CVE-2024-0204: Fortra GoAnywhere MFT Authentication Bypass Vulnerability

Proof-of-concept exploit details are available for a newly disclosed critical vulnerability in Fortra GoAnywhere Managed File Transfer (MFT), a product historically targeted by ransomware
Background
On January 22, Fortra (formerly HelpSystems) published a security advisory (FI-2024-001) for a critical vulnerability in GoAnywhere, its managed file transfer (MFT) software.
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2024-0204 | Fortra GoAnywhere MFT Authentication Bypass Vulnerability | 9.8 |
According to the advisory, it was discovered on December 1, 2023. Its discovery is credited to security researchers Mohammed Eldeeb and Islam R Alater. A patch for this vulnerability was released on December 7, though the advisory was not made public until January 22.
we @IslamRalsaid1 got some zero-days vulnerabilities in "goanywhere" product, patch your instance ASAP#0day #bugbounty pic.twitter.com/pazqDpYKmZ
— mohammed eldeeb (@malcolmx0x) December 5, 2023
Analysis
CVE-2024-0204 is an authentication bypass vulnerability in Fortra’s GoAnywhere MFT software. An unauthenticated, remote attacker could exploit this vulnerability by sending a specially crafted request to a vulnerable GoAnywhere MFT instance. Successful exploitation would allow an attacker to bypass authentication to create new users, including a user with administrator privileges.
Based on Tenable’s telemetry as of January 23, 96.4% of GoAnywhere MFT assets are using an affected version, while 3.6% are using a fixed version.
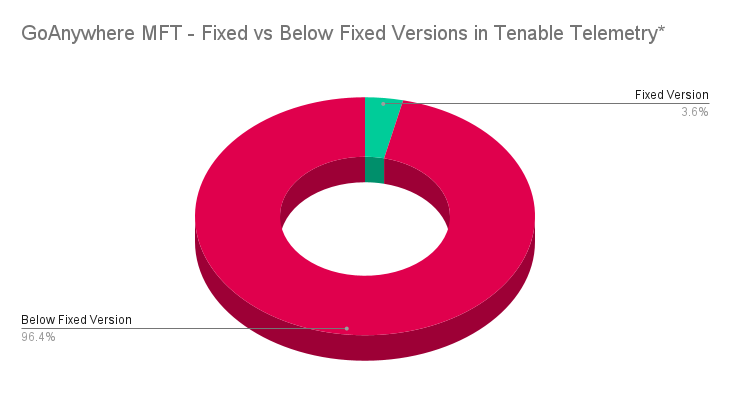
*The figures presented in this chart are representative of a data snapshot on January 23, 2024.
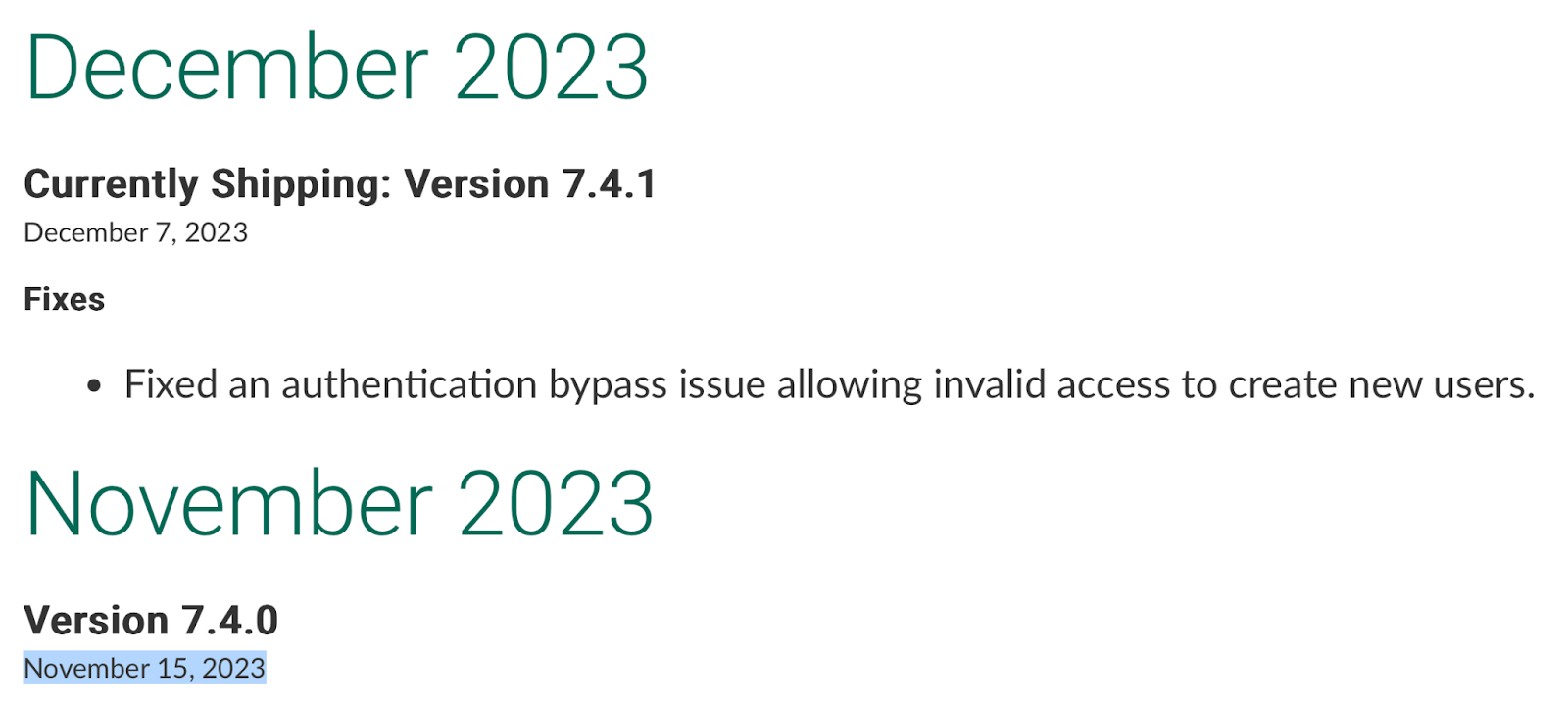
Despite being released on November 15, only 1.6% of assets in Tenable’s telemetry are using GoAnywhere 7.4.0.
Historical targeting of GoAnywhere MFT and Clop’s penchant to target MFTs
In late January 2023, CVE-2023-0669, a zero-day command injection vulnerability in GoAnywhere MFT was exploited by the Cl0p ransomware group to steal data from organizations, which were used for extortion. The group claims they stole data from “over 130 organizations” using the flaw.
The Cl0p ransomware group has consistently targeted file transfer solutions as part of their ransomware campaigns over the last three years including several flaws in Accellion’s File Transfer Appliance (FTA) in late 2020/early 2021, CVE-2023-0669 in Fortra’s GoAnywhere MFT in January 2023 and CVE-2023-34362 in Progress Software’s MOVEit Secure MFT in May 2023.
The attacks by Cl0p gained attention from The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) who issued a joint cybersecurity advisory for CVE-2023-34362 (AA23-158A) in June as part of their #StopRansowmare campaign.While researchers were credited with discovering CVE-2024-0204, it is not out of the realm of possibility that Cl0p or another ransomware group may adopt this flaw in conducting attacks against vulnerable organizations. We strongly encourage affected customers to apply the available patch as soon as possible.
Public proof-of-concept exploit available for CVE-2024-0204
On January 23, researchers at Horizon3.ai published a blog post analyzing CVE-2024-0204. The blog post also includes a proof-of-concept (PoC) for the vulnerability.
Ease of exploitation of CVE-2024-0204 is considered relatively easy. On Mastodon, security researcher Kevin Beaumont says the flaw is “incredibly easy to exploit” adding that it is a “1998 style” path traversal flaw.
With the availability of a PoC, we anticipate exploit scanning to begin soon, followed by in-the-wild exploitation of this flaw.
Proof of concept
Horizon3.ai researchers published a working proof-of-concept exploit to GitHub on January 23 that exploits CVE-2024-0204 to create an administrative user.
Solution
The following are the affected and fixed versions of GoAnywhere MFT:
| Affected Version | Fixed Version |
|---|---|
| 7.4.0 and below | 7.4.1 |
| 6.0.1 and above | Upgrade to 7.4.1 |
Fortra released version 7.4.1 of GoAnywhere MFT on December 7 according to its release notes. In the release notes, Fortra references fixing a “authentication bypass issue” that could allow “invalid access to create new users.” While Fortra has yet to include a reference to CVE-2024-0204 in its release notes as of January 23, they confirm this is the fixed version for this CVE in its security advisory.
If applying the patches are not feasible, Fortra provides two mitigation options for affected customers:
| Deployment Type | Mitigation |
|---|---|
| Non-container Deployment | Delete “InitialAccountSetup.xhtml” from installation directory and restart services |
| Container Deployment | Replace “InitialAccountSetup.xhtml” from installation directory with an empty file and restart services |
Identifying affected systems
A list of Tenable plugins for this vulnerability can be found on the individual CVE page for CVE-2024-0204 as they’re released. This link will display all available plugins for this vulnerability, including upcoming plugins in our Plugins Pipeline.
Get more information
- Fortra Security Advisory (FI-2024-001): Authentication Bypass in GoAnywhere MFT
- Horizon3.ai Analysis of CVE-2024-0204
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management


