IDC Ranks Tenable Number One in the Worldwide Vulnerability Management Market Share for 2019

IDC’s first-ever market share report for the worldwide device vulnerability management market ranks Tenable as #1 in market share for 2019 and credits the company for extending its reach far beyond vulnerability management.
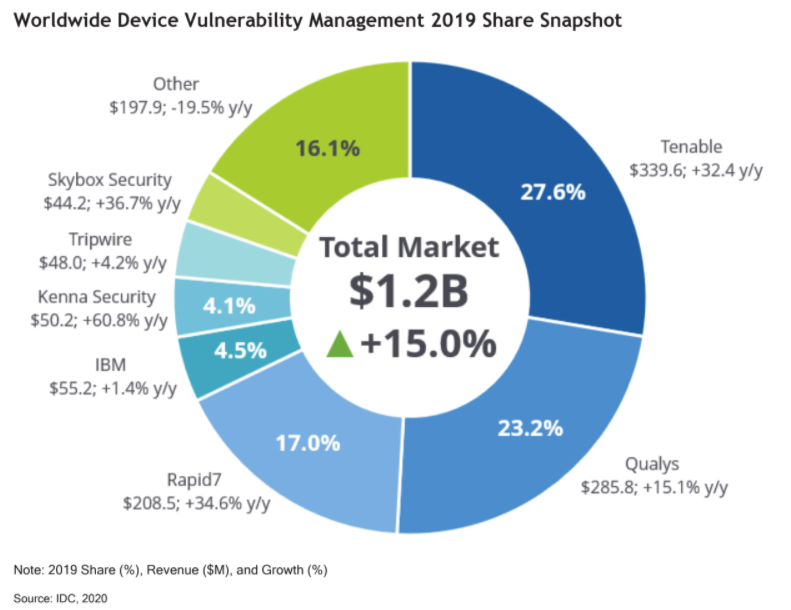
IDC recently published their Worldwide Device Vulnerability Management Market Shares, 2019: Finding the Transitional Elements Between Device Assessment Scanning and Risk-Based Remediation (May 2020) report to highlight the most prominent VM providers in the world. The report ranks Tenable as #1 in market share and revenue for the past two years.
IDC credits Tenable’s success to a number of key elements, including:
- The ability to deliver broad visibility across the modern attack surface, including IT, operational technology (OT) and cloud environments
- The expertise to help organizations quantify cyber risk, prioritize remediation decisions and benchmark against peers
- A research team that plays an integral part in supporting Tenable customers through threat intelligence, vulnerability detections and security alerts
CVSS alone is failing you
While v3 of the Common Vulnerability Scoring System (CVSS) has certainly made some improvements over past versions, IDC acknowledges that it’s still problematic, stating that, “a CVSS score provides a one-dimensional representation of a multidimensional problem.” At Tenable, we couldn’t agree more.
CVSS is risk-unaware. Since most CVSS scores are assigned within two weeks of vulnerability discovery, the score only employs a theoretical view of the risk a vulnerability could potentially introduce. That leads security teams to waste the majority of their time chasing after the wrong issues while missing many of the most critical vulnerabilities that pose the greatest risk to the business.
Instead, security teams must understand the full context of each vulnerability. In addition to the CVSS score, Tenable correlates and analyzes other essential contextual data, including threat and exploit intelligence, an assessment of asset criticality and continuous analysis of a 4.5 petabyte data lake that includes more than 20 trillion threat, vulnerability and asset data points. All of this data is processed using machine learning automation to render an accurate risk score for every vulnerability within seconds.
Armed with the full context of each vulnerability, security teams are able to take decisive action to reduce the greatest amount of business risk with the least amount of effort.
World-class research enables companies to predict the risks that matter most
In highlighting Tenable’s vast research capabilities, IDC acknowledges the crucial synergies of integrating technology with research to inform customer decisions. Tenable research certainly fulfills this need. According to the report, “Tenable has written over 141,000 plug-ins encompassing more than 56,000 CVE and 30,000 Bugtraq IDs. Tenable Research satisfies the criteria of 126 CIS Benchmarks.”
Tenable processes over 1.5 billion instances of vulnerabilities per week and analyzes exposure trends from more than 4.5 petabytes of data. Our machine learning algorithms predict which vulnerabilities are most likely to be exploited in the near future and assign Vulnerability Priority Ratings (VPR) and Asset Criticality Ratings (ACR) accordingly. The VPR is calculated based on what we can determine about the vulnerability itself, as well as what we see in the current threat environment. The ACR is a calculation of how important the asset is to the organization, so it’s highly customized to each customer. Predictive Prioritization is then applied to both ratings to help customers prioritize remediation efforts based on actual business risk, determine their cyber risk reduction over time and benchmark their level of cyber exposure against industry peers.
Traditional IT assessments leave blind spots
In addition to traditional IT assets, the modern attack surface also includes OT, web apps, cloud and container environments, creating a cyber exposure gap that’s being exploited by attackers. All of these environments contain vulnerabilities, and adversaries routinely scan the entire attack surface to find the easiest way in. Yet, legacy vulnerability management methods are limited to scanning traditional IT environments, so cloud and OT assets — and the vulnerabilities that reside on them — remain invisible to the organization.
IDC credits Tenable for extending its visibility far beyond traditional assets to include broad coverage and thorough assessments of an organization’s entire attack surface. By assessing modern assets as well as traditional on-premises IT environments, Tenable eliminates the blind spots that plague legacy tools and enables security teams to discover and assess all of their vulnerabilities in a unified platform. As a result, users can determine which vulnerabilities to prioritize for remediation based on the risk they pose to the organization — regardless of where they reside.
In addition, IDC points out that Tenable can secure and harden Docker and Kubernetes environments against CIS Benchmarks, and is integrated into CI/CD pipelines to quickly assess new container image builds for vulnerabilities and malware to prevent security issues from reaching production.
Comprehensive risk-based VM solution
Tenable helps customers evolve from legacy vulnerability management programs — which are interrupt-driven and error-prone — to a more proactive and strategic approach. Legacy VM is limited to discovering and assessing vulnerabilities. But Tenable solves the higher-order challenge of helping organizations effectively prioritize what matters most, calculate key metrics, compare their progress against industry standards and determine when and where to make adjustments to optimize their strategy. Clear reporting also enables teams to build and maintain management’s confidence in their capabilities and prevent panic mode when high-profile exploits occur.
To highlight the value of this comprehensive approach, IDC points to Tenable Lumin® which enables customers to calculate, communicate and compare their cyber risk. Lumin helps them understand vulnerabilities in the context of business risk and use that intelligence to prioritize the team’s efforts so they can focus first on the vulnerabilities and assets that matter most. In IDC’s words, “Lumin is used to establish an assessment of a company's overall security posture, industry benchmarking, and how a company's posture improves with certain remediation measures.”
Want to learn more? Download the IDC report excerpt now.
- Vulnerability Management


