BYOD and Mobile Security: 2016 Spotlight Report Results

Tenable recently sponsored a survey on BYOD (bring your own device) and mobile security run by our friends at the LinkedIn Information Security Community. Given that mobile comes up frequently when we speak with customers about their challenges with unknown assets and shadow IT, we want to share a few highlights, let you know how to download the full report and invite you to attend an upcoming webcast that digs into the details of the results.
BYOD and mobile growth
In the study, the majority of respondents (72%) had reached the stage where BYOD was available to all (40%) or some (32%) employees. This matches the number seen in similar studies and is expected to grow even higher in the next few years.
The majority of respondents (72%) had reached the stage where BYOD was available to all (40%) or some (32%) employees
Employees are able to do a lot more with their mobile devices now. While email, calendar and contact management were the most common applications (used by 84% of respondents), many respondents reported that other employee productivity applications were also available via BYOD and mobile, including:
- 45% - document access and editing
- 43% - access to SharePoint and intranets
- 28% - access to SaaS applications like Salesforce
With the number of mobile devices increasing and the types of activities on those devices getting more complex, organizations should expect attackers to target mobile devices for data breaches, intrusions and malware incidents.
Mobile threats and breaches
39% of respondents reported that within their organization, BYOD or corporate-owned devices had downloaded malware at some point in the past. That number could be higher though, because 35% of surveyed respondents said they are “not sure” if malware has been downloaded in the past.
39% reported that within their organization, BYOD or corporate-owned devices had downloaded malware
The use of mobile malware by attackers is definitely on the rise. In February of this year, Checkpoint announced that for the first time, mobile malware was one of the ten most common attack types seen in its threat intelligence database. For example, the previously-unknown malware called HummingBad targets Android devices, installs malicious apps and enables malicious activity such as key-logging, which can help attackers steal credentials that could be used to gain access to corporate networks and data.
The survey also reveals that security breaches using BYOD and mobile devices are on the rise, with 21% of respondents saying they experienced a security breach through the use of BYOD or mobile devices. However, like the mobile malware responses, the actual number of breaches could be higher because 37% answered that they "weren't sure."
21% of respondents said they had experienced a security breach through the use of BYOD or mobile devices
It’s not surprising that 35% of respondents said they didn’t know if mobile malware was present and 37% said they didn’t know if they’d had a mobile breach. Gaining visibility into device status is a huge challenge with mobile security, simply because the devices are so transient. They move from 3G to 4G to wireless networks seamlessly and are turned off and on at random times, making it difficult to include them in a security management program. Technologies like mobile device management (MDM) and passive detection will become increasingly important to ensure mobile security.
Managing mobile device security
The top three tools mentioned in the survey to manage mobile device security were:
- 43% - mobile device management (MDM)
- 28% - endpoint security tools
- 27% - Network Access Controls (NAC)
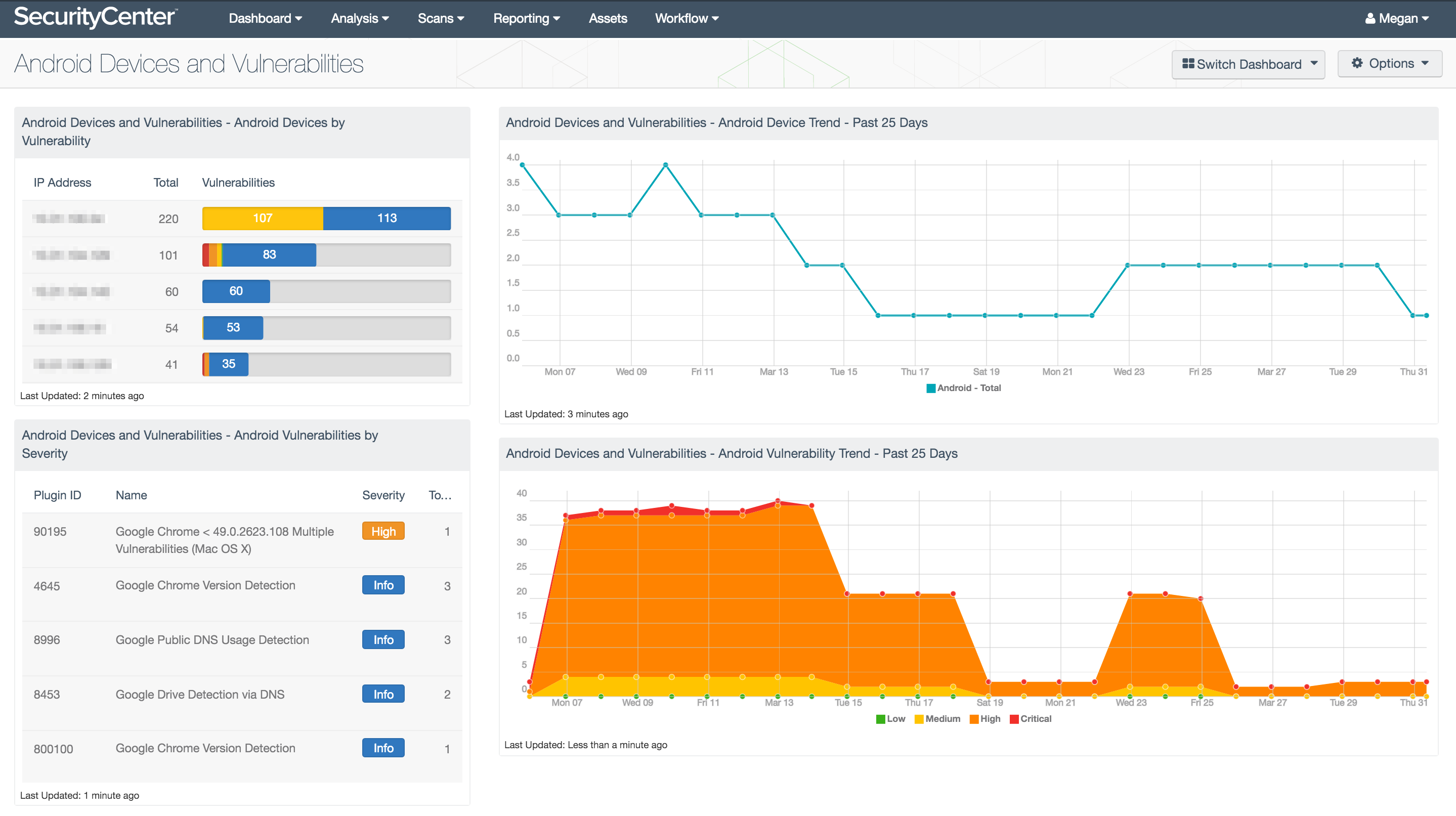
At Tenable, we believe that whatever tool you decide to use to manage mobile security, it’s important that it integrates with the other security solutions you have in place and fits seamlessly into your overall vulnerability management program. Look for integration points like the example in the screenshot below, where MDM data can be fed into your vulnerability management / continuous monitoring solution.
More information
I have touched on just a few of the findings from the 2016 Spotlight Report. There is lots more data on topics such as breach recovery, user and application behavior, supported platforms, and typical support. To learn more:
- Download the full report from the Tenable website
- Register for a live webcast with all the report sponsors
- Date: April 14, 2016
- Time: 12 pm ET | 9 am PT | 5 pm GMT
- BYOD
- Mobile Security
- Research Reports
- Shadow IT



