CVE-2023-4966: Citrix NetScaler ADC and NetScaler Gateway Information Disclosure Exploited in the Wild

A critical information disclosure vulnerability in Citrix NetScaler Application Delivery Controller (ADC) and NetScaler Gateway has been exploited in the wild as a zero-day vulnerability. Organizations are urged to patch immediately.
Update October 25: The Proof of concept section has been updated reflect the availability of an exploit script and technical writeup on the vulnerability.
Background
On October 10, Citrix published a security bulletin (CTX579459) that addressed a critical severity information disclosure vulnerability in Netscaler ADC (formerly known as Citrix ADC) and Netscaler Gateway (formerly known as Citrix Gateway).
On October 17, Mandiant released a blog post and remediation guidance document where they noted that exploitation of a zero-day vulnerability, later identified as CVE-2023-4966, was observed in late August.
| CVE | Description | CVSSv3 | Severity |
|---|---|---|---|
| CVE-2023-4966 | Sensitive information disclosure | 9.4 | Critical |
In addition to CVE-2023-4966, Citrix patched one additional vulnerability in security bulletin CTX579459.
| CVE | Description | CVSSv3 | Severity |
|---|---|---|---|
| CVE-2023-4967 | Denial of service (DoS) | 8.2 | High |
Analysis
CVE-2023-4966 is an information disclosure vulnerability in NetScaler ADC and NetScaler Gateway. When configured as a gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or as an AAA virtual server, an unauthenticated attacker could exploit the device in order to hijack an existing authenticated session. Depending on the permissions of the account they have hijacked, this could allow the attacker to gain additional access within a target environment and collect other account credentials. Successful exploitation allows the attacker to bypass multifactor authentication (MFA) requirements.
CVE-2023-4966 was exploited as a zero-day
In a remediation guidance blog post by Mandiant, the firm acknowledges that they first observed exploitation of the then zero-day vulnerability in late August. While no further information was provided on who might be behind the attacks, Mandiant’s investigation resulted in some remediation and risk reduction advice.
As part of their guidance, Mandiant notes that an attacker's session could persist even after a device has been patched. In order to resolve this, the following command can be run using the command line interface (CLI):
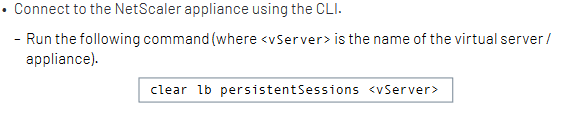
Image Source: Mandiant, October 2023
In addition, Mandiant offers recommendations and investigation suggestions to determine if a device may have been impacted. Mandiant states that they have “not identified any available logs or other artifacts resident on NetScaler appliances that record evidence of exploitation.” We strongly recommend reviewing their guidance and following the suggestions outlined.
ADC and Gateway Historically Targeted by Attackers
Citrix’s NetScaler ADC and NetScaler Gateway appliances have long been valuable targets for attackers. In December 2022, Citrix patched a critical remote code execution (RCE) vulnerability, CVE-2022-27518, in Citrix NetScaler ADC and NetScaler Gateway, that was also exploited in the wild.
Following the disclosure of CVE-2019-19781, another unauthenticated RCE vulnerability in NetScaler ADC and NetScaler Gateway appliances in late 2019, active exploitation began in early 2020 and it remained a popular vulnerability with a variety of attackers including Chinese state-sponsored threat actors, Iranian-based threat actors, Russian state-sponsored threat groups as well as ransomware groups. Additionally, CVE-2019-19781 was featured as one of the Top 5 vulnerabilities in our 2020 Threat Landscape Retrospective report.
Due to the historical nature of exploitation against NetScaler ADC and NetScaler Gateway appliances, we strongly urge organizations to patch CVE-2023-4966 as soon as possible.
Proof of concept
At the time that this blog post was published, there was no proof-of-concept (PoC) available for CVE-2023-4966. However on October 24, a PoC was released by Assetnote on GitHub along with a technical writeup published on October 25. In the post from Assetnote, they are calling vulnerability Citrix Bleed and discuss the process of identifying the vulnerability and developing their PoC.
Solution
Citirix has released patches for CVE-2023-4966 as well as the DoS vulnerability, CVE-2023-4967, as outlined in the table below:
| Affected Product | Affected Version | Fixed Version |
|---|---|---|
| NetScaler ADC and NetScaler Gateway | Prior to 13.0-92.19 | 13.0-92.19 and later releases of 13.0 |
| NetScaler ADC and NetScaler Gateway | Prior to 13.1-49.15 | 13.1-49.15 and later releases of 13.1 |
| NetScaler ADC and NetScaler Gateway | Prior to 14.1-8.50 | 14.1-8.50 and later releases |
| NetScaler ADC 12.1-NDcPP | Prior to 12.1-55.300 | 12.1-55.300 and later releases of 12.1-NDcPP |
| NetScaler ADC 12.1-FIPS | Prior to 12.1-55.300 | 12.1-55.300 and later releases of 12.1-FIPS |
| NetScaler ADC 13.1-FIPS | Prior to 13.1-37.164 | 13.1-37.164 and later releases of 13.1-FIPS |
Citrix also notes that NetScaler ADC and NetScaler Gateway versions 12.1 is End of Life (EOL), and users are urged to upgrade to a supported version immediately.
Users of Citrix-managed cloud services or Citrix-managed Adaptive Authentication do not need to perform any actions according to the Citirx security bulletin, which clarifies that it only applies to customer-managed servers.
The October 23 blog post from the Cloud Software Group also provides some recommendations on steps to take after updating an affected device. This includes removing any current active and persistent sessions. We recommend reviewing the blog for more information.
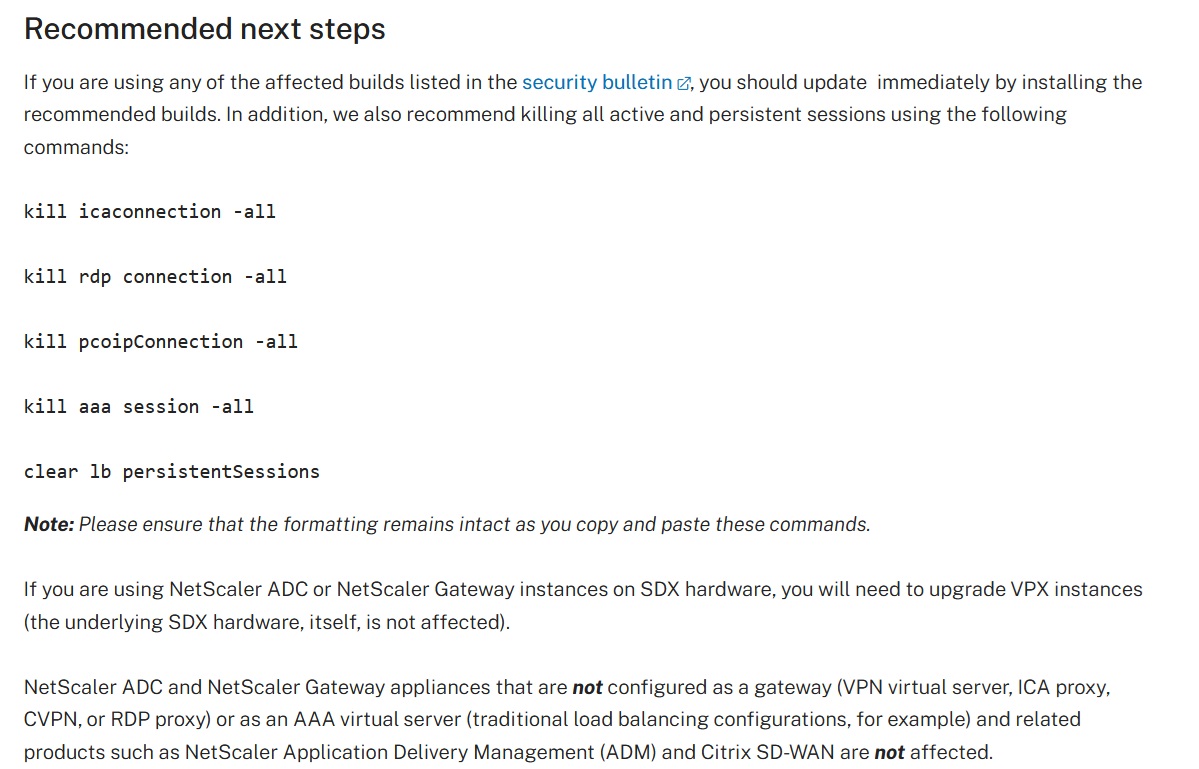
Image Source: Cloud Software Group, October 2023
Identifying affected systems
A list of Tenable plugins to identify affected systems can be located on the individual CVE pages for CVE-2023-4966 and CVE-2023-4967. These links will display all available plugins for these vulnerabilities, including upcoming plugins in our Plugins Pipeline.
Get more information
- Citrix Security Bulletin (CTX579459)
- Mandiant Remediation Guidance Blog Post
- Mandiant Remediation Guidance PDF
- CVE-2023-4966: Critical security update now available for NetScaler ADC and NetScaler Gateway
- Citrix Bleed: Leaking Session Tokens with CVE-2023-4966
Change Log
Update October 25: The Proof of concept section has been updated reflect the availability of an exploit script and technical writeup on the vulnerability.
Update October 23: The blog has been updated to include a link to a Cloud Software Group blog post warning of active exploitation of CVE-2023-4966.
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management


