CVE-2020-3566, CVE-2020-3569: Zero-Day Vulnerabilities in Cisco IOS XR Software Targeted in the Wild

Cisco warns of two zero-day denial-of-service vulnerabilities in its IOS XR Software actively exploited in the wild.
Update September 29, 2020: The Solutions section has been updated with details regarding patches that were released by Cisco.
Background
On August 29, 2020, Cisco published an advisory regarding a zero-day denial-of-service (DoS) vulnerability in its Cisco IOS XR Software. This advisory was released in response to the Cisco Product Security Incident Response Team (PSIRT) becoming “aware of attempted exploitation of these vulnerabilities in the wild” on August 28. Cisco updated its original advisory on August 31 to reflect an additional vulnerability in the IOS XR Software and include another CVE. The Cybersecurity and Infrastructure Security Agency (CISA) also issued an alert on August 31 regarding the attempted exploits in the wild, recommending that organizations apply mitigations or patches when available.
Analysis
CVE-2020-3566 and CVE-2020-3569 are unauthenticated DoS vulnerabilities in the Distance Vector Multicast Routing Protocol (DVMRP) feature of Cisco IOS XR Software, an operating system that comes installed on a range Cisco carrier-grade and data center routers. These vulnerabilities exist because the affected device is unable to correctly implement queue management for Internet Group Management Protocol (IGMP) packets.
A remote unauthenticated attacker that successfully exploits these vulnerabilities could exhaust the process memory on a vulnerable device, starving it of resources. For an attacker to take advantage of this flaw, they would need to send specially crafted IGMP packets to a vulnerable device. This could result in instability in processes including, but not limited to, an impact in the routing protocols for both internal and external networks which could result in the slowing or crippling of a network.
These vulnerabilities impact Cisco devices running any version of the Cisco IOS XR Software that also has multicast routing enabled on any of its interfaces. If multicast routing is not enabled on the device, then it is not affected by either of these vulnerabilities. Running the command show igmp interface on a device with Cisco IOS XR Software will show the multicast routing configuration. If the output is empty, the device is not affected. Below is an example output of a device with multicast routing enabled:
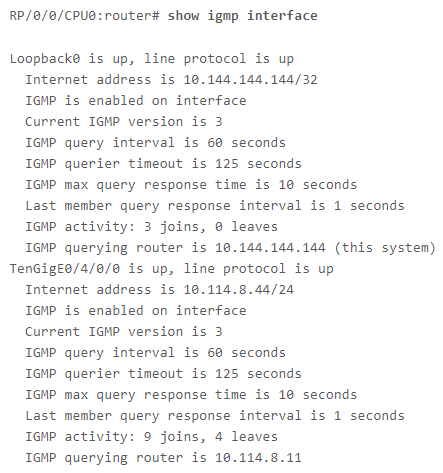
Source: Cisco IOS XR Software DVMRP Memory Exhaustion Vulnerability Advisory
Proof of concept
There was no proof-of-concept available for these vulnerabilities at the time this blog post was published.
Solution
All Cisco devices running any version of Cisco IOS XR Software with an active interface configured under multicast routing are affected by these vulnerabilities. On September 29, Cisco updated their original advisory, noting that they’ve released Software Maintenance Upgrades (SMUs) to address both vulnerabilities for Cisco IOS XR versions. For more details about the patches, please review the Fixed Releases section in Cisco’s advisory.
If upgrading is not feasible at this time, Cisco has recommended two mitigations to implement where appropriate for the environment of a vulnerable device. The first mitigation will not prevent exploitation but rather limits the rate of IGMP traffic to that lower than the current average rate, increasing the time required for successful exploitation. This mitigation can be implemented by entering the following command while in configuration mode:
RP/0/0/CPU0:router(config)# lpts pifib hardware police flow igmp rate
The second mitigation is to update an interface access control list (ACL) or create a new one with an access control entry that denies DVMRP traffic inbound on that interface. This mitigation can be implemented by entering the following command:
RP/0/0/CPU0:router(config)# ipv4 access-list
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
Get more information
- Cisco IOS XR Software DVMRP Memory Exhaustion Vulnerability Advisory
- CISA Warning for DVMRP Vulnerability in IOS XR Software
- Cisco IOS XR Software
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


