Bridging the Infosec/Business Communication Gap with Tenable’s Assurance Report Cards™

Traditionally, business executives have been concerned with revenue, market share, competitive threats, expenses and economic indicators. Today, inundated with frequent headlines about high profile security breaches, cybersecurity has joined their list of concerns. Executives need to know if their organizations are managing cyber risk effectively, and they must be able to communicate that information upward to their board members who have the responsibility for risk oversight.
Cybersecurity is a business issue
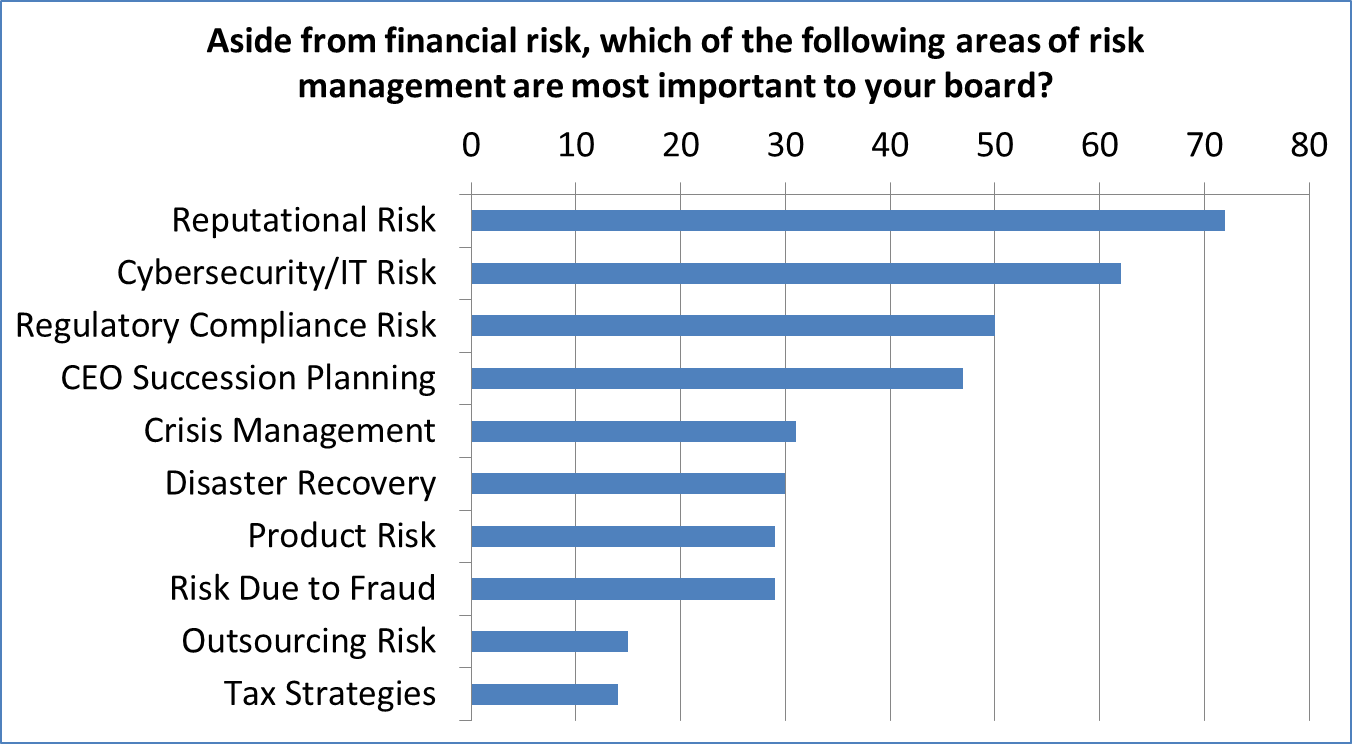
Although information security professionals may not think business executives and board members know enough or care enough about cybersecurity, there is mounting evidence to the contrary. Research performed by the law firm EisnerAmper demonstrates that board members are quite concerned about risks related to cybersecurity, and the research was not restricted to board members of public companies. 26% of the respondents were from private companies, and 36% were from not-for-profit organizations. In fact, the top three concerns of board members are related to information security:
How do you communicate technical security status details to business leaders?
Cybersecurity affects everyone in an enterprise. It has quickly become a C-level concern. But as an infosec professional, how do you communicate technical security status details to business leaders? Acronyms like APT, IOC, and DDoS may not sit well with executives, but you also don’t want to boil down the status of complex security controls into a handful of metrics. Executives need evidence demonstrating that the cybersecurity and compliance controls are in place and operating effectively, and security leaders often respond with statistics about new vulnerabilities discovered, blocked attacks and the patch rate. Those technical details may not help executives see the big picture; business leaders typically prefer dashboard-like reports that present status and details in easy-to-understand visual presentations. The challenge is to find a tool that defines and operationalizes automated indicators that are both meaningful and easily understood throughout the organization. How do you bridge this gap between business language and technical details?
Enter Assurance Report Cards
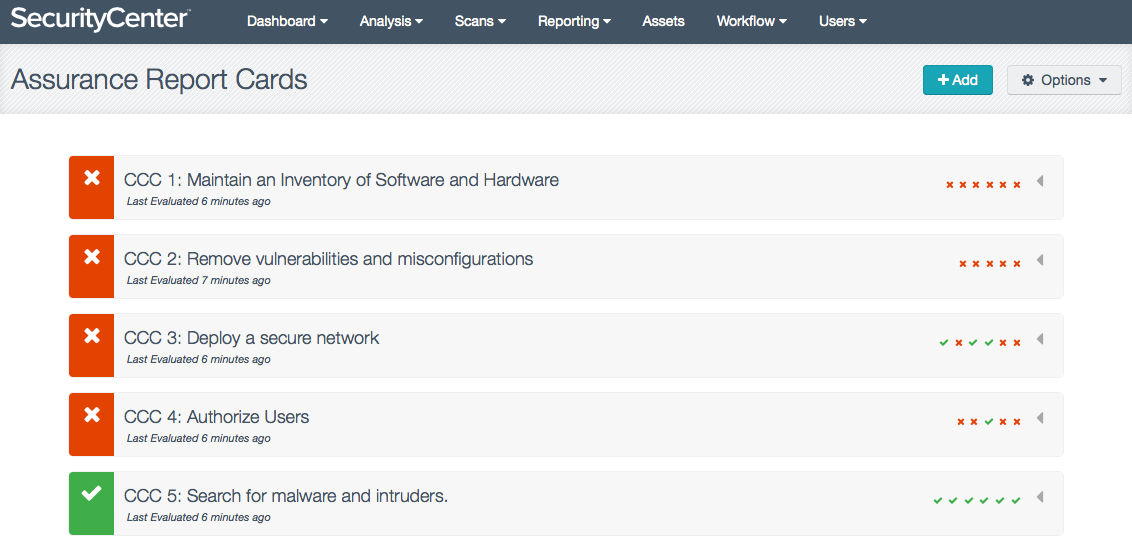
Assurance Report Cards™ (ARCs) are Tenable’s answer to the communication dilemma. ARCs are available in SecurityCenter™ 5.0 and display an enterprise’s security posture in the familiar paradigm of a report card. ARCs bridge the communication gap between business executives and security professionals by measuring and visually communicating the status of the most critical, fast-moving, automated security controls in an intuitive format. They present your executives with an up-to-date status relative to your organization’s security standards and compliance requirements so the executives can quickly understand your cyber risk and compliance posture.
As part of SecurityCenter Continuous View™ (SecurityCenter CV™), Tenable’s enterprise continuous network monitoring™ platform, ARCs are a visualization capability built onto SecurityCenter CV’s measurement and analysis capabilities.
How do ARCs work?
SecurityCenter CV comes pre-packaged with 5 ARCs that automate Tenable’s 5 Critical Cyber Controls:
- Maintain an inventory of software and hardware
- Remove vulnerabilities and misconfigurations
- Deploy a secure network
- Authorize users
- Search for malware and intruders
These controls are the most common objectives that should be tracked and measured by any cybersecurity program. The 5 controls summarize the most important points presented in industry standards such as the 20 Critical Security Controls from the SANS Institute and the Council on CyberSecurity, the NIST Cybersecurity Framework, and the PCI Data Security Standard. By starting with these 5 common ARCs, you can position your security program for success. ARCs correspond to these control objectives and rely on multiple policy statements to evaluate the underlying controls.
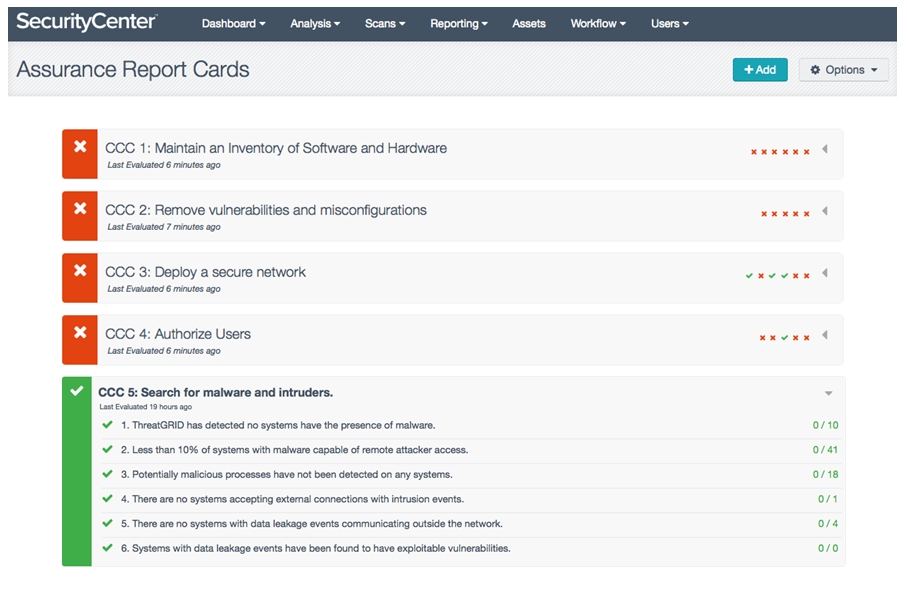
Each ARC objective is represented in SecurityCenter CV’s user interface on a separate line in the report card. A status summary of each of the ARC’s underlying policy statements is represented by the red x and green ✓ indicators on the right. If desired, individual policy statements and detailed scores can be expanded under a control objective:
Although ARCs summarize the status from potentially hundreds of controls, they retain the underlying data so it can be readily examined if necessary. For example, the Search for malware and intruders ARC is graded on a pass/fail status based on SecurityCenter’s evaluation of its underlying policy statements, which are typically conditional tests which evaluate to true or false. For example, these policy statements may include:
- No compromised laptops with malware processes
- No Internet facing web servers with exploitable vulnerabilities
- No systems accepting connections with intrusions
- No systems with data leakage talking to external devices
The ARC will only pass if all of its underlying policy statements evaluate to True. So in this case, all four conditions must be met for the ARC to receive a passing grade.
The measurements behind an Assurance Report Card are performed and continuously evaluated by SecurityCenter’s underlying tools:
- Nessus®: Actively scans networks, systems, data and applications to assess vulnerabilities, configurations and compliance status
- Passive Vulnerability Scanner™ (PVS™): Monitors network traffic in real-time to identify new assets, risk and vulnerabilities
- Log Correlation Engine™ (LCE®): A SecurityCenter CV component that collects and aggregates data from network and security infrastructure, raw network traffic and user activity to detect complex malware and isolate threats and compliance issues
Analysis is initially performed by Tenable’s more than 77,000 plugins that identify assets, detect vulnerabilities, assign severities, evaluate configurations and discover protected/proprietary data at rest and in transit. SecurityCenter CV then applies filters, queries and conditional logic to perform additional analysis.
The following graphic illustrates how this sample ARC and its underlying policy statements gather information from Nessus, PVS, and the LCE to determine if the business objective of Search for malware and intruders is being met.
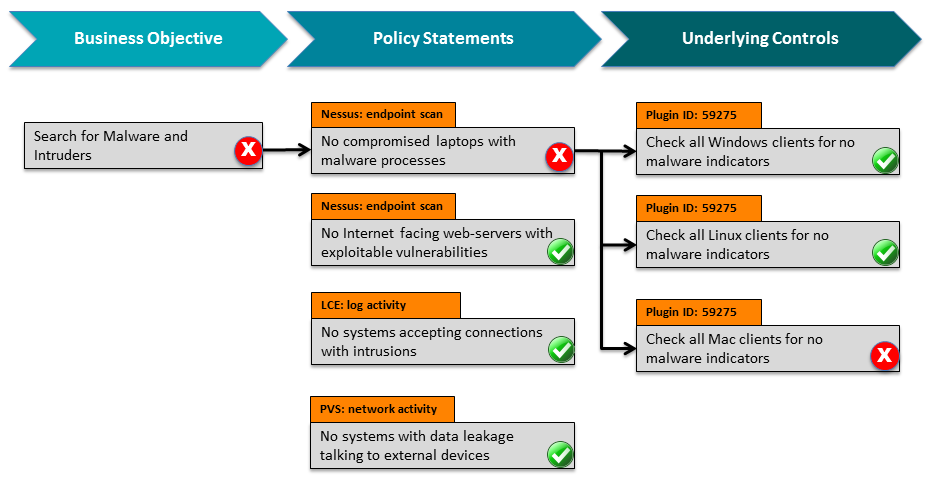
Together, these measurement capabilities gather configuration, compliance, vulnerability and real-time threat information from hundreds of different assets, including operating systems, network devices, virtual infrastructure, databases, mobile devices, web servers and embedded systems. They also gather information about network and system activity to identify suspicious traffic and anomalies.
ARCs go beyond reporting to solving problems
Besides summarizing your current security status information for executives, ARCs also foster discussion among internal stakeholders about high-level business objectives and the specific controls and effectiveness indicators that should be examined to evaluate your risk posture. Additionally, an ARC’s underlying data, showing which policy statements passed and which failed, is useful for security and compliance staff when prioritizing areas for improvement.
Customizing ARCs
You can customize the 5 Critical Cyber Control ARCs by adding any policy measurement or indicator that is critical to your business needs. You can also create your own ARCs to support enterprise-specific security and compliance requirements and objectives.
The new tool in your arsenal
ARCs measure what is most important to your business objectives using terminology that is familiar to your executives. They bridge the communication gap by avoiding technical jargon and by presenting the big picture in attractive, color-coded charts. And ARCs are available for presentation at a moment’s notice; SecurityCenter is continually monitoring the status of your critical systems and updating the ARCs with the latest data so that you can report to your business leaders at any time.
ARCs measure what is most important to your business objectives using terminology that is familiar to your executives
Additional resources
To learn more about SecurityCenter CV and the new Assurance Report Cards, check out these resources:
- SecurityCenter Assurance Report Cards: A How-to Guide
- SecurityCenter 5.0 FAQ
- What’s new in SecurityCenter 5.0
- Tenable Announces the Industry’s First Assurance Report Cards in SecurityCenter 5
- SecurityCenter 5.0 download for existing customers
- SecurityCenter 5.0 demo for new customers
- Executive Management
- SecurityCenter