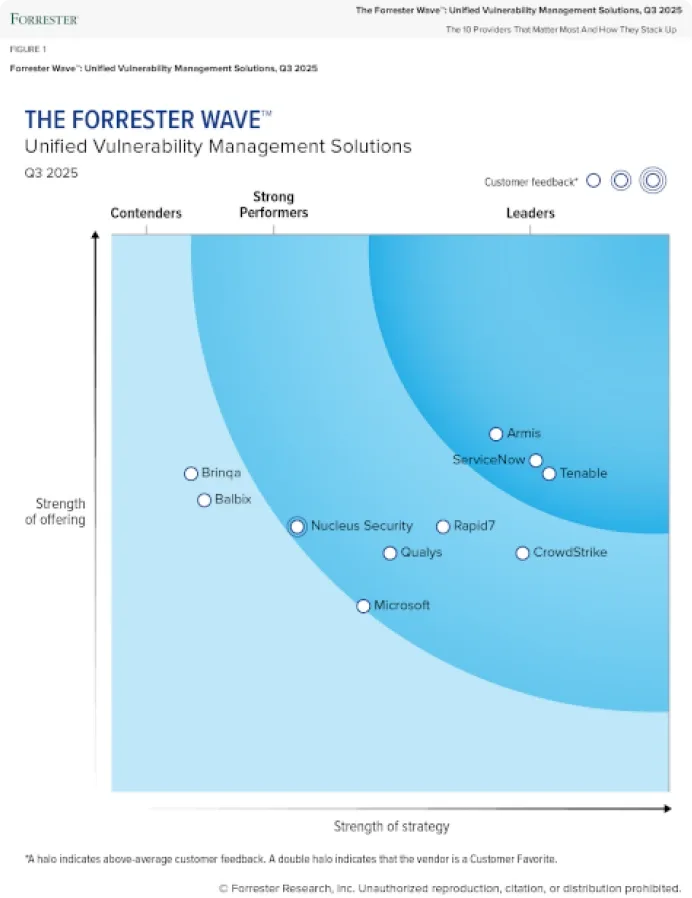
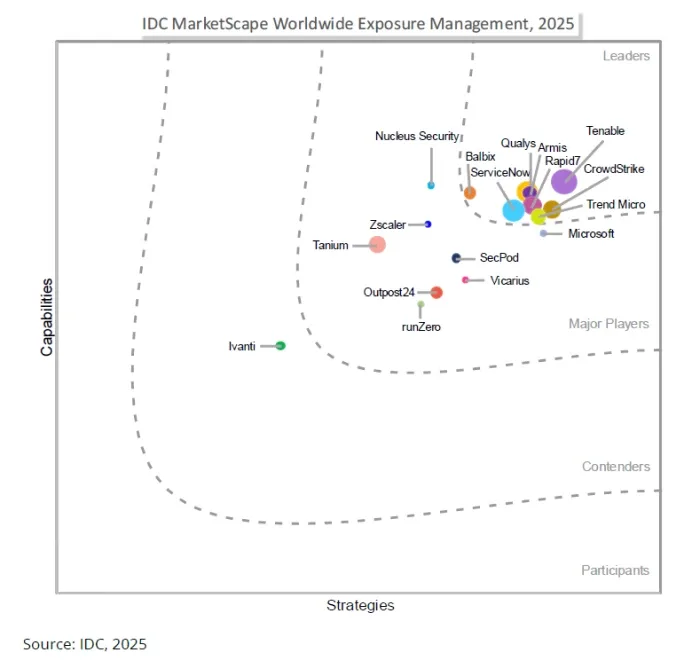
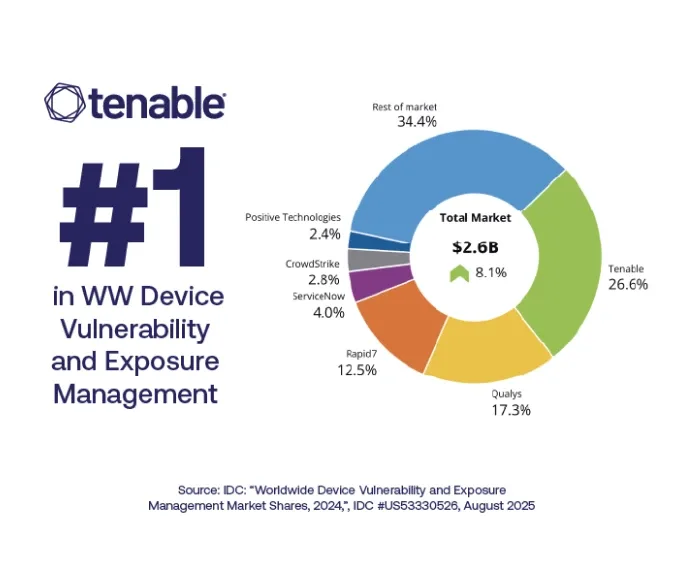
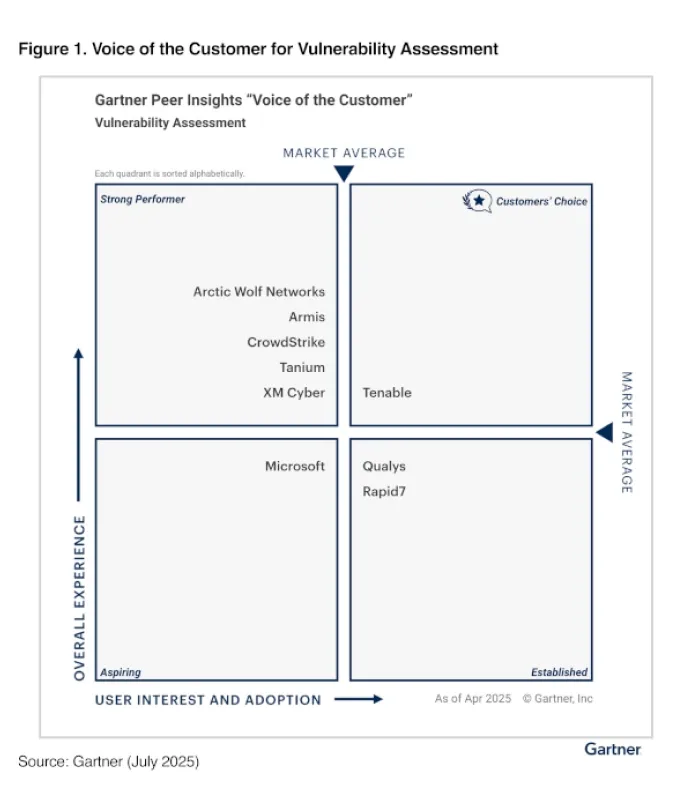
Tenable versus CrowdStrike
“Good enough” exposure management from CrowdStrike leaves you exposed
CrowdStrike’s endpoint-first approach to exposure management leaves dangerous visibility gaps across cloud, OT, IoT, web apps and networks — gaps attackers exploit. Tenable delivers complete attack surface coverage with faster and more accurate exposure detection, stronger compliance capabilities and richer vulnerability intelligence so you can know, expose and close risk everywhere it lives.
Don’t settle for “good enough.”
Talk with one of our experts and learn how Tenable delivers the exposure clarity, coverage and confidence an endpoint vendor can’t match.