by Cody Dumont
October 10, 2016
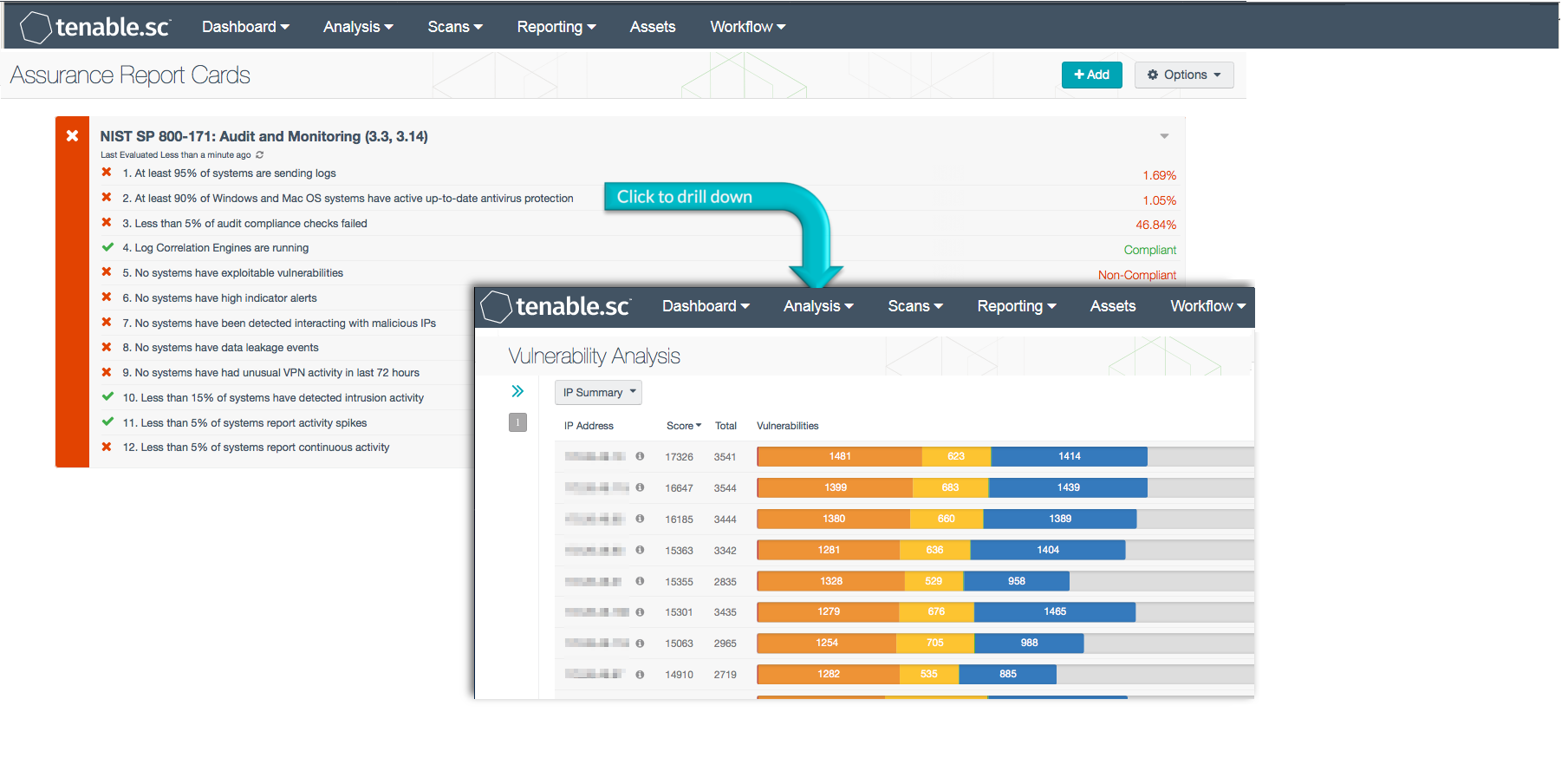
Protecting and retaining records, monitoring systems security alerts, and identifying system flaws in a timely manner are essential to protecting information systems. Monitoring inbound and outbound communications is essential to detect attacks, and potential indicators of attacks. Improperly maintained systems, accounts, or audits will hinder investigations concerning inappropriate system activity, and may potentially allow attackers opportunities to exploit them.
The federal government relies heavily on external service providers and contractors to assist in carrying out a wide range of federal missions. Sensitive but unclassified federal information is routinely processed by, stored on, or transmitted through nonfederal information systems. Failing to properly protect this Controlled Unclassified Information (CUI) could impact the ability of the federal government to successfully carry out required missions and functions.
The National Institute of Standards and Technology (NIST) created Special Publication 800-171 "Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations" to provide recommended requirements for protecting the confidentiality of CUI. Federal agencies should use these requirements when establishing contracts and agreements with nonfederal entities that process, store, or transmit CUI.
This Tenable Assurance Report Card (ARC) aligns with the Audit and Accountability (section 3.3) and System and Information Integrity (section 3.14) families of security requirements in NIST SP 800-171. These families are closely related and requirements focus on the monitoring, analysis, investigation, and reporting of unlawful, unauthorized, or inappropriate information system activity, including inbound and outbound communications traffic, to detect attacks and indicators of potential attacks. Using this ARC, an organization will be better able to correlate audit review, analysis, and reporting processes for investigation and response to indications of inappropriate, suspicious, or unusual activity. Organizations will also be able to monitor information system security alerts and advisories and take appropriate actions in response.
More details on each of the policy statements included in the ARC are given below. Clicking on a policy statement will bring up the analysis screen to display more details related to that policy statement. The ARC policy statement parameters are guides that can be customized as necessary to meet organizational requirements.
This ARC is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance. The dashboard requirements are:
- Tenable.sc 5.4.0
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
- Compliance data
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist an organization in monitoring inappropriate information system activity. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to find vulnerabilities, and can also make use of audit files to assess compliance. Passive listening provides real-time monitoring to collect information about systems and vulnerabilities. Host data and data from other security devices is analyzed to monitor inbound and outbound communications traffic, to detect attacks and indicators of potential attacks. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure systems and safeguard sensitive information.
ARC Policy Statements
At least 95% of systems are sending logs - This policy statement displays the number of systems that are sending logs to the Tenable Log Correlation Engine (LCE) to total systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Logs can provide valuable information on network, application, and security events from multiple devices across a network. To get the clearest picture of network status and security, all systems on the network should be sending logs to LCE.
At least 90% of Windows and Mac OS systems have active up-to-date anti-virus protection - This policy statement displays the ratio of systems with active and up-to-date anti-virus protection to total systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. All systems should have active and up-to-date anti-virus software installed to protect against malware infections. Organization can use this information to identify and resolve anti-virus software issues on systems.
Less than 5% of audit compliance checks failed - This policy statement displays the percentage of audit compliance checks that failed. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Audit settings may include log retention and required event collection settings, among other things. Compliance is measured against those policy checks that reference standards such as the Cybersecurity Framework, NIST 800-53, NIST 800-171, the CIS Critical Security Controls, and ISO/IEC 27001.
Log Correlation Engines are running - This policy statement displays a non-compliant status if Tenable.sc has not received LCE events within the last 24 hours. CSC 6 suggests that comprehensive logging be enabled and hosts centralize their logs. Loss of event data could indicate a potential failure, configuration change, or license expiration has occurred and should be checked immediately.
No systems have exploitable vulnerabilities - This policy statement displays the ratio of systems that have exploitable vulnerabilities to total systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. An exploitable vulnerability is one for which malware already exists that can take advantage of the vulnerability in order to gain control of a system. Reducing the number of exploitable vulnerabilities can greatly help to reduce the risk to the network. Any exploitable vulnerabilities should be remediated immediately.
No systems have high indicator alerts - This policy statement displays the number of systems with high indicator alert events to total systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. High indicator alert events indicate that a suspicious sequence of 10 or more events occurred. Events could be the result of denial of service attacks, suspicious network connections, or malicious code being executed.
No systems have been detected interacting with malicious IPs - This policy statement displays the percentage of total systems that have been detected interacting with known malicious IP addresses. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Tenable.sc receives a daily and updated list of IP addresses and domains that are participating in known botnets. Using this information, systems on the network that interact with known malicious IP addresses can be detected. Any systems interacting with known malicious IP addresses should be investigated immediately by the organization to minimize security risks.
No systems have data leakage events - This policy statement displays the percentage of total systems where data leakage has been detected. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Any type of data leakage, either intentional or unintentional, can result in the exposure of confidential or private information. This policy statement will help to measure the effectiveness of security controls in place on the network. Systems with detected data leakage should be investigated immediately to minimize potential security risks.
No systems have had unusual VPN activity in the last 72 hours - This policy statement displays the number of systems with unusual VPN activity to the total number of systems detected on the network. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. This policy statement utilizes the LCE event “VPN_Login_From_Unusual_Source”. This event triggers when a VPN login originates from a source IP address that is not part of the same address space as what is normal for the login user ID. Systems that detect unusual VPN activity should be investigated immediately by the organization, as this could indicate possible unauthorized activity.
Less than 15% of systems have detected intrusion activity - This policy statement displays the number of systems with potential intrusion activity to the total number of systems detected on the network. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Intrusion events include password guessing, IDS events, network sweeps as well as other things such as malicious activity. Intrusion events could indicate ongoing attacks or hosts that have been compromised. Organizations should investigate intrusion events to determine the scope, impact, and actions needed for remediation.
Less than 5% of systems report activity spikes - This policy statement displays the percentage of systems reporting activity spikes. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Activity detected by the Tenable Log Correlation Engine (LCE) for the current hour is compared to the same hour in all previous days for each IP address. Any large anomalies (spikes) in activity will be automatically reported by LCE. Activity spikes could indicate malicious behavior or network issues and should be investigated further by the organization to determine the cause.
Less than 5% of systems report continuous activity - This policy statement displays the percentage of systems reporting continuous activity. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Continuous activity is activity that occurred over a long period of time. The activity may be legitimate, or it may be activity such as port scanning, server issues, repeated login failures, or potential malware activity. The organization should further investigate any systems with continuous activity.