Microsoft’s September 2020 Patch Tuesday Addresses 129 CVEs

For the fourth month in a row, Microsoft patches over 120 CVEs, addressing 129 CVEs in its September release.
Update September 10, 2020: Updated the section for CVE-2020-16875 to account for a revision made by Microsoft to the description for this vulnerability.
Microsoft patched 129 CVEs in the September 2020 Patch Tuesday release, including 23 CVEs rated critical. This month, several remote code execution (RCE) flaws in Microsoft Office products were patched. Many of these RCEs require a user to open a specially crafted document, making these vulnerabilities a growing concern for e-learning students and teachers alike as they return to school across the U.S. The patches for September include Microsoft Windows, Microsoft Edge, Microsoft ChakraCore, Internet Explorer, SQL Server, Microsoft JET Database Engine, Microsoft Office and Office Services and Web Apps, Microsoft Dynamics, Visual Studio, Microsoft Exchange Server, ASP.NET, Microsoft OneDrive and Azure DevOps.
CVE-2020-1200, CVE-2020-1210, CVE-2020-1452, CVE-2020-1453, CVE-2020-1576 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2020-1200, CVE-2020-1210, CVE-2020-1452, CVE-2020-1453, and CVE-2020-1576 are RCE vulnerabilities in Microsoft SharePoint when SharePoint fails to properly check the validity of uploaded application packages. An attacker could exploit this vulnerability by uploading a malicious application to a vulnerable SharePoint application or server. These vulnerabilities are reminiscent of CVE-2019-0604, a similar RCE which was exploited nine months after Microsoft released a patch. The same vulnerability continues to be widely used in multiple attacks and was also featured in the CISA top 10 report as one of the top vulnerabilities exploited between 2016 and 2019.
CVE-2020-16875 | Microsoft Exchange Remote Code Execution Vulnerability
CVE-2020-16875 is a remote code execution vulnerability in Microsoft Exchange Server because it does not properly validate PowerShell cmdlet arguments for Exchange. To exploit this vulnerability, an attacker would need to compromise the account of a user authenticated to the Exchange server with a specific role. Successful exploitation would allow an attacker to execute arbitrary code with the same rights as the System user. Please note that Microsoft originally provided an incorrect description for CVE-2020-16875, and it has since been updated with the correct information.
CVE-2020-1252 | Windows Remote Code Execution Vulnerability
CVE-2020-1252 is a vulnerability in Microsoft Windows because of the way objects are handled in memory. In order to exploit this flaw, an attacker would need to trick a user into opening a specially crafted application containing exploit code. Successful exploitation would give the attacker arbitrary code execution on the vulnerable system.
CVE-2020-1057, CVE-2020-1172 and CVE-2020-1180 | Scripting Engine Memory Corruption Vulnerability
CVE-2020-1057, CVE-2020-1172 and CVE-2020-1180 are vulnerabilities in Microsoft’s ChakraCore scripting engine due to the way objects are handled in memory. Exploitation of this flaw would result in memory corruption, which could result in an attacker gaining arbitrary code execution with the same system privileges as the current user. This vulnerability would be amplified if the current user has administrative privileges, because an attacker would be able to perform a variety of administrative actions, resulting in a takeover of the vulnerable system.
CVE-2020-1129 and CVE-2020-1319 | Microsoft Windows Codecs Library Remote Code Execution Vulnerability
CVE-2020-1129 and CVE-2020-1319 are vulnerabilities in the Microsoft Windows Codecs Library because of the way objects are handled in memory. To exploit the flaw, an attacker would need to create a malicious image file that is processed by a program on the vulnerable system. Once exploited, the attacker would be able to access information needed in order to compromise the system.
CVE-2020-0878 | Microsoft Browser Memory Corruption Vulnerability
CVE-2020-0878 is a vulnerability in ChakraCore, Internet Explorer 9 and 11, and Microsoft Edge (EdgeHTML-based) browsers because of the way objects are accessed in memory. Exploitation of this vulnerability would result in memory corruption, which could give an attacker arbitrary code execution on the vulnerable system with the same rights as the current user. This vulnerability would be amplified if the current user has administrative privileges, because an attacker would be able to perform a variety of administrative actions, resulting in a takeover of the vulnerable system. To exploit the flaw, an attacker would first need to plant the exploit code on a website, either by creating a new website or injecting the exploit code on another website. From there, the attacker would need to either utilize social engineering to trick their victim into visiting one of these malicious websites or wait for the users to visit a compromised website.
CVE-2020-1193, CVE-2020-1332, CVE-2020-1335, CVE-2020-1594 | Microsoft Excel Remote Code Execution Vulnerability
CVE-2020-1193, CVE-2020-1332, CVE-2020-1335 and CVE-2020-1594 are RCE vulnerabilities in Microsoft Excel because of the way the software improperly handles objects in memory. To exploit these flaws, an attacker would need to create a malicious Excel file and convince their target to open the file using a vulnerable version of Microsoft Excel either by attaching the file to an email or hosting it on a website and sending a link to their victim via instant message. Once exploited, the attacker would gain arbitrary code execution on the vulnerable system with the same rights as the current user. This vulnerability would be amplified if the current user has administrative privileges, because an attacker would be able to perform a variety of administrative actions, resulting in a takeover of the vulnerable system
CVE-2020-1218, CVE-2020-1338 | Microsoft Word Remote Code Execution Vulnerability
CVE-2020-1218 and CVE-2020-1338 are remote code execution vulnerabilities in Microsoft Word caused by the mishandling of memory objects, which would allow an attacker to execute code as the current user. To exploit this vulnerability, an attacker would be required to entice a user to open a maliciously crafted Word document. An attacker could send the malicious document as an attachment as part of a malicious email. Successful exploitation of this flaw would allow the attacker to execute scripts and perform actions with the permissions of the current user account. This could allow an attacker to take full control of a target if the current user was an administrator.
CVE-2020-0836 and CVE-2020-1228 | Windows DNS Denial of Service Vulnerability
CVE-2020-0836 and CVE-2020-1228 are denial of service (DoS) vulnerabilities within Windows Domain Name System (DNS) due to a parsing error of DNS queries. In order to exploit this issue, an authenticated attacker would need to send a crafted, malicious DNS query to an affected host, resulting in an exhaustion of resources causing the device to become unresponsive. Windows DNS was recently in the news after researchers identified a wormable RCE vulnerability that has persisted in Windows for over 17 years. Dubbed “SIGRed” (CVE-2020-1350), the vulnerability was patched in Microsoft's July 2020 Patch Tuesday update. These two new CVEs within Windows DNS highlight that attackers and researchers alike continue to target applications that have previously faced little scrutiny for security concerns.
While DoS vulnerabilities are lower severity vulnerabilities, the impact of their exploitation can be quite significant. With businesses and schools relying heavily on internet connectivity, attackers are turning to DoS attacks, a tried and true method, to cause havoc.
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains September 2020.
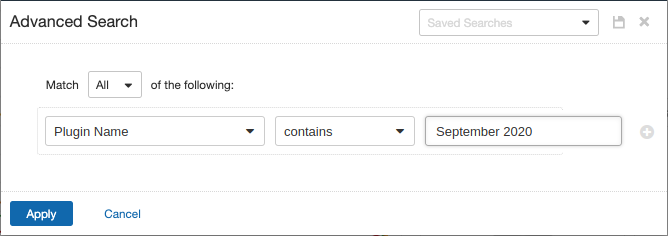
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
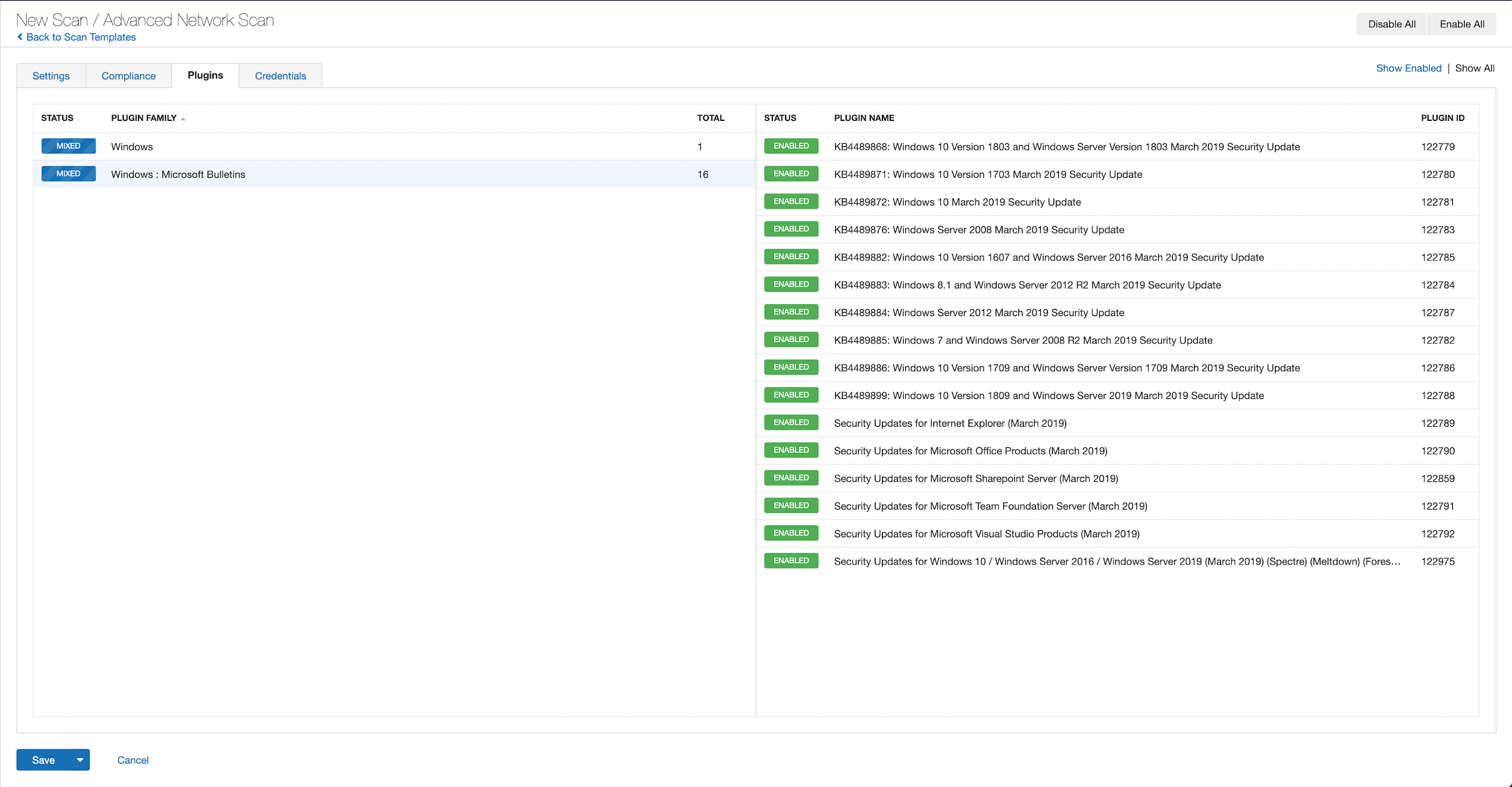
A list of all the plugins released for Tenable’s September 2020 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's September 2020 Security Updates
- Tenable plugins for Microsoft September 2020 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

