Tenable Identity Exposure secures active directory and eliminates attack paths
Tenable Identity Exposure secures active directory and eliminates attack paths
-
Decrease identity risk and secure human and machine identities with best practices for preventative Active Directory Security.
-
Unified view of identities across Active Directory and Entra ID (Formerly Azure Active Directory) deployments.
-
Enhance your ITDR (Identity Threat Detection and Response) capability by auditing Active Directory directory changes in real time and establishing timelines for indicators of attack.
-
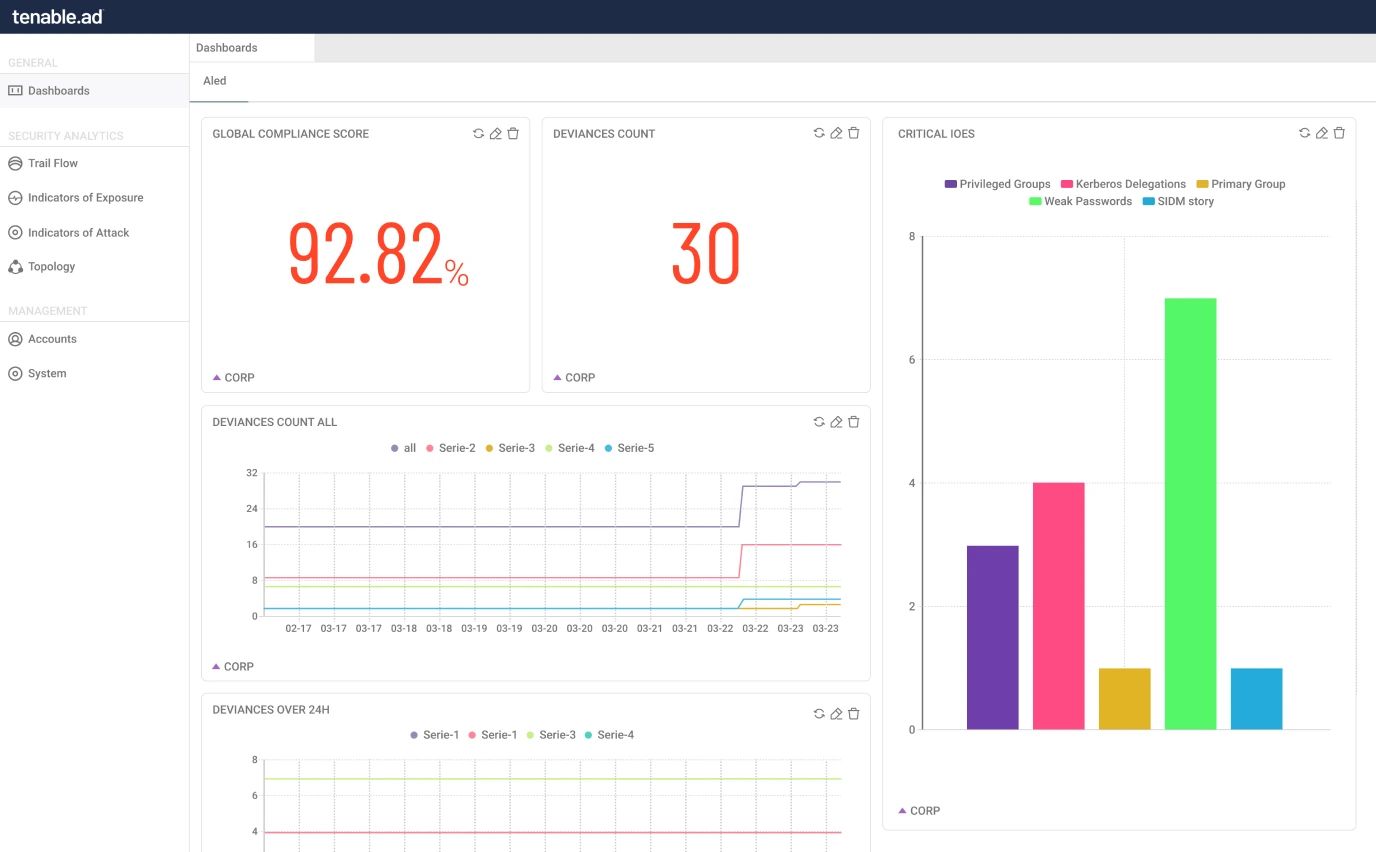
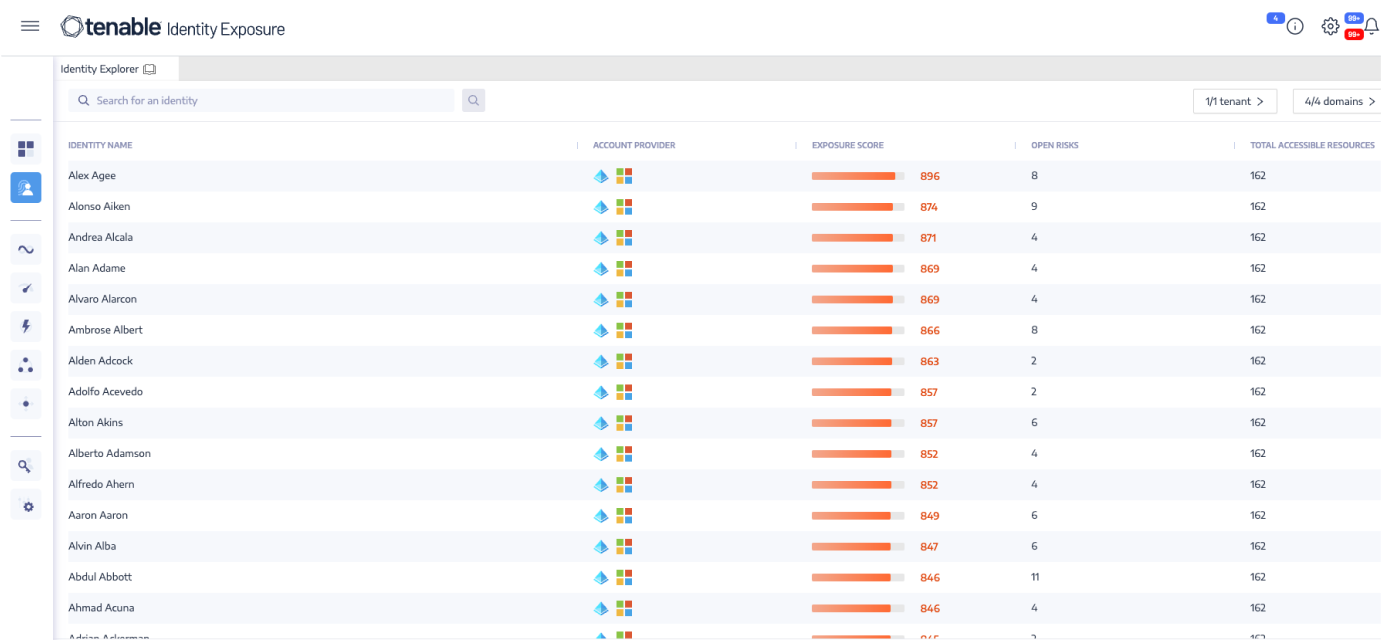
Exposure management is based on calculated identity risk scores, focusing on areas of highest risk.
-
Continuous validations and assessment of AD for attack prevention and detection.
cloud-security/use-cases/ecosystem-view-of-risk /products/nessus/nessus-professional/refer-a-friend /products/nessus/nessus-professional/refer-a-friend ظطلب إصدار تجريبي
Tenable customers - 65% of the Fortune 500 trust Tenable
With Tenable Identity Exposure, you'll always have:
Tenable Identity Exposure benefits
With Tenable Identity Exposure, you'll always have:

Identity unification and
AI-driven risk scoring
يمكنك توحيد حسابات Active Directory والحسابات الهجينة وحسابات Entra ID جميعها في طريقة عرض واحدة.Gain control of identities dispersed between multiple directory services, domains and forests in a single view. Prioritize remediation with our data-science backed identity risk score that ranks identities by level of risk to the environment. Optimize team efficiency and focus efforts on risk mitigation and preventing attacks.
Expand
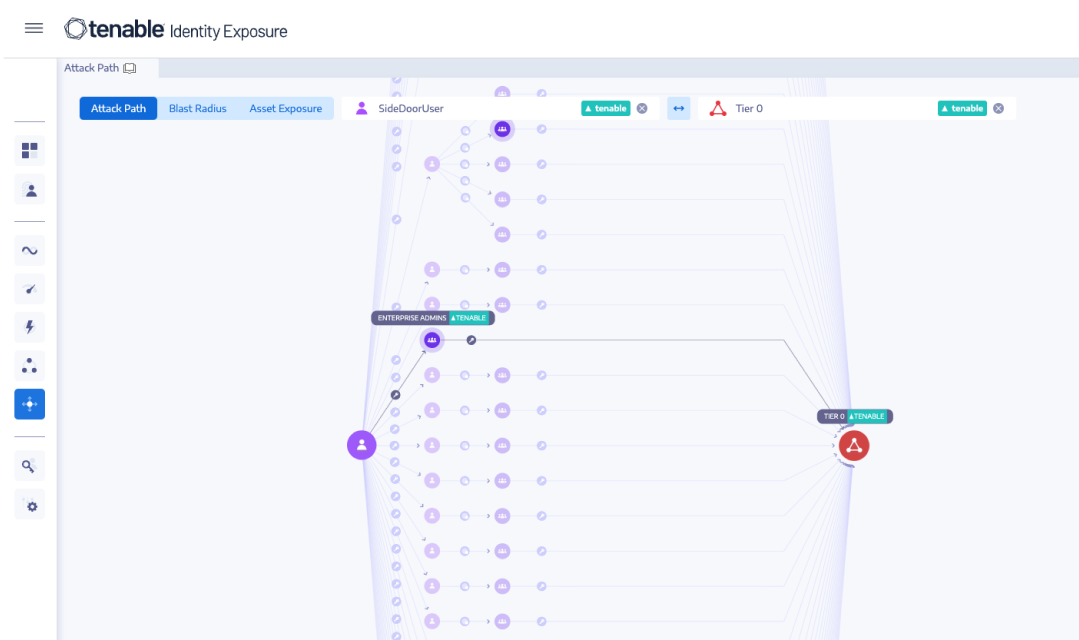
Eliminate attack paths that lead to domain domination
Make sense of the complex interrelationships between objects, principals, and permissions, and eliminate attack paths that lead to domain dominance. Attack path analysis surfaces all the possible steps that attackers could take to move laterally, escalate privileges, and gain control over your enterprise directory services.
Expand
Continually assess directory services security in real-time
يمكنك تقييم الوضع الأمني لخدمات الدليل لديك والكشف عن الثغرات الأمنية والتكوينات الخطرة والتسلل للأذونات.Tenable Identity Exposure provides a step-by-step tactical guide that identifies affected objects, eliminating the need for time-consuming manual reports or scripts, hardening AD and Entra ID.
Expand
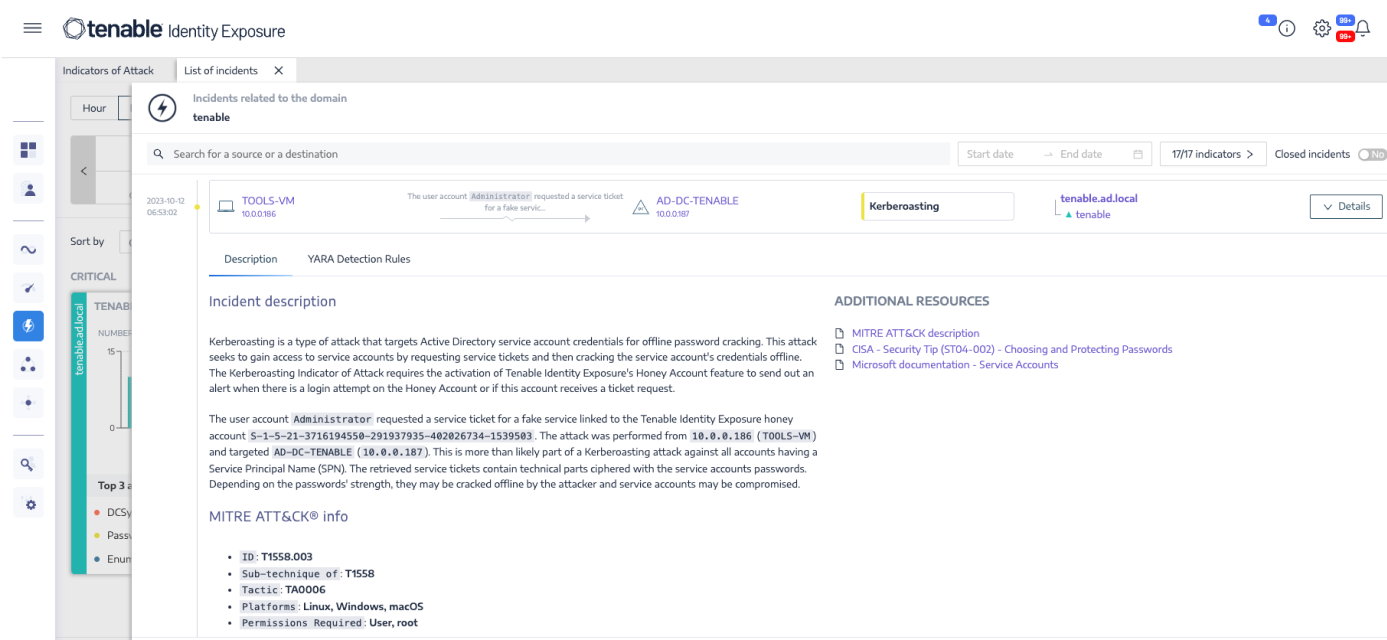
Real-time attack detection
Receive instant alerting against indicators of attack, including credential dumping, Kerberoasting, DCSync, ZeroLogon, and many more. Respond to attacks in real time by integrating Tenable Identity Exposure with your SIEM and SOAR. Tenable’s research team regularly updates indicators of attack as new identity-based exploits are discovered.
Expand
Investigate and inform
Reduce MTTR (mean time to respond) and audit active directory by capturing all changes to Active Directory using Trail Flow. Inform your incident response teams and enrich your security operations processes with real-time prioritization and detailed remediation steps.
Expand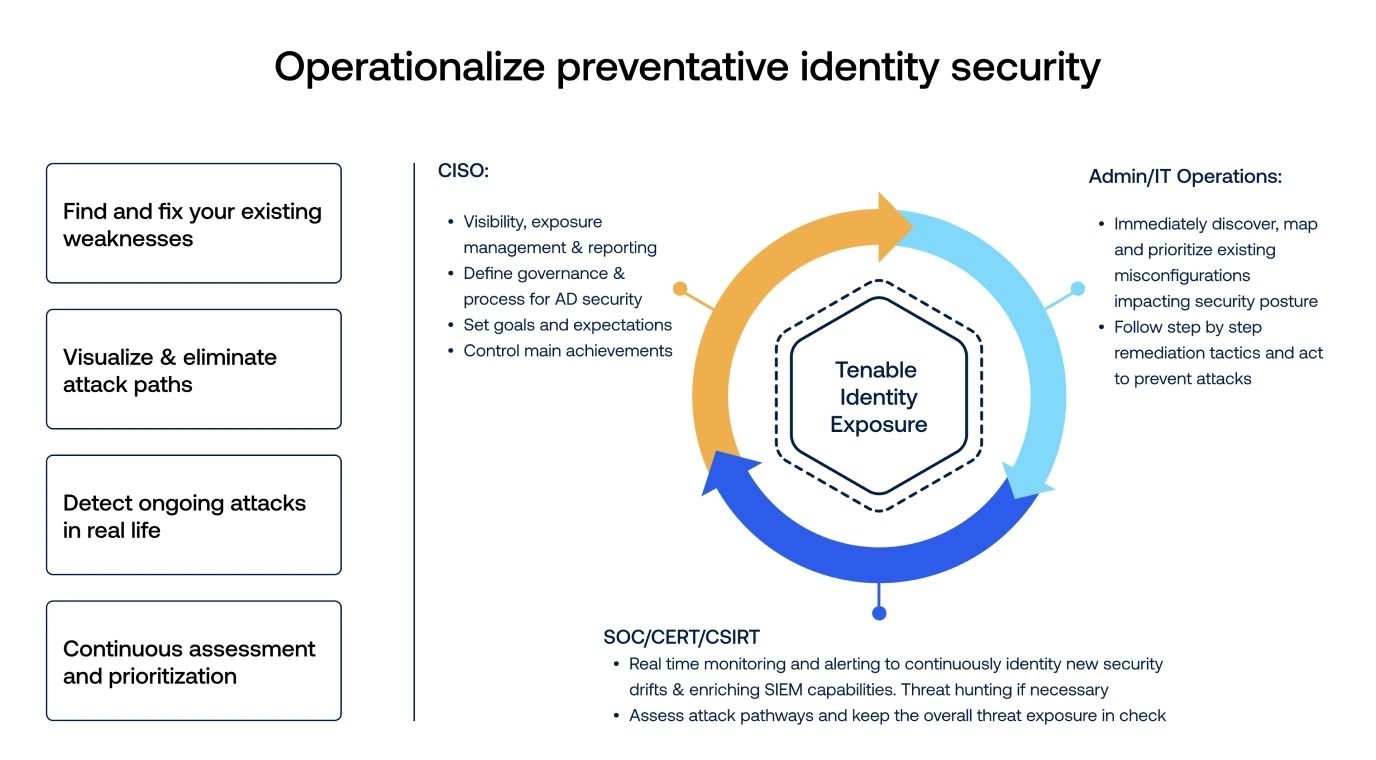
Introduction to Tenable Identity Exposure and Identity Aware Exposure Management
A quick walkthrough of Tenable Identity Exposure highlighting why Identity aware exposure management provides critical context to prioritize cyber security remediation efforts.
Continuously detect
and prevent active directory attacks
-
لا يوجد وكلاء. No privileges.
لا تأخيراتيمنع شن الهجمات المتطورة على Active Directory، ويكشفها دون وكلاء وامتيازات.
-
Clouds covered
Extended support for protecting public and hybrid cloud Azure Active Directory deployments and managing cloud identity risk with Indicators of Exposure specific to Azure AD.
-
يُنشر في أي مكان
يوفر الحل Tenable Identity Exposure مرونة اثنين من التصميمات المعمارية. حل في مكان العمل للحفاظ بياناتك في الموقع وتحت سيطرتك. وحل البرنامج كخدمة (SaaS)؛ حتى تتمكن من الاستفادة من السحابة.