by Stephanie Dunn
November 17, 2016
Monitoring critical changes within a network can be overwhelming for any organisation to manage effectively. Changes that go unmonitored within network security devices, privileged user accounts, unsupported products, and cryptographic controls could lead to vulnerabilities in critical systems. The Australian Prudential Regulation Authority (APRA) and the associated Prudential Practice Guides (PPG) aim to assist regulated institutions by outlining prudent practices that can aid in managing security risks within specific elements of their business. This dashboard covers key concepts within the PPG CPG 234 guide that can assist with areas such as monitoring IT security solutions, suspicious network events, privileged user account changes, and tracking outdated software.
The APRA developed a series of PPGs specifically designed to address specific compliance requirements for regulated institutions. The CPG 234 - Management of Security Risk in Information and Information Technology PPG guide was developed to provide guidance for management and IT security specialists in identifying, targeting, and managing IT security risks.
The information presented within this dashboard has been developed to assist organisations with lifecycle management, monitoring IT security solutions, network processes, auditing and accountability, change management, and encryption solutions within the enterprise. Additionally, these concepts also align with 21 mitigation strategies from the Australian Signals Directorate (ASD) list of Strategies to Mitigate Targeted Cyber Intrusions (ASD Top 35 Mitigation Strategies) framework, which addresses patch management vulnerabilities, network security solutions, unsupported software, log and event collection, suspicious behaviour, encryption concerns, and effectiveness of existing controls. Components will notify analysts to user changes, new devices, and configuration changes that could be considered unauthorised or malicious.
Monitoring security solutions such as firewalls, proxies, IPS, IDS, and anti-malware tools can highlight misconfigurations or vulnerabilities that could adversely impact the network. Identifying systems using outdated operating systems or software can highlight critical systems that may be vulnerable to exploitation. Tenable Nessus will scan patch management systems and report on any vulnerabilities that have been discovered. Event data on user account activity can assist in monitoring both performed or attempted administrative actions by users. Tracking cryptographic controls currently in use will highlight potential misconfigurations or insecure encryption protocols being used. Monitoring event changes highlights compromised systems that have been infected with malware, unusual patterns of behaviour, data leakage, and potential attacks already in progress. Collecting log data helps track key events, identify critical changes, and provide an audit trail for active investigations and incident-detection analysis.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.3.1
- Nessus 8.5.1
- NNM 5.9.0
- LCE 6.0.0
Tenable Network Security transforms security technology for the business needs of tomorrow through comprehensive solutions that provide continuous visibility and critical context, enabling decisive actions to protect the organization. Tenable.sc is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audit files. Active scanning examines running systems and services, detects vulnerable software applications, and analyses configuration settings. Passive listening collects data to continuously monitor traffic, collect information about user privilege changes, and administrative activity, along with the discovery of additional vulnerabilities. Monitoring the network to ensure that all systems are secured against vulnerabilities is essential to ongoing security efforts. Tenable enables powerful, yet non-disruptive, continuous monitoring that will enable organizations with the information needed to proactively respond to threats within the enterprise.
The following components are included in this dashboard:
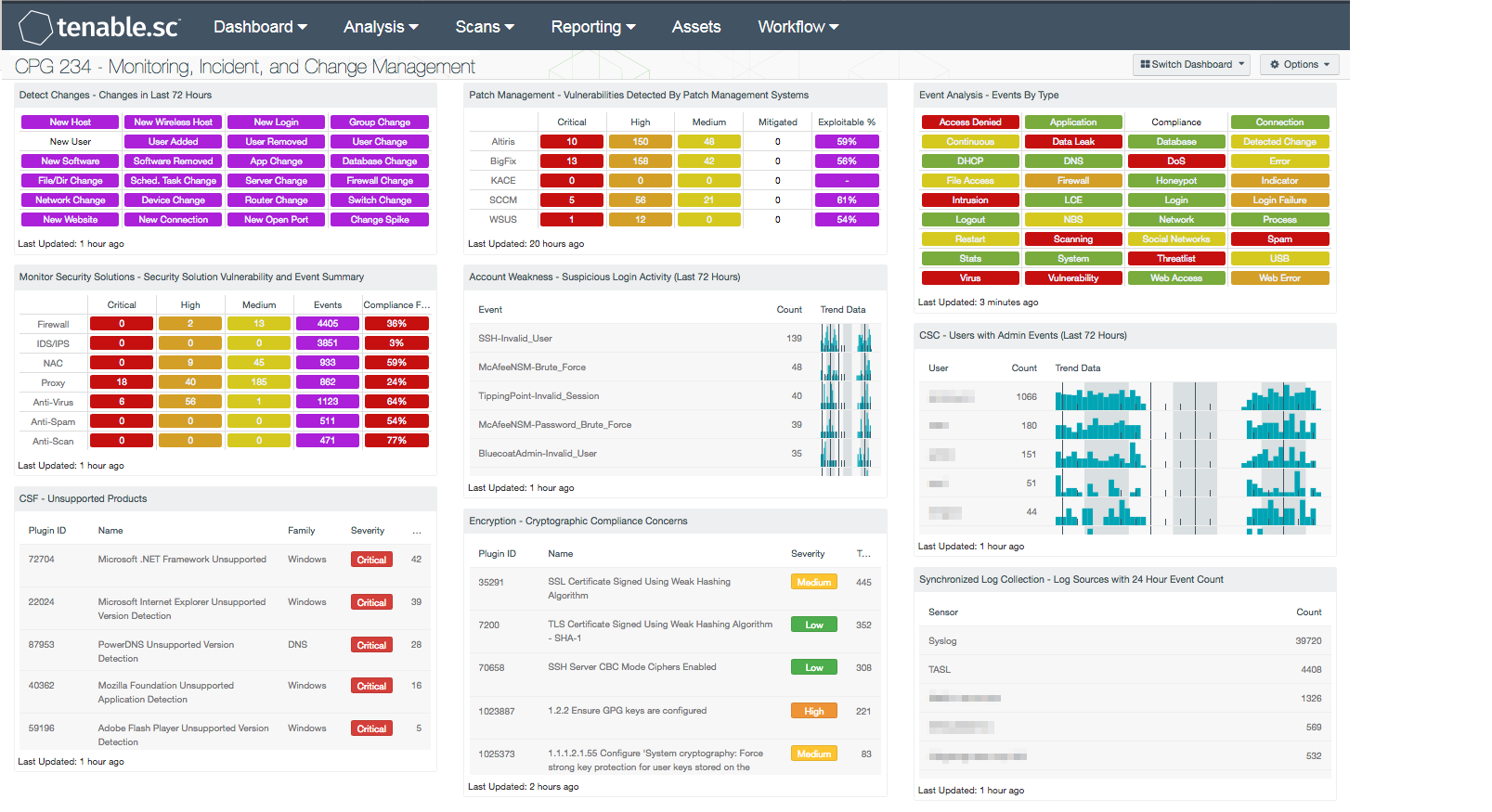
- Detect Changes – Changes in Last 72 Hours: This component assists in maintaining up-to-date inventories and detecting changes. The matrix presents indicators for network changes detected in the last 72 hours. Each indicator is based on one or more Tenable Log Correlation Engine (LCE) events; the indicator is highlighted purple if the event occurred in the last 72 hours.
- Monitor Security Solutions – Security Solution Vulnerability and Event Summary: This component presents indicators that will alert to vulnerabilities, events, and compliance issues on security solutions within a network. Devices and services such as firewalls, IDS/IPS, NAC, anti-virus, and anti-malware are all designed to protect networks against attacks and other forms of malicious activity. Each row includes the respective security solution category, which highlights critical, high, and medium severity vulnerabilities, along with event data, and compliance failures for each category. Using this data, organizations can identify events and mitigate detected vulnerabilities on security devices or services across the network. Data presented within this component can be modified to include additional or specific information per organizational requirements.
- CSF – Unsupported Products: This table displays all unsupported products by name, sorted by severity. Displayed is the plugin ID, product name, plugin family, severity, and the total found. This component identifies unsupported products by filtering on the text “unsupported” in the vulnerability plugin name. Products and applications that are no longer supported can be serious security risks, as any vulnerabilities will no longer be patched by the vendor.
- Patch Management – Vulnerabilities Detected By Patch Management Systems: This matrix presents an overview of detected vulnerabilities reported by patch management systems. Tenable supports a wide variety of patch management solutions including SCCM, WSUS, IBM BigFix, Dell KACE K1000, and Symantec Altiris. Vulnerabilities are filtered by the Windows: Microsoft Bulletins plugin family, and presents a list of Microsoft vulnerabilities that have been reported by a patch management system. Each column presents the total count of vulnerabilities per severity level, mitigated vulnerabilities, and percentage of exploitable vulnerabilities. Analysts can use this component to compare the effectiveness of existing patch management systems, and how often systems are being patched.
- Account Weakness – Suspicious Login Activity (Last 72 Hours): This component presents an overview of suspicious login events reported within the last 72 hours on a network. Event data can include login attempts using invalid or unknown user accounts, brute force attacks, and login attempts using an invalid password. Analysts can drill down into the table to obtain additional information on the detected event. Clicking on Browse Component Data icon will bring up the event analysis screen to display the summary events and allow further investigation. Setting the tool to Raw Syslog Events can provide additional details such as IP addresses, the date and time the event occurred, user account, and ports used.
- Encryption - Cryptographic Compliance Concerns: This table presents a summary of both compliance concerns and vulnerabilities associated with encryption and cryptographic issues. Information presented in this component can highlight issues such as weak hashing algorithms and keys as well as the use of insecure encryption ciphers, including SSLv2, SSLv3, and TLSv1.0. Data is sorted by the highest number of compliance and vulnerability concerns at the top, which can assist in prioritizing remediation efforts. Many of these issues are the result of misconfigurations or use of outdated encryption methods. This component also includes vulnerabilities that can be exploited by attackers. Security teams should review the data to determine the risks to the organization.
- Event Analysis – Events By Type: This indicator provides a series of indicators for each event type, and is refreshed every 24 hours. This matrix allows the security administrator to receive information on current events.
- CSC – Users with Admin Events: This table presents those users associated with events that indicate performed or attempted administrative actions. The table is sorted so that the users with the most detected events are at the top. The user associated with an event cannot always be determined, so there will likely be a large number of events for the “unknown” user. Any unexpected users in this list should be further investigated to determine why and how they are executing administrative actions.
- Synchronized Log Collection – Log Sources with 24 Hour Event Count: This component identifies log sources and helps the organization ensure that all systems that can send logs are sending them to LCE and/or allowing NNM to scan them. Identifying patterns of suspicious behavior using NNM, and sending these logs to the LCE, will show correlated events across multiple workstations and servers.