by Josef Weiss
February 25, 2016
The proliferation of unsupported products is an issue for many organizations and increases the effort required to minimize risk. The Department of Homeland Security has issued alerts stating that running unsupported software opens your business up to elevated cybersecurity risks. As applications reach their end-of-life (EOL), vendors stop offering support. As patches and updates are released for new versions of software, unsupported versions will be left out. Essentially zero-day vulnerabilities could be in effect for applications that are no longer supported. Therefore, security and stability decrease, raising concern as time progresses. Identifying systems running unsupported applications is an important part of assessing and minimizing organizational risk.
The Center for Internet Security (CIS) provides a list of 20 security controls, the CSC 20 (Critical Security Controls) for effective cyber defense, formerly the SANS Top 20. Control 2 identifies risks associated with unauthorized software. Identifying unauthorized software is critical to help secure the environment. Unauthorized software may contain vulnerabilities, by exploitable by malware, and reduce productivity with no vendor support. Potentially copyrighted, counterfeit, or unlicensed materials can put an organization at risk for legal action.
This report is comprised of two chapters that report on unsupported and unauthorized products found in the environment. Elements include pie charts and tables to display, track, and report on unsupported and unauthorized applications.
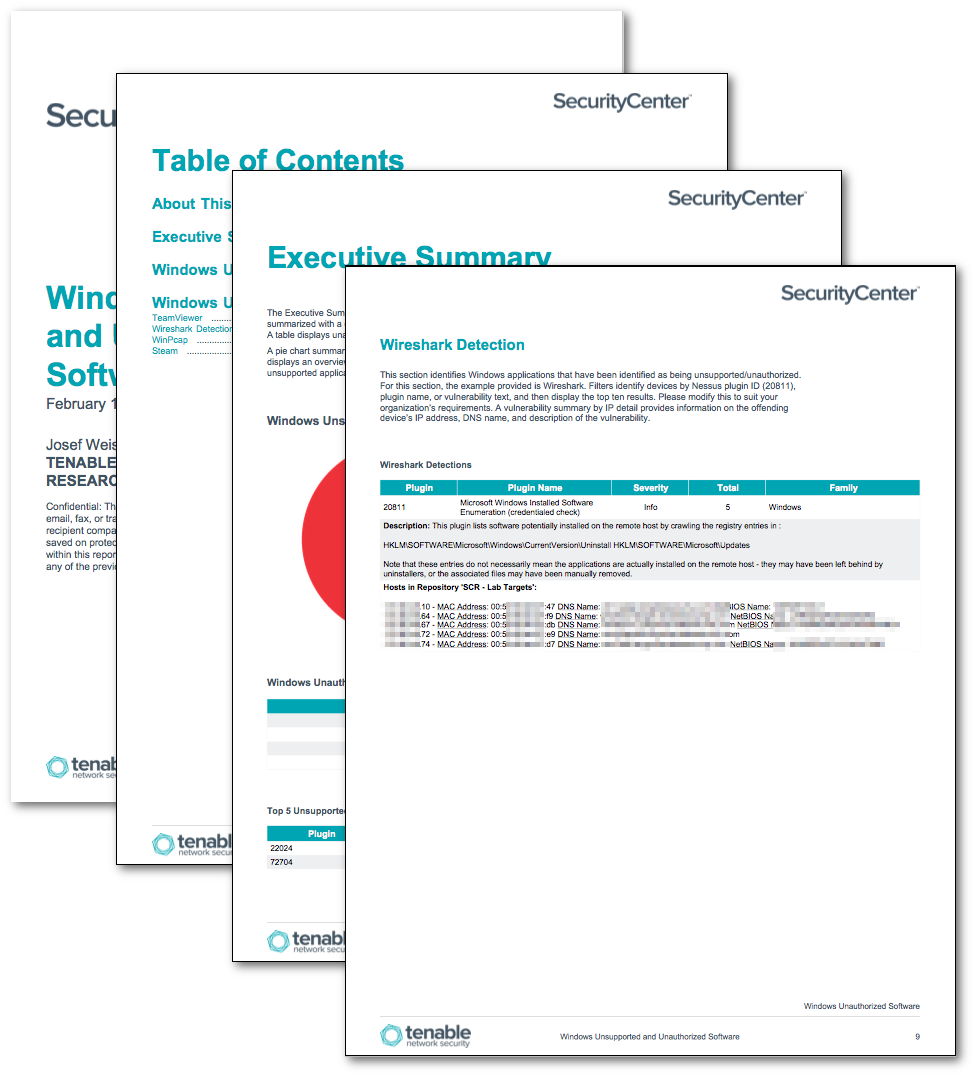
Vulnerability data for unsupported vulnerabilities is filtered using Nessus plugin 20811, Microsoft Windows Installed Software Enumeration, as well additional filters for unsupported applications. Unauthorized software components will require additional customization by the analyst. Once an organization has determined which software is considered as unauthorized, tables and filters can be modified to reflect that policy.
Within this report, reporting sections include Wireshark, WinPcap, TeamViewer, and Steam as a reporting example. One suggested method is to use asset lists to identify black list software that the analyst would like to identify and track. Then utilize the asset list as a filter for reporting host details. Another method would be to replace the filters contained in this chapter with keywords that identify software the organizations policies have determined to be inappropriate. Using these examples, the analyst can modify the details and create new chapters or tables specific to the organization’s needs.
The report is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The report can be easily located in the SecurityCenter Feed under the category Threat Detection and Vulnerability Assessments.
The report requirements are:
- SecurityCenter 5.2.0
- Nessus 6.5.4
SecurityCenter Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. SecurityCenter CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new types of regulatory compliance configuration audits. SecurityCenter CV allows for the most comprehensive and integrated view of network health.
The report contains the following components:
- Executive Summary - The Executive Summary provides an overview of the two chapters of this report. Each chapter is summarized with a chart, which displays details of the unsupported products, along with severity information. A table displays unauthorized software and the count of how many were found in the environment.
- Unsupported Software - The Unsupported Software chapter provides details on software that is no longer supported by the vendor. Systems running unsupported software are more vulnerable to exploitation.
- Unauthorized Software - The Unauthorized Software chapter provides details on software that has been identified by organization policy to be unauthorized. Systems running unauthorized software may introduce viruses, malware, and reduce productivity. Potentially copyrighted, counterfeit, or unlicensed materials can put an organization at risk for legal action.