by Josef Weiss
December 21, 2022
2022 began with concerns over supply chains and Software Bills of Material (SBOM) as organizations worldwide were forced to reconsider how they respond to incidents in anticipation of the next major event. Tenable’s Security Response Team (SRT) continuously monitors the threat landscape throughout the year, always at the forefront of trending vulnerabilities and security threats. This dashboard provides a summary of Tenable data that has been compiled over the past year.
In a year marked by hacktivism, ransomware and attacks targeting critical infrastructure in a turbulent macroeconomic environment, organizations struggled to keep pace with the demands on cybersecurity teams and resources. Attacks against critical infrastructure remained a common concern. Ransomware continued to wreak havoc, even as some groups had operations shuttered by law enforcement, collapsed under the weight of internal power struggles, or splintered into new groups. New and complex vulnerabilities emerged, providing remediation challenges.
Perhaps most alarming is that the vulnerabilities of years past continue to haunt organizations. In fact, known flaws were so prominent inn 2022 that they warranted a spot on Tenable’s list of top vulnerabilities of 2022. We cannot stress this enough: Threat actors continue to find success with known and proven exploitable vulnerabilities that organizations have failed to patch or remediate successfully.
The constant evolution of the modern digital environment introduces new challenges for security practitioners. Successful security programs must take a comprehensive approach and understand where the most sensitive data and systems reside and what vulnerabilities or misconfigurations pose the greatest risk. Given the brisk rate of digital transformation, a complete understanding of the external attack surface is paramount.
With thousands of new vulnerabilities patched each year, only a small subset will ever see active exploitation. Focusing resources on the vulnerabilities that are exploitable and understanding how attackers chain vulnerabilities and misconfigurations enables security teams to design comprehensive strategies to reduce their overall risk exposure.
The Tenable 2022 Threat Landscape Report (TLR) inspects key aspects of the cybersecurity landscape and describes how organizations can revise their programs to focus on reducing risk. The TLR covers:
- Significant vulnerabilities disclosed and exploited throughout the year, including how common cloud misconfigurations can affect even large tech companies
- The continuous transformation of the ransomware ecosystem and the rise of extortion-only threat groups
- Ongoing risks, vulnerabilities and attacks within the software supply chain
- Tactics used by advanced persistent threat groups to target organizations with cyber espionage as well as financially motivated attacks.
- Breach factors and the challenges in analyzing breach data, given the limited information available and lack of detailed reporting requirements
- Details of the key vulnerabilities affecting enterprise software
Tenable Research delivers world class cyber exposure intelligence, data science insights, alerts, and security advisories. The Tenable Research teams perform diverse work that builds the foundation of vulnerability management. The Security Response Team (SRT) tracks threat and vulnerability intelligence feeds and provides rapid insight to the Vulnerability Detection team, enabling them to quickly create plugins and tools that expedite vulnerability detection. This fast turnaround enables customers to gain immediate insight into their current risk posture. Tenable Research has released over 180,000 plugins and leads the industry on CVE coverage. Additionally, the SRT provides breakdowns for the latest vulnerabilities on the Tenable Blog and produces an annual Threat Landscape Report. The SRT continuously analyzes the evolving threat landscape, authors white papers, blogs, Cyber Exposure Alerts, and additional communications to provide customers with comprehensive information to evaluate cyber risk.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.sc discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture. The requirements for this dashboard is: Nessus.
Components
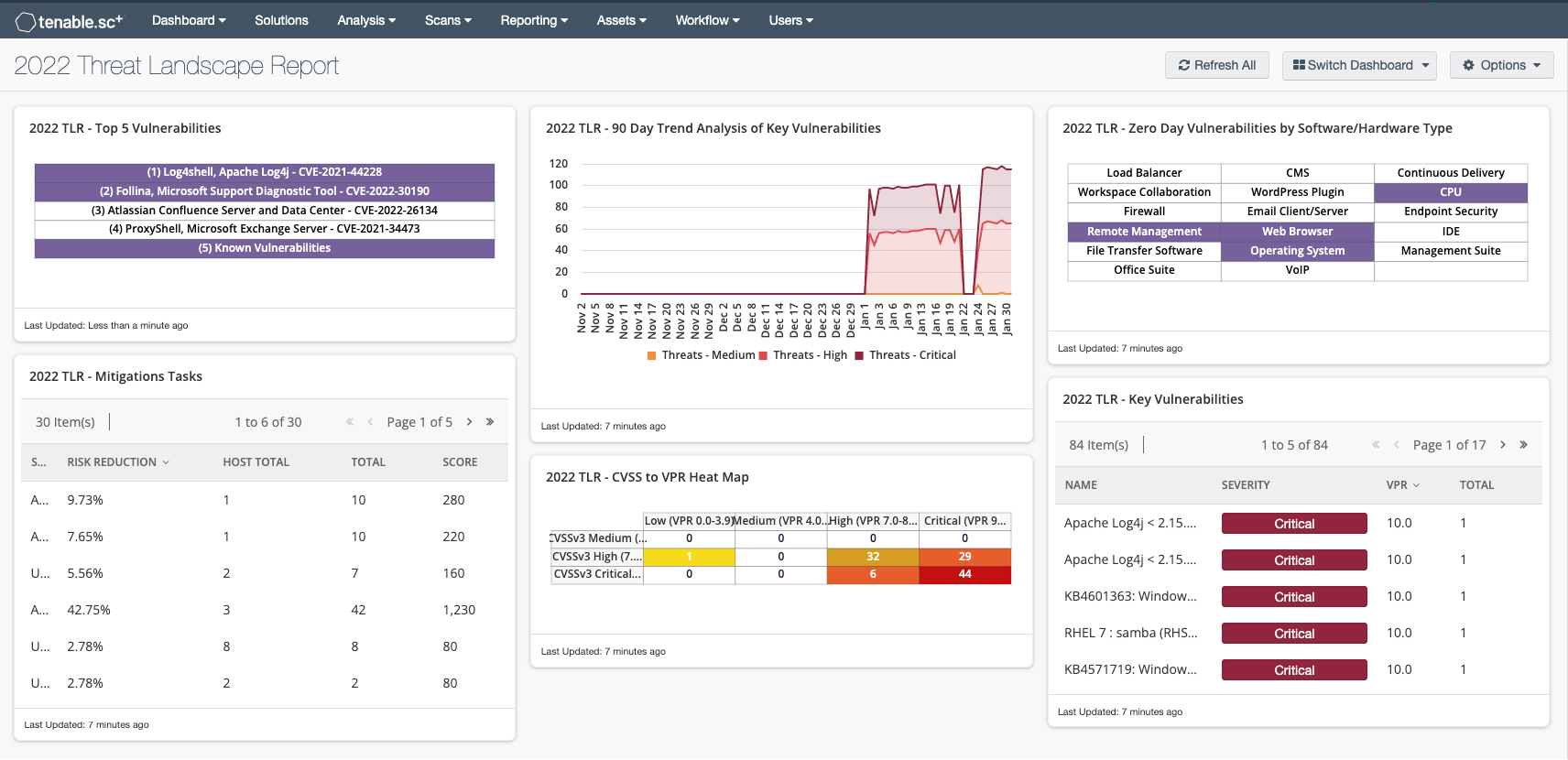
TLR 2022 – Top 5 Vulnerabilities: This component features the top five vulnerabilities of 2022 as described in Tenable's 2022 Threat Landscape Report: Log4shell, Apache Log4j - CVE-2021-44228, Follina, Microsoft Support Diagnostic Tool - CVE-2022-30190, Atlassian Confluence Server and Data Center - CVE-2022-26134, ProxyShell, Microsoft Exchange Server - CVE-2021-34473, and Known Vulnerabilities - CVE-20XX-XXXX.
2022 TLR – Mitigation Tasks: This component provides a list of patches that mitigate the key vulnerabilities in 2022, leveraging the CVEs identified in Tenable's 2022 Threat Landscape Report (TLR). The Remediation Summary tool uses the concept of a Patch Chain, and identifies the top patch to be remediated for the greatest risk reduction. When the top patch is applied, all other patches in the chain will be remediated.
2022 TLR – 90 Day Trend Analysis of Key Vulnerabilities: This component provides a 90-day analysis of the most notable vulnerabilities in 2022, leveraging the CVEs identified in Tenable's 2022 Threat Landscape Report (TLR). There are over 180 CVEs discussed in the TLR, which, combined with the trend line, helps risk managers determine how risk has been reduced over a period of 90 days. The vulnerability last observed filter is set to 1 day to display risk changes on a daily basis.
2022 TLR CVSS to VPR Heat Map: This component provides a correlation between CVSSv3 scores and Vulnerability Priority Rating (VPR) scoring for the key vulnerabilities listed in the 2022 Threat Landscape Report (TLR). The CVSSv3 scores are the standard scoring system used to describe the characteristics and severity of software vulnerabilities. Tenable's VPR helps organizations refine the severity level of vulnerabilities in the environment by leveraging data science analysis and threat modeling based on emerging threats. Each cell is comprised of a combination of cross-mapping of CVSS, VPR scoring, and 2022 CVE identifiers. Using a heat map approach, the filters begin in the left upper corner with vulnerabilities that present least risk. Moving to the right and lower down the matrix the colors change darker from yellow to red as the risk levels increase. Tenable recommends that operations teams prioritize remediation for risks in the lower right corners, and then work towards the upper left cells.
2022 TLR – Zero Day Vulnerabilities by Software/Hardware Type: This component displays a list of software/hardware that had zero-day vulnerabilities described in the 2022 Threat Landscape Report (TLR). Each indicator uses CVE from the report through the entire 2022 year. Details are provided in Tenable's 2021 Threat Landscape Report (TLR).
2022 TLR Key Vulnerabilities: This component displays cells for the most significant vulnerabilities of 2022 using CVE filters from the 2022 Threat Landscape Report. These filters display the key vulnerabilities from 2022 as well as the notable legacy vulnerabilities from prior years. Details are provided in Tenable's 2022 Threat Landscape Report.