Adobe Flash Vulnerability Can Lead to Code Execution and Asset Takeover (CVE-2018-15982)

Adobe has issued an out-of-band advisory for CVE-2018-15982. Through the use of a maliciously crafted RAR file, an attacker exploiting this vulnerability can take over the machine of users that run it.
Background
Adobe has released an out-of-band security bulletin. that includes patches for CVE-2018-15982, a critical arbitrary code execution vulnerability in Adobe Flash which has been used to allegedly attack Polyclinic No. 2, which is affiliated with the Presidential Administration of Russia. Users are encouraged to update all applications that incorporate Flash.
التحليل
The attack requires a user to open and run a malicious file that takes advantage of a dangling pointer, allowing the attacker to insert their code into the target’s memory, which Flash then executes. As with most code execution vulnerabilities, this vulnerability establishes a backdoor or similar foothold on the target.
In spear phishing campaigns, attacks are often designed to appear as legitimate emails, documents or tools, such as a Chrome extension that the organization often uses. In this case, attackers created a fake employee survey document that users understandably believed they needed to complete.

Source: 360 Core Security
Proof of concept
360 Core Security, one of the groups credited by Adobe with discovering this vulnerability, has an excellent technical write-up on how this attack works, and specifically how it was allegedly used against the Polyclinic site.
Once the payload is delivered, it disguises itself as an Nvidia driver application to further obfuscate infection.
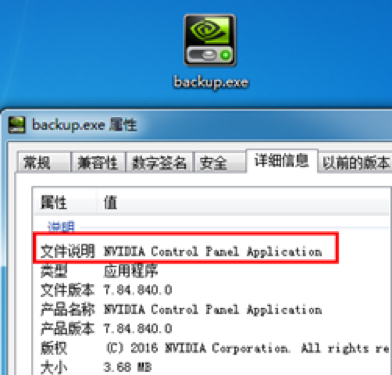
Source: 360 Core Security
الحل
Adobe’s advisory provides the following information on updating Flash:
- Adobe recommends users of the Adobe Flash Player Desktop Runtime for Windows, macOS and Linux update to Adobe Flash Player 32.0.0.101 via the update mechanism within the product* or by visiting the Adobe Flash Player Download Center.
- Adobe Flash Player installed with Google Chrome will be automatically updated to the latest Google Chrome version, which will include Adobe Flash Player 32.0.0.101 for Windows, macOS, Linux and Chrome OS.
- Adobe Flash Player installed with Microsoft Edge and Internet Explorer 11 for Windows 10 and 8.1 will be automatically updated to the latest version, which will include Adobe Flash Player 32.0.0.101.
*Note: Users who have selected the option to 'Allow Adobe to install updates' will receive the update automatically. Users who do not have the 'Allow Adobe to install updates' option enabled can install the update via the update mechanism within the product when prompted.
Identifying affected systems
A list of Nessus plugins to identify this vulnerability will appear here as they’re released.
الحصول على مزيد من المعلومات
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management



