by Liz Hutto
March 24, 2022
A security researcher posted private chat messages between members of the Conti ransomware group, providing valuable insight into which vulnerabilities are leveraged by the group and affiliates in their cyber attacks. The Conti ransomware group has earned a reported $180 million in profits by leasing their Ransomware-as-a-Service (RaaS) model to cripple cyber-infrastructure in vulnerable organizations. Tenable has published a variety of content to assist customers with identifying the vulnerabilities leveraged by the Conti ransomware group and its affiliates.
Conti and their affiliates have had a particularly devastating impact on healthcare services, including at least 16 U.S. health and emergency networks. Conti attacked Ireland’s Health Service Executive (HSE), demanding a $20 million dollar ransom, which the HSE refused to pay, opting instead to shut down IT services for mitigation efforts.
Tenable’s 2021 Threat Landscape Retrospective report revealed that 24.7% of healthcare data breaches were the result of ransomware attacks, and ransomware itself was responsible for 38% of all breaches last year. The leaked data revealed that Conti and its affiliates have been exploiting a number of vulnerabilities. There are also reports that Conti and its affiliates have targeted vulnerabilities in the Fortinet FortiOS found in Fortinet’s SSL VPN devices to gain initial access to target environments.
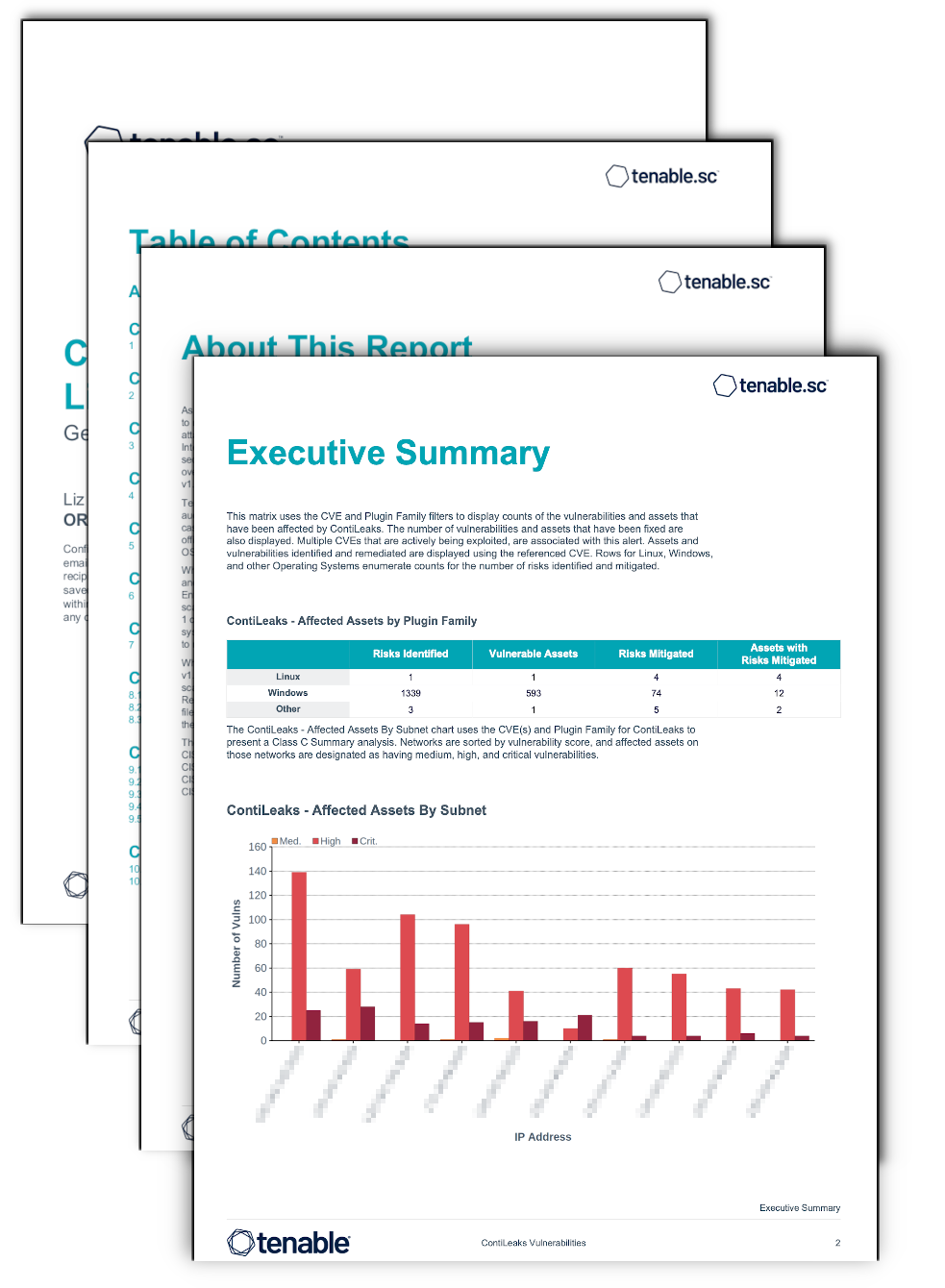
Organizations are often breached from legacy vulnerabilities present in the IT infrastructure of small companies they have recently acquired. The analysis of the ContiLeaks data identifies the vulnerabilities that are being actively exploited, enabling security managers to prioritize mitigation.
The Security Response Team (SRT) of Tenable Research has analyzed the ContiLeaks data to ensure customers are fully informed of their vulnerability to Conti RaaS attacks. The SRT also provides breakdowns for the latest vulnerabilities in the Tenable Blog. Tenable Research has released over 165,000 plugins and leads the industry on CVE coverage. Tenable's SRT team continuously works to help organizations prioritize and create remediation plans for the new threats, which often leave very little time for reflection.
This report contains the following chapters:
Executive Summary Chapter - Contains information from the ContiLeaks Dashboard that uses the CVE and Plugin Family filters to display counts of the vulnerabilities and assets that have been affected by ContiLeaks.
Linux Chapter - Contains charts and tables that group together ContiLeaks related CVEs for all Linux Operating Systems and includes an IP Detail for the hosts identified.
Windows Chapter - Contains charts and tables that group together ContiLeaks related CVEs for all Windows Operating Systems and includes an IP Detail for the hosts identified.
Other Chapter - Contains charts and tables that group together ContiLeaks related CVEs for all "Other" Operating Systems and includes an IP Detail for the hosts identified.