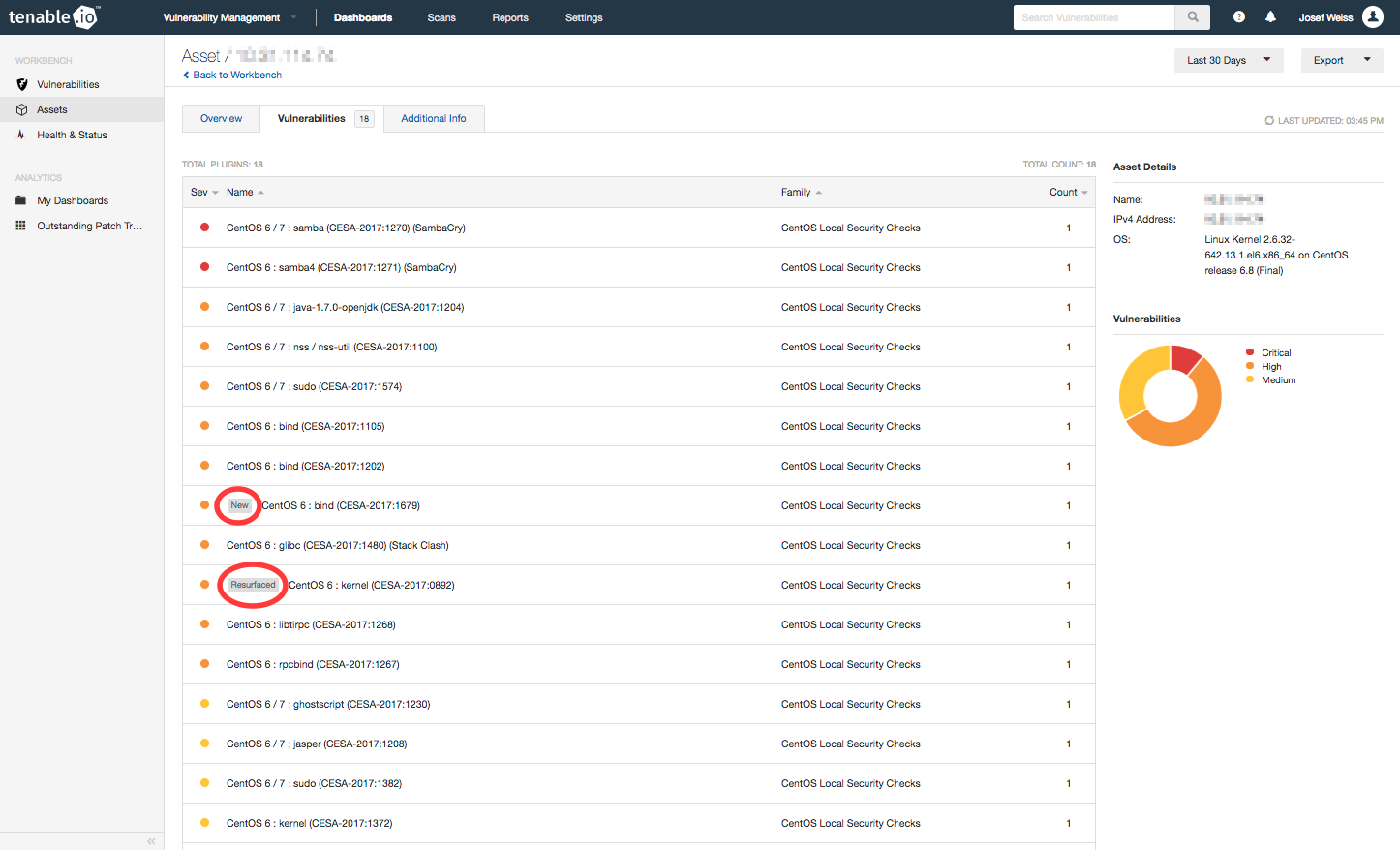
Clicking anywhere on the asset loads a page for that asset, displaying the host details and all the missing patches. Patches that are missing and those that have been detected in the last 14 days are presented with a ‘New’ tag. Those patches that have resurfaced are also tagged appropriately.
I recommend setting additional filters to refine the data further, such as a filter for ‘Exploit available = true.’ Adding this filter to the previous filter will only return results for hosts which are missing patches from the last 90 days in which an exploit exists. You may add filters for specific severity levels to refine data further. You should also conduct queries with filters to search for missing patches over a year old or more.
Timely patch management can reduce your organization's cyber risk, eliminating the types of scenarios demonstrated here. Data breaches based on high-profile malware dominate the media, often times leading to a loss of reputation for those organizations who become the unfortunate targets of a malicious attack.
Utilizing Tenable.io and these methods will enable you to successfully navigate vulnerability data with ease. By adding filters for exploitable vulnerabilities, and filtering on specific date ranges, you can identify and focus your patching efforts on applications or hosts which are most likely to be exploited. Reviewing the vulnerable assets and applications will allow you to further identify and prioritize software and devices that should take priority. I also utilize dashboards such as the Outstanding Patch Tracking Dashboard to gain additional insight into patching efforts.
Wrapping up
Tenable.io helps you to manage, measure and reduce your cyber risk by identifying missing patches and prioritizing those most critical. Whether you are communicating up the chain, to peers or to your team, Tenable.io enables flexible navigation through vulnerability data, while allowing you to quickly and effortlessly take a thorough look at your outstanding risk.
Interested in learning more about Tenable.io?
- Visit the Tenable.io product page
- Start a Tenable.io Vulnerability Management free trial
- Patch Auditing
- Tenable Vulnerability Management
- Tenable Vulnerability Management (DO NOT USE)
