by Josef Weiss
March 22, 2017
Developed in 1988, OpenSSL is an open source toolkit and cryptographic library for the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. OpenSSL is used in a number of technologies from virtual private networks (VPN), network file shares (NFS), domain name servers (BIND), Java, and more. Other common use cases are to secure communications using https and to create certificate authorities. OpenSSL is mostly found in server side implementations and is commonly used by a wide variety of web servers. There are many versions of OpenSSL in existence. In some instances, OpenSSL libraries may be installed on a host even if the application itself is not running, potentially opening hosts to risks of compromise.
Notable OpenSSL vulnerabilities have included Heartbleed, timing attacks on RSA keys, and Change Cipher Spec (CCS) Injection Vulnerabilities. The POODLE vulnerability, while mostly directed at SSL v3.0, also affected vulnerable SSL/TLS OpenSSL libraries. A critical element in understanding potential OpenSSL risks is the identification of the installed OpenSSL applications, libraries, and versions within an organization's environment.
Organizations can save development costs by utilizing open-source projects such as OpenSSL, but they need to remain diligent in keeping the code up to date. Understanding which OpenSSL versions and vulnerabilities are present in the environment is a critical aspect of risk reduction. This dashboard provides the analyst with the ability to better prioritize OpenSSL patching efforts and highlights the networks which may have the greatest potential for concern. In addition to identifying risks associated with each OpenSSL version back to pre-2006, analysts can discover OpenSSL installations of which they might not even be aware, further decreasing the cost of analysis in determining the best approach to remediate OpenSSL vulnerabilities.
The dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 5.4
- Nessus 6.10.0
- PVS 5.2.0
Tenable SecurityCenter Continuous View (CV) is the market-defining continuous network monitoring solution, and assists in securing an organization’s internal network. SecurityCenter CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to detect vulnerabilities within operating systems, software applications, and hardware. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Passive listening provides real-time discovery of vulnerabilities on operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. Host data and data from other security products is analyzed to monitor activity from patch management solutions and services. SecurityCenter CV provides an organization with the most comprehensive view of the network and the intelligence needed to fully understand the impact of OpenSSL vulnerabilities on the network.
The following components are included within this dashboard:
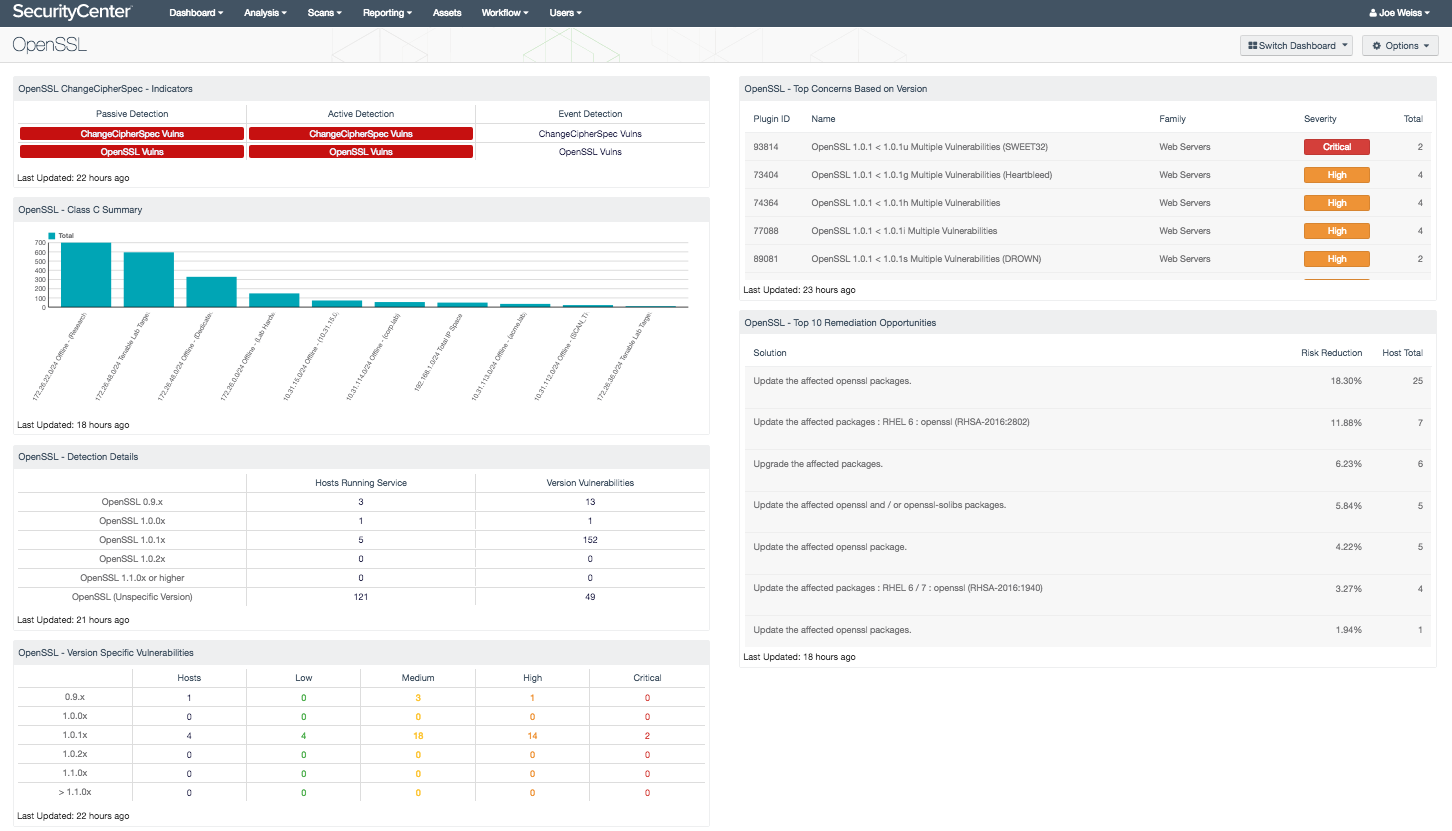
- OpenSSL ChangeCipher Spec - Indicators - This component provides an overview of OpenSSL vulnerabilities and the related ChangeCipherSpec vulnerabilities. There are three columns, one for each vulnerability type (active, passive, event). Each column has an indicator for the six CVEs related to OpenSSL ChangeCipherSpec vulnerability, and one indicator for all OpenSSL related vulnerabilities. The active and passive indicators will turn red, signifying immediate action should be taken, while the event vulnerabilities are orange and signify that administrators should investigate the true severity of the event.
- OpenSSL – Detection Details - This matrix displays the OpenSSL versions detected as running in the environment and identifies the total number of vulnerabilities associated with each version.
- OpenSSL – Version Specific Vulnerabilities - This matrix displays OpenSSL vulnerabilities by specific OpenSSL version, displayed by row. Each row presents columns showing the number of hosts and counts of vulnerabilities by severity from low to critical.
- OpenSSL – Top Concerns Based on Version - This table displays OpenSSL vulnerabilities by OpenSSL version. Vulnerabilities are ranked from most to least severe.
- OpenSSL – Top 10 Remediation Opportunities - This component displays which remediation opportunities should be targeted to achieve the largest reduction of identified OpenSSL vulnerabilities.
- OpenSSL – Class C Summary - This chart displays OpenSSL vulnerabilities by Class C subnet. Vulnerabilities displayed are for all severity levels and are sorted into Class C address blocks.