CISA Directive 22-01: How Tenable Can Help You Find and Fix Known Exploited Vulnerabilities

While U.S. federal agencies are required to remediate the vulnerabilities outlined in the U.S. Cybersecurity and Infrastructure Security Agency's Binding Operational Directive 22-01, any organization would do well to consider prioritizing these flaws as part of their risk-based vulnerability management program.
On November 3, 2021, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released Binding Operational Directive 22-01 - Reducing the Significant Risk of Known Exploited Vulnerabilities, requiring government agencies to address a catalog of known exploited vulnerabilities that carry significant risk to federal information systems within six months. With this new catalog, CISA is targeting vulnerabilities for mitigation that have known exploits and are being currently used by malicious adversaries in an ongoing manner.
While U.S. federal agencies are required to remediate the vulnerabilities outlined in the new CISA catalog, any organization would do well to consider prioritizing these vulnerabilities as part of their risk-based vulnerability management program.
Detecting CISA's catalog of known exploited vulnerabilities
The initial CISA catalog includes approximately 300 Common Vulnerabilities and Exposures (CVEs) across dozens of different vendors and software products, 115 of which are either past due or due for remediation by federal agencies on November 17, 2021. In addition, there are over 175 more vulnerabilities being tracked by CISA, which federal agencies will be required to remediate by May 3, 2022. Tenable customers should use the Vulnerability Priority Rating (VPR) to help prioritize which of these 175+ CVEs need to be addressed first.
While the CISA catalog is an important resource to help security professionals identify vulnerabilities to remediate, it’s still a vast number to address and it's challenging to detect them all in any single specific way. Attackers don't target what's easy to detect and fix, they target what's effective to exploit and get them closer to their end goal.
Effective remediation requires the right combination of tools and best practices. In particular, we'll focus below on two key areas — assessment frequency and assessment depth — and provide guidance on how Tenable products can help with each. In addition, we provide detailed guidance on how to use Tenable.sc, Tenable.io and Tenable's Vulnerability Priority Rating (VPR) to further aid in your remediation efforts.
Choosing the correct sensor for the job
The following Tenable options offer a starting point for addressing the CISA vulnerabilities:
- Use Nessus, as a part of Tenable.sc or Tenable.io, for network-based assessments of systems that are hard-wired into your infrastructure.
- Use Nessus Agents to assess remote users that may not consistently or ever physically plug-in to the corporate network.
- Use Tenable.ot to analyze industrial control systems (ICS) and supervisory control and data acquisition (SCADA) networks for the specialized equipment and software that don't typically respond well to traditional security tools.
- Use Tenable.io Cloud Connectors and Frictionless Assessment to have insight to what cloud virtual machine instances are configured and automatically assess them without deploying additional software or scanners.
- Use Tenable.ad for real-time insight into changes introducing risk and attacks on your Microsoft Active Directory infrastructure.
Fine-tuning your assessment frequency
Wherever possible, assess in a continuous process. This means using tools like Nessus Network Monitor, Tenable.ad or Tenable.ot, all of which work in near-real time to provide insight to changes or events that can introduce risk into your environment.
For scheduled assessments using tools like Nessus or Nessus Agents, scan at least twice a week to track environmental changes and discover newly released vulnerabilities or existing ones introduced into your environment.
Achieving assessment depth
As you begin your process of addressing the CISA catalog of CVEs, it's important to have as much information as possible. From a network scan perspective, fully authenticated assessments are a key part of that process as they provide up to 45 times more findings and insight than uncredentialed assessments (assessments by Nessus Agent are authenticated in terms of plugin coverage).
Source: Tenable, November 2021
Tenable Lumin customers automatically have their assessment maturity rated and tracked over time, including depth grade, authentication coverage, scan cycle and scan frequency. This quantifies the best practices put forth in this blog in an easy to read A-F grade scale to verify the scanning activities that promote good cyber hygiene.
Learn how to set up credentialed scans on Windows and Linux and protect scanning credentials.
Given the wide array of CVEs emphasized in the new CISA catalog, the more in-depth you can make your network assessments, the more effective your remediation process will be. There are several scan policy settings in Nessus (and thus Tenable.sc and Tenable.io) that can be tweaked to provide more in-depth results; note that there are potential impacts to changing these settings and any scan policy setting changes should be tested thoroughly before deployment to production environments. The list below addresses notable scan policy settings you can modify to improve your assessment depth:
- Service Discovery - “Probe all ports to find services” to On (Default Setting)
- When enabled, the scanner attempts to map each open port with the service that is running on that port.
- Assessment - “Perform thorough tests” to On
- Causes various plugins to work harder. For example, when looking through SMB file shares, a plugin can analyze three directory levels deep instead of one. This could cause more network traffic and analysis in some cases. However, by being more thorough, the scan is more intrusive, while potentially providing better audit results.
- Brute Force - “Only use credentials provided by the user” to Off
- This will enable plugins that check for default or known credentials; but could cause account lockouts depending on environmental configurations.
- Web Applications - “Scan web applications” to On
- This will increase scan times and could cause a performance impact to systems that host web applications.
- Report - “Show missing patches that have been superseded” to On (Default Setting)
- When enabled, includes superseded patch information in the scan report. Disabling this setting will hide superseded findings and limit visibility into older missing patches.
- Plugins - Enable all families (Default Setting)
- Tenable automatically determines the correct plugins to run against a target at scan time; unless you're targeting a very specific vulnerability there generally isn't a need to do system or OS specific scan policies.
Using Tenable.sc to track CISA's catalog of known exploited vulnerabilities
Tenable.sc users should start with the "DHS Binding Operational Directive 22-01" dashboard, released in the product on Nov 4, 2021.
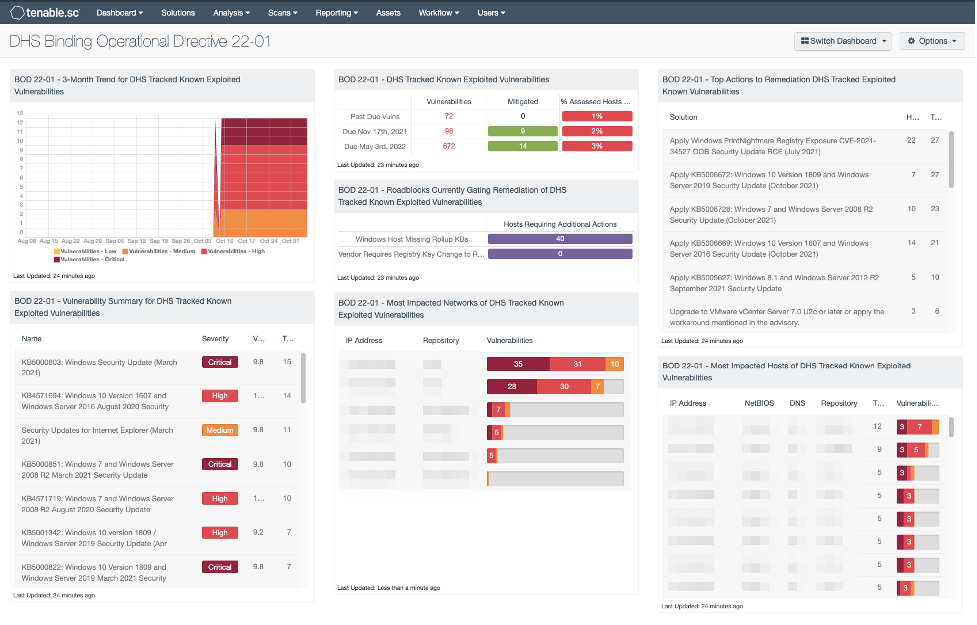
Source: Tenable, November 2021
This dashboard focuses on the 115 CVEs that are either past due or due for remediation by federal agencies on November 17, 2021. It provides visibility into the systems impacted and the vulnerabilities present in an organization in a variety of views. Notably:
- A ranking of the highest impact actions to take to remediate the vulnerabilities across your environment in BOD 22-01 - Top Actions to Remediation DHS Tracked Exploited Known Vulnerabilities
- A matrix of the outstanding vulnerabilities detected, the quantity of remediated vulnerabilities and the percentage of hosts that are still impacted in BOD 22-01 - DHS Tracked Known Exploited Vulnerabilities
- Insight into systems that may require additional actions, such as Microsoft Rollup KBs or registry key changes for remediation in BOD 22-01 - Roadblocks Currently Gating Remediation of DHS Tracked Known Exploited Vulnerabilities
Users can click into each of the components in this dashboard to see how they’re built and to modify them if needed for custom use. Users can also filter the entire dashboard automatically when it's added by repository, asset list or particular IP lists/ranges.
View the webinar: How Risk-Based Vulnerability Management Helps You Effectively Address CISA’s Binding Operational Directive 22-01
Tenable.sc users may also wish to create queries that are then usable throughout the tool to help track these vulnerabilities, as opposed to relying solely on the provided dashboard or maintaining a giant list of CVEs in a clipboard (lists of these CVEs in the proper format can be copied from the BOD 22-01 - DHS Tracked Known Exploited Vulnerabilities dashboard component). These queries can then be maintained in one location and then re-used throughout Tenable.sc in dashboards, assurance report cards, vulnerability analysis, reports and alerts.
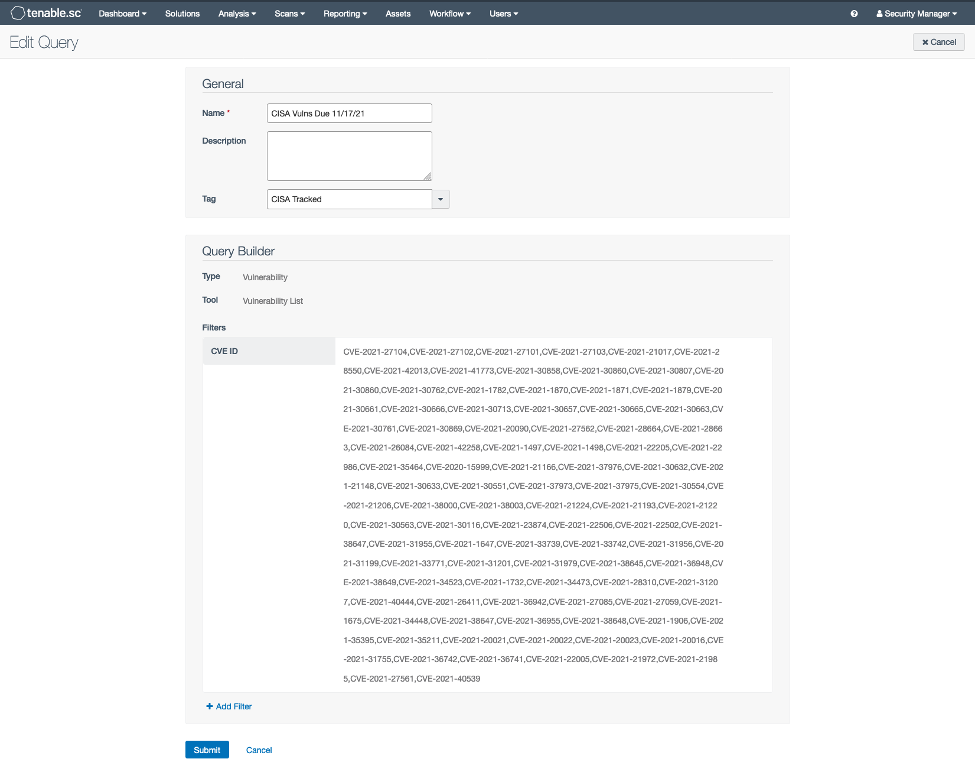
Source: Tenable, November 2021
Tenable.sc users can also add the DHS CISA Binding Operational Directive 22-01 Report to produce an artifact or communicate the progress and status toward fixing the vulnerabilities that CISA is tracking. Like the dashboard, this report focuses on the vulnerabilities due to be remediated by November 17, 2021.
Using Tenable.io to track CISA's catalog of known exploited vulnerabilities
Tenable.io customers can use saved searches to track the findings CISA is monitoring in its catalog. Simply add the CVE filter you want to the vulnerabilities workbench and save the filter.
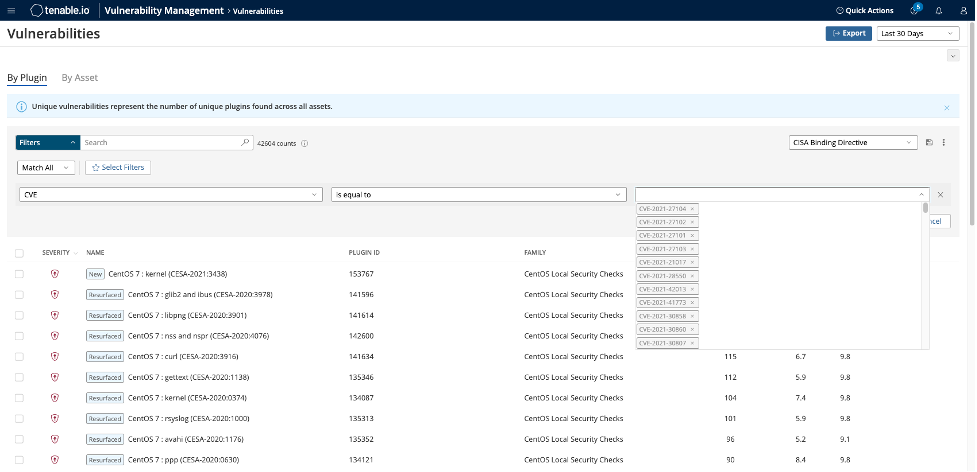
Source: Tenable, November 2021
This saved search can then be shared with other users or selected in custom dashboard widgets.
Using Tenable's VPR to prioritize CISA's catalog of known exploited vulnerabilities
CISA's list of vulnerabilities is a great place to start for organizations looking for more actionable content on what to prioritize to reduce their cyber risk.
As CISA adds vulnerabilities to its catalog and Tenable develops detections for those vulnerabilities, VPR is automatically calculated and added to every plugin that tracks a CVE. The threat data that VPR tracks is analyzed on a daily basis and those updates are provided automatically to Tenable.sc and Tenable.io customers. VPR filters can be added to dashboards and analysis views/exports in both Tenable.sc and Tenable.io, giving further insight and context to the active threat potential of a particular CVE.
Conclusion
Tenable has long championed the idea of ‘focusing on what matters first’ and we applaud CISA for the public release of this catalog. Additional data that organizations can use to help prioritize vulnerabilities and remediation will help create more secure networks and let organizations spend more time being proactive vs reactive with their cyber security programs.
Learn More
Tenable resources:
- Tenable.sc Dashboard for CISA Directive
- Tenable.sc Report for CISA Directive
- Tenable Blog: CISA’s Binding Operational Directive on Managing Unacceptable Risk Vulnerabilities in Federal Enterprises Is Key to Stopping Federal Cyberattacks
- Tenable Webinar: How Risk-Based Vulnerability Management Helps You Effectively Address CISA’s Binding Operational Directive 22-01
CISA resources:
- Active Directory
- Cloud
- Container security
- Energy Industry
- Executive Management
- Federal
- Government
- Risk-based Vulnerability Management
- SCADA
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning



