Cybersecurity Snapshot: As ChatGPT Concerns Mount, U.S. Govt Ponders Artificial Intelligence Regulations

As ChatGPT security worries rise, the Biden administration looks at crafting AI policy controls. Plus, Samsung reportedly limits ChatGPT use after employees fed it proprietary data. Also, how password mis-management lets ex-staffers access employer accounts. In addition, the top identity and access management elements to monitor. And much more!
Dive into six things that are top of mind for the week ending April 14.
1 – Amid growing ChatGPT agita, White House mulls AI rules
With no end in sight to the world’s fascination with generative AI chatbots like ChatGPT, the Biden administration is considering creating “guardrails” to protect American citizens from artificial intelligence abuses.
This week, the National Telecommunications and Information Administration (NTIA), which advises the White House on telecom and information policy issues, announced it is seeking public comments about “AI accountability.”
The comments will help the Biden administration develop policies via “AI audits, assessments, certifications and other mechanisms” to promote trust in AI systems and ensure they work as intended and without harming people.
“Companies have a responsibility to make sure their AI products are safe before making them available,” reads the NTIA’s announcement.

That straightforward declaration touches on key questions raised repeatedly since the release in recent months of OpenAI’s ChatGPT and other generative AI chatbots: Were they released to the public prematurely? Is the world unprepared to deal with the consequences of abuse and misuse of these products’ powerful capabilities?
Examples of topics the NTIA is interested in include: What trust and safety testing should AI system developers conduct? How can regulators encourage accountability among AI system developers?
To get more details, you can go to the NTIA’s “AI Accountability Policy Request for Comment” main page and read the full document.
For more information about regulatory efforts around ChatGPT and generative AI:
- “UK regulator: How using ChatGPT can break data privacy rules” (Tenable)
- “Italy became the first Western country to ban ChatGPT. Here’s what other countries are doing” (CNBC)
- “As ChatGPT Fire Rages, NIST Issues AI Security Guidance” (Tenable)
- “ChatGPT is entering a world of regulatory pain in Europe” (Politico)
- “Governments worldwide attempting to regulate generative AI” (TechTarget)
VIDEOS
After Italy blocked access to OpenAI's ChatGPT chatbot, will the rest of Europe follow? (Euronews Next)
The potential dangers as AI grows more sophisticated and popular (PBS NewsHour)
2 – And another reminder that ChatGPT keeps no secrets
It’s been a regular warning: Don’t enter confidential information into ChatGPT because all the data users input into it gets ingested into its vast data store. Once there, the AI chatbot could use it to answer other users’ questions.
Well, now we have a real-world example of this faux-pas: Samsung employees reportedly fed the AI chatbot private, sensitive information about the company, including proprietary source code and meeting minutes.
That’s according to the South Korean edition of The Economist magazine, which reported that, in response, the consumer electronics titan is now limiting ChatGPT use.
For more information about privacy concerns related to ChatGPT:
- “Samsung may be 'limiting' use of ChatGPT for employees, here’s why” (Times of India)
- “A major bank has banned ChatGPT—should your company follow suit?” (Fortune)
- “Amazon Begs Employees Not To Leak Corporate Secrets To ChatGPT” (Futurism)
- “ChatGPT Has a Big Privacy Problem” (Wired)
- “ChatGPT is a data privacy nightmare, and we ought to be concerned” (Ars Technica)
VIDEOS
NCSC Raises Privacy Concerns About ChatGPT (Tenable)
CEO behind Chat GPT-4 says he's 'a little bit scared' by AI (ABC News)
3 – What’s your No. 1 worry? How do you prioritize bug patching?
Those were two of the questions we asked participants in our recent webinar, “Tenable Research Shares Its 2022 Recap and Defender Recommendations for 2023,” in which Tenable experts discussed the recently published “Tenable 2022 Threat Landscape Report.” Check out how respondents answered.
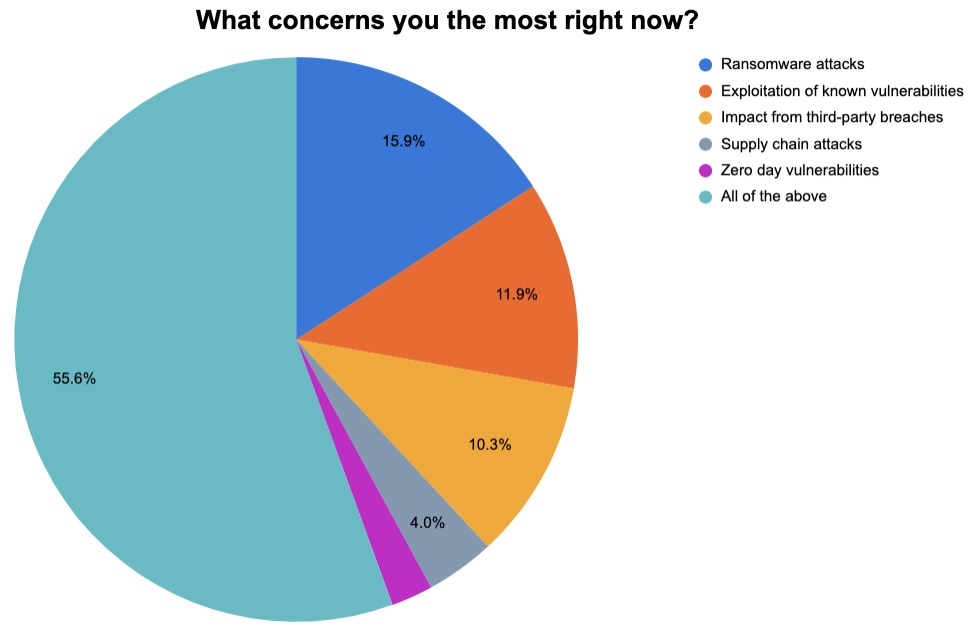
(Source: 126 webinar participants polled by Tenable, March 2023)
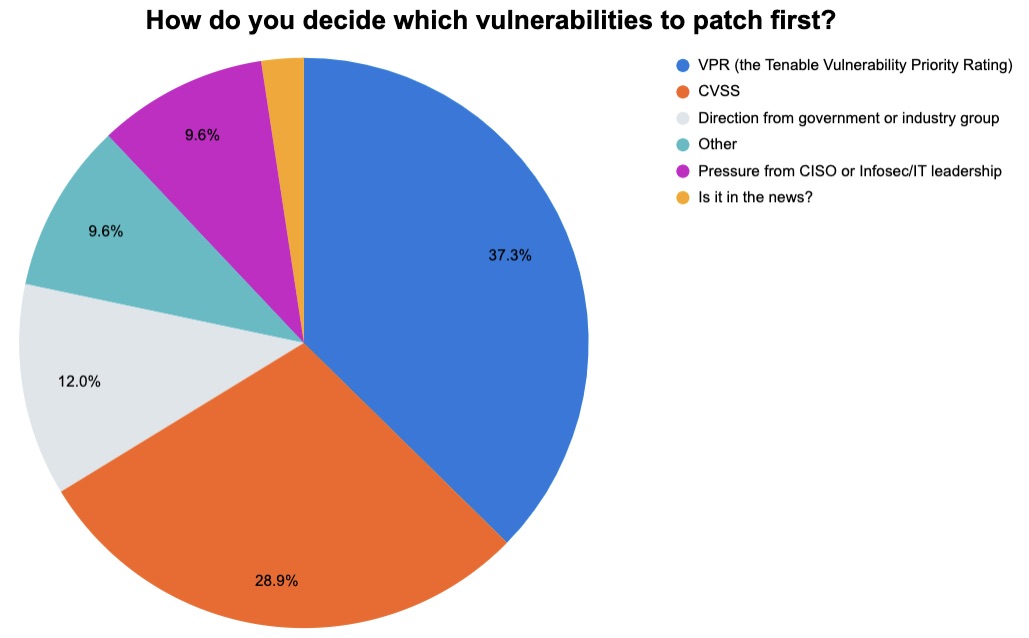
(Source: 83 webinar participants polled by Tenable, March 2023)
For more information about the “Tenable 2022 Threat Landscape Report” check out:
- Download the full report
- Watch the on-demand webinar
- Read the blog “Reduce Your Exposure by Tackling Known Vulnerabilities”
- Watch this Ticker Insight interview with Tenable Senior Staff Research Engineer Satnam Narang
4 – It’s a password problem: People using ex-employers’ accounts
Could your business unwittingly be giving former employees access to its paid subscription services, commercial software, email inboxes and other digital resources? Apparently, it happens more often than one would think, and bad password management is to blame.
That’s according to a survey from Password Manager which found that 47% of U.S. employees have tapped into at least one of their former employers’ digital accounts. These former staffers use passwords they had when they worked there; get them from a current employee; or simply guess them.
What do they do? Many mooch their ex-employers’ paid tools, and some even maliciously tinker with their systems and data.
Password Manager, a website that rates and compares password managers, hired Pollfish to survey 1,000 U.S. respondents who’ve had access to employer passwords within the past five years.
How were you able to access your former employers’ passwords?
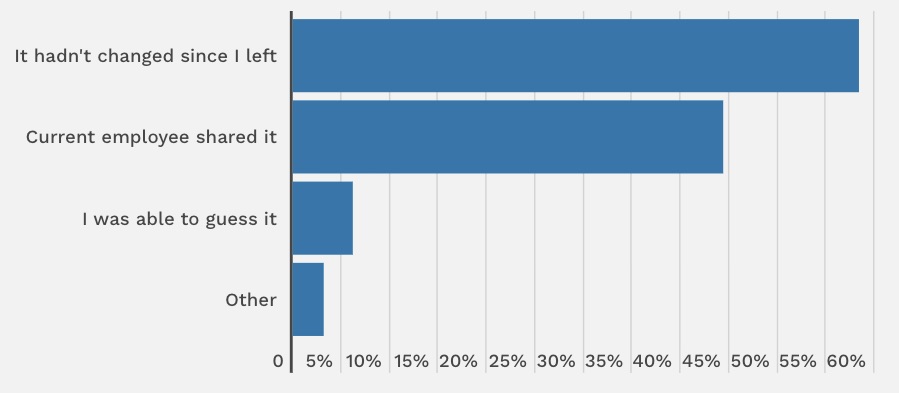
(Source: Password Manager survey, April 2023)
And it gets worse: Among those who’ve used former employers’ passwords, only 15% said they’ve been caught doing it, and one-third said the passwords worked for more than two years – including a small percentage who used them for 10-plus years.
For how long were you or have you been using former employers’ passwords?
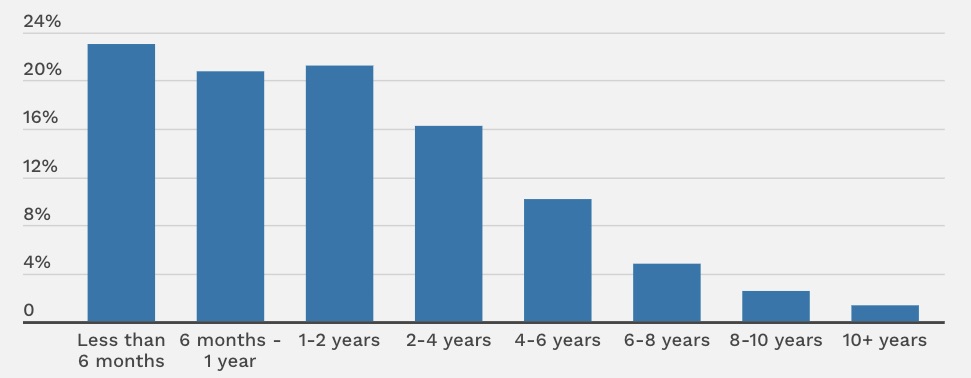
(Source: Password Manager survey, April 2023)
The motivation for the majority of these ex-staffers is saving money on tools and services they’d otherwise have to pay for (58%), while others – around 10% – want to disrupt a former employer’s operations.
The bottom line: Companies need to get better at managing their passwords. Among Password Manager’s recommendations are:
- Appoint a senior-level staffer to be in charge of password-management policies and processes
- Starting during onboarding, spell out to employees what’s considered authorized and non-authorized handling of intellectual property and proprietary information
- Create incentives for managing passwords and company accounts properly
- Continuously update your inventory of password-protected assets, and rate their criticality
- Create standard operating procedures and schedules for updating passwords
For more information about password management best practices for businesses:
- “Enterprise password security guidelines in a nutshell” (TechTarget)
- “Choosing a Password Manager for Business: 8 Features to Look For” (Techopedia)
- “How password management tools are helping enterprises prevent intrusions” (VentureBeat)
5 – Adopting a zero-trust architecture? Check CISA’s revised model
If you’re evaluating or already implementing a zero-trust architecture, you might want to check out the newest version of the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) “Zero Trust Maturity Model – Version 2.0” (ZTMM), published this week.
In the ZTMM, CISA identifies five pillars for implementing a zero-trust architecture – identity, devices, networks, applications/workloads and data – underpinned by the principles of visibility/analytics, automation/orchestration and governance.
The agency also outlines four stages of zero-trust maturity: traditional, initial, advanced and optimal. The initial stage was added to the ZTMM in version 2.0, which provides “a gradient of implementation” across the five pillars. Version 2.0 of the ZTMM also adds several new and updated zero-trust functions.
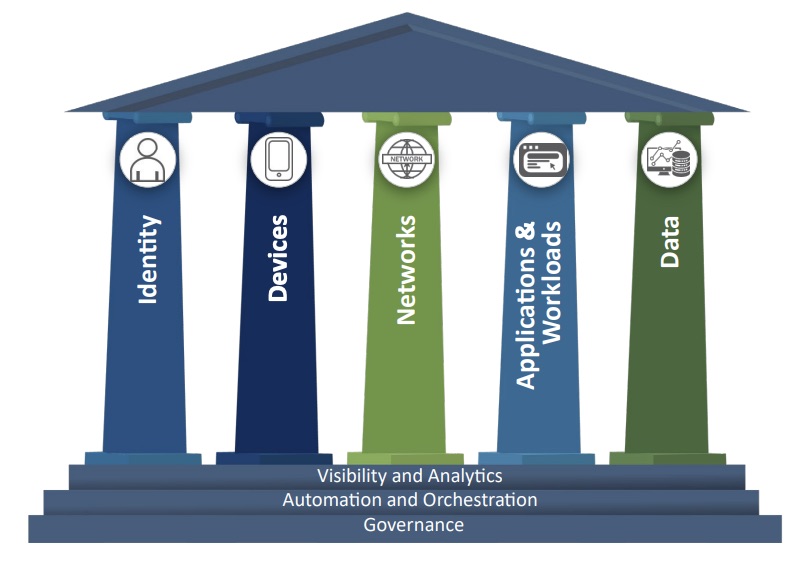
(Source: CISA’s “Zero Trust Maturity Model – Version 2.0,” April 2023)
The CISA guide builds upon these seven “tenets” of zero trust outlined by the U.S. National Institute of Standards and Technology (NIST):
- Consider as resources all data sources and computing services
- Secure all communication regardless of network location
- Grant access to individual resources on a per-session basis
- Determine access to resources by dynamic policy
- Monitor and measure the integrity and security posture of all owned and associated assets
- Strictly and dynamically enforce the authentication and authorization of all resources before access is allowed
- Collect as much information as possible about the current state of assets, network infrastructure and communications and use it to improve your security posture
For example, here’s how a zero-trust architecture would look like in the optimal stage of maturity.
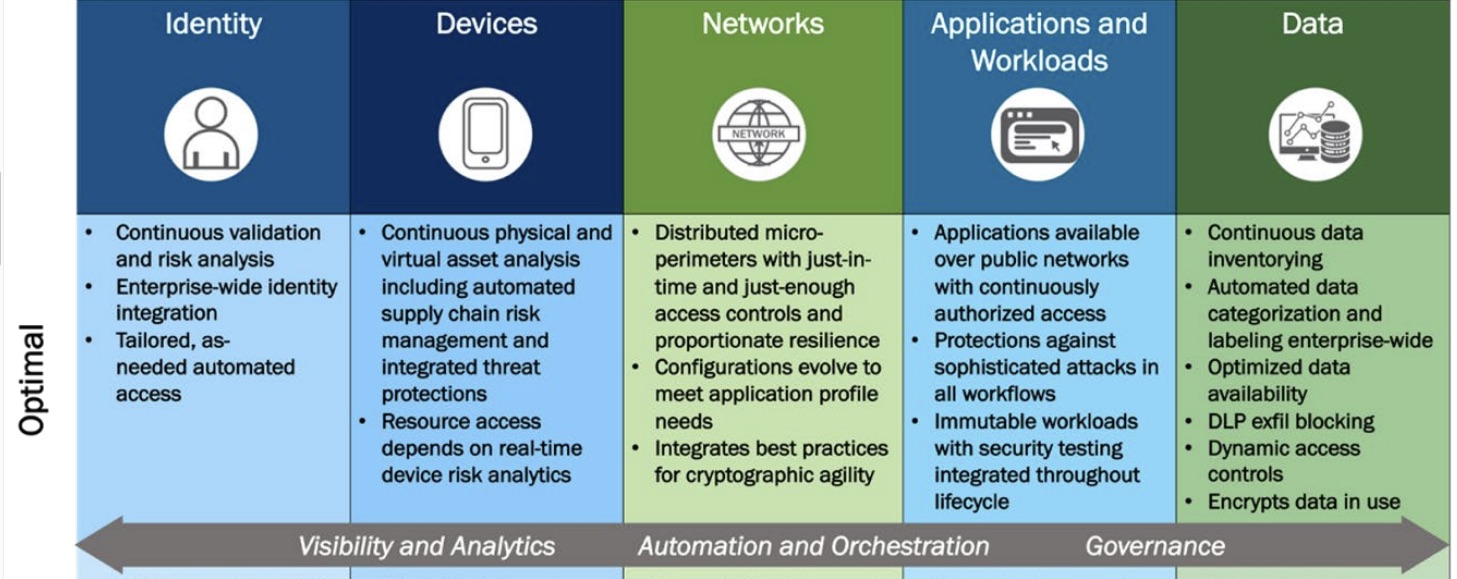
(Source: CISA’s “Zero Trust Maturity Model – Version 2.0”, April 2023)
For more information, read CISA’s “Zero Trust Maturity Model – Version 2.0” and “Applying Zero Trust Principles to Enterprise Mobility,” as well as the Office of Management and Budget’s Federal Zero Trust Strategy and NIST’s “Implementing a Zero Trust Architecture.”
6 – Cloud Security Alliance: Top IAM attributes to monitor
Since the importance of protecting identity and access management (IAM) systems can’t be stressed enough, here’s a quick overview of the Cloud Security Alliance’s (CSA) “top 7 attributes to monitor,” as outlined in its recent blog “Configuration and Monitoring of IAM.”
- User identities, including the accuracy of user information, such as names, roles and group memberships
- Permission grants, to ensure the permissions match users’ roles and responsibilities
- Session management, to verify that user sessions are terminated in a proper and timely manner
- Logs and audit trails, in order to record and track all access to sensitive data and systems
- IAM configuration, including verifying the accuracy of authentication methods and access control policies
- Service accounts and resource accounts, to ensure that users can’t use these “service principals” accounts to access any resources
- Programmatic access, to check for unauthorized access and misuse of APIs, roles and machine identities

For more information about IAM security, check out these Tenable resources:
- “Active Directory Vulnerabilities: How Threat Actors Leverage AD Flaws in Ransomware Attacks” (blog)
- “How Automated Discovery of AD Threats Eliminates Blind Spots and Makes Your SOC Identity Aware” (on-demand webinar)
- “Eliminating Attack Paths in Active Directory: A closer look at preventing privilege escalations” (white paper)
- “The Top 10 Active Directory Security Questions CISOs Must Ask” (blog)
- “Adopt a Proactive Process for Detecting and Preventing Critical Attack Paths in AD” (on-demand webinar)
- Active Directory
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Legislation
- Vulnerability Management



