by Cody Dumont
June 20, 2016
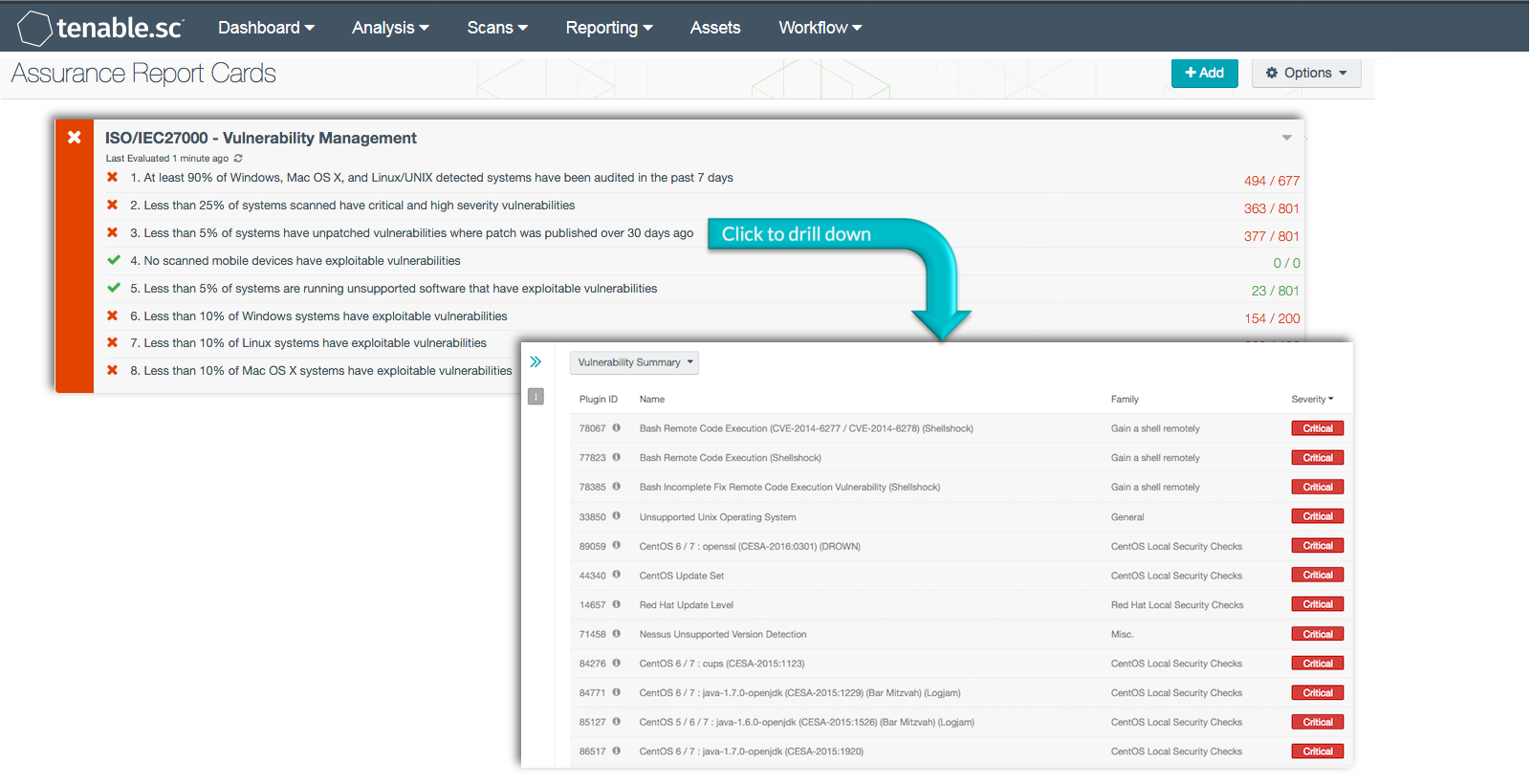
Not all vulnerability scans will obtain the most accurate results when detecting vulnerabilities, as many organizations have network devices that connect intermittently. Many of these transient devices can present additional security risks and no assurance of being fully patched or free from malware. This Assurance Report Card (ARC) will report on existing vulnerabilities across all active and passively detected devices, which can be used to measure and improve current vulnerability scanning and patch management efforts across the organization
Vulnerability scans often include large amounts of information on existing vulnerabilities, which can be difficult to prioritize. Information can include recommendations to disable unused services and user accounts, along with applying hotfixes and patching software. An effective vulnerability management strategy should also contain an effective asset management program. Together, this will allow organizations to obtain complete visibility into their current risk profile and ensure that vulnerabilities on all systems and devices are remediated in a timely manner. This ARC aligns with the vulnerability management controls of the ISO/IEC 27002 framework, which can be used to strengthen existing vulnerability management policies.
Many vulnerability scanning tools perform active scanning, which will only account for systems and devices that are currently connected to the network, and do not account for transient systems that connected to the network for a short amount of time. Using Tenable Passive Vulnerability Scanner (NNM), organizations will be able to fill the gap left by intermittent vulnerability scanning, and identify vulnerabilities on systems in real-time. Along with Tenable's Tenable.sc Continuous View (Tenable.sc CV), Tenable Nessus will actively scan the network for vulnerabilities, and provide an accurate snapshot of existing risks. Additionally, deploying Nessus Agents on systems will eliminate the need for scanning systems with credentials. Having a complete picture into existing vulnerabilities on the network will enable organizations to detect and respond faster to potential threats before critical systems are impacted.
Information presented within this ARC will report on how often systems are being scanned for vulnerabilities. Several policies will detect exploitable vulnerabilities across Windows, Linux, and Mac OS X systems. Attackers frequently target and exploit unpatched software to gain access and compromised internal systems. Organizations should take appropriate measures to patch exploitable vulnerabilities immediately. Additional policy statements focus on vulnerabilities that have been detected on scanned systems and mobile devices. Any delay in patching vulnerabilities could provide attackers the opportunity to exploit vulnerabilities, gain control over critical systems, and obtain access to confidential data.
This ARC is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The ARC can be easily located in the Feed under the category Compliance. The ARC requirements are:
- Tenable.sc 5.3.2
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
Tenable's Tenable.sc Continuous View (Tenable.sc CV) is the market-defining continuous network monitoring platform. Tenable Log Correlation Engine (LCE) performs automatic discovery of users, infrastructure, and vulnerabilities across more technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure. Tenable Nesuss Network Monitor (NNM) provides deep packet inspection to continuously discover and track users, applications, cloud infrastructure, trust relationships, and vulnerabilities. Tenable Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. Tenable.sc CV, which includes Nessus, LCE, and NNM, scales to meet future demand of monitoring virtualized systems, cloud services, and the proliferation of devices.
ARC Policy Statements:
At least 90% of Windows, Mac OS X, and Linux/UNIX detected systems have been scanned in the past seven days: This policy statement displays the number of Windows, Mac OS X, and Linux/UNIX systems that have been detected within the past seven days to the total number of Windows, Mac OS X, and Linux/UNIX systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. This policy statement will alert organizations to any new or existing systems that have been detected passively by NNM and actively by Nessus. Organizations should scan the network on a continual basis to ensure that every system is properly identified and evaluated.
Less than 25% of systems scanned have critical and high severity vulnerabilities: This policy statement displays the number of systems that have critical and high severity vulnerabilities to total number of systems with vulnerabilities. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Information within this policy statement includes detected vulnerabilities by critical, high, and medium severity levels. Continuous vulnerability scanning can help an organization identify weaknesses throughout the enterprise. Information provided within this policy statement can help organizations identify and reduce the number of vulnerabilities on the network.
Less than 5% of systems have unpatched vulnerabilities where a patch was published over 30 days ago: This policy statement displays the number of systems with unpatched vulnerabilities with a patch published over 30 days ago to total systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Unpatched vulnerabilities leave systems exposed to exploitation and should be patched as soon as possible.
No scanned mobile devices have vulnerabilities: This policy statement displays the number of systems with scanned mobile devices with vulnerabilities to the total number of scanned mobile devices. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Scanned mobile devices detected within this policy statement are considered unmanaged/non-MDM mobile devices. Unmanaged mobile devices often remain unpatched for long periods of time, and can present serious security risks for an organization. Organizations should monitor all scanned mobile devices to ensure that the device is authorized and up-to-date.
Less than 5% of systems are running unsupported software with exploitable vulnerabilities: This policy statement displays the number of systems running unsupported software with exploitable vulnerabilities to total systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Exploitable vulnerabilities on unsupported software can expose the network to malware, malicious users, and attacks. Information provided within this policy can be used to quickly target and remediate exploitable vulnerabilities.
Less than 10% of Windows systems have exploitable vulnerabilities: This policy statement displays the number of Windows systems with exploitable vulnerabilities to total Windows systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Windows is the most widely used operating systems within organizations and is frequently targeted by attackers. Exploitable vulnerabilities on Windows systems can expose the network to malicious code, intruders, and attacks. Information provided within this policy can be used to quickly target and remediate exploitable vulnerabilities.
Less than 10% of Linux systems have exploitable vulnerabilities: This policy statement displays the number of Linux-based systems with exploitable vulnerabilities to total Linux systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. The majority of Linux distributions are considered relatively secure. However, Linux systems are not immune from exploitable vulnerabilities or attacks. Exploitable vulnerabilities on Linux-based systems can expose the network to malicious software, intruders, and attacks. Information provided within this policy can be used to quickly target and remediate exploitable vulnerabilities.
Less than 10% of Mac OS X systems have exploitable vulnerabilities: This policy statement displays the number of Mac OS X systems with exploitable vulnerabilities to total Mac OS X systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Although Mac OS X is a relatively secure operating system, it is not immune from exploitable vulnerabilities or attacks. Exploitable vulnerabilities on Mac OS X systems can expose the network to malicious software, intruders, and attacks. Information provided within this policy can be used to quickly target and remediate exploitable vulnerabilities.