NIST Cybersecurity Framework 1.1

On April 10, the comment period closed for the NIST revised Framework for Improving Critical Infrastructure Cybersecurity (Framework). The current draft includes expanded explanations, refinements and a completely new section: Measuring and Demonstrating Cybersecurity.
Measuring and demonstrating cybersecurity to business leaders and partners is simultaneously very important and very challenging. Various sources, including the EisnerAmper accounting firm and the National Association of Corporate Directors, have reported that only about 20% of boards have confidence in the state of their organization’s cybersecurity. Clearly measuring and demonstrating cybersecurity is important to boards.
The difficult issue is accurately correlating cybersecurity activities and outcomes to desired business objectives
Unfortunately, measuring and demonstrating cybersecurity is not easy. The first issue is measuring cybersecurity posture. This is typically performed by auditing cybersecurity activities and outcomes to determine if controls are implemented correctly, operating as intended and producing the desired outcome. The second — and in my opinion —much more difficult issue is accurately correlating cybersecurity activities and outcomes to desired business objectives.
We could consider many examples of business objectives, but consider the example cited in the draft Framework: a retail bank wanting to increase the number of online banking customers may do so by implementing stronger authentication. The draft Framework readily admits that achieving an increase in online banking customers is also contingent upon:
- Developing messages regarding trusted online transactions
- Targeting specific consumer demographics
- Selecting communication channels that are most meaningful to those demographics
- Marketing through those communication channels over the necessary timeframe to achieve the objective
Correlating cybersecurity with business objectives — a laudable goal
Clearly, it would be difficult to separate the effects of stronger authentication from the above-listed communication factors to calculate the impact on the number of online banking customers. Even if it were possible, communication factors are only one of the variables that would need to be isolated to measure the impact of stronger authentication on online banking customers. Ideally, measuring the impact of stronger authentication would require a controlled experiment that isolates marketing communications, the economy, the competitive environment, sales promotions, training and other factors.
As much as I applaud the Framework’s goal of measuring cybersecurity and correlating it with business objectives, I think it remains a long-term aspiration for most organizations. Most organizations are challenged to measure cybersecurity in a meaningful way.
Measuring cybersecurity remains a significant, but achievable, challenge
Most security organizations struggle to communicate timely security status to business leaders and business partners. Synchronizing volumes of data across multiple sources and abstracting it in a manner that makes sense to business leaders is a difficult challenge. However, it is a challenge that can be addressed today.
Tenable Assurance Reports Cards (ARCs), available through SecurityCenter Continuous View® (SecurityCenter CV), make this task much easier. ARCs bridge the communication gap between security professionals and business executives by visually communicating the status of the most critical security controls in a familiar report card format.
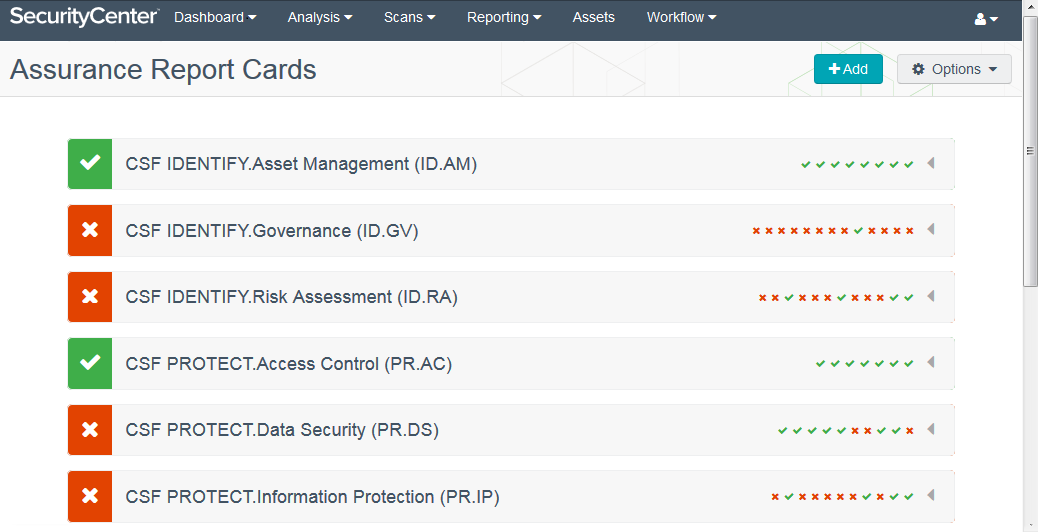
SecurityCenter CV includes multiple ARC templates to measure technical control status across the NIST Cybersecurity Framework’s Identify, Protect and Detect functions. At the highest abstraction level, ARCs present pass/fail status. The screenshot below shows six ARCs – two passing and four failing. You can easily tailor an ARC to scope it to report on a specific business system so you can communicate status to the business owner.
Evaluation of multiple policy tests determines an ARC’s pass/fail status. The rows of small green check marks and red Xs indicate which policy tests have passed and failed, respectively. When all policy tests pass, the overall ARC achieves passing status.
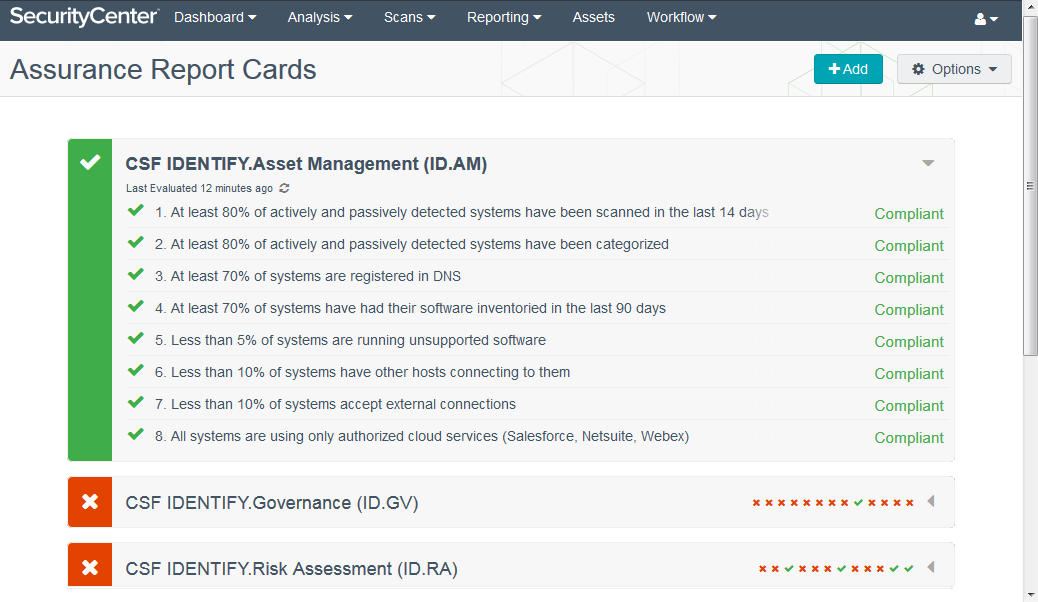
The screenshot below shows the specific policy tests evaluated for the CSF IDENTIFY. Asset Management (ID.AM) ARC. You can add, delete or edit policy tests as needed to assess your environment.
Accurately correlating cybersecurity status to business objective attainment is not a pipe dream, but it will likely remain a stretch goal into the foreseeable future. However, you can start communicating security status based on the NIST Cybersecurity Framework today. ARCs deliver security status in a format that your organization’s business leaders and partners can understand.
Measuring state and trends over time, internally, through external audit, and through conformity assessment, enables an organization to understand and convey meaningful risk information to dependents, partners, and customers. [NIST CSF 1.1]
For more information
Learn more about how Tenable SecurityCenter Continuous View supports the NIST Cybersecurity Framework.
- NIST
- Security Frameworks
- SecurityCenter