Prioritize Hosts Dashboard

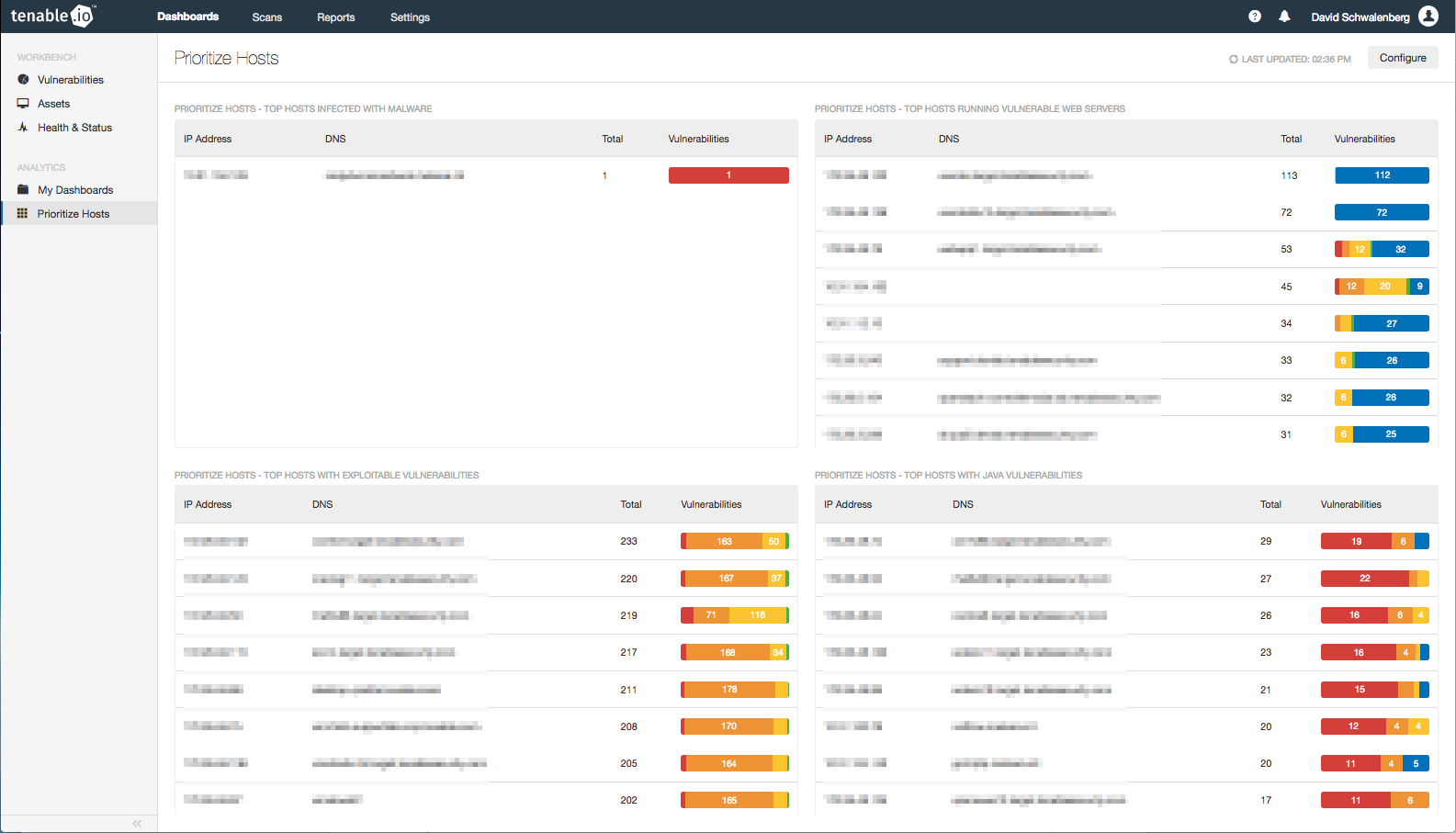
What systems on your network need attention now? With all the administrative work you need to have done by yesterday, how do you prioritize mitigation efforts to deal with host vulnerabilities? The enhanced vulnerability detection capabilities of Tenable.io™ can help you make the best prioritization decisions for keeping your network secure. The Prioritize Hosts dashboard presents several lists of hosts requiring immediate attention, such as top hosts infected with malware and top hosts with exploitable vulnerabilities, to help you decide which hosts should be prioritized first.
Top priority assets to secure
The Top Hosts Infected with Malware table displays the top hosts on the network that have detected malware infections. The plugin family Backdoors is used to detect malware on the hosts. A count of malware detections and a bar graph indicating the severity of the malware are given for each host. The hosts presented in this table are probably already compromised, making them the highest priority to deal with before an infection can spread.
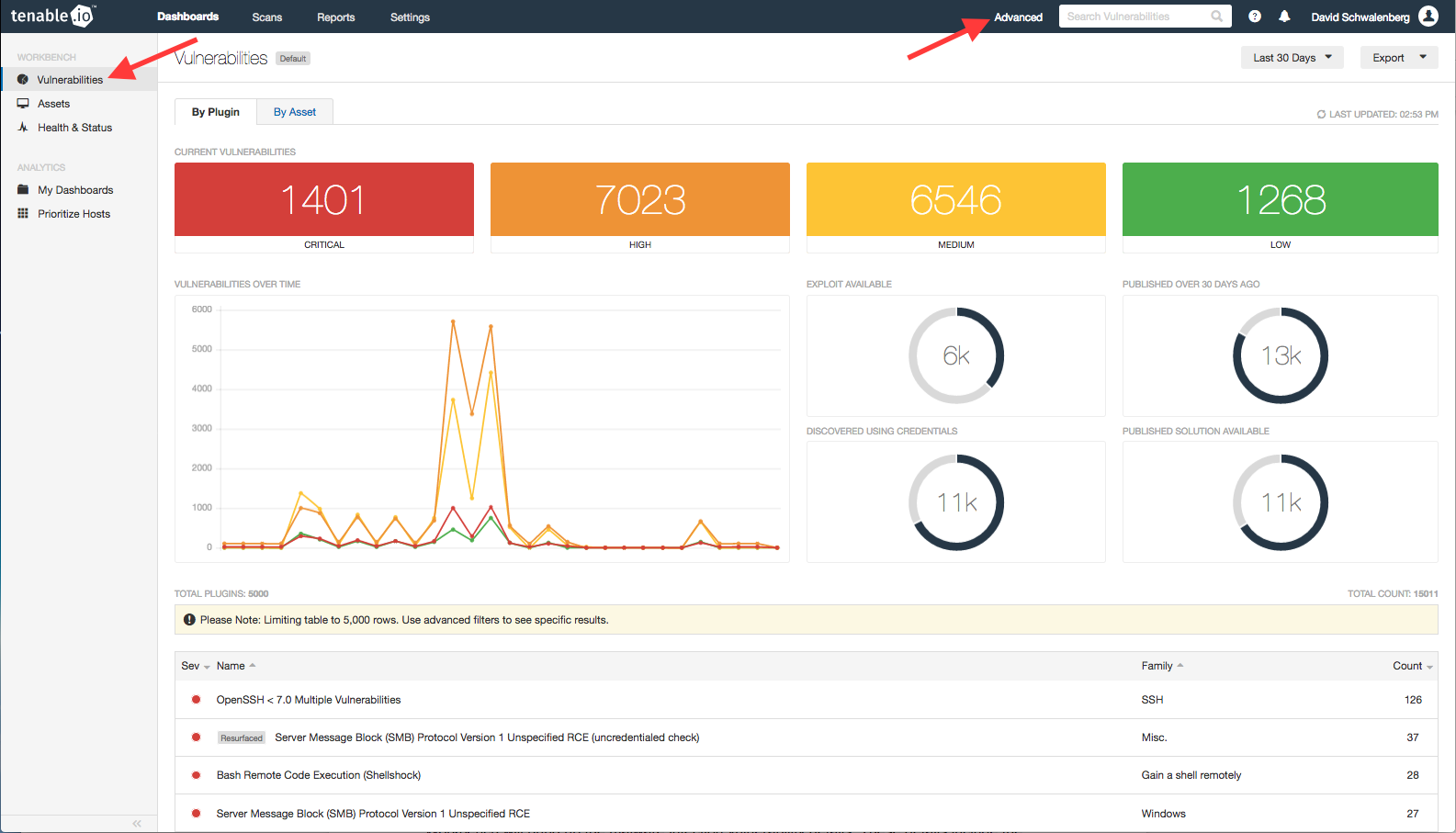
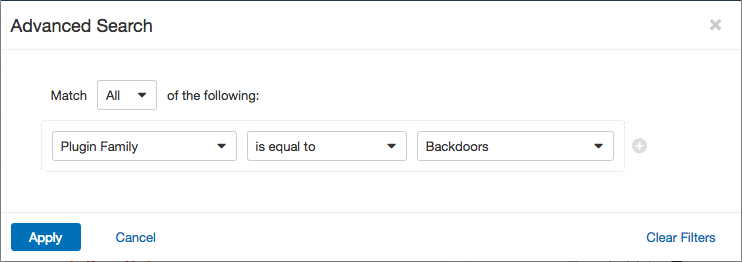
To learn more about these malware infections, go to the Vulnerabilities Workbench and set an Advanced filter of Plugin Family equal to Backdoors:
Once the filter is applied, clicking on individual vulnerabilities in the table at the bottom of the Workbench will bring up the malware infection vulnerability details. These details include the vulnerability description and the assets the vulnerability was detected on, and may also include information such as plugin output, last seen time, and solution information.
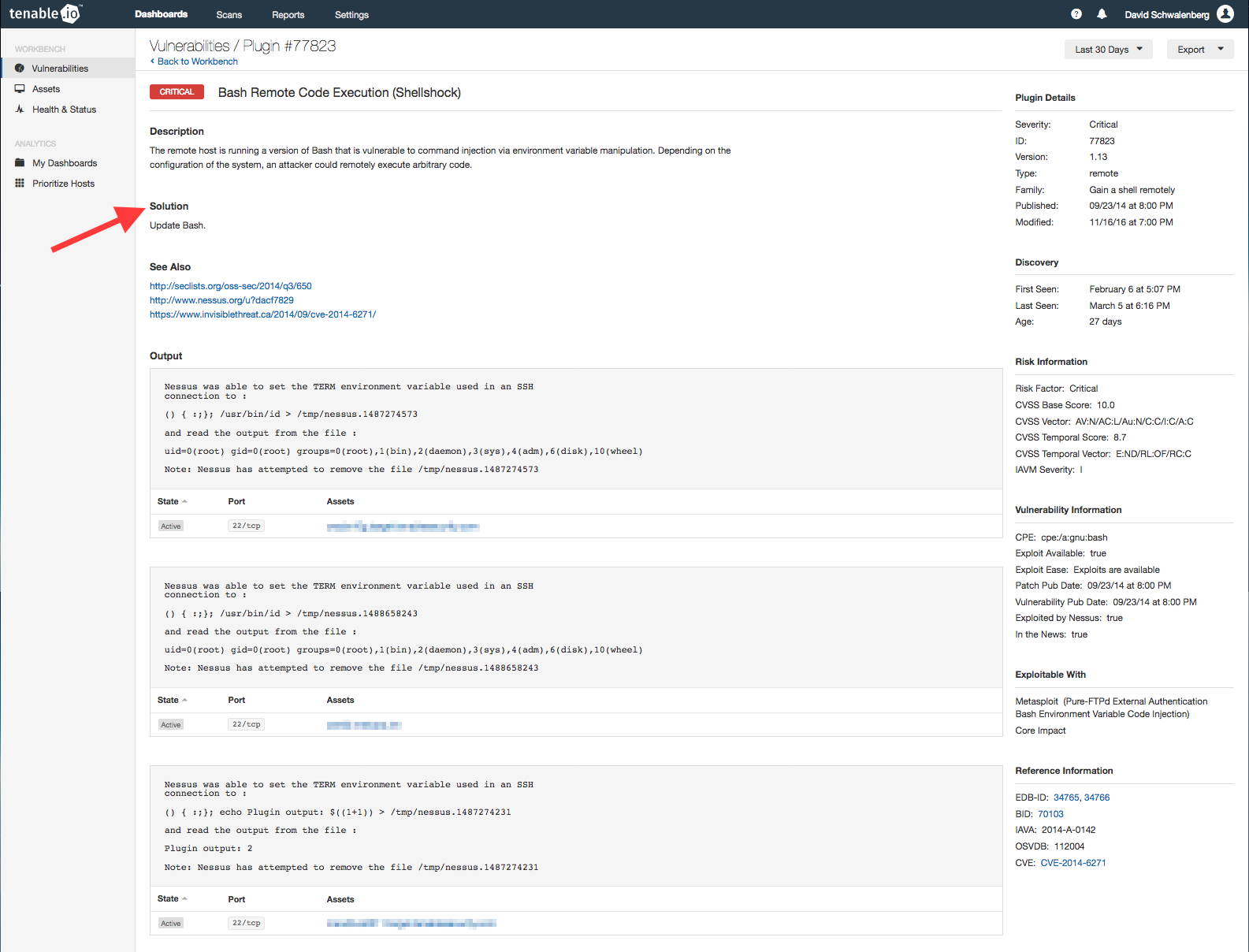
The Top Hosts with Exploitable Vulnerabilities table displays the top hosts on the network that have vulnerabilities that are known to be exploitable. Well-known exploits such as Shellshock are added to exploit frameworks like Metasploit or Core Impact to allow pen testers to exploit vulnerable systems. Unfortunately, malicious adversaries also use these frameworks to attack companies. This table is showing systems that are vulnerable to these frameworks and other malware known to exist in the wild. I find these vulnerabilities particularly concerning because any script kiddie can easily knock over any of your machines that have one of these vulnerabilities. I recommend making these hosts a high priority to lock down—especially if they are internet-facing!
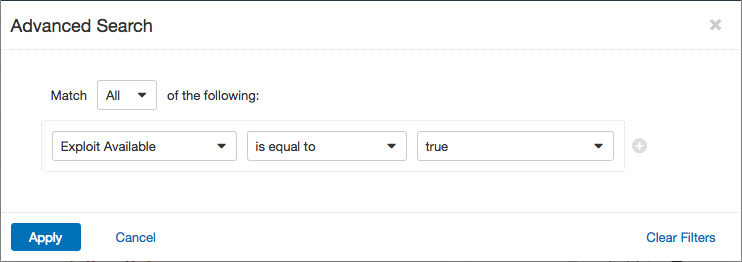
To learn more about these exploitable vulnerabilities, go again to the Vulnerabilities Workbench and this time set the Advanced filter of Exploit Available equal to true:
As before, clicking on an individual vulnerability will bring up the details:
These details provide lots of useful information, including the vulnerability description and the assets the vulnerability was detected on. Also included may be plugin output, when the vulnerability was first seen, reference information, and links to go to for more information. Most importantly, solutions to the vulnerabilities are given. In almost all cases, the solution to these exploitable vulnerabilities is to patch your applications and operating systems, and upgrade older versions of software.
Prioritizing assets using vulnerability plugin families
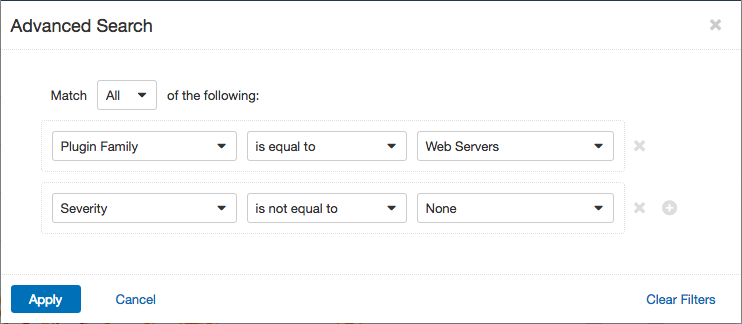
The Top Hosts Running Vulnerable Web Servers table displays the top hosts with web server vulnerabilities and vulnerabilities in web technologies such as PHP and OpenSSL. These vulnerabilities are troublesome because they may allow an attacker to access data that should not be publicly accessible. Leakage of this data can lead to loss of sensitive information and may even put people at risk of identity theft. You will likely discover that you have more web servers on your network than you thought you did, which is a security risk as well! Make sure all detected web servers are authorized, and that they are properly secured.
For details on these web server vulnerabilities, go to the Vulnerabilities Workbench and set the Advanced filter of Plugin Family equal to Web Servers. In addition, to only display those vulnerabilities that are of most concern, set a filter of Severity not equal to None:
Both the Top Hosts Infected with Malware table and the Top Hosts Running Vulnerable Web Servers table make use of filters on Plugin Family. You can use other plugin family filters to detect other types of vulnerabilities on assets. For example, you may want to know how vulnerable your databases are: you can use the Databases plugin family. Other plugin family suggestions are Firewalls, SCADA, Cisco, and local security checks for various operating systems. Use the plugin families that are appropriate in your environment to help you prioritize assets to secure, and check the vulnerability details for guidance on how to secure the assets.
Prioritizing assets using vulnerability keywords
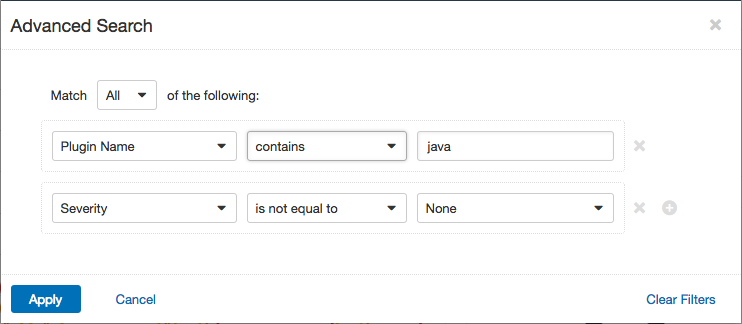
The final table on the dashboard, Top Hosts with Java Vulnerabilities, uses a keyword filter for “java” in the Plugin Name to display the top hosts with Java vulnerabilities. These vulnerabilities include outdated versions of Java and the Java Development Kit (JDK), and vulnerabilities in applications that use Java. Because of the filter, concerns with JavaScript will also be included. Since Java is so commonly used on all kinds of devices, Java vulnerabilities can potentially open up huge security holes. These vulnerabilities must be dealt with as soon as possible.
For details on these vulnerabilities, go to the Vulnerabilities Workbench and set the Advanced filter of Plugin Name to contains java (the filter is not case sensitive):
You can use other Plugin Name keywords to detect other types of vulnerabilities. For example, use “adobe” to find vulnerabilities in Adobe products, “unsupported” to find products that are no longer supported, “default”, “malicious process”, and “xss”. These and other plugin name keywords may be appropriate in your environment and can help you prioritize assets to secure. Experiment a bit! There are many possible filters; find the ones that best help your organization discover vulnerabilities that are the highest priority to fix.
Flexible licensing
The Tenable.io Vulnerability Management platform accurately captures vulnerabilities on transient and dynamic assets. Because asset data can change constantly, Tenable’s new Elastic Asset Licensing model employs an advanced algorithm to track changing asset attributes across the network over time. This asset-based model helps you recover licenses for temporary systems and isolated assets that are scanned periodically.
Try Tenable.io
Tenable.io provides accurate information on how well your organization is addressing security risks, and helps track improvements over time. Try Tenable.io Vulnerability Management free for 60 days.
- Vulnerability Management