Init15: Vote for Your Favorite Tenable Enhancement (Update: Now closed)

Note: Nessus Cloud is now a part of Tenable.io Vulnerability Management. To learn more about this application and its latest capabilities, visit the Tenable.io Vulnerability Management web page.
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
Sitting on a sofa on a Sunday afternoon
Going to the candidates’ debate
Laugh about it, shout about it
When you’ve got to choose
Every way you look at it you lose
— Simon And Garfunkel
We're in the midst of campaign season here in the United States, and many people may be thinking about these Simon and Garfunkel lyrics. There are certainly times when having too many choices is a real problem.
Update: We have a winner!
Many thanks to all who voted. There were a number of projects that received many votes, and we are pleased to announce that “Remediation Prioritization (Caught With Your Pants Down)” was the winner.
Several other projects that received votes were also so well done during the three days of work at Init15 that we will be able to include them in upcoming releases as well: Nessus Cloud 2FA, SAML Authentication for Nessus Cloud (Hypersquirrel), and possibly others.
The Tenable Hackathon
Tenable’s Product Management team also has too many choices right now. Tenable just finished our Init15 hackathon, when more than twenty teams competed in a three day effort to create innovative new capabilities for Tenable products, and each team presented its project at the end of the competition. The Tenable team then voted on their favorites to determine the winning projects. For the developers, it was the end of a great week building both technologies and relationships.

But for Product Management, our work was just starting as the competition finished. We’re responsible for coordinating with developers to ensure that our products continue to deliver the solutions that our customers and partners need to help secure their networks. At the end of Init15, we found that every one of the projects provided a really valuable capability. With so many choices, what should Project Management do when you’ve got to choose?
That’s where you come in.
Vote!
Listed here are twenty of the projects that were created and presented at Init15 (there were several others dealing with internal-only capabilities like QA automation that, while very useful, are not presented here). We want to hear from you on which projects you’d like to see added to our products. Follow the link below to a SurveyMonkey form to vote for your favorite. We’ll collect votes until Monday August 24; then we’ll tally the results and update our roadmap and this blog with the 3 winning projects. Until then, good luck choosing!
So you got to let me know
Should I stay or should I go?
— The Clash
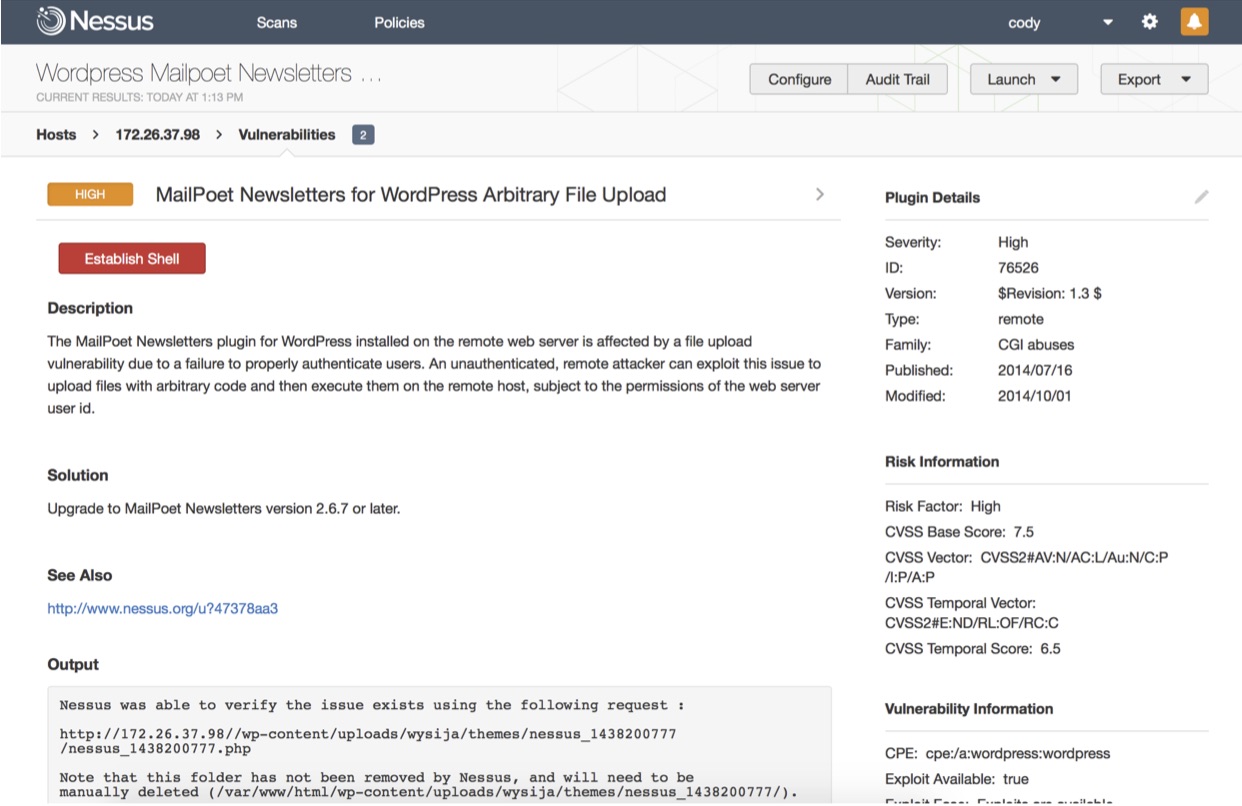
Project 1 – Nessus Exploit Simulator
Nessus is able to test for the presence of exploitable vulnerabilities; the Nessus Exploit Simulator takes this one step farther by providing a Establish Shell button.
Project 2 – SAML Authentication for Nessus Cloud (Hypersquirrel)
A micro-services based architecture that lets customers use SAML authentication services (such as Okta) for access to Nessus Cloud.
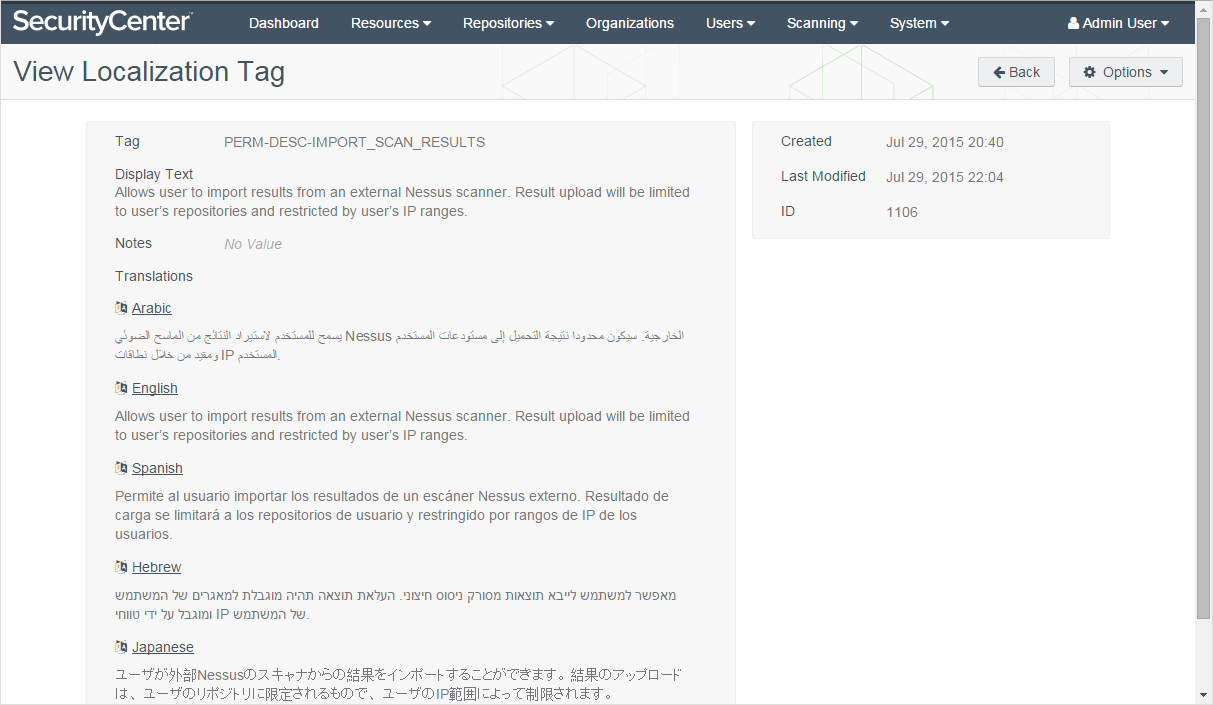
Project 3 –Localization Tools (Ten-abel Fish)
A framework to enable easy translation of product content and UIs into local languages.
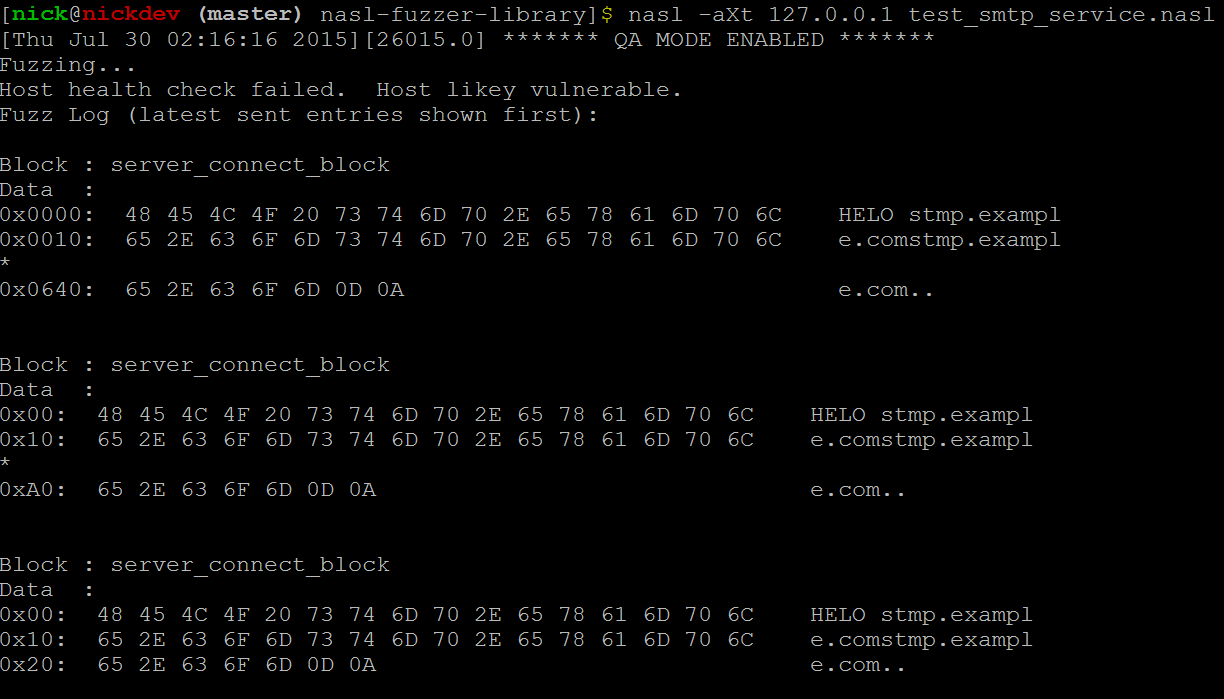
Project 4 – NASL Fuzzer Plugin
A plugin for Nessus that provides fuzzing capabilities to find problems with input validation and handling.
Project 5 – Web Application Inventory (Eye of Providence)
A plugin for Nessus that determines web application inventory and versions using non-traditional techniques.
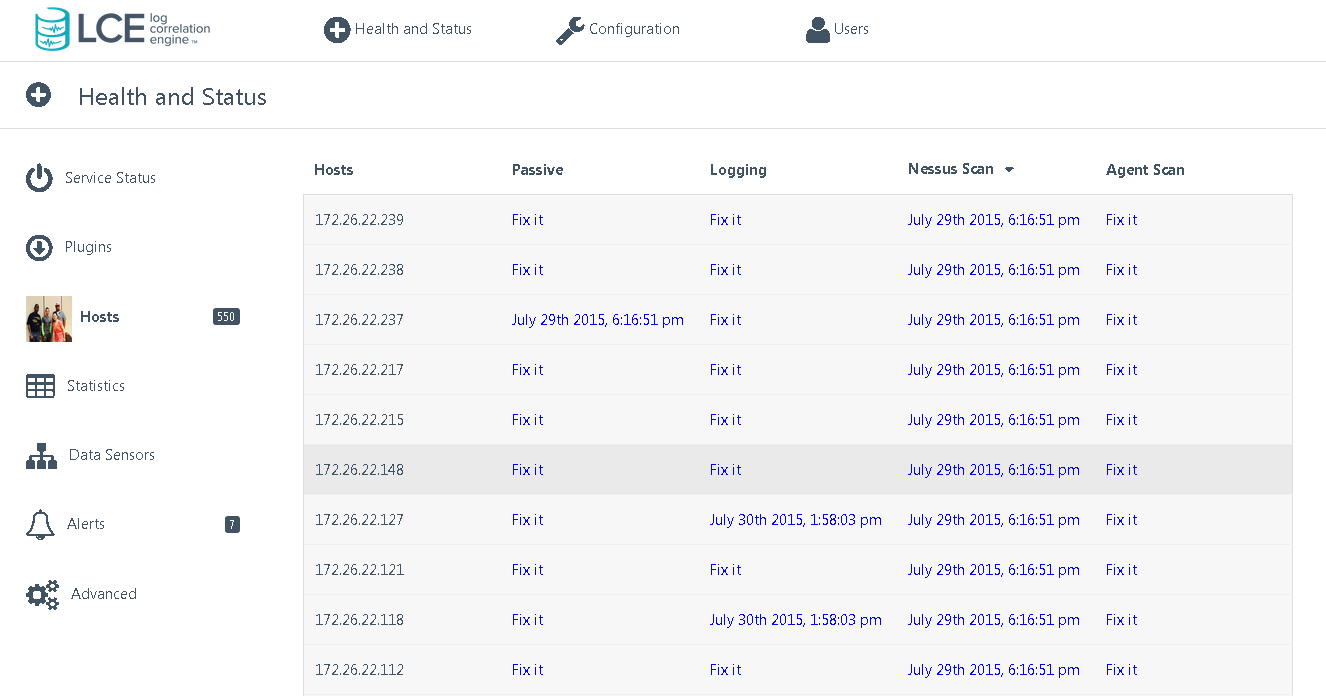
Project 6 – Integrated Asset Discovery (Cover Your Assets)
Enhancements in SecurityCenter to show the coverage of detected assets by various techniques including active scanning, passive detection, and log analysis. Includes a Fix Now button to add coverage.
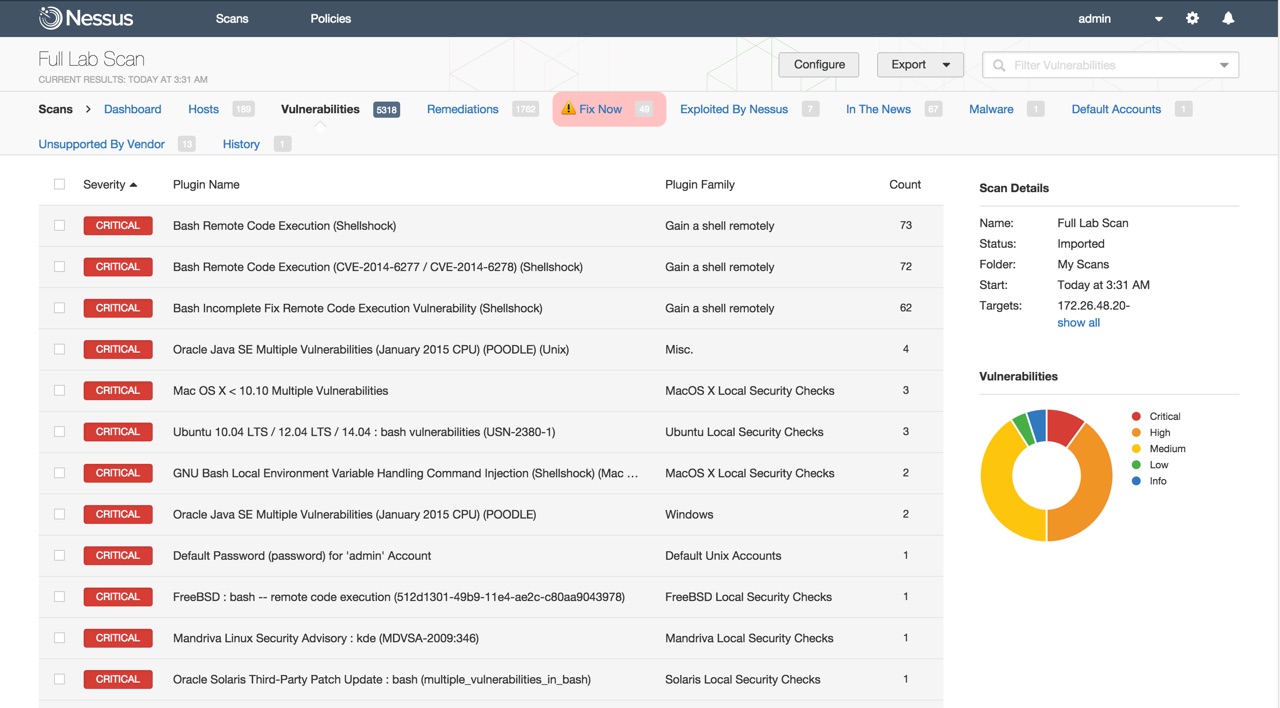
Project 7 – Remediation Prioritization (Caught With Your Pants Down)
Filtering capabilities in Nessus that show the most important vulnerabilities to fix – those with exploits in the wild, etc. – so that remediation efforts can be prioritized.
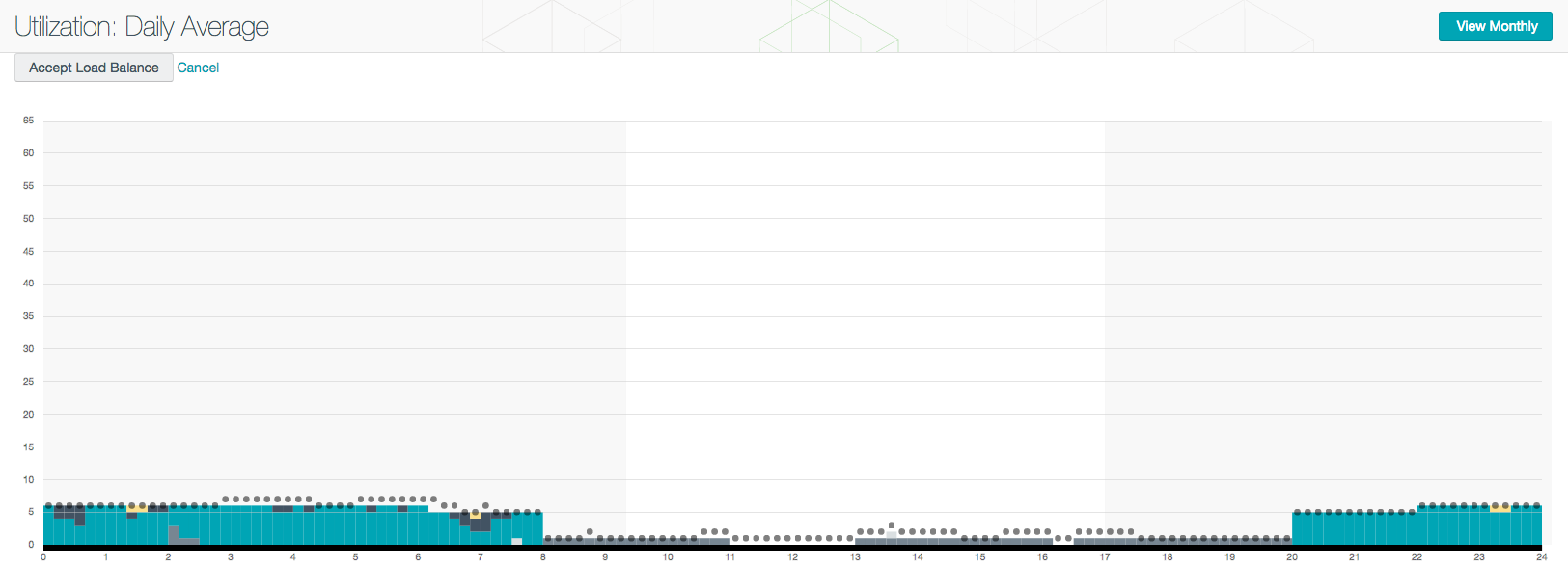
Project 8 – SecurityCenter Schedule Load Distribution (Poseidon’s Lullaby)
A tool to distribute the load of various SecurityCenter processes (scanning, dashboard calculations, etc.) evenly over time.
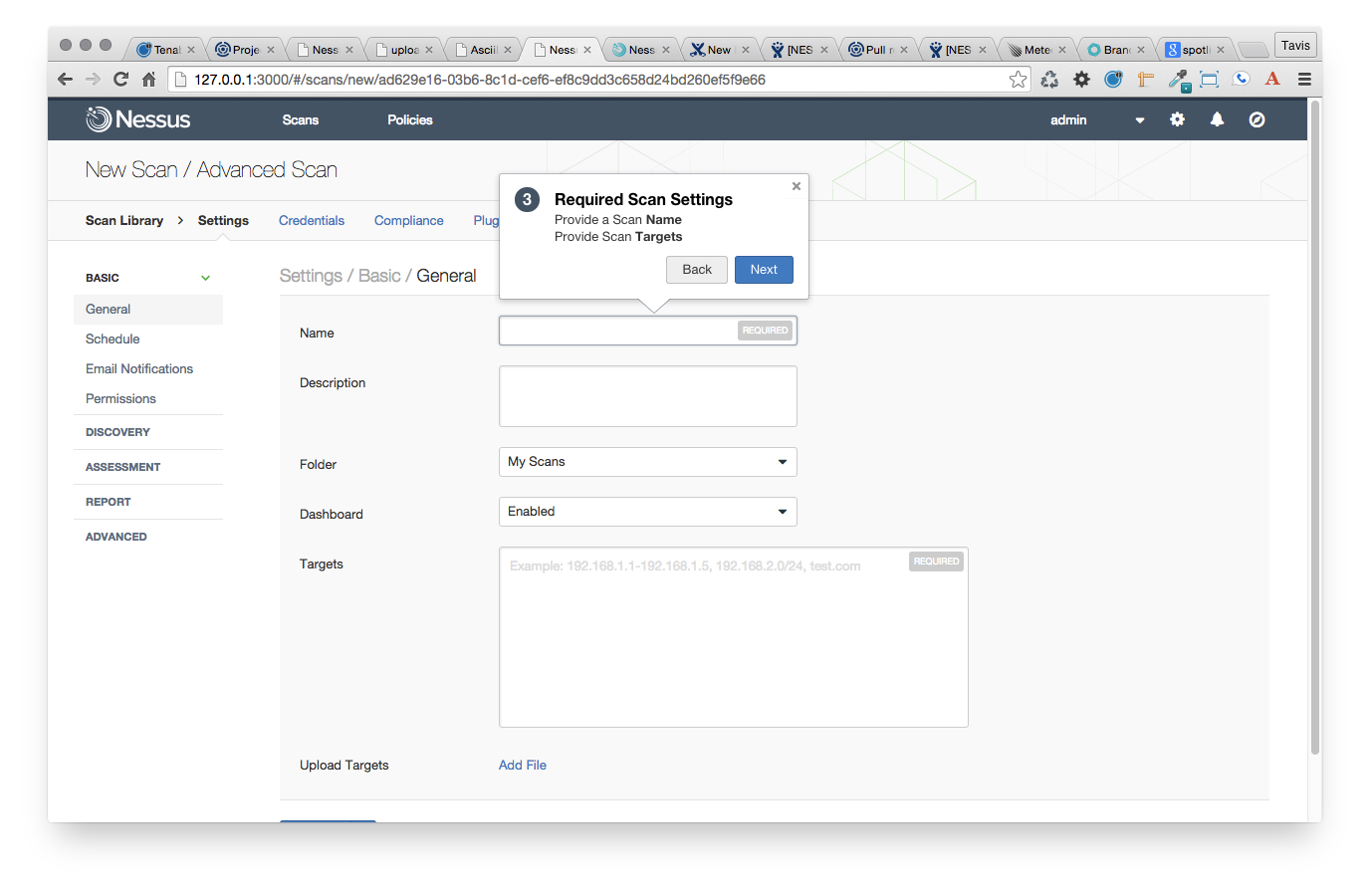
Project 9 – Task Wizards (Nessus Feature Tours)
A step-by-step walkthrough to accomplish tasks in Tenable products, guided by in-product pop-up notes.
Project 10 – Community Ratings (FATE)
A mechanism for customers to create and share ratings for templates, dashboards, etc., inside Tenable products.
Project 11 – User Behavior Analytics
Machine-based learning that evaluates user behavior gleaned from scans, logs, and network activity. Anomalous activity can be identified and then highlighted for follow-up.
Project 12 – Enhanced Nessus Plugin Search
Enhancements to the Nessus Plugin Search page to enable searching by multiple complex criteria.
Project 13 – Compliance Baselines
A capability to create a “baseline” out of compliance scan results, and then compare future scans for changes against the baseline.
Project 14 – Honeypot Analysis
A system for using honeypots to prioritize scan findings and assist with the creation of plugins for new vulnerabilities.
Project 15 –Raspberry Pi PVS (Minion PVS)
A PVS architecture that separates data collection, data analysis, and reporting into unique components. The data collection component can be run on a $35 Raspberry Pi.
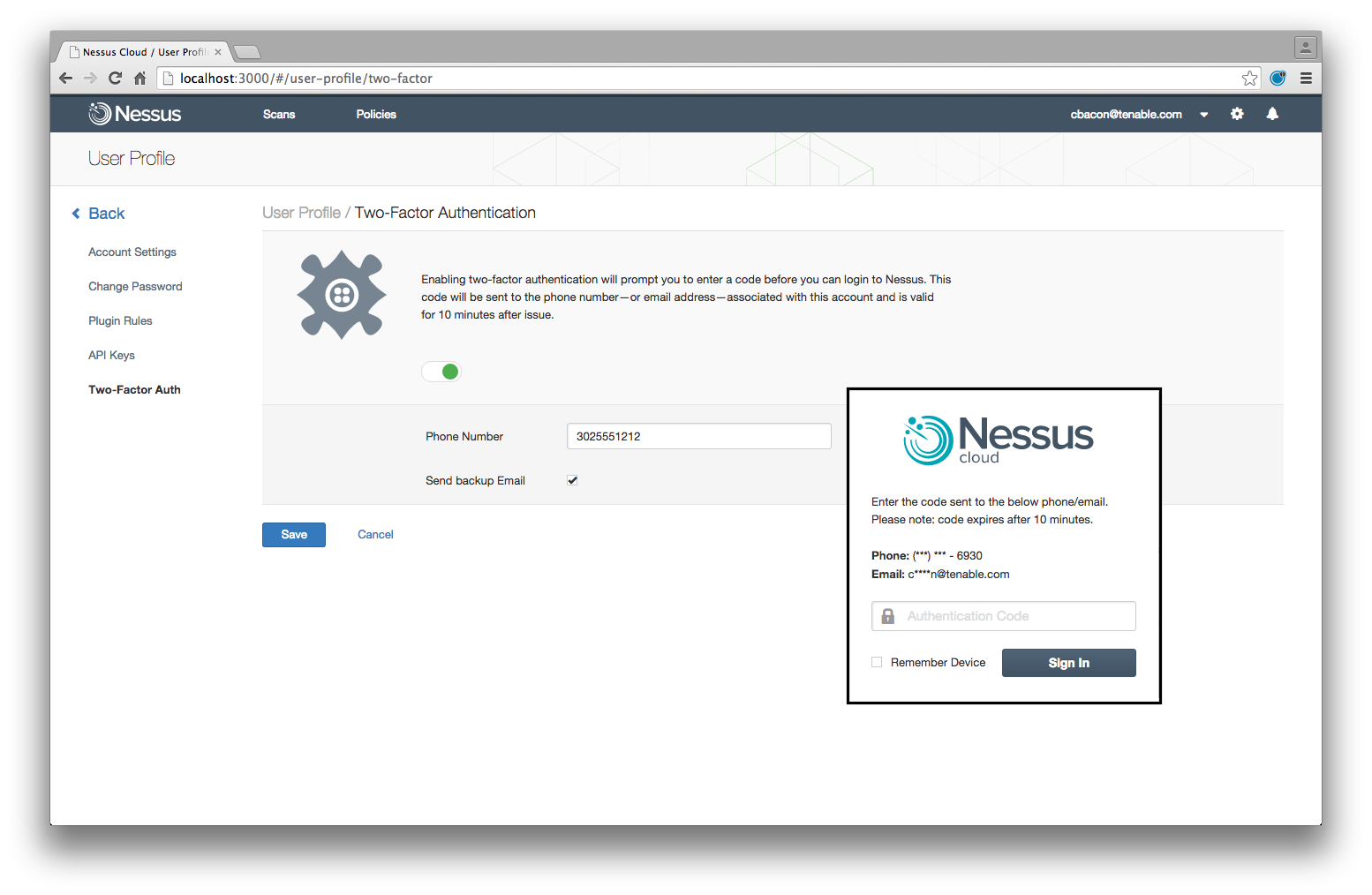
Project 16 – Nessus Cloud 2FA
Two-factor authentication for Nessus Cloud using Twilio and SMS.
Project 17 – Fortinet PCap-Based PVS
Integration between Fortinet device’s pcap capabilities and PVS, enabling the capture of traffic without requiring a span port.
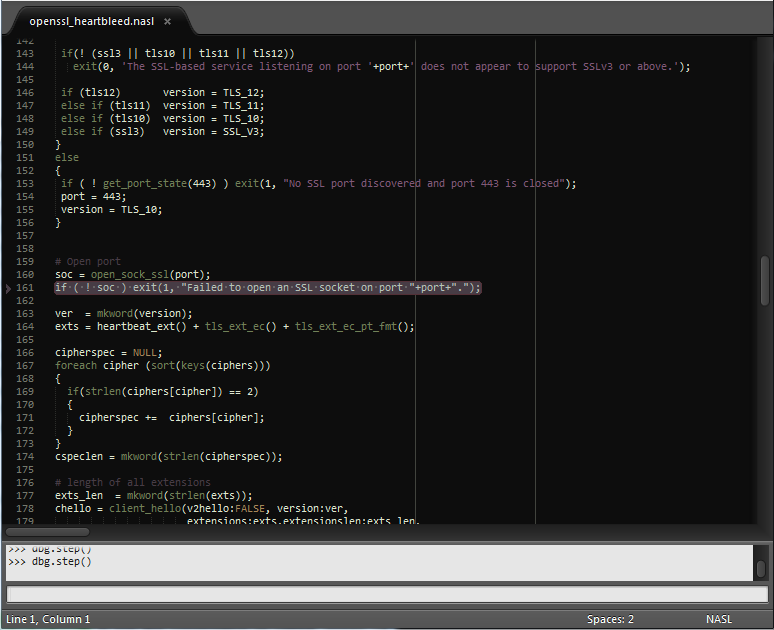
Project 18 – NASL Debugger (FANG)
A NASL debugger supporting breakpoints, step-by-step execution, and a Sublime-based UI.
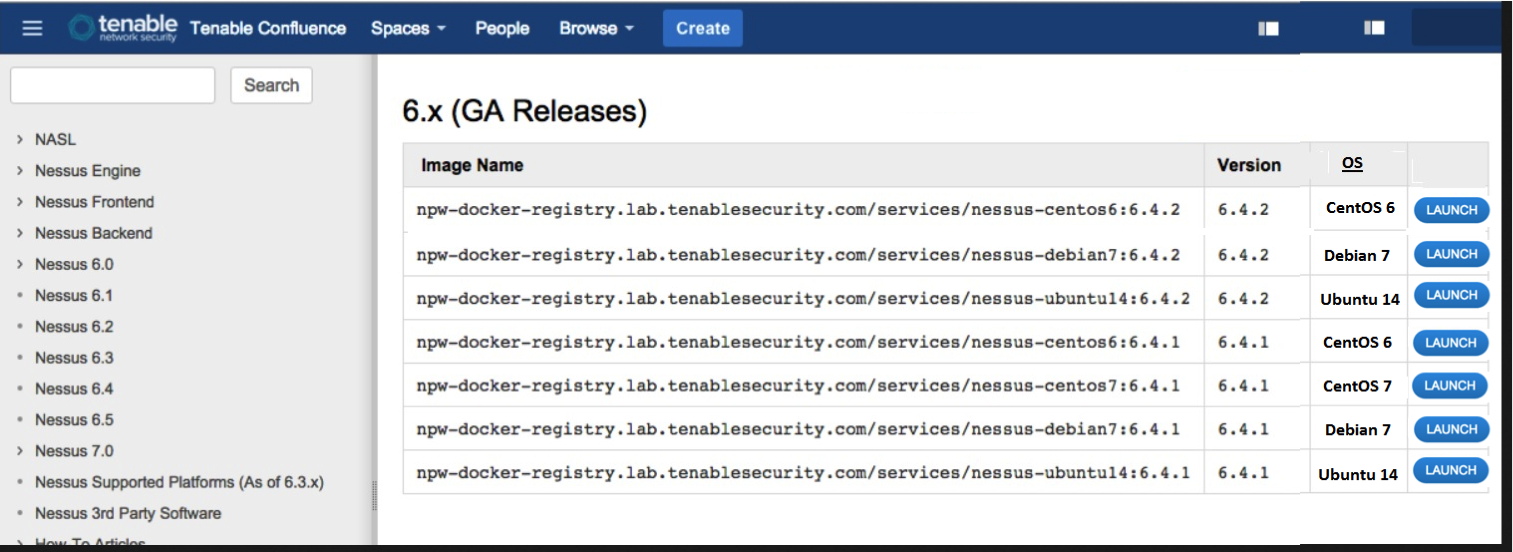
Project 19 – Nessus in Docker (Terminus)
A Docker repository with ready-to-use versions of Nessus.
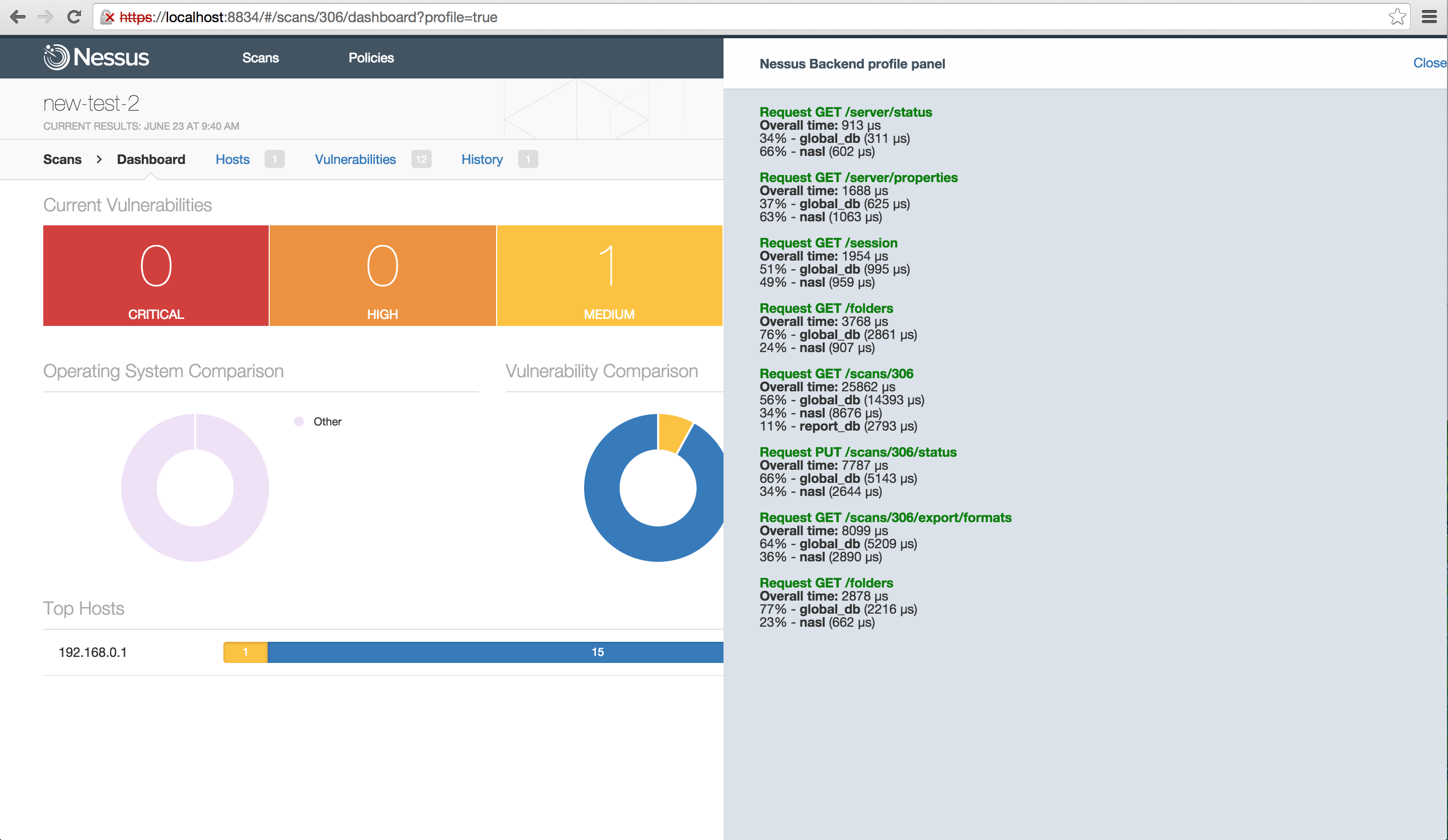
Project 20 – Nessus Profiling/Tracing
A profiler and tracing facility for Nessus to debug and improve front end/back end communications.
- Announcements
- Events
- Nessus
- Nessus Network Monitor
- SecurityCenter