CVE-2017-7391: Vulnerability in Magento Mass Import (MAGMI) Plugin Exploited in the Wild

Just as Magento 1 reaches end of life, attackers are exploiting a vulnerability in a Magento plugin from 2017. Site owners should prepare to migrate their stores immediately.
Background
On May 17, ZDNet published an article about an FBI flash security alert shared with the private sector regarding attacks against Magento stores. Magento is a popular e-commerce platform used by many companies. There are two separate offerings of Magento: Magento Open Source (formerly known as Magento Community Edition), which is freely available to all users, and Magento Commerce (formerly known as Magento Enterprise Edition), which is the enterprise solution. In May 2018, Adobe announced it would be acquiring Magento Commerce, the company behind Magento.
Since 2016, Magento sites have become the target of a type of attack named Magecart, a name derived from Magento and shopping cart. Magecart attackers inject malicious JavaScript code into legitimate Magento sites in order to steal customer payment card information during online checkout.
Despite the name and initial connection to Magento, Magecart has since become a catch-all term to describe various types of malicious code injections into e-commerce sites with the intention to steal payment card data.
The May 6 FBI alert provides additional information about the recent activity involving Magento and a specific Magento plugin.
Web applications like Magento enable organizations large and small to build e-commerce websites rapidly and fulfill a critical business need. However, such apps also pose challenges in terms of ensuring that these websites are secure from attackers. The modular nature of these web applications, such as the ability to enhance them with plugins or extensions, adds an additional layer of complexity when it comes to securing these websites. Given the nature of web applications, attackers usually don’t need credentials to exploit and the exploits themselves are generally easy to run. Regular scanning using a web application security product can help determine the accurate cyber exposure and help with risk-based mitigation.
Analysis
CVE-2017-7391 is a cross-site scripting (XSS) vulnerability in the Magento Mass Importer (also known as MAGMI or Magmi) plugin for Magento stores. The flaw exists due to insufficient handling of user-supplied input in the prefix parameter for requests made to ajax_gettime.php. The vulnerability was discovered by Haojun Hou of Venustech’s ADLab.
To exploit the flaw, an attacker would need to send a specially crafted request to a Magento site using the vulnerable version of the Magmi plugin. Exploitation of the flaw would allow an attacker to inject arbitrary HTML or javascript code within the browser in the context of the vulnerable application. The SecurityFocus entry for this vulnerability mentions that an attacker would be able to “steal cookie-based authentication credentials and launch other attacks.”
The FBI alert references an example where a United States e-commerce website was exploited using this vulnerability to “successfully retrieve environment credentials,” which were used to download web shells onto the vulnerable site to enable persistence and file uploading capabilities.
The vulnerability was addressed by wrapping the prefix parameter using the htmlspecialchars PHP function that converts reserved characters like ampersands, double quotes, single quotes, less-than and greater-than symbols into their respective HTML/character entities.
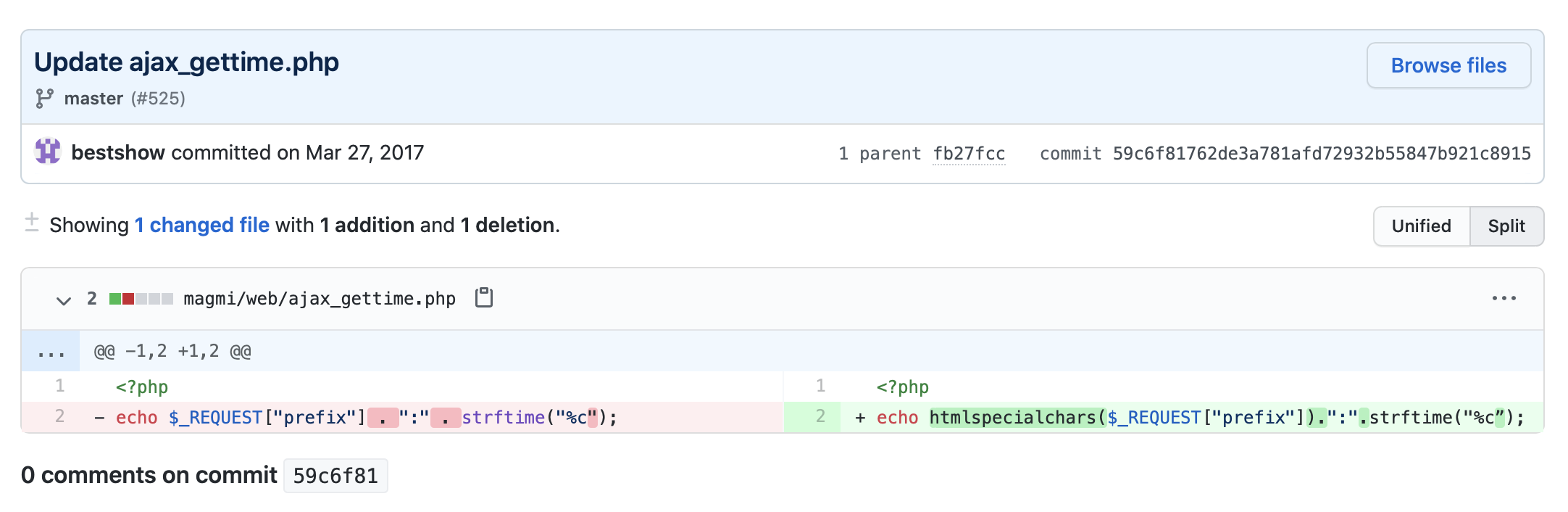
This fix is supposed to prevent an attacker from injecting script code in requests to the ajax_gettime.php file as part of the prefix parameter.
Magento 1 End of Life
The FBI issuing an alert like this is significant, because it shows that the Magecart attackers are still actively targeting vulnerable Magento sites. To complicate things, Magento announced in 2018 that it would end support for Magento 1 in June 2020. Specifically, the end of life (EOL) for Magento 1 is June 30. This notice provided Magento site owners time to migrate their sites to Magento 2 in anticipation of the EOL.
Magento 1 Receives Last Batch of Security Patches
On June 22, Adobe released ASPB20-41, its final set of security updates for Magento Commerce and Magento Open Source. After June 30, Magento 1 will no longer receive security updates. Therefore, it is imperative for Magento site owners to transition away from Magento 1 as soon as possible. It is likely that attackers may be sitting on vulnerabilities in Magento 1 that they’ve not yet utilized, as they wait for Magento 1 to officially reach EOL before targeting vulnerable sites.
Proof of concept
An example proof-of-concept to exploit this flaw was provided in a GitHub issue:
hxxp://localhost/.../magmi-git-master/magmi/web/ajax_gettime.php?prefix=%22%3E%3Cscript%3Ealert(1);%3C/script%3E%3C%22
Solution
According to the developers of the Magmi plugin, CVE-2017-7391 was addressed in Magento version 0.7.23 of the plugin. However, there is no official “release” page for the plugin. The latest release still shows up as 0.7.22.
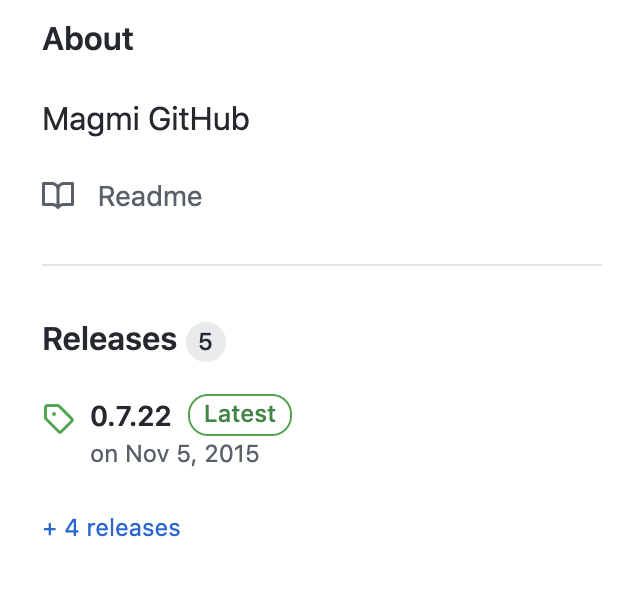
Therefore, users hoping to retrieve the patched version of the plugin would need to clone the latest version of the plugin’s GitHub repository. Otherwise, their Magento sites will still be vulnerable to CVE-2017-7391.
Whether or not site owners are able to upgrade to the patched version of the Magmi plugin, we strongly recommend taking some preventative measures to help mitigate attacks targeting Magmi by securing its installation:
- Apply IP source allowlisting to ensure only specific IP addresses are capable of accessing the Magmi web interface
- Use a custom unpredictable folder name instead of the default /magmi path when installing Magmi so attackers can’t easily locate the web interface
- Ensure that the conf/magmi.ini file located in the Magmi installation directory is not accessible from the web to avoid sensitive information exposure, for example, using Apache Module mod_access to deny access to .ini files.
These mitigation steps should be applied in addition to the best practices defined for securing the Magento core installation.
Since Magento 1 will no longer receive security updates, administrators and site owners are strongly advised to upgrade to Magento 2 as soon as possible.
Identifying affected systems
To identify the Magmi vulnerability using our Web Application Scanner (WAS), please use Plugin ID 112441.
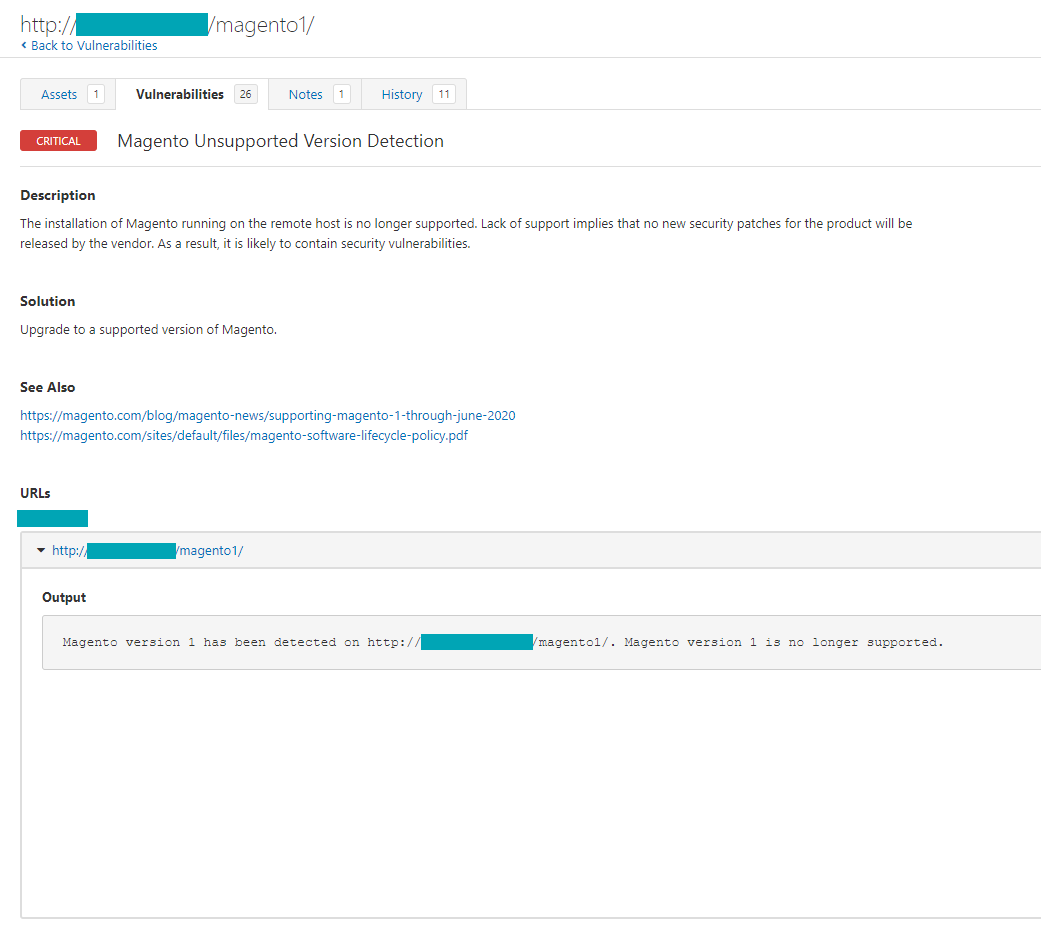
In addition, Tenable customers can utilize our Magento Unsupported Version Detection plugin (Plugin ID 11250) for WAS to identify targets running unsupported versions of Magento.
Get more information
- FBI Flash Alert MU-000127-MW
- ZDNet Article about FBI Alert for Magmi Plugin
- GitHub Repository for Magmi Plugin
- Magento Security Best Practices
- Securing MAGMI Data Import Tool
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

